Unveiling Secrets Detection with JFrog Frogbot
Elevating DevOps Security
A leap forward in DevOps security
In today’s interconnected world, secrets are the keys to unlocking sensitive data and systems. Like hidden gems for attackers, any inadvertent exposure of these secrets could lead to data breaches, unauthorized access, and security compromises. As organizations adopt DevOps practices, artifacts containing secrets are often stored and shared across various stages of the software supply chain, amplifying the risk of exposure.
Secrets Detection with JFrog Frogbot delivers the proactive and holistic DevOps security today’s organizations require. It seamlessly integrates into the software supply chain, becoming a vital component of your DevOps workflow. Secrets Detection is just one outcome of JFrog’s commitment to providing end-to-end security solutions, ensuring that every stage of software development is fortified against potential vulnerabilities.
A glimpse into JFrog Frogbot
JFrog Frogbot is a Git bot that introduces a new level of security to your software development workflow. It’s designed to scan pull requests immediately after they’re opened, but before they’re merged. This preemptive approach allows Frogbot to detect more than 150 specific types of credentials before they become part of your codebase. By doing so, it empowers developers to fix issues proactively, and helps them improve their code so they can avoid the introduction of new vulnerabilities in the future. In addition, Frogbot scans the entire repository periodically, and creates pull requests with recommended fixes for vulnerabilities it detects.
Unveiling Secrets Detection with Frogbot
Imagine a solution that can proactively and automatically identify and alert you to potential security risks within your software artifacts. This is precisely what Secrets Detection with JFrog Frogbot does. Frogbot’s Secrets Detection is an automated security scanning mechanism that scours your source code for sensitive information, such as:
- Internal tokens
- Keys
- Credentials
- Expired certificates (i.e. SSL certificate, security certificate)
- Inclusion of plaintext API keys, private keys in code
How Secrets Detection works
JFrog Frogbot leverages advanced algorithms to meticulously analyze your source code, including configuration files and text files. It possesses a comprehensive database of over 900 specific types of keys and credentials. This database, coupled with Frogbot’s proprietary secrets matcher, ensures a high level of accuracy in detecting secrets.
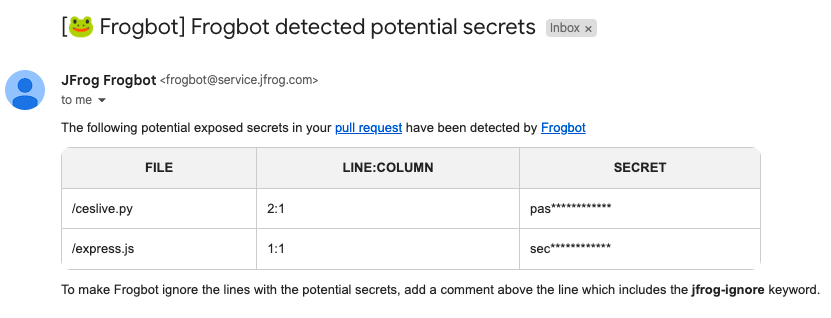
When Frogbot scans pull requests right after they are opened, it searches for secrets that have been inadvertently exposed within the code of the pull requests. If secrets are found, Frogbot promptly triggers an email notification to the user who pushed the corresponding commit. The email address utilized for this notification is sourced from the committer’s Git profile configuration. Frogbot offers the flexibility to direct the email notifications to an extra email address if desired.
The bigger picture: JFrog’s holistic security approach
In the ever-evolving landscape of software development, security remains a paramount concern. Developers and DevOps teams are on the front lines, defending against potential vulnerabilities that could compromise the integrity of their software supply chain. As these teams embrace automation to accelerate delivery, it’s imperative that security solutions evolve to keep pace.
In the age of rapid software delivery, security cannot be an afterthought. JFrog Frogbot’s Secrets Detection takes a proactive stance against potential vulnerabilities, safeguarding your software artifacts from data breaches. With Frogbot by your side, you can accelerate your DevOps journey without compromising security.
Secrets Detection is just one facet of JFrog’s commitment to DevOps security. Our solutions span the entire software supply chain, from code to containers to production. With features like Software Composition Analysis (SCA), Vulnerability Contextual Analysis of CVEs, Infrastructure-as-Code (IaC) security, and Static Application Security Testing (SAST), JFrog provides a comprehensive shield against a wide array of security threats.
Ready to explore the possibilities? Try out JFrog Frogbot now!