DevOps-Centric Security is Finally Here | Announcing JFrog Advanced Security
The world’s first security solution designed with modern DevOps workflows in mind
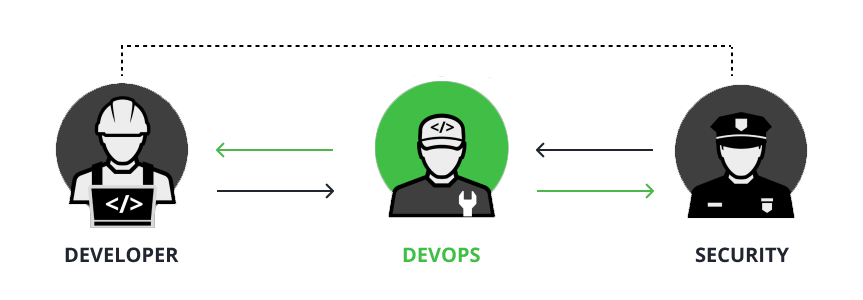
Today marks an exciting day for JFrog and a substantial step forward towards ensuring end-to-end software supply chain security. JFrog Advanced Security is our unique approach for DevOps-centric security, and the only solution that was built especially for today’s modern DevOps workflows.
Developers and the DevOps infrastructure are now the attack vector for today’s hackers and bad actors. The myriad tools and processes, not to mention the huge amounts of open source libraries and binaries, all introduce opportunities for accidental and nefarious injection of risk across the software supply chain. As owners of the software supply chain (SSC), DevOps teams have become de-facto “security owners” in organizations. At the same time, security teams are trying to balance multiple tools, configurations, reports and more (that all require development team resources), as well as being held responsible for compliance and business requirements.
Currently, no solution adequately bridges these groups or delivers unified data and insights, effectively making security teams taskmasters for development organizations, who are being overrun with requests, processes and regulations that are not their core competency. Further, teams are often hampered with myriad point solutions that require integration in technology, reporting and aggregation, and of course manual analysis and assessment, as well as providing disparate context and remediation advice that is not centralized.
We need a different, holistic approach for a new era of software supply chain security threats.
Security for DevOps
JFrog is the pioneer of end-to-end binary management, the core technology behind its Liquid Software vision. Continuing to advance through a natural (yet substantial) evolution towards the full enablement of software management from development to production, security became a critical component and key enabler as part of this evolution.
There are many key factors that have enabled this evolution, including:
- JFrog’s unique position as the bridge between developers, production, and security personas, and as the platform that in its core enables governing and controlling the supply chain.
- The slew of recent security mega-events such as Log4Shell, Spring4Shell, SolarWinds, etc. increasing the need for security throughout the entire software supply chain, and not just from a shift-left security approach that’s focused on source code analysis.
- New security requirements and regulations that are being drafted almost weekly, which impact enterprises and government organizations alike, including the Presidential order from May 2021, the recent H.R. 7900 bill, and White House Office of Management and Budget (OMB) memorandum on enhancing Software Supply Chain security through secure software development practices. Even more recently, we see fresh software supply chain guidance from the United Kingdom’s National Cyber Security Centre and additional initiative from the European Union.
Above all, JFrog’s unique, binary-level approach provides a level of insight beyond source code, which brings true understanding of the real vs the alleged security risks within your software.
Security from a single source of truth
Millions of developers and thousands of companies worldwide, including a majority of the Fortune 100, already depend on JFrog solutions to securely manage their mission-critical software supply chain. The JFrog Platform is their centralized, single source of truth for managing their critical software assets: their binaries. Security vendors who want to provide true end-to-end security solutions are completely dependent upon access to these assets. After all, there is no shifting left or shifting right without controlling the middle.
The “shift left” approach is not enough
Source code players (such as SCA tools and typical AST – SAST, DAST, fuzzer, etc.) understand that source code analysis is not enough to truly analyze context. Contextual understanding can only be achieved by looking at the software binary, which contains much more information than code alone. Containers, archives, even simple EPM files all deliver a picture of the software’s journey. Since the binary is the ultimate asset being delivered to customers, it is of course what is being targeted by today’s attackers. Without this critical information, it is impossible to deliver contextual understanding to determine risk. Identified issues can’t be identified, remediated, mitigated or fixed across the board in an efficient, prioritized manner when the focus is only on the developer’s IDE. Security needs to be handled holistically from code, to compiled code, to images, builds, releases and then run time in order to be comprehensive.
Shifting right for run-time security is not enough
Enterprise-security solutions that are focused on runtime and production (such as cloud security and container security) are moving a little bit to the left, but not as far as source pure-players. They do it to the extent they need to, in order to feed back the findings from production to the developers through DevOps processes.
Visibility into source as well as the binary is the requirement of a supply chain solution. If a product cannot see into the center of the supply chain at the binary level as well to deliver visibility from the inside-out, it will not and cannot deliver comprehensive security.
With the Vdoo acquisition, JFrog dramatically accelerated its security journey to build and offer security solutions purpose-designed for DevOps. The binary-analysis capabilities brought by Vdoo – coupled with the centralized “source of truth” that JFrog Platform provides for DevOps – enables true end-to-end security and control. It allows a consolidated and effective experience that dramatically reduces overhead for developers, DevOps engineers and security leaders.
Throughout the last year, JFrog Xray and Xray databases were enhanced and improved upon significantly, transforming Xray into an enterprise-grade, leading product that covers both shift-left via IDE use cases and deep, binary-level analysis. Today, with the launch of JFrog Advanced Security, JFrog’s security offering has made a tremendous leap forward, becoming a holistic security solution, designed to be infused into your DevOps workflow. JFrog Advanced Security – which augments Xray with many more innovative capabilities – addresses modern supply chain threats, working alongside JFrog Artifactory as a single source of control for your binaries, all in a single platform.
Introducing JFrog Advanced Security
JFrog Advanced Security augments Xray with many new capabilities, all connected to supply chain threats. In order to deliver this new layer of security, we first enhanced JFrog Xray substantially to include the JFrog Security Research team’s proprietary data on CVEs and malicious packages, as well as granular remediation and mitigations instructions that were added to the CVE articles in the database. Notable resources were put on making JFrog Xray data on CVEs and licenses more reliable, enhancing JFrog Xray’s scalability and reducing the data-update-latency significantly. An “operational risk” policy capability was also added to decide on package-blocking based on soft attributes such as number of maintainers, maintenance cadence and more.
The core technology approach of JFrog Xray is based on efficient and accurate indexing of package metadata. JFrog Advanced Security adds a new approach of in-depth binary scanning to look into data that is not accessible via package managers, SBOM or typical metadata. Therefore, it allows a whole new understanding of the security state of the analyzed binaries, especially when it comes to containers. The designated scanners allow the identification of security issues that in most of the cases cannot be found via source code analysis. Using such in-depth scanning will enable, for the first time, a comprehensive understanding of the security issues in a contextual manner – not only identifying the issues that are blind spots to others, but also understanding their potential impact in production. This is thanks to their wider view of the software, when compared to source code analysis alone.
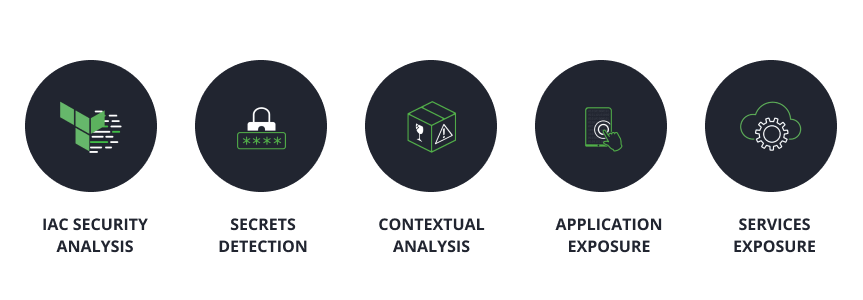
New capabilities now available as part of JFrog Advanced Security:
1. Container contextual analysis of CVEs
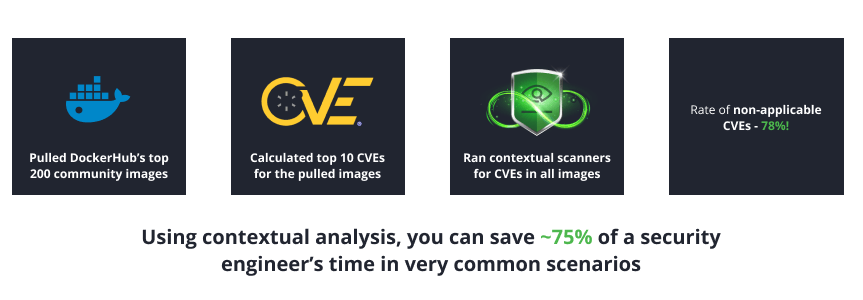
One of the most common inputs we gathered from developers on SCA tools is that they generate far too many results, requiring them to fix many vulnerabilities that do not, in reality, impose any risks. We also learned that these results are being inefficiently or incorrectly prioritized because of lack of context. Traditional CVSS scoring methods create even more complications, as they don’t take into account specific configurations, security mechanisms and other attributes of the analyzed software.
JFrog Advanced Security introduces a first-of-its-kind capability for containers: examining the applicability of identified CVEs when revealed, by deeply analyzing the container and its specific contents and attributes. For example, it will check if the first party code calls the vulnerable function in the vulnerable package, associated with the specific CVE. It will also scan for additional configurations and file attributes to tell if the prerequisites for exploitation of the CVE are met. In the era of new supply chain security regulations, such as the 7900 bill that requires 0 CVEs that impact the security of the product or alternatives for mitigations, contextual analysis becomes the only way not to impact delivery time and ensure security of the software product. Contextual analysis also recommends concrete, actionable and cost-effective remediation steps that take into account the specific attributes and configurations of the container and recommend cost-effective mitigations. For the first time, developers won’t be asked to “simply fix everything” but will be provided with proof and priorities that are accurate and contain instructions on how to fix the issues with minimal effort. Applying the contextual analysis on both source code (via IDE) and binary analysis via JFrog Advanced Security is the ultimate approach that will lead to secure software – with minimal effort and retrospective fixes. Binaries are the center of gravity in software development and a core competence of the JFrog Platform; scanning them contextually is the most advanced and streamlined scan-and-fix path that can be offered today.
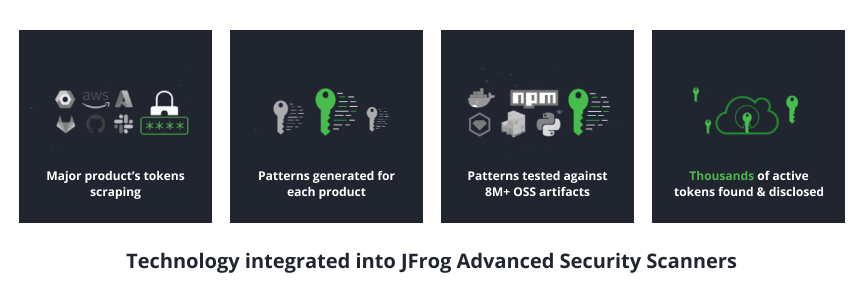
2. Exposed secrets
Commonly enough, keys and credentials are being kept in containers and other forms of artifacts. They can appear as tokens and key files, sometimes hardcoded in the binary (which is clearly a malpractice) and sometimes in configurations and other text files. JFrog Advanced Security’s Secrets Detection can trace secrets that exist in any containers stored in JFrog Artifactory. Unlike other scanners that generate high amounts of false positives due to wrong heuristic approaches, our engines look for 900+ specific types of keys and credentials and therefore are very accurate. In addition, the scanner results will not only point out where the secret resided but also will explain the problem, which may be how the secret is being utilized and not necessarily about its specific attributes (such as encryption, encoding, etc.). As secrets many times do not reside in source code, scanning for them in the binary form becomes essential. By identifying those secrets and fixing them in accordance with the systems’ instructions, any accidental leak of internal tokens, keys or credentials can be prevented or traced.
3. Insecure use of libraries and services
One of the most common issues that are traditionally ignored by existing application security solutions (and are relatively easy for attackers to utilize) are issues related to how packages are being used and not only what is being used (which is the common practice of SCA tools). Cutting edge security engines will scan the configuration and way of usage of common OSS libraries (such as Django and Flask) and services (such as Apache and Nginx) and will identify misuse or misconfigurations that expose the software product to attack. The scanners take in account a wider context of containers and will suggest actionable steps that deliver the fastest path to remediation.
4. Infrastructure-as-Code (IaC)
As more and more organizations and their developers adopt IaC, there is increased risk of infrastructure being misconfigured and becoming the weak link in the chain. Therefore, making sure that IaC is properly secured becomes critical. In its first edition, the IaC security scanner focuses on Terraform configuration files that are stored in JFrog Artifactory for early detection of cloud and infrastructure misconfigurations that can be exploitable. To comply with JFrog’s universality approach, more IaC types will soon be added to enable full coverage.
New JFrog Xray capabilities include:
- Enhanced CVE data and severity assessment:
Be the first to understand critical CVEs and create additional vulnerability insights to enable developers, DevOps, and security teams to deeply understand issues across OSS and commercial environments. Driven by a dedicated security research team’s manual, proactive analysis & enhanced severity assessments. - Enhanced CVE remediation data:
Drive mitigation strategies with enhanced remediation data for critical CVEs, enabling developers, DevOps, and security teams to understand more about how to intelligently mitigate vulnerabilities, often with just configuration changes. Provides easy to follow, step-by-step instructions. - Malicious package detection:
Discover and eliminate unwanted or unexpected packages, using JFrog’s unique database of identified malicious packages. The database is sourced with thousands of packages identified by our research team in common repositories alongside continuously-aggregated malicious package information from global sources. Learn more about how we identify such packages automatically. - Operational risk policies:
Enable easy handling of risks like package maintenance issues & technical debt. - Developer-oriented features:
Integrate directly into the most popular IDEs, Docker Desktop, vulnerability scanning via CLI, and a Frogbot scanner for discovering vulnerabilities upon pull requests in git repositories. - Security-oriented features:
Make compliance a breeze with SBOMs out of the box, including industry-standard exports and new security UI screens that aggregate issues across all repositories to ensure comprehensive coverage.
Summary
JFrog Xray together with the new JFrog Advanced Security features form the world’s first DevOps-centric security solution designed to control and protect the software supply chain from code to containers to production. We bring advanced binary security analysis into the DevOps workflow, uniting Developers, DevOps, and Security teams and delivering unrivaled vulnerability and risk detection into a unified DevOps and security platform.
We alleviate today’s security and development teams’ stress levels and workloads by providing a cutting-edge security solution with industry-leading security research at their fingertips. The elimination of false positives and offering easy-to-implement fixes, saves them time and effort, speeding up the software development process. The incorporation of contextual analysis gives a holistic picture of possible threats, delivering on the promise of continuous security. We invite you to give it a test drive for yourself and see the Advanced Security difference.
Want to learn about JFrog Advanced Security?
Register to our JFrog Xray and Advanced Security Demo each month where we’ll talk about the recent enhancements, dive deep into their advantages, and explore a demo of the JFrog Platform and the Advanced Security features.
START FREE TRIAL