Advanced DevOps Security With Development Flexibility
The only Advanced DevOps-centric security solution is now available as self-hosted, cloud, multi-cloud, and hybrid.
Announcing the general availability of JFrog Xray’s advanced security features in self-hosted subscriptions, organizations have the flexibility to manage and secure their software development pipelines in-house and in the cloud.
Since Developers and the DevOps infrastructure are the primary attack vector in the software supply chain, we designed our platform and the advanced security features to better discover, assess and remediate security vulnerabilities and automate and integrate into existing software development ecosystems. Including:
- Container Contextual Analysis of CVEs
- Detecting Exposed Secrets
- Infrastructure-as-Code (IaC) Security
- Insecure Use of Open-Source Libraries and Services
Customers can now utilize these advanced DevOps-centric features in their chosen software development pipeline strategy. This offering puts leading-edge binary-centric security capabilities into the hands of more organizations looking to strengthen their software supply chain (SSC) for self-hosted development.
JFrog Advanced Security Features… A Refresher…
JFrog’s advanced security capabilities augment Xray’s software composition analysis with the ability to detect and protect against software supply chain threats. The features add a new approach of in-depth source and binary scanning to look into data that is not accessible via traditional package managers, SBOMs, or typical artifact metadata.
This allows a new understanding of the security posture of the analyzed binaries and code, especially regarding container images. The advanced scanners allow the identification of security issues that in most cases can’t be found via source code analysis alone.
Source Code Analysis is Not Enough
Source code analysis is not enough to truly analyze the context of security vulnerabilities. The context can only be understood by looking at the binary, which contains more information than the source code alone. Containers and archives deliver the details of the software’s journey and context for running in production, and hence what is being targeted by today’s attackers. Binaries contain critical information, making it possible to decipher the contextual insight to determine whether a vulnerability is definitely applicable to an application and considered a risk.
Using in-depth binary scanning enables a comprehensive understanding of the security issues in context – not only identifying the issues but also understanding their impact (if any) in production.
Continue reading to learn how the new advanced security features can help secure your software supply chain.
Spend Less Time on False Positives
Are you tired of using security tools that overwhelm you with countless vulnerabilities – many of which don’t even pose a substantial risk? Do traditional scoring methods waste your valuable time by ignoring critical software attributes? It’s time to take your security game to the next level with contextual analysis. By understanding the vulnerability context, you can prioritize your focus on the vulnerabilities that truly matter and avoid wasting time on irrelevant ones. Don’t settle for subpar security measures – switch to a solution that takes your software’s unique configurations and security mechanisms into account. With contextual analysis, you can finally achieve the secure software development you deserve.
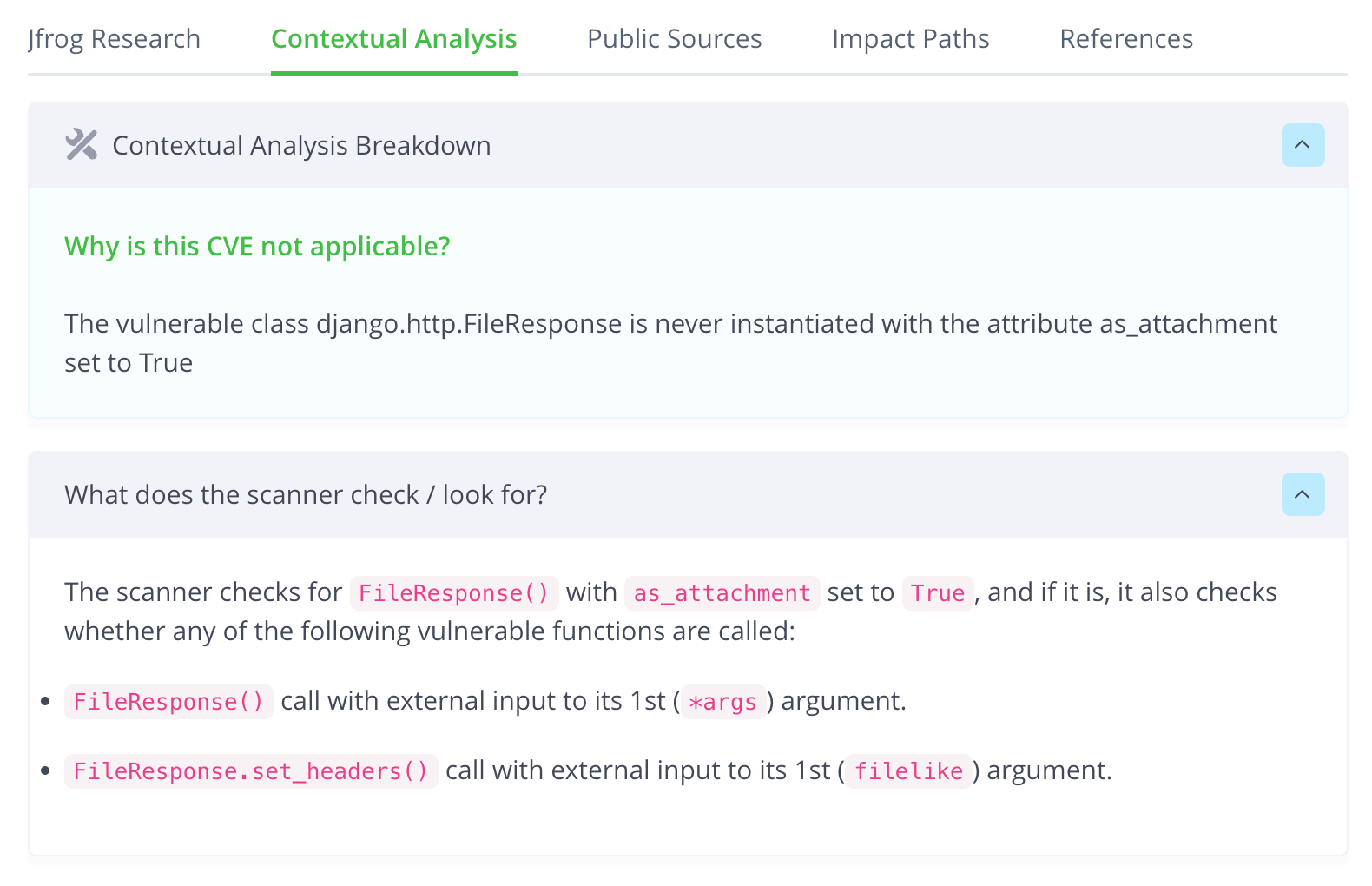
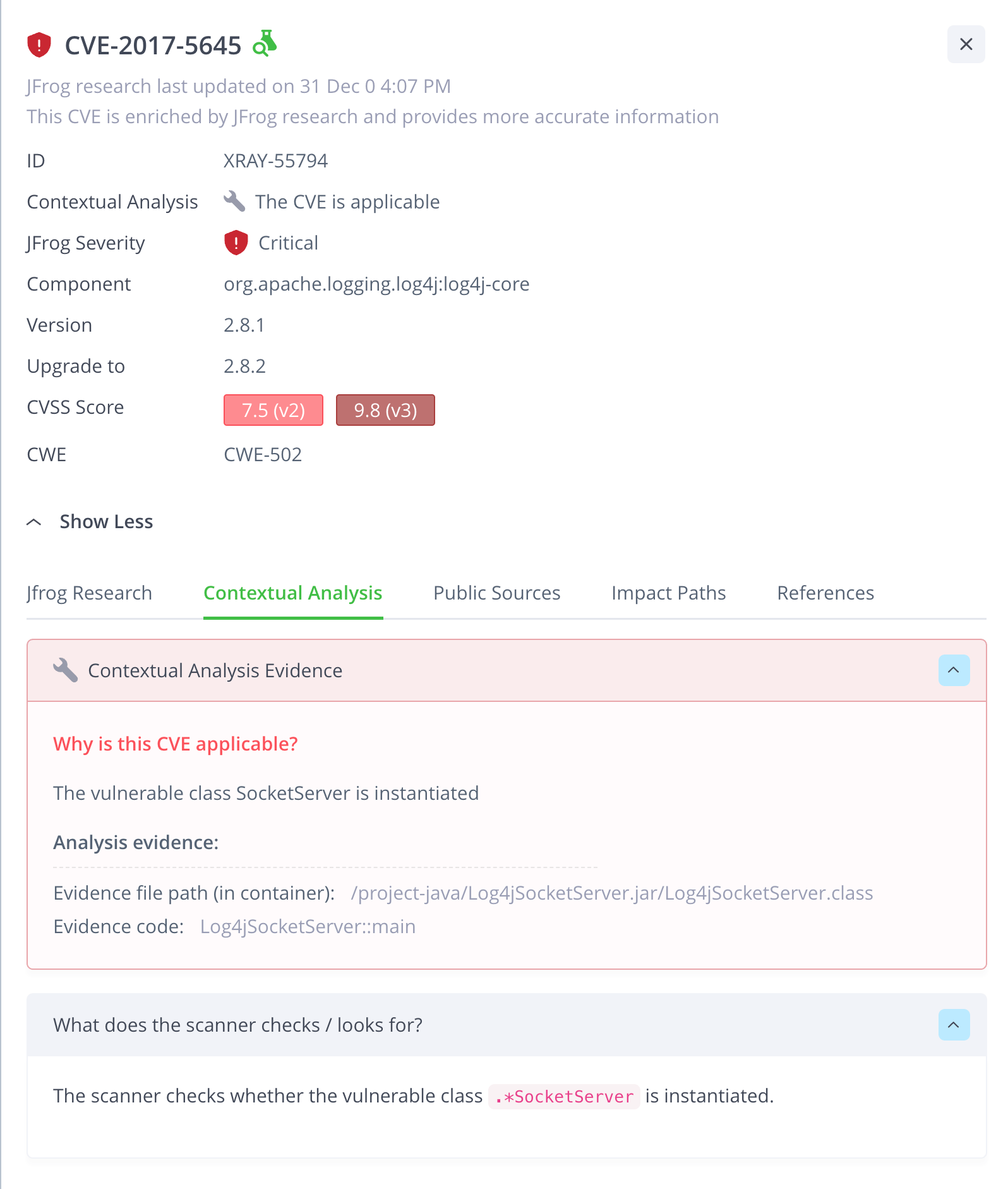
The contextual analysis engine (the first-of-its-kind for containers) examines the applicability of identified CVEs, by analyzing the container contents and attributes. It checks if the first-party code calls the vulnerable function in the OSS package, associated with the specific CVE. It also scans additional configurations and file attributes for CVE exploitation prerequisites.
Get ahead of the game and prepare for the new era of software supply chain security regulations with JFrog’s contextual analysis feature. With regulations like the 7900 bill requiring zero security-impacting CVEs, it’s crucial to have a tool that can help you meet these standards. Our contextual analysis goes beyond simply identifying vulnerabilities – it also provides solid, actionable, and cost-effective remediation that considers the unique attributes and configurations of your container. Say goodbye to the daunting task of fixing everything and hello to an efficient approach that prioritizes critical issues.
This feature can be a real asset in the run-up to complying with the new era of software supply chain security regulations, such as the 7900 bill that requires zero CVEs impact the security of the product. The contextual analysis feature also recommends solid, actionable, and cost-effective remediation that takes into account the specific attributes and configurations of the container. For the first time, developers won’t be asked to “simply fix everything” but will be provided with proof and priorities that are accurate. The ultimate approach is to apply the contextual analysis on both source code (via IDE) and binary analysis.
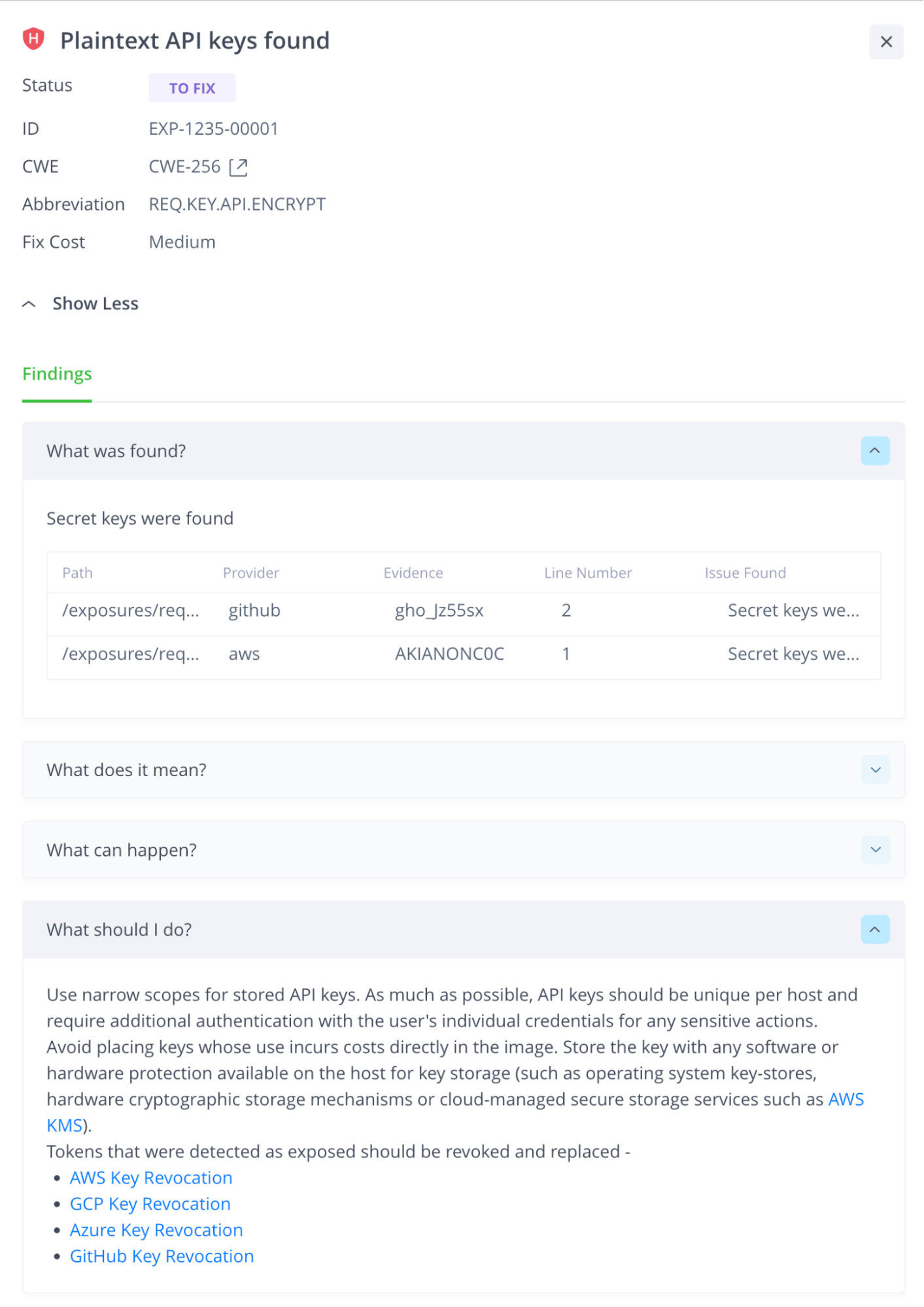
Clear up any unintentionally exposed credentials
Have you considered the safety of your keys and credentials stored in containers and other artifacts? Don’t let them be an easy target for malicious actors. With JFrog’s secrets detection, you can rest assured that your exposed credentials are traced and accounted for. Secrets detection searches for known structures and completely random credentials (using suspicious variable matching), ensuring that our detection engines generate minimal false positives. Don’t settle for subpar security measures – trust JFrog’s architecture to provide the utmost accuracy to identify exposed keys and credentials.
This feature not only identifies where your secrets are stored but also provides crucial information about the issue at hand – whether it’s being utilized or not. It’s not just about the specifics of the secret itself. Hard-coded secrets can pose a serious security threat, which is why our binary scanning capabilities are essential to provide a comprehensive solution to your secret detection needs.
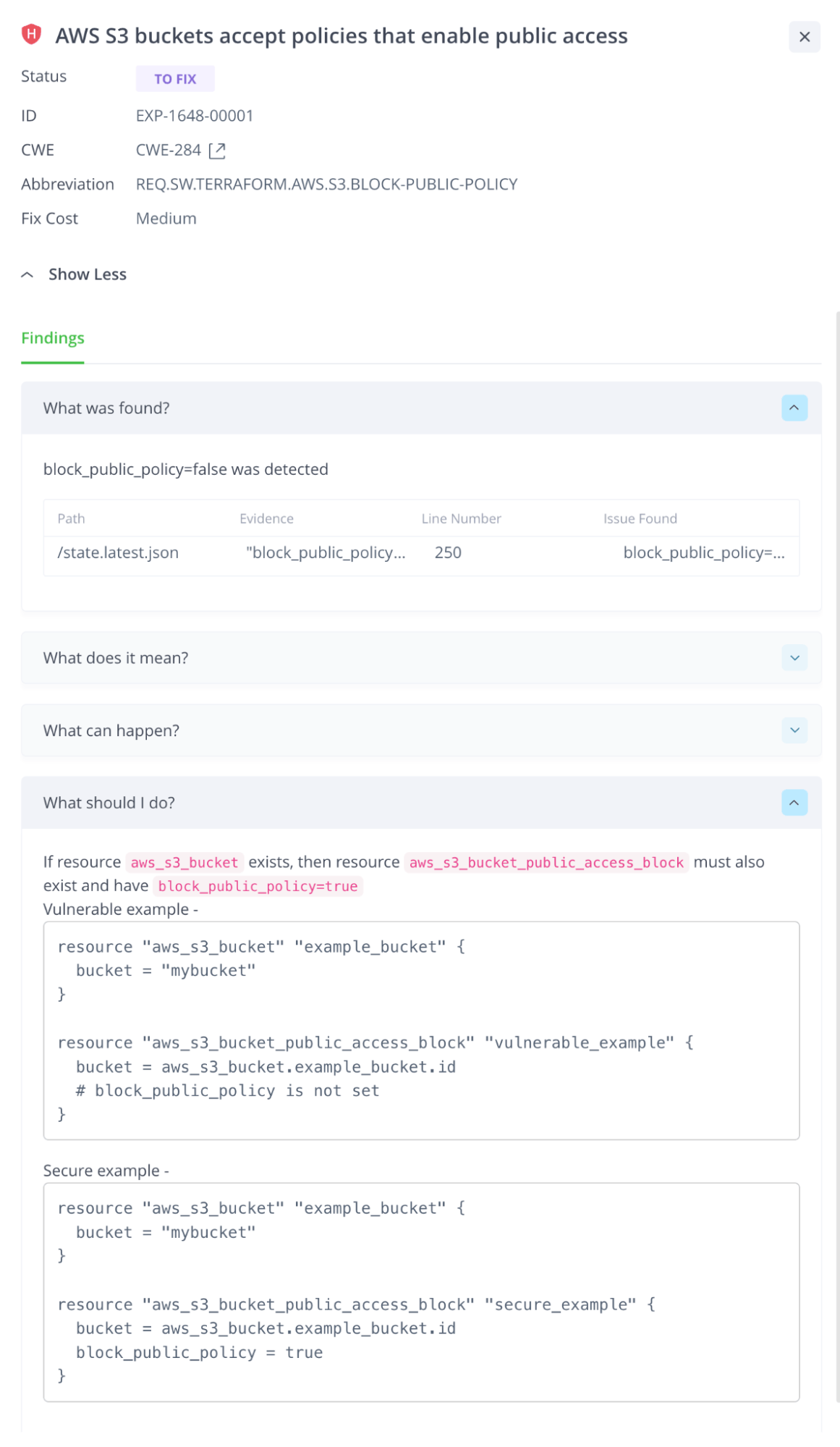
Secure your Infrastructure-as-Code (IaC) configurations
Are you concerned about the potential risks of misconfiguring your infrastructure and compromising your cloud deployment? With the rise of Infrastructure-as-Code (IaC) files, the likelihood of human error is higher than ever. But don’t worry – securing your IaC files is critical to keeping your cloud deployment safe and secure. JFrog’s IaC security scanner is a vital tool in protecting your infrastructure, with a particular focus on Terraform configuration files stored in JFrog Artifactory. And with our universality approach, you can expect even more IaC file types to be added in the future, providing even broader coverage for your security needs. This provides a comprehensive, proactive solution to your IaC security concerns.
Gain Confidence in The Use of Open-Source Libraries and Services
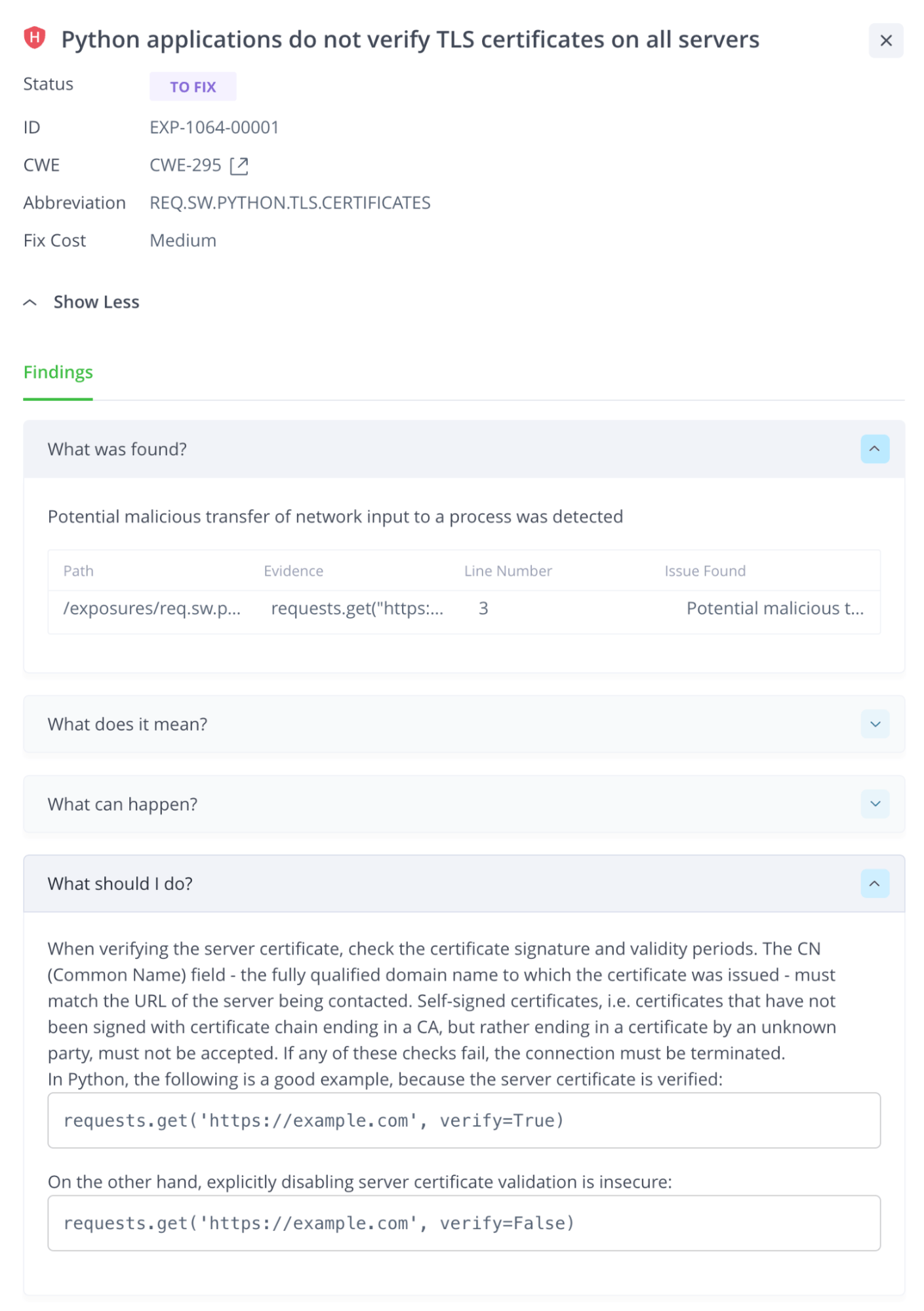
Are you worried that your open-source packages might be putting your applications at risk of attack? Traditional application security solutions often overlook this critical aspect, focusing solely on what packages are being used (as with SCA tools) instead of how they’re being used. But with JFrog’s cutting-edge security engines, we go beyond the surface level to scan the configuration and usage methods of common OSS libraries and services, such as Django, Flask, Apache, and Nginx. This means we can identify misuse and misconfigurations that could be leaving your software vulnerable to attack. And our scanners take into account the broader context of containers, providing a comprehensive and proactive solution to your application security concerns.
Summary
To effectively deliver this new layer of security, we first enhanced the JFrog Xray database to include the JFrog Security Research team’s proprietary data on CVEs and malicious packages – including granular remediation and mitigation instructions. We also made the JFrog Xray data on CVEs and licenses more reliable, enhancing JFrog Xray’s scalability and reducing the data-update latency significantly. An “operational risk” policy capability was also added to enable package blocking based on soft attributes such as the number of maintainers, maintenance cadence, and more.
Our unique platform approach to managing and securing the software supply chain brings unparalleled advantages to DevOps-based software development. This announcement solidifies the JFrog Software Supply Chain Platform as the only security solution built for today’s modern DevOps workflows – baked in. Binaries are the center of gravity in software development and a core competence of the JFrog Platform; scanning them in a contextual manner is the most advanced and streamlined find-and-fix path available today.
Learn about JFrogs’ advanced security features
Register for our JFrog Xray and Advanced Security Demo or a dedicated 1:1 session, where you can learn about the features and recent enhancements, dive deep into their advantages and explore a demo of the JFrog Platform.
The quickest and easiest way to try the advanced security features on your own is to start a cloud trial. Alternatively, if you want to try the advanced security features in a self-hosted trial or POC – then please contact us.