JFrog Curation defends your software supply chain, enabling early blocking of malicious or risky open-source packages before they even enter. Seamlessly identify harmful, vulnerable, or risky packages, ensuring increased security, compliance, and developer productivity. This capability also extends to your other third-party downloads like IDE extensions and models.
Gain control and visibility over third-party package downloads. Drive organizational alignment, improve the developer and DevSecOps experience, and realize cost savings.
Track the open-source packages, IDE extensions and models downloaded by your organization to gain centralized visibility and control. Prevent harmful packages from getting into your software development pipelines as part of a holistic software supply chain platform.
Protect against known and unknown threats, allowing only trusted software packages, secured IDE extensions and models into your software development pipelines. Feel confident your development teams are developing with only pre-approved open-source components. Turn policy blocks into productive moments by automatically providing developers with the latest compliant package version, ensuring they build without friction or frustrating delays
Automated policies block third-party party downloads with known vulnerabilities, malicious code, operational risk, or license compliance issues. Select from predefined templates to drive governance over the open-source consumed in your organization. Learn More
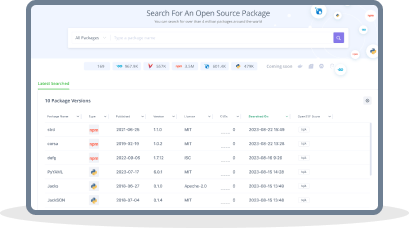
Explore the metadata of the open-source packages you want to use with JFrog Catalog. Discover their version history, security vulnerabilities, OpenSSF score, license data, operational risk, and if they have any dependencies and transitive vulnerabilities. Over 12 million OSS packages have been cataloged for easy reference.
Transparency and accountability enable easy auditing of the open-source used by developers. Seamlessly-integrated vetting of software packages before entry into the SDLC, ensure a better developer experience with reduced remediation efforts and lower costs.
The largest data breach in history was due to a leaked access token. 1 billion records with personally identifiable information were stolen. Don't become the next data breach storyline and make sure you keep your credentials and secrets out of the hands of nefarious actors.
Want to See the Impact of All This Research? Discover how JFrog Xray can save your team time by reducing manual remediation and accelerating secure releases.
Calculate Your Security Time Savings
Yes
Curation checks dependencies before they are cached in Artifactory. Hence, Curation helps with proactive vetting of dependencies entering your organization
Curation reduces time spent on remediation and clears backlog faster by preventing new vulnerabilities from getting in
Security, license compliance, operational and custom conditions
Developer machine: Providing real-time feedback as you add or update dependencies
CI/CD Pipelines: Scanning your code during builds to prevent risky dependencies from being deployed
Manually looking up CVEs is time-consuming and doesn't provide a holistic view. Curation automates this process, integrates it into your workflow, and provides additional context like license information and operational risks. It also helps you understand the impact of vulnerabilities within your specific dependency tree
Yes, JFrog Curation is primarily focused on analyzing and managing open-source software dependencies
Curation works with Artifactory’s remote repositories by analyzing client’s requests and applying the specified policy conditions
Integration within the JFrog Platform provides a unified experience for managing your software supply chain. You get a holistic view of your artifacts and checks, controls based on their associated risks in one place, streamlining governance and security efforts
JFrog Catalog which is Curation's vulnerability databases is regularly updated with the latest information from various security sources to ensure you have the most up-to-date risk assessments
Block and Dry-run
Yes
Yes
Yes
Curation uses JFrog Catalog - https://jfrog.com/help/r/jfrog-security-user-guide/products/catalog
No, Curation and Xray work together to check and control OSS dependencies with slightly different use cases. Xray continuously checks dependencies through the SDLC and Curation checks them before they enter your development environment.
Yes. By applying automated policies, JFrog Curation acts as an intelligent gatekeeper that proactively vets and approves every extension. It directly blocks harmful or vulnerable tools before developers can install them, securing the 'final mile' of the software supply chain right at the developer's IDE.
Yes. With the new multi-site curation capability, JFrog Curation enforces governance policies consistently across distributed sites, while still being managed from a single point of control. supports governance from a single point of control