Definition
DevSecOps is the incorporation of continuous security testing into all stages of the software development lifecycle (SDLC). Development, security, and operations teams share the responsibility for creating secure software in a DevSecOps model.
Overview of DevSecOps
DevSecOps has intensified how and where security testing is done by scanning for vulnerabilities and adding multiple forms of security testing at different stages of the software development lifecycle (SDLC). The process repeats as new features are developed and bugs are fixed, creating a vision for a secure software development lifecycle (SSDLC).
Best practices should ensure that it incorporates security as an integral part of the software development lifecycle (SDLC). The process repeats as new features are developed and bugs are fixed. Another important consideration is that developers have become reliant upon open source packages which are now used in almost every project.
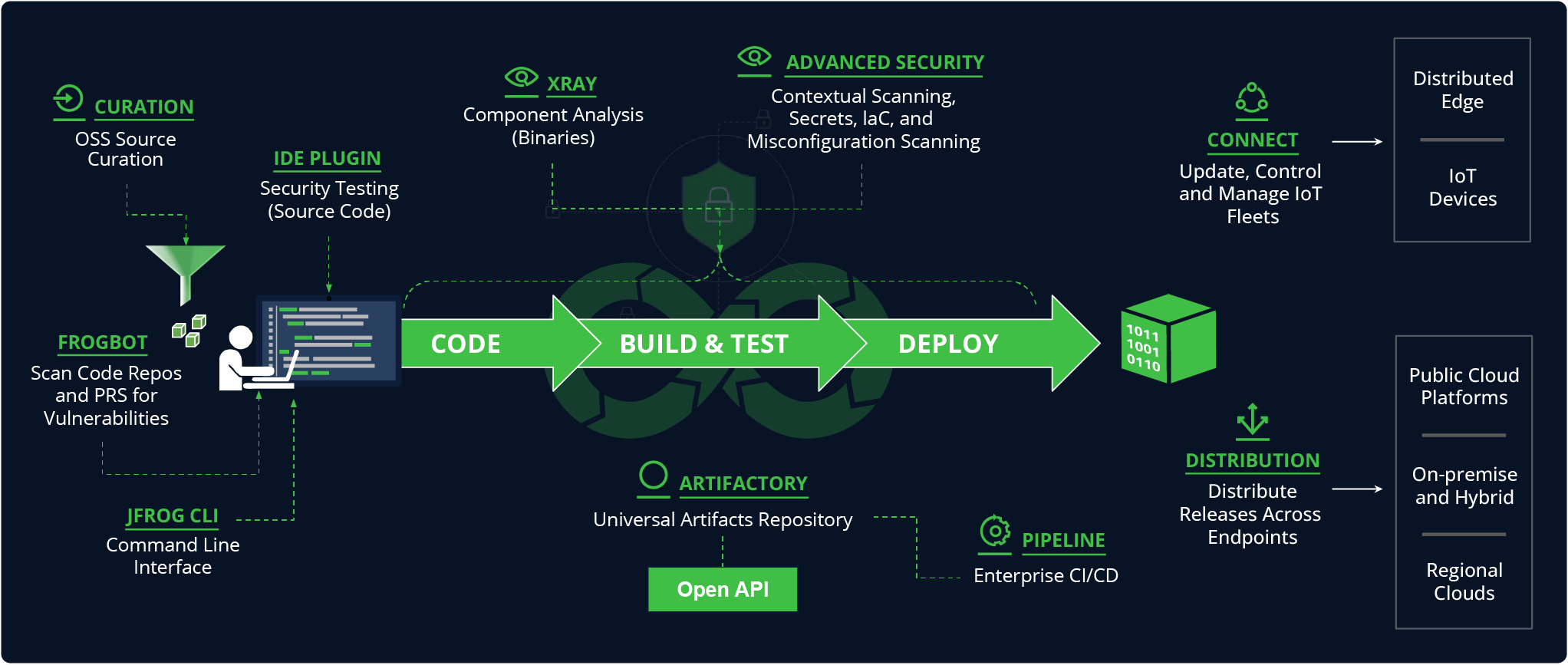
Flow of the software development lifecycle with corresponding JFrog solutions at each stage (click to enlarge the image)
Origin of DevSecOps
The need for DevSecOps emerged from the increased speed and velocity at which software was being developed, updated, and deployed from the application DevOps practices. As the release cadence increased, so did the rate at which vulnerabilities were introduced. In addition to increased velocity, the trend of component based development using open source packages also became prevalent in the industry which helped speed development but also opened a whole new set of security challenges and potential threats.
In short, DevSecOps has evolved into its own discipline that is now responsible for integrating security into every step of the software development lifecycle. But it doesn’t end there, as It continues to adapt to new infrastructures, emerging technologies, evolving threats, and improved best practices that ensure the delivery of secure and reliable software applications.
Importance and Benefits of DevSecOps Adoption
Over 90% of today’s applications use open source packages. This has the potential to introduce complications within an organization such as:
- Security vulnerabilities
- License compliance issues
Relying on developer reports and manual processes only provides a partial picture. Hence, security and compliance are an essential part of the DevSecOps process.
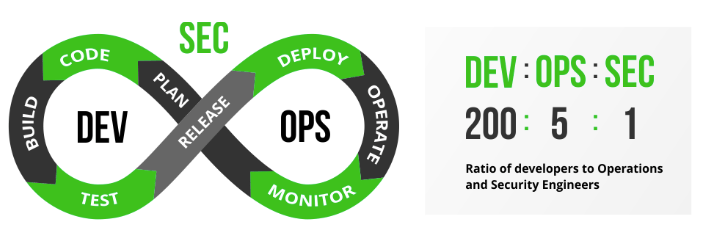
The ratio of developers to DevOps and security professionals
There is an existing ratio of 200:5:1 which is a short and demonstrative way to express the number of developers, the number of DevOps professionals and number of security specialists in a typical organization. This means that any security issue identified by a security vulnerability scanning tool needs to be reviewed by a very small DevSecOps team that may lack the technical expertise to fully understand the overall security ramifications of a specific vulnerability. This challenge can be met by shifting left to the developer and operations teams, making them share the responsibility for security and compliance issues, while bringing security as early as possible in the SDLC process.
Implementing and identifying security issues as early as possible in the development process, as well as automating security and compliance procedures can significantly improve security posture. More importantly, organizations that do not emphasize the “Sec” in DevSecOps, may face security and compliance issues that become evident closer to release, resulting in higher costs of remediation.
DevSecOps Principles
Introducing and implementing DevSecOps to an organization requires cultural and operational changes. Including: security training, tools and resources. Here are some useful concepts when making the shift in your organizational culture.
Security champions
These team members are responsible for the overall security aspects, making sure they are implemented in the DevOps pipeline, and exposing them to other members of the team. For example, A development team security champion will lead the implementation and usage in the team of:
- Static Application Security Testing (SAST), to discover security flaws in the source code
- Software Composition Analysis (SCA) for visibility into open source dependencies.
A QA team security champion will implement:
- Dynamic Application Security Testing (DAST) as part of automated QA cycles.
Security as an integral part of the process
DevSecOps practices require security as part of the SLDC, rather than just before software is released to production. This means that developers integrate security scanning into the build process, as well as their IDE environment to identify vulnerable dependencies.
Easily accessible data
Developers outnumber security professionals by 200:1. Using dedicated IDE plugins, can bring security data directly into the tools developers are already using, making it simple to adopt. Introduce best practices for developers on how they can avoid security issues as they write their code.
Automated Governance
In addition to manual checks, such as code reviews, security checkpoints can be distributed at each phase of the DevOps pipeline to determine if your software can continue to the next phase. A governing system can automatically enforce company policies, and be able to take action accordingly without intervention:
- Notification of security or compliance violations (Email, Slack, Instant Messages, Jira, etc.)
- Blocking of downloads
- Failing of builds that depend on vulnerable components or fail to comply with license policies
- Prevention of the deployment of vulnerable release bundles
Key Concepts in DevSecOps
There are a couple of key concepts in DevSecOps regarding communications and development methodologies that are important to emphasize.
Collaboration and Communication
One of the major components for ensuring that security is implemented at every stage of development is the communications which enable collaboration between development, operations and security teams.
Cross-functional Teams
Cross-functional teams are necessary for creation of secure software applications. For example, the development team must produce the core product while operations makes sure all relevant artifacts are stored in a repository and security checks for potential threats and vulnerabilities. While there are many challenges due to conflicting priorities, cross functional teams are meant to increase collaboration, speed up software development and minimize risks.
Shared Responsibility
When it comes to software security, it is crucial to distribute the responsibility of everyone participating in the software supply chain including development, operations and security. By each team taking responsibility for its role in producing secure software, the aggregate result should be a more robust and resilient security posture, quick identification of potential vulnerabilities and an overall reduction in security incidents.
Communication Channels
Communications in DevSecOps, fosters collaboration, information sharing and increased coordination among multiple teams and the team members themselves. The common communications channels include team meetings, online chats, collaborative communications tools, bug tracking systems, knowledge sharing platforms, video conferencing and email. By leveraging these channels effectively, DevSecOps teams can enhance collaboration, streamline information sharing, and ensure that security considerations are integrated into every aspect of the SDLC.
The Role of Culture in DevSecOps
In a DevSecOps culture, each team member takes responsibility for the security of the jointly developed applications. The introduction and implementation of DevSecOps in a company therefore requires a change in corporate culture and a rethink of processes.
DevOps Culture
As DevSecOps builds upon DevOps, the approach naturally also draws on the basic principles of the DevOps culture, but adds security as a central value to the organizational culture.
Security Culture
Security culture is a set of principles and practices that prioritize security as an integral part of an organization’s values. While this applies to the entire organization, within the narrower focus of DevSecOps, it ensures that development and operations teams are aligned in all aspects of software supply chain security.
Security Mindset
A security mindset prioritizes security throughout the software development process, including being proactive, identifying potential vulnerabilities, communicating with the DevSecOps team and staying aware of the latest threats.
Security Awareness
Security awareness starts at the core of an organization. Development and operations teams must be educated and aligned regarding security best practices and what it takes to secure the supply chain security. To properly instill security awareness requires fostering a security-conscious culture that permeates every aspect of software development and general operations.
Continuous Learning
Successful implementation of security in an organization should have a continuous learning component designed to keep teams informed and encourage improvement. In addition, a feedback loop should be established where teams can share information regarding security concerns and updates.
Implementing DevSecOps in Organizations
As opposed to concepts, methodology and culture, implementation focuses on how security is actually integrated into development processes and used by DevSecOps teams in reality.
Assessing the Current State of Security Operations
One of the most important first steps in improving DevOps and Security procedures, is to establish a baseline, which is then used to measure improvements in performance such as speed of builds, frequency of releases, number of security incidents and other relevant metrics.
Security Vulnerability Assessment
An expert team of security researchers should be used to analyze novel attack vectors, monitor threats, scan malicious packages, and track potential vulnerabilities. Their assessment help to understand the weaknesses of the current processes while establishing a baseline for improvement.
DevOps Maturity Assessment
While not mandatory, performing a DevOps Maturity Assessment can be important when implementing DevSecOps in organizations. It helps to provide an understanding of current operations that help set goals and develop a roadmap by identifying risks and challenges, facilitating resource allocation, driving continuous improvement, and aligning stakeholders.
Building Security into DevOps Pipelines
Just as DevSecOps culture integrates security into traditional DevOps thinking, DevSecOps pipelines layer in security throughout traditional DevOps CI/CD pipelines. Building security into DevSecOps pipelines ensures security is taken into account at every stage of the development process.
Secure Coding Practices
It’s critical to ensure that strong access controls are in place for CI/CD servers, source code management systems, and other tools that developers use during the coding stage. If these precautions are not taken, there is a risk that attackers could compromise the development environment and insert malicious code into the application as happened, for example, in the SolarWinds attack.
Infrastructure as Code (IaC)
When deploying infrastructure as code, IaC files should be secured by checking the configuration is secure to keep cloud deployments safe and secure. An IaC security scanner is a vital tool than can provides a comprehensive, proactive solution to your IaC security concerns.
Compliance as Code
Automate regulatory and governmental compliance by referencing the software bill of materials available for all applications. It is also recommended to define granular policies and automate governance across the entire software supply chain to meet increasingly stringent compliance requirements with the least possible effort.
Tools and Technologies in DevSecOps
There are several families of security and compliance tools to address different aspects of the SDLC. This includes: Static Code Analysis (SAST), Software Composition Analysis (SCA), and different approaches for testing the code for vulnerabilities (DAST and IAST). In addition there are tools that are aimed to monitor and protect binaries in production environments against attacks that exploit vulnerabilities in either the code itself or the development environment. Ideally teams should aim to adopt tools that cover all of these areas to achieve complete SDLC security.
Security Testing
Security Testing uncovers vulnerabilities, threats and risks in a software applications with the goal of preventing potential attacks. It does this by identifying possible weaknesses which might result in injection of malicious code into applications themselves or their operating environments.
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) tools can help you in identifying vulnerabilities in your own proprietary developed code. Developers should be aware of and use SAST tools as an automated part of their development process. This will help to detect and remediate potential vulnerabilities early on in the DevOps cycle.
Dynamic Application Security Testing (DAST) & Interactive Application Security Testing (IAST)
Dynamic and Interactive Application Security Testing (DAST and IAST) tools test the running application’s exposed interfaces, looking for vulnerabilities and flaws. While DAST looks at the application as a black box, IAST uses instrumentation that combines dynamic application security testing (DAST) and static analysis security testing (SAST) techniques to increase the accuracy of application security testing.
Container Runtime Security Testing
Container Runtime Security tools monitor the containers in their runtime environment. Such tools provide different abilities including – fire walling on different levels, identifying anomalies based on behavioral analytics and similar variables associated with runtime environments.
Future Trends and Innovations in DevSecOps
Emergence of new threats, vulnerabilities, and attack vectors is a perpetual state of change in the security field. Organizations can effectively manage evolving security concerns by proactively adapting their DevSecOps methods by being updated about future trends and breakthroughs.
DevSecOps in Cloud-Native Environments
DevSecOps involves developing in cloud-native environments to handle the particular opportunities and problems brought about by cloud technologies like:
- Serverless Environments
- IaC Security
- Container Security
- Cloud Security Posture Management (CSPM)
- Tools for DevSecOps Cloud Automation
- Cloud-Native Security
- Shift-Left Security
With an emphasis on protecting cloud-native resources, these trends demonstrate how DevSecOps techniques are continuously evolving in the cloud throughout the SDLC to ensure the security and compliance of cloud-native apps and infrastructure.
AI and Machine Learning in Security
AI/ML technologies have the potential to greatly assist DevSecOps teams in automated security testing, threat Intelligence, anomaly detection, and analytics, resulting in better compliance and policy enforcement as well as increasing awareness and offering better training.
Although AI can help DevSecOps, it cannot yet surpass the team’s expertise and decision-making capabilities. So at this stage, AI should be viewed as a tool to improve DevSecOps efficiency, giving team members more time to concentrate on core tasks and long-term security objectives.
The JFrog Software Supply Chain Platform
The JFrog Platform is the universal software supply chain solution for DevOps, DevSecOps, and MLOps. With 50+ integrations, it can house your entire ecosystem of tools, providing automated, integrated, extendable, and secure software supply chain management. Continue to explore more topics related to DevSecOps here, or if you’d like to see the platform in action, schedule a demo or start a free trial at your convenience.