You have Docker; Now are your Docker images secure?
This is the second blog in our series on Docker. In our initial blog called You have Docker; Now what?, we discussed the reasons for using a universal binary repository when implementing Docker to production with confidence.
It’s great that you’re using Docker, but managing security vulnerabilities is vital to ensuring your Docker environment is free of malicious artifacts. This is crucial mainly when downloading binaries from a 3rd party vendor as you need to be sure to actively block any vulnerabilities from ending up in your Docker Image.
In this blog post, we will review the four main four security challenges when working with Docker and how using JFrog Artifactory as your binary repository can help you mitigate these security risks in your Docker environment.
Challenge 1: Managing loads of binaries across multiple layers
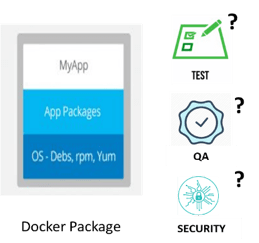
Docker images are not empty as they contain multiple binaries (such as OS packages and applications). In an ideal world, you want to ensure that all the binaries added to the Docker image have been tested, passed QA and have undergone a security check. As you scale, managing multiple packages becomes more and more of a challenge and it is difficult to gain control.
In a simple environment, you may be managing ten different Docker images with two flavors of OSs and fifteen different binary types. However, the main challenge arises when your environment grows to include fifteen different flavors of operating systems and forty different binaries within a single image.
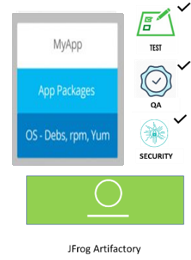
Solution: Artifactory serves as your binary release gate
Artifactory tackles this challenge by allowing you to control the content that goes into a Docker image as it lets you store all your binaries in a single location – a Docker registry. So, if you have flagged a binary as tested, QA’d and passed security – then you can put it in the Docker image. If the binary fails to meet the classification attributes, then you can easily restrict it from being pushed to the Docker image.
Challenge 2: Securing access to Docker images
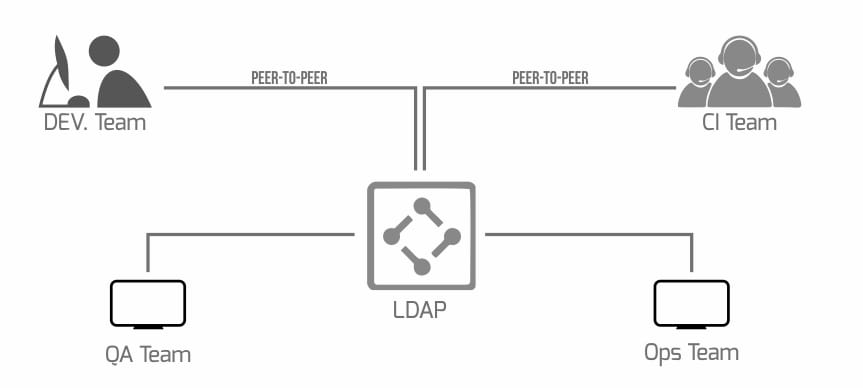
Now that you have ensured that your Docker image content is free of vulnerabilities, you are ready to tackle the next challenge. How do you access these Docker images? If you rely on cleartext passwords, then it can pose a security risk. Very few companies set policies determining how employees manage their password. For example, they can save it on a post-it note, share it with other members or put it in a script. All the above serve as security risks.
Using an encrypted password does not help either. The reason is that the encrypted password is decrypted on the client side and ends up as cleartext in the memory, which is then transmitted over the net (unless SSL is also enforced).
Another alternative could be using API keys. However, if an employee leaves the company, they still have the password. The security risk is real as the API keys do not expire by default, and can only be revoked by the initiator of the API key.
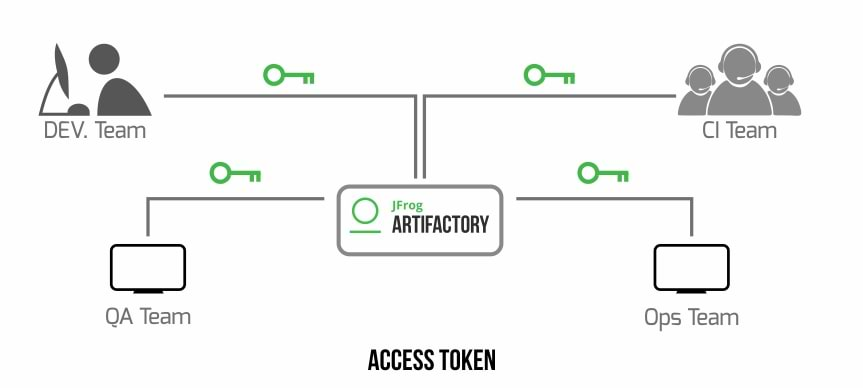
Solution: Artifactory supports secured access using access tokens
Artifactory supports access tokens providing advanced and flexible authentication with a range of capabilities:
- Cross-instance authentication: Access tokens can be used for authentication, not only by the Artifactory instance or cluster where they were created but also for other instances and clusters that are all part of the same “circle of trust”.
- User and non-user authentication: The case for authenticating Artifactory users is clear; however, access tokens can also be assigned to non-user entities such as CI server jobs.
- Time-based access control: Access tokens have an expiry date. You can control the period of time for which you grant access. However, you may also delegate control to the receiving user by making them refreshable.
- Flexible scope: Control the access level by assigning groups to tokens.
Challenge 3: Providing selective access to Docker images
The next question is how can you control who can download or move binaries and to specific Docker images. Once the binaries are part of to the Docker image, you can then determine who has access to that image? You may also want to set different read and write permissions to the different users.
Solution: Artifactory provides fine-grained access control to Docker images
Artifactory allows you to control access to repositories by selecting users or groups with a corresponding set of permissions. You can restrict access to entire repositories down to a single binary, and from a group of any size down, to a single developer.
With this flexible mechanism, you can define anything from an entire repository to be excluded from your organization’s access to including a single artifact within a repository, which may be critical for your development efforts.
Challenge 4: Detecting potential security risks and vulnerabilities
Finally, you need to gain insight into the security of your Docker images. The earlier in your DevOps cycle you detect and remove a vulnerability, the faster you can release the software to production. Most people resort to a 3-party tool, that needs to be managed separately.
Solution: Artifactory Package Native UI displays JFrog Xray metadata
To gain end-to-end Docker security coverage, our dedicated Docker package native UI in Artifactory is integrated seamlessly with JFrog Xray to show vulnerability metadata directly in the UI viewer. Let’s see how this works.
The Artifactory Package Viewer, lets you search for Docker images by name or tag and displays the results using a package-native UI that emphasizes the most relevant metadata with the look and feel of a native Docker registry.
Artifactory’s tight integrated with JFrog Xray provides automated and continuous governance of your software artifacts and dependencies throughout your software development lifecycle process. So, if you have any vulnerabilities, you will be able to detect and manage it on the Artifactory dashboard.
Conclusion
Whether you’re in a small startup or a large company, security is always a concern. JFrog Artifactory acts as a gatekeeper to ensure that the right image is pushed to production. It enables you to gain fine-grained control over what goes in your docker image, who can access Docker as well as who can upload what to Docker image. Artifactory’s native integration with Xray helps you gain vulnerability insight at an early stage. In the next blog, we will discuss how to configure high availability for your Docker Environment.