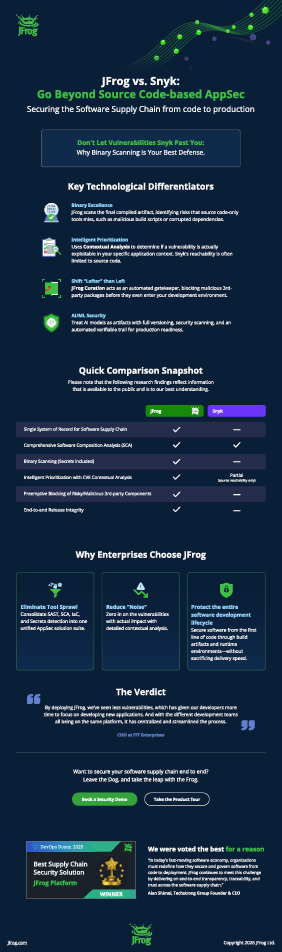
JFrog vs. Snyk: Go Beyond Source Code-based AppSec
Securing the Software Supply Chain from code to production.
The Visibility Gap
Relying solely on source code security (SAST/SCA) creates a dangerous blind spot as software moves toward production. Once code is compiled into binaries and containers, traditional tools lose the context needed to determine if a vulnerability is actually reachable or exploitable.
The Solution: Binary-First Security
This infographic compares JFrog and Snyk, highlighting why a Binary-First approach is essential for 100% software integrity. By securing the actual building blocks of your applications—the binaries—JFrog provides a continuous line of defense from the IDE to the edge.
Key Comparison Points:
- Contextual Analysis: Reduce developer “noise” and false positives by up to 80%.
- Platform Integration: Security is natively built into the world’s leading artifact repository.
- Full Supply Chain Coverage: Integrated protection for Secrets, IaC, and AI/ML models.
- Operational ROI: Consolidate your toolchain to eliminate sprawl and administrative overhead.
Bottom Line: Don’t just scan code—secure your software.
Discover why a binary-centric platform is the only way to achieve proactive DevGovOps without sacrificing release velocity.
Or click on the image to download the infographic.