Advanced Security in your Software Supply Chain – Part 1
Spend more time innovating and less time remediating with JFrog's Container Contextual Analysis
Containerised deployment is widely becoming a standard in every industry, ensuring these containers are protected at every level with a high level of accuracy is one of the most important tasks. Some industry vendors rely solely on the manifest files to provide them with a list of components, others have to manually convert the container image to a TAR archive before scanning, and even then they may only work on the application layer instead of evaluating the entire filesystem. All these methods make CI/CD development less automated, disjointed and more time consuming, costing more money and increasing release times.
With the newly released JFrog Advanced Security, the right way to ensure your applications are secure has never been easier. Unlike most solutions currently available, JFrog’s Advanced Security capabilities cover much more of the attack surface of the software supply chain, from looking for exposed secrets in your proprietary code, Infrastructure as Code (IaC) security misconfigurations, application and service exposures, to vulnerabilities in all layers of your container images.
JFrog’s Security Research team invests their time and expertise to continually improve the effectiveness and applicability of the scanners that power our Advanced Security contextual analysis capability. This research furthers the scope of findings, enabling development teams to focus on the CVEs that matter to each specific application. This minimizes time spent remediating false positives, and adds a new dimension to container security.
JFrog Xray’s advanced security features ensure you have 100% visibility into the entire container image during your fully automated CI/CD processes, as well as providing scan results in a contextual way, so you know exactly where you stand and where you need to focus. JFrog’s contextual analysis capabilities have shown that 78% of reported CVEs on top DockerHub images are not really exploitable. Imagine the impact on your release schedules with that kind of time saving on vulnerability remediation.
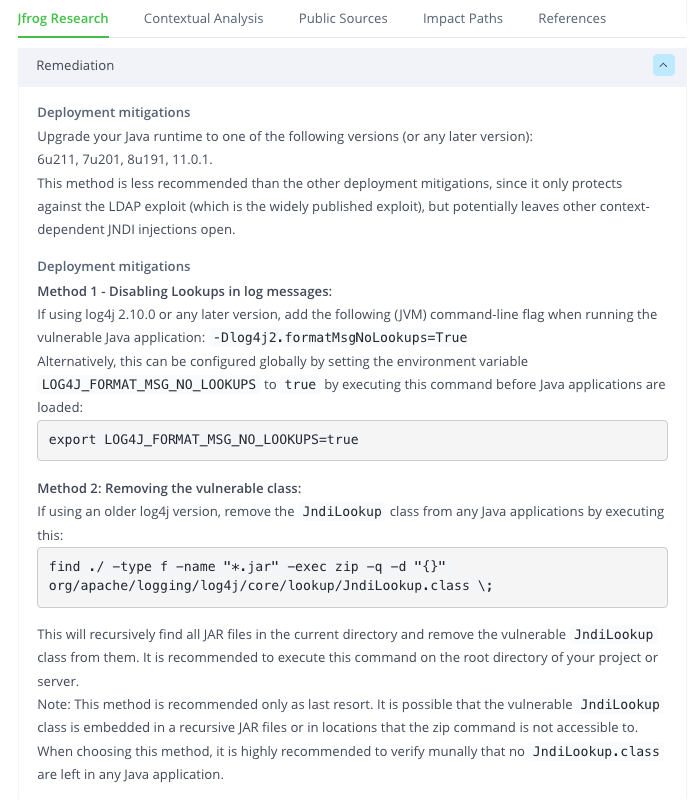
When you do have CVEs to remediate, your developers, DevOps and security teams will benefit from the industry leading expertise of the JFrog Security Research team. The researchers spend their days analyzing novel attack methods and remediation options for the most common, highest severity CVEs. They offer detailed explanations of the CVE, what it means and how it can affect your application, with more context and solutions than standard vulnerability databases. They often find “simple to implement” configuration or code fixes that enable developers to self-serve their remediation tasks quickly and efficiently. This speeds up development and CI/CD processes, accelerating your releases and increasing your level of trust.
This ensures you have the most up to date comprehensive information at your fingertips, allowing you to focus on the most important issues with the capability of finding the best resources invested in fixing them.
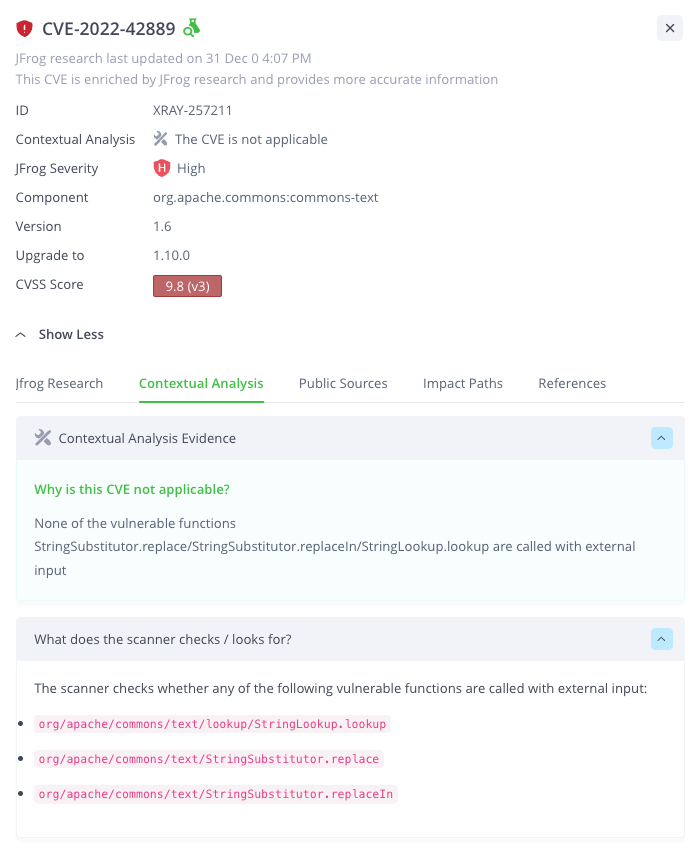
JFrog Xray’s contextual analysis feature delivers a more accurate picture of what vulnerabilities exist within all layers of your container image, if they are relevant, and/or easily exploitable – enabling developers and DevSecOps teams to prioritize efforts and resources for swift remediation. This way development teams can spend more time innovating and less time remediating.
So how does JFrog Contextual Analysis really work?
As soon as your container image has been built and stored in JFrog Artifactory, JFrog Xray goes to work identifying Open Source Software (OSS) components and the vulnerabilities associated with them. Identification and assessment of relevant contextual factors that affect the CVE’s applicability are applied to produce an accurate threat analysis of your application, removing the need for manual research to identify what can really be exploited.
Contextual analysis will look at a number of factors when executing:
- Reachability paths – Do the required function calls and arguments exist in the right path for the vulnerability to be exploited?
- Configuration relevancy – Has your application been configured in such a way that if the vulnerability exists it can actually be exploited?
- Compilation flags – During the compilation of your application, the compilation flags themselves can control whether or not a vulnerability can be exploited.
The combination of all these factors indicates whether the CVE is applicable with the contextual reasoning. Correlating this with the enhanced CVE research efforts of the JFrog security research team, will significantly reduce the level of time and effort required to ensure your application is secure.
This puts time back in the hands of your Development, DevOps and Security teams saving you money, speeding up development and gives you trust and confidence in your production releases.