helping to deliver secure software updates from code to the edge.
You have been redirected to the JFrog website
JFrogとSnykとの徹底比較:
AppSecソリューション比較
ソースコードのスキャンだけに頼る手法には、重大なセキュリティ上の欠落が残ります。だからこそJFrogは、ビルドから配布、実行に至るまで、すべての成果物の安全を徹底して守り抜きます。JFrogは、コードからパッケージ、バイナリ、コンテナ、ランタイムイメージに至るまで、ネイティブかつフル機能のAppSecを提供します。これにより、チームは信頼性を一切妥協することなく、開発スピードを極限まで高めることが可能です

Frogの導入により、脆弱性そのものが大幅に減少しました。その結果、エンジニアは修正作業に追われることなく、本来のミッションである『新しいアプリケーションの開発』に、より多くの時間を割けるようになっていますさらに、すべての開発チームが同一のプラットフォーム上で活動することで、情報の集約とプロセスの一元管理が実現しました。これにより、組織全体の開発フローが劇的にスリム化されています

JFrog とSnyk、その決定的な違いを確かめる
JFrogとSnyk、どちらを選ぶべきか? その答えは、『バイナリ』と『スピード』の両立にあります
JFrog独自の強みを詳しく見る
JFrogは、世界中のセキュリティ、DevOps、そして開発の第一線で活躍するエキスパートたちに選ばれ続けている、包括的なソフトウェア・サプライチェーン・セキュリティ・プラットフォームです
ソースコード保護の、その先へ。―― それは、文字通り『次元の違う』保護を提供します
ソースコードのみに依存する手法とは異なり、JFrogは開発の最初の一行から、バイナリ、パッケージ、コンテナ、そして複雑な依存関係に至るまで、そのすべてを確実に保護しますリスクのある要素をSDLC(ソフトウェア開発ライフサイクル)に一切混入させない。JFrogは、業界標準を超えた最高水準のAppSecスキャンを提供するのはもちろん、自社開発のモデルや利用中のAIまでをも保護する、高度なAIセキュリティ機能を備えています。
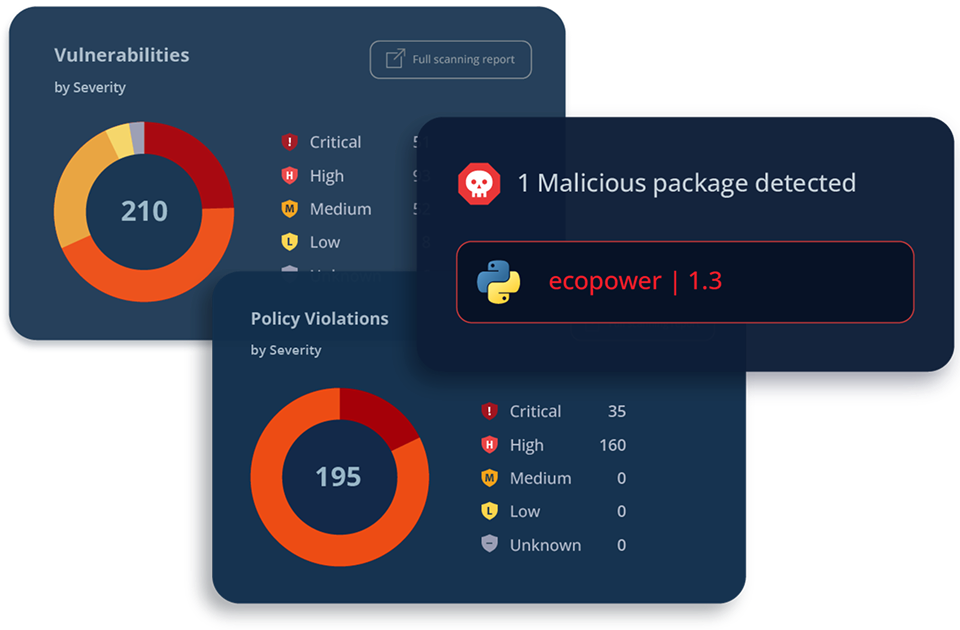
後付けのセキュリティではなく、パイプラインに深く『統合』されたAppSecを
JFrogのセキュリティソリューションは、ソフトウェア・サプライチェーン・プラットフォームに欠かすことのできない、中核的な構成要素として統合されていますArtifactoryが組織内のあらゆる成果物、AIモデル、コンテナなどの『真実の単一の源(信頼できる唯一の情報源)』として機能することで、JFrogのセキュリティは既存のDevOpsパイプラインやベストプラクティスへ、一切の滞りなくシームレスに融合します組織の縦割りや運用上の摩擦に、もう悩まされることはありません。
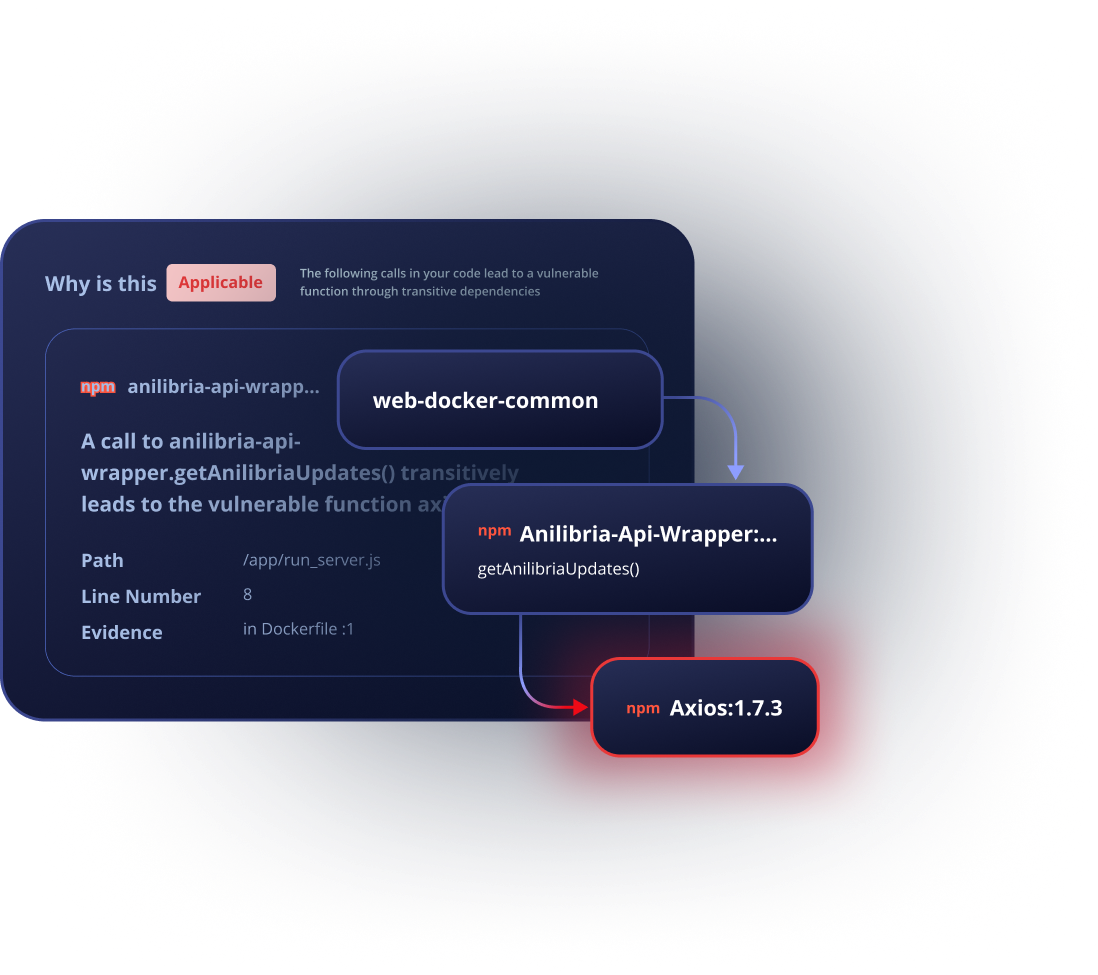
JFrogとSnykにおける脆弱性修復(リメディエーション)の比較
ソースコードの解析だけで脆弱性の優先順位を決める手法には限界があります。JFrogは、アプリケーションや成果物全体の状況(コンテキスト)を把握し、コード、バイナリ、コンテナイメージを網羅した『波及効果を含むコンテキスト解析』によって、真に修正すべきリスクを特定します対応すべき真のリスクを明確に浮き彫りにし、迅速な解決へと導く修復ガイドラインを提供します
開発からデプロイまでを網羅: JFrogが提供する一気通貫のAppSec保護
開発者向けに設計されたセキュリティ
コードから本番環境まで、ソフトウェアの全工程をセキュアに。JFrogのSAST、SCA、IaC、シークレットスキャン、そしてランタイムセキュリティが、ソースコードとバイナリの双方において、SDLC全体の確かなガバナンスと統制を実現します。
これらすべての高度なセキュリティを、開発者が愛用するツールやワークフローをそのまま活かしながら実現します
リスクの侵入をゼロへ。サプライチェーンの入り口から、鉄壁の守りを実現
悪意あるソフトウェアやリスクをSDLCの入り口で遮断。開発者が『検証済みの安全なコンポーネント』のみを使用してビルドできる環境を徹底します。パッケージ、AIモデル、IDE拡張機能にいたるまで。開発に必要なあらゆる要素をJFrogが精査(キュレート)し、安全なものだけを提供します
AppSecにおける『バイナリ』という決定的な違い]
バイナリをスキャンしましょう。バイナリこそが最終製品であり、真の攻撃対象領域(アタックサーフェス)を象徴する存在だからです。JFrogは、攻撃者の標的となるバイナリレベルのセキュリティリスクを解消し、アプリケーションに脆弱性が隠れる隙を与えません。
AI/MLセキュリティ
AI開発をセキュアに。AI活用をセキュアに。JFrogはAIモデルの管理と統制により、未承認のシャドーAIを可視化し、セキュリティカタログや高度なAI機能を提供することで、アプリケーションセキュリティの効率化と迅速化をサポートします。
専門リサーチチームの知見を活用したAppSec
JFrogのセキュリティリサーチチームはCVE番号発番機関(CNA)であり、脆弱性情報の標準化と公開において重要な役割を担っています。弊社のセキュリティ製品や革新的なテクノロジーは、膨大な技術検証とコミュニティを通じた徹底的なリサーチに基づいています。私たちは常に最新の脅威に目を光らせ、それらに対抗するための最適な技術進歩を追求し続けています。
世界をリードする企業が JFrog を採用する理由

私はAppSecの基本原則である「予防、検知、修復」を遵守しています。そして、JFrogが提供するソリューションを確認した際、それらがまさに私の求める要件をすべて満たしていると確信しました。]


5つも6つも異なるアプリケーションを使い分ける代わりに、本当に活用できるものは何かを見極めたいと考えていました。「これらすべてを単一のソリューションで完結させることはできないか」と考えていたのです。その課題を解決し、窮地を救ってくれたのがArtifactoryでした。結果として、それは私たちが必要なものすべてが揃う、ワンストップな解決策となりました。文字通り、私たちが必要としていたものがすべてが揃っていたのです。


JFrogを導入したことで、脆弱性は劇的に減少しました。その結果、エンジニアは新しいアプリケーションの開発という、本来集中すべき業務に、より多くの時間を割けるようになっています。異なる開発チームがすべて同一のプラットフォームを利用することで、プロセスの集約と効率化が実現しました。


Artifactoryへの移行以来、メンテナンスの負担を大幅に削減できています。その結果、私たちは次のステップへ進み、より深化を遂げたDevOps組織へと進化することができました。


以前は、新しいAIモデルを届けるまでに数週間を要していました……。今では、リサーチチームが独立して迅速にデプロイできるようになったため、エンジニアリング部門やプロダクト部門との連携も円滑になり、組織全体の満足度が向上しました。わずか4週間のうちに、5つもの新しいモデルを本番環境で稼働させることができたのです。


ビジネスが成長を遂げる中で、JFrog Connectはオペレーションの質をより高めるための大きな力となりました。一度に多数のデバイスを対象としたアップデートの自動実行が可能になり、リリースのたびに発生していた工数とコストを最小限に抑えることができました。エンジニアの人的コストに照らし合わせれば、これこそが選ぶべき明快な答えだったのです。







