5 Software Security Best Practices
In a world where cybersecurity breaches are growing steadily in frequency and intensity, software security is a critical consideration for businesses of all types and sizes.

Devising a plan for securing software, however, can be a major challenge today. Application architectures are becoming more and more complex as organizations migrate to microservices, multicloud or hybrid cloud environments and Internet of Things (IoT)-based infrastructures. At the same time, reliance on third-party code, such as open source modules and libraries, means that businesses need to worry about the security not just of the code they develop in-house, but also of the software supply chains on which they rely.
This article offers guidance on addressing these challenges by discussing five best practices for securing software today. It focuses in particular on techniques that can protect complex software that relies on third-party components and that runs in highly dynamic environments.
Best practices for software security
No matter which type of application you develop or how you deploy it, the following strategies will help keep it secure.
Know the components of your software
A 2021 report found that 70 percent of applications contain flaws that originate in open source components. The first step in protecting against risks like this is to identify the components within your applications so that you can determine whether they are vulnerable.
This is not a simple task, given that there are many ways in which open source components can find their ways into an application’s codebase. Developers could include libraries or modules dependencies within source code. They could copy and paste third-party code into their own codebase. They could incorporate external dependencies into container images. And so on.
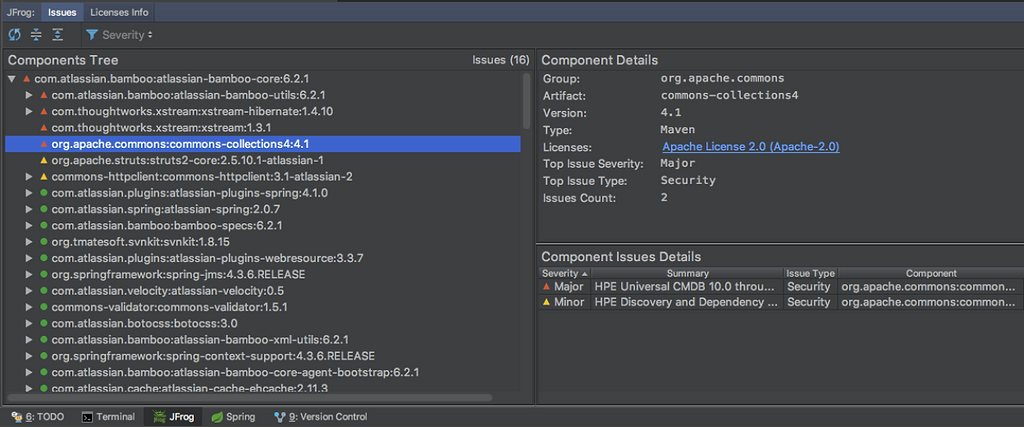
Analyzing software components with JFrog Xray.
In order to detect third-party components within your codebase at all layers of the codebase and all stages of development, you can use a Software Composition Analysis (SCA) tools. SCA tools can scan both source code and binaries to identify the components within them.
SCA tools work by parsing all layers of an application and looking for components that resemble those drawn from external sources, such as an open source software repository. They also check dependencies to determine which third-party components an application requires to run.
Continuously monitor for vulnerabilities
After identifying the components of your software, you should continuously scan vulnerability databases to determine whether any of those components contain known risks. Vulnerability databases track security flaws that are known to exist in open source libraries, modules and other resources that developers could incorporate into applications.
Continuously monitoring vulnerability databases manually is not practical. Instead, use a vulnerability scanner, such as JFrog Xray, which automatically alerts you to security risks within software components. Xray also offers the advantage of being able to identify the components of your software, so that you don’t have to perform that step using a separate tool.
Vulnerability analysis with JFrog Xray.
This means that, by using Xray, you don’t have to deploy different tools to identify components and check them for vulnerabilities.
Patch and update software
Keeping software patched and up-to-date is another basic safeguard against software security risks.
Knowing which components exist in your software is critical for ensuring that you patch and update your software comprehensively. If you don’t know about third-party components within your codebase, you can’t identify when patches or updates are available for those components.
Assess risks with threat intelligence
Not all software security risks pose an equal threat. Some flaws can only be exploited under unusual conditions, which may not exist in your configuration. Others may allow only for minor breaches, such as the leakage of debugging information that, generally speaking, is not highly sensitive from a security standpoint.
Given the variation in threat intensity, it’s wise to assess each risk that you discover within your codebase in order to determine which level of priority to assign it. Software scanners that incorporate threat intelligence reporting make this easy to do because they offer context on the seriousness of each vulnerability that they report.
Audit software configurations
Sometimes, the greatest software security risks lie not in software itself, but in the way it is configured. For example, an application that is designed for use only on a private network may become vulnerable if firewall rules expose it to the public Internet.
To protect against this type of risk, you should scan the configurations of the software environments in which applications run, in addition to scanning the applications themselves. Configuration auditing software can automatically assess your configurations and alert you to potential oversights that may enable or exacerbate software security problems.





