See Where Containers Travel with Portshift and Artifactory
Please welcome our technology partner Portshift, with this informative article that has also been posted on the Portshift company website.
DevOps engineers often struggle with making their complete pipeline for Docker containers fully visible and traceable. Even after they succeed in mapping and controlling the CI/CD pipeline, there remains a gap between the pipeline and the container runtime environment. By integrating JFrog Artifactory with the Portshift platform, DevOps engineers can gain visibility and control over your CI/CD artifacts, directly from Artifactory’s Docker repository, in runtime.
JFrog Artifactory makes the CI/CD pipeline visible and traceable by storing information from build tools that enable control of how those builds are deployed. But this control and visibility don’t extend to runtime, without the ability to monitor which Docker repository containers are running in production, where, and how. The integration with Portshift empowers DevOps engineers to see, track and monitor the Docker images deployed from Artifactory, while they are running in production.
How Portshift and Artifactory Can Work Together
Here’s how Portshift’s Artifactory integration can be of use:
- Compliance – The ability to prove and track where artifacts are running, compared to what was planned, and to satisfy regulatory demands.
- Artifacts cleanup – Artifact repositories, especially when using Docker images, can quickly grow to unmanageable scale. With the Portshift-Artifactory integration, DevOps managers can easily discover which artifacts are not in use and can be deleted.
Runtime Containers Visibility
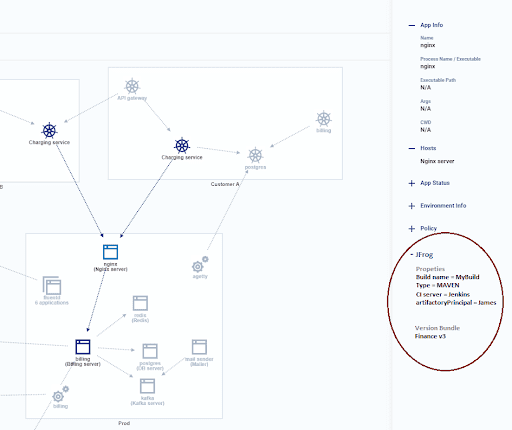
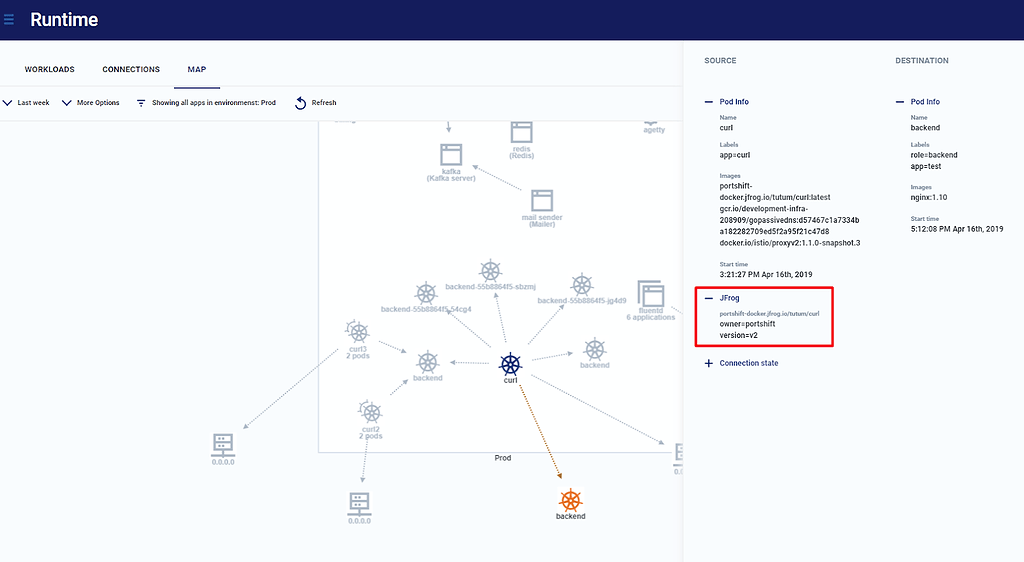
Portshift is an identity-based workload protection platform that generates signed identities for your application during CI/CD, and controls them at runtime. By tracking the signed identities Portshift can draw a runtime map of your application containers, throughout your cloud infrastructure.
When Portshift is integrated with JFrog Artifactory, Portshift signs the identities, based on artifacts that are stored in the Artifactory database, and extends the Artifactory key information to the runtime. Information such as build, bundle, CI server, and more, will be visible in runtime as part of your realtime runtime application map.
Feedback to CI/CD Pipeline
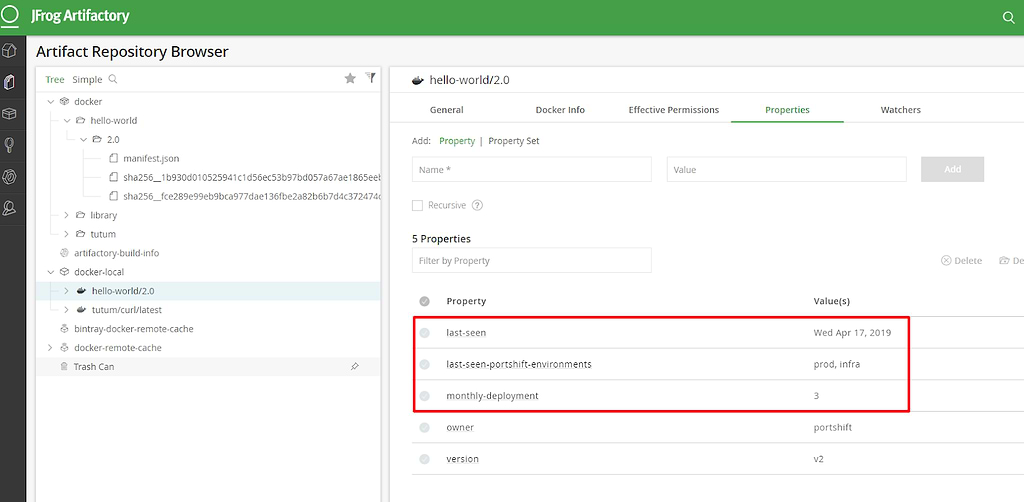
Once the integration is installed, Portshift reports information about runtime execution back to Artifactory, providing your CI/CD pipeline with a record of each Docker image’s usage. In the Properties display of the Artifactory console, you can view information about each artifact’s use in runtime, such as monthly deployment, environments in which it is being used, when it was last seen in runtime, and more.
Portshift provides Artifactory with details about the image’s runtime use too, such as the number of hosts, VPC, Region, Account, CSP, and more.
With this greater visibility into how your Docker images are being accessed, it’s simple to identify the ones that aren’t being used, speeding decisions that might otherwise take weeks of a bureaucratic process.
Installing the Integration
The Jfrog-Portshift integration currently supports all types of K8s clusters (including managed services such as EKS or GKE). This guide will walk you through the integration process.
Prerequisites
These are the things you will need before you start:
- An Artifactory account.
- A Portshift Console account.
- Portshift deployed on the K8s cluster (see tutorial). In order to make the most out of the integration, we recommend this cluster be integrated with Helm as well (see tutorial). Using the Helm integration you can automatically generate Portshift Identities based on Helm charts. Using the plugin, Helm will notify Portshift before each deployment which artifacts from Artifactory are about to be deployed. Portshift will then automatically upload all relevant artifacts to the Portshift platform and will generate signed identities for them.
Connect Portshift Platform to Artifactory
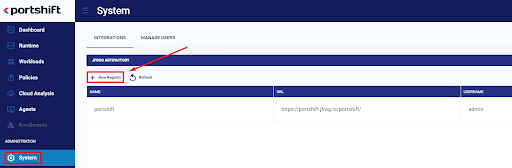
In your Portshift account, navigate to System > Integrations, and under JFrog Artifactory select New Registry.
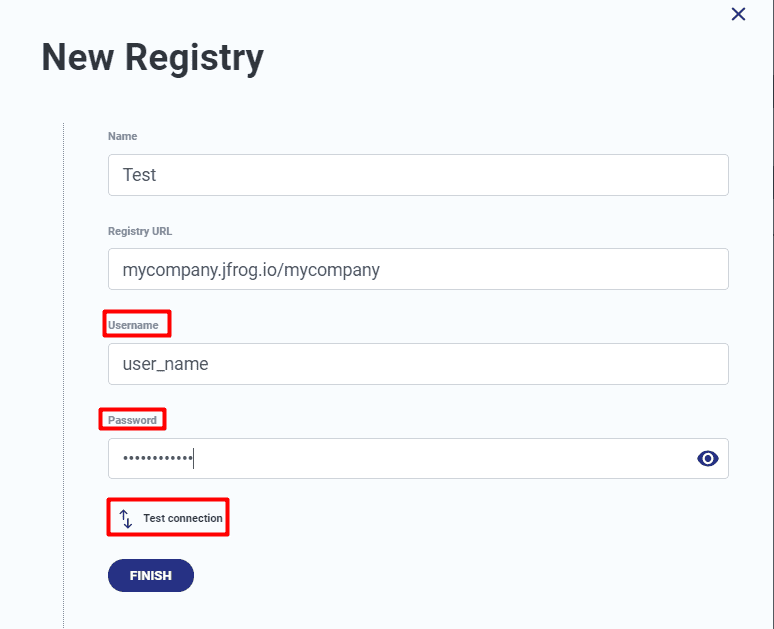
Now, just specify a name on Portshift for your existing Artifactory registry, enter its URL and login details, using your Artifactory credentials. Passwords are stored in a dedicated vault server (Hashicorp Vault), so accessing your Portshift account will not jeopardize your Artifactory credentials. To test everything is set right, click Test Connection. If you have additional Artifactory accounts you would like to connect, repeat these steps for them.
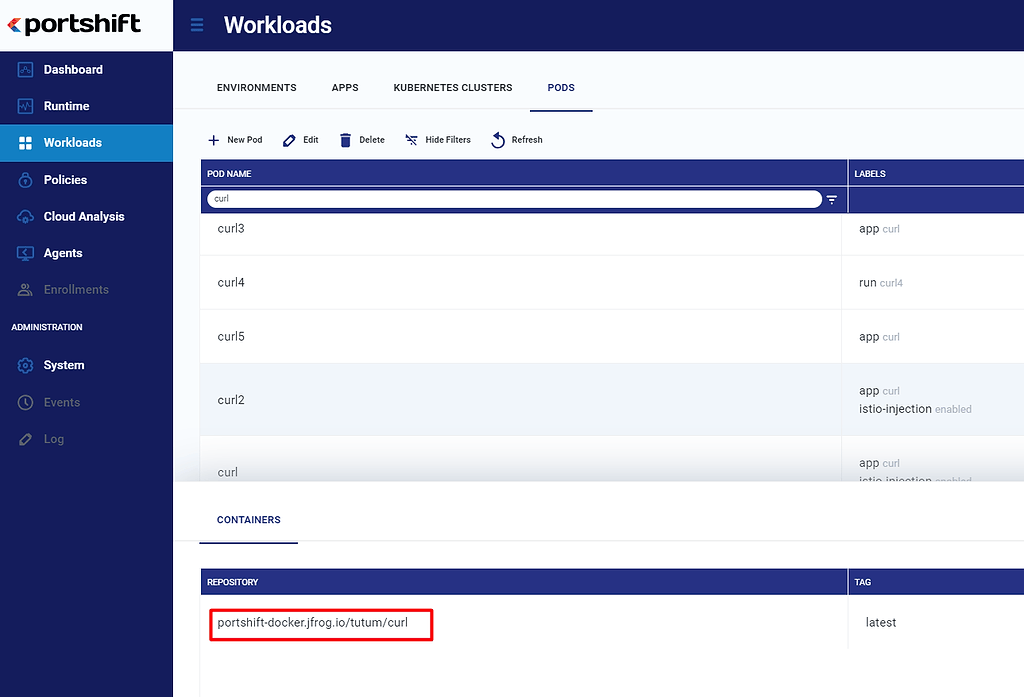
After your account is connected, any containers in your environment that originated in Artifactory will appear in the Workloads screen and in the Runtime view, with the relevant JFrog attributes.
For security, Portshift will immediately detect any artifact running in your environment that didn’t originate from your artifacts database. Establishing compliance with what is actually running out there, and where, is now a simple query. Sensitive artifacts can be tagged during the CI/CD phase, and Portshift will enforce the environments in which they can run, based on the information received from the artifact database.
Conclusion
Artifactory and Portshift are independent products that, together, can close the DevOps gap between CI/CD planning and runtime. This integration will enhance both the velocity of day-to-day operations tasks and will improve the security of your DevOps pipeline. Knowing exactly where and when containers are being used, together with the ability to detect any unauthorized artifact in runtime, will add a new layer of control that is essential for every cloud environment in scale.