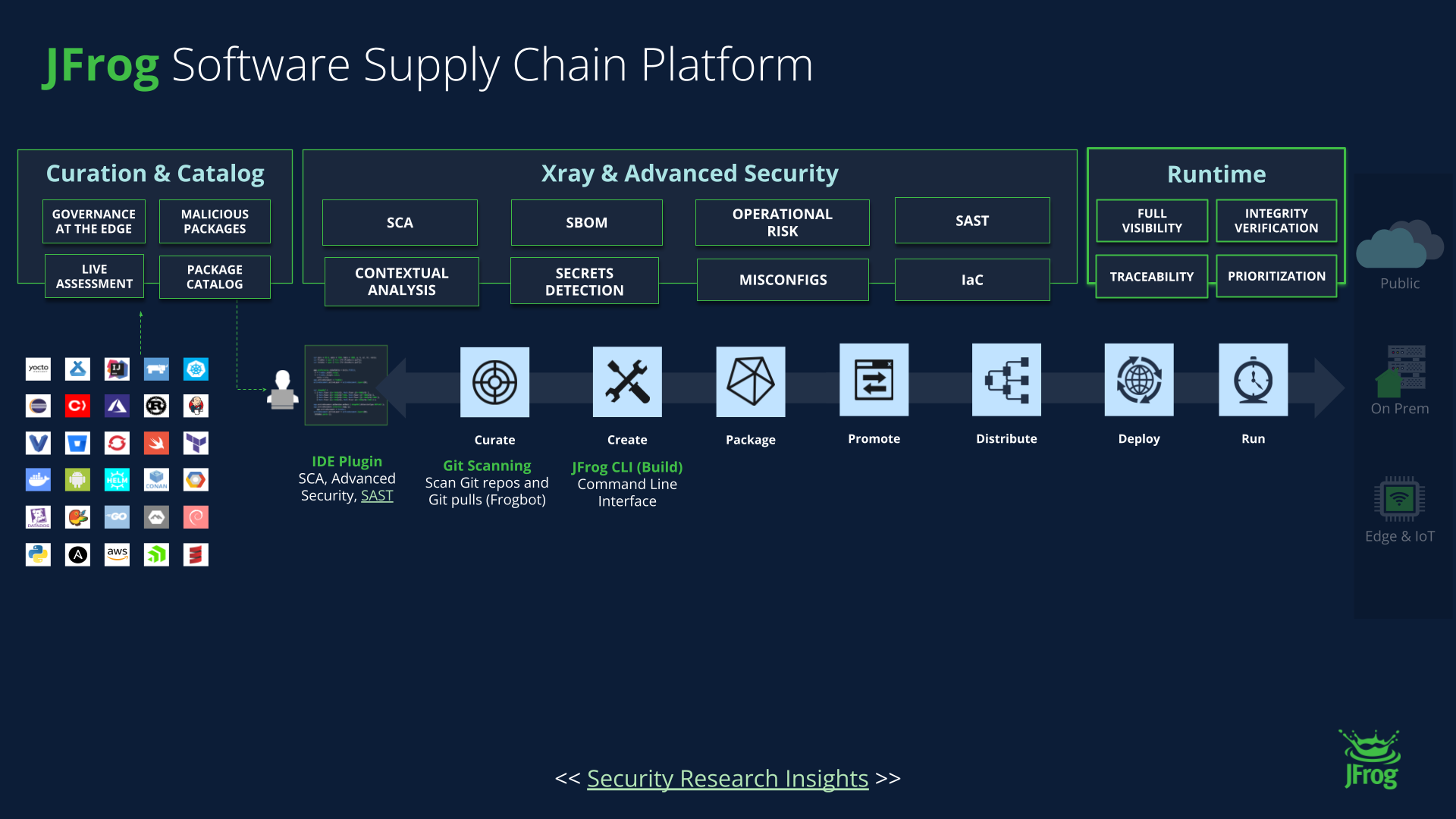
Definition
A software supply chain attack occurs when malicious actors insert malware or tampered code into the software development or delivery process—often targeting third-party dependencies. These attacks exploit trust relationships between developers, tools, and components, giving attackers a stealthy and scalable way to compromise systems.
Overview of Malware Insertion
Malware enters the software supply chain through insecure development practices, compromised third-party packages, and vulnerable infrastructure. As organizations rely more on open source and automation, their attack surface expands. These attacks are difficult to detect and increasingly common, causing DevSecOps teams to take a more proactive approach.
Understanding Software Supply Chain Attacks
Unlike traditional cybersecurity threats that target the perimeter—such as firewalls, endpoints, or network access points—software supply chain attacks exploit the internal trust between systems and tools. These attacks don’t need to breach firewalls; they embed themselves in code and packages that developers believe are safe. By embedding malicious components into development tools or source code dependencies, attackers can compromise software long before it reaches production.
CI/CD pipelines are an increasingly attractive target. Attackers may inject malicious scripts into build processes or tamper with automation tools like Jenkins or GitHub Actions. These pipelines, which are designed for speed and efficiency, often lack strict security controls, making them vulnerable to subtle compromises that ripple through multiple applications.
Software supply chain attacks exploit the interconnected nature of modern development. Rather than attacking systems directly, attackers aim upstream—compromising the components, tools, or libraries used during software creation. The goal is to insert malicious code that reaches production environments without detection.
Attackers often compromise open source libraries, inject poisoned code into container images, manipulate CI/CD pipelines, or act as malicious contributors. These approaches take advantage of blind spots in DevOps pipelines and the distributed, fast-moving world of software development. One tactic might involve publishing a trojanized version of a widely used npm package, which then silently becomes part of thousands of downstream applications.
Types of Malware in Software Supply Chains
In addition to traditional malware types, supply chain-specific threats include dependency confusion, brandjacking, and typosquatting. Dependency confusion, for instance, occurs when internal packages are accidentally overridden by identically named packages from public registries. Attackers exploit this by uploading malicious versions to those registries, tricking builds into pulling their compromised code instead.
Brandjacking and typosquatting involve creating malicious packages that closely mimic trusted ones, relying on developers mistyping a name or overlooking a subtle variation. Once included in a build, these impersonated packages behave like legitimate software—until they execute malicious actions during runtime or deployment.
Malware embedded in the supply chain is typically more subtle and insidious than traditional forms. Instead of launching immediate attacks, it often hides within trusted components, evading detection for long periods. Some malware is programmed to activate under specific conditions, adding another layer of stealth.
Examples range from credential stealers baked into scripts, to backdoors quietly residing in container images. In some cases, logic bombs are embedded in packages, designed to activate on deployment. Attackers may also use obfuscation to conceal harmful code inside dependencies.
A widely cited example is the SolarWinds Orion breach, where attackers slipped malicious code into a legitimate software update. Another case—the event-stream incident—saw an attacker take control of a popular npm package and quietly introduce malware to extract data from cryptocurrency wallets. What makes these threats especially dangerous is how they inherit the credibility of the upstream project or vendor, often bypassing traditional perimeter defenses.
The Impact of Open Source Software on Malware Risks
Open source software is foundational to modern software engineering, but its widespread use has also made it an attractive target for attackers. Organizations often rely on hundreds—or even thousands—of open source components. That is why it is so important to make sure packages undergo vulnerability scanning before they enter the development environment. Unfortunately, many organizations pull OS packages into projects automatically, with little scrutiny which creates an ideal entry point for malware.
Risks increase when projects are poorly maintained, or when attackers compromise trusted maintainers and insert harmful code. Developers might unknowingly include malicious packages simply by running an npm install or adding a dependency with unresolved sub-dependencies.
The compromises of ua-parser-js and color.js/faker.js highlight how quickly malware can spread once introduced into popular libraries. In both cases, malicious code propagated widely before being discovered. These incidents show how a single open source package can serve as a delivery mechanism for malware at scale.
More recently, the Shai-Hulud npm open source repository attack, which was reported by JFrog along with guidance on remediation and prevention, illustrates how wide malware insertion attacks can spread in multiple waves to unsuspecting developers using well known and generally secure OSS repositories.
To reduce these risks, organizations should track and audit dependencies, prefer actively maintained projects, lock dependency versions to avoid surprise updates, and scan components regularly using security solutions such as JFrog Xray and protect against potentially harmful OSS packages with JFrog Curation.
Why are Software Supply Chain Attacks Increasing?
Supply chain attacks have become more common for several reasons. The first is simply that the software development process has grown more complex. With hundreds of third-party tools, services, and libraries in use, there are more opportunities for attackers to find weak spots. This complexity also makes it harder for security teams to maintain visibility.
The pressure on DevOps for faster development cycles and continuous delivery has accelerated the pace of software changes, sometimes at the expense of thorough security reviews. Automation and speed are prioritized, but this can leave gaps that malicious code can exploit. In addition, the return on investment for attackers has increased—compromising a single upstream component can affect thousands of downstream applications.
Nation-state actors have also begun leveraging these methods as part of their cyber arsenals, recognizing the reach and subtlety of supply chain compromises. The broader context of digital transformation has amplified the urgency. As businesses adopt cloud-native technologies, containers, and infrastructure-as-code, they often introduce new tooling faster than they secure it—leaving their supply chains exposed.
Where does Application Security Break Down?
Despite awareness of these risks, many organizations struggle to identify exactly where their defenses fail. Security gaps often stem from lack of visibility—development teams may not even know all the components their applications rely on. Legacy infrastructure and outdated tooling can further obscure the source and status of software dependencies.
Time pressures also drive risky behavior. Developers under deadline might copy code from public forums, disable security warnings to resolve build issues, or rely on unvetted plugins to accelerate progress. Even well-intentioned teams face “security fatigue,” where the constant influx of alerts makes it easy to miss—or ignore—genuine threats.
These failures aren’t always technical. Organizational silos, unclear ownership of security responsibilities, and inconsistent processes all contribute to weak points in the supply chain. Without a coordinated effort across engineering, security, and operations, malware can exploit even well-intentioned teams.
How to Strengthen Software Supply Chain Security
Reducing malware risk requires more than traditional perimeter defenses. It calls for a security-first mindset throughout the entire software lifecycle. Adopting a DevSecOps approach helps embed security at each stage—from code and build to release and runtime.
One of the most effective practices is to continuously scan artifacts in the pipeline using automated vulnerability scanning tools that detect known flaws in packages, containers, and binaries before they reach production. It’s also vital to validate all artifacts—signing and verifying packages, container images, and binaries to ensure their authenticity.
A software bill of materials (SBOM) offers transparency into the components that make up an application. Knowing what’s in your software—and where it comes from—enables quicker responses to newly disclosed vulnerabilities. Automated policy enforcement can further reduce risk by blocking builds that don’t meet defined security criteria.
Choosing and vetting third-party components with care is another foundational practice. Teams should rely on reputable sources, enforce version control, and prefer packages with active maintainers and a clear security posture. Integrating vulnerability management solutions ensures that threats are not only identified, but also remediated quickly.
How JFrog Supports Software Supply Chain Security
As software becomes more interconnected, malware in the supply chain poses a growing and urgent threat. Modern development practices have introduced new efficiencies—but they’ve also created blind spots. Protecting the software supply chain isn’t just about securing the end product—it’s about securing every component, contributor, and process that touches it.
Organizations must take a proactive stance by embedding security throughout their development workflows. This includes adopting automated scanning, maintaining visibility through SBOMs, validating artifacts, and carefully managing third-party dependencies. Resilience comes from making security an integrated, continuous function—not a gate at the end of development.
The future of supply chain security depends on transparency, automation, and shared responsibility. With the right strategy and tools, companies can protect their environments without compromising on speed or innovation.
For more information, please visit our website, take a virtual tour, or set up a one-on-one demo at your convenience.