Contextual Analysis for Python, Java, and JavaScript Projects with JFrog Frogbot
When scanning packages, CVE (Common Vulnerabilities and Exposures) scanners can find thousands of vulnerabilities. This leaves developers with the painstaking task of sifting through long lists of vulnerabilities to identify the relevance of each, only to find that many vulnerabilities don’t affect their artifacts at all.
Vulnerability Contextual Analysis uses the artifact context to eliminate false positive reports on vulnerabilities that aren’t applicable, significantly reducing the noise caused by irrelevant alerts and allowing developers to concentrate on addressing the most critical vulnerabilities.
In this article, we’ll focus specifically on the advantages of leveraging Frogbot’s Vulnerabilities Contextual Analysis for Python, Java, and JavaScript projects.
What is JFrog Frogbot?
JFrog Frogbot is a Git bot that scans your Git repositories for security vulnerabilities. Frogbot executes this in two primary ways:
- Scan Repository: Periodically examines chosen branches within the Git repository and generates pull requests containing fixes for identified vulnerabilities.
- Scan Pull Request: Scans open pull requests before they are merged to ensure that no new vulnerabilities have been introduced into the source code.
Combining these two capabilities helps to guarantee the security of your Git Repository. This involves regular scans of your current dependencies to identify recently uncovered vulnerabilities, while preventing the inclusion of any recognized vulnerabilities into your code during the development process.
Vulnerability Contextual Analysis in Frogbot leverages the code context uncovered by these scans to eliminate false positive CVE reports, providing developers with relevant, precise, and actionable vulnerability information.
How Vulnerabilities Contextual Analysis works
With Frogbot’s Vulnerabilities Contextual Analysis, developers receive accurate vulnerability reports tailored to their Python, Java, and JavaScript projects. Here’s how that works: When Frogbot scans your source code, it adds the Contextual Analysis results for each CVE it reports.
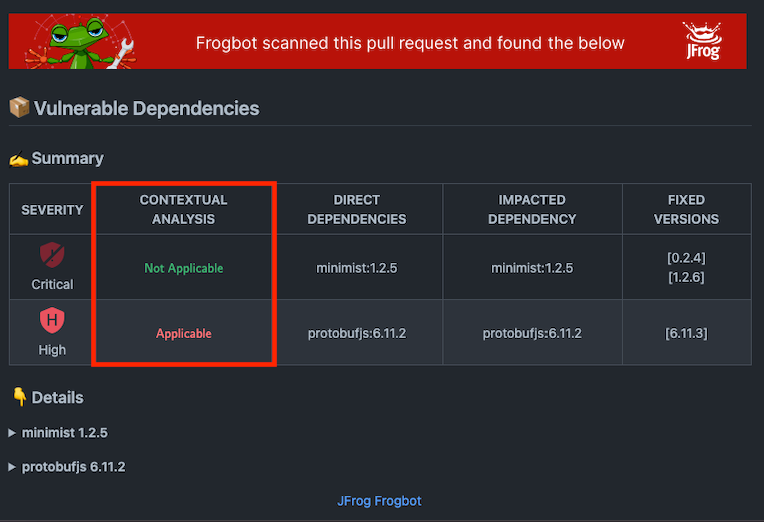
In the screenshot below, you can see that two CVEs were found. The findings indicate that the CVE with “Critical” severity isn’t applicable to the code of the pull request, and can therefore be prioritized after the “High” severity CVE, which was marked as applicable.
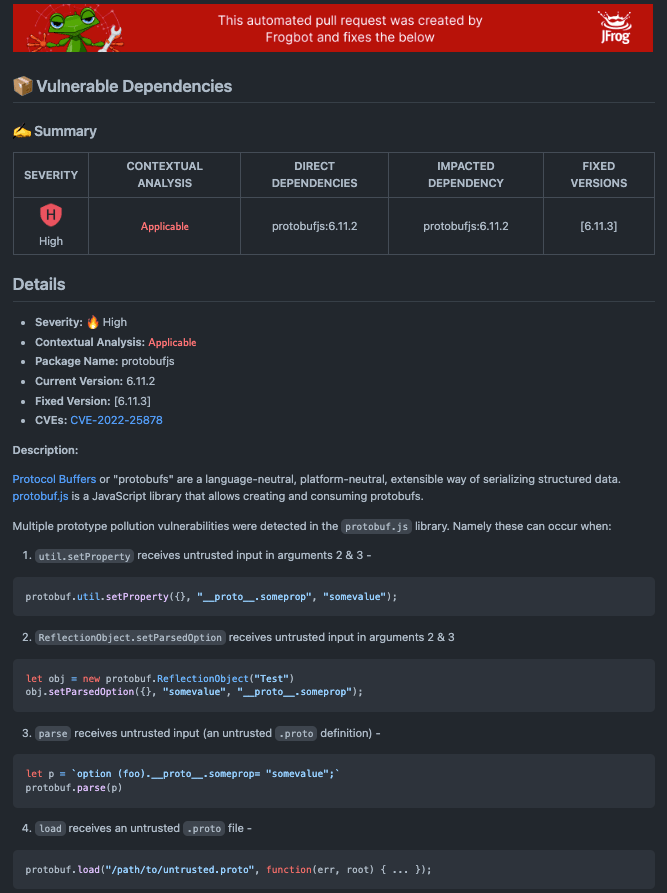
Every identified vulnerable dependency comes equipped with details regarding its discovery. This includes metadata about the CVE and even snippets of code for reference.
Advantages of JFrog Frogbot’s Vulnerability Contextual Analysis
There are multiple advantages of applying Frogbot’s Vulnerability Contextual Analysis when working in Python, Java, and JavaScript.
Efficiency and speed
By eliminating false positive reports, developers save valuable time and effort. Instead of sifting through long lists of vulnerabilities that may not affect their artifacts, developers can focus on addressing genuine security risks. This streamlined approach to vulnerability management enhances development efficiency, enabling teams to allocate resources effectively and deliver secure code faster.
Increased visibility
The Vulnerabilities Contextual Analysis feature in Frogbot enables developers to understand the impact and exploitability of vulnerabilities within the context of their artifacts. By testing vulnerabilities as an attacker would, developers gain insight into the likelihood of a vulnerability becoming an exploit, and can prioritize remediation efforts accordingly. This targeted approach allows developers to confidently use severity scores to ensure that high-risk vulnerabilities are addressed promptly, minimizing the risk of security breaches.
Best-in-class vulnerabilities database
JFrog continuously updates its vulnerabilities database, incorporating new component vulnerability from multiple leading sources including the NVD, GitHub, Ubuntu, Debian, Red Hat, PHP, and vulnerability data uncovered by the JFrog Security Research Team.
Improve your development efficiency by focusing on fixing what’s actually important. Try JFrog Frogbot now!