Twistlock and JFrog Steer the Container DevSecOps Seas

Twistlock and JFrog have partnered to provide continuous scanning and security for your builds. Twistlock directly integrates with JFrog Artifactory, which provides a fully automated Docker promotion pipeline for maintaining your Docker registries.
What is Twistlock?
Twistlock is a versatile security solution that works well with the Kubernetes container orchestrator and integrates smoothly with JFrog Artifactory as your Kubernetes Docker Registry. Its rule-based access control policy system helps automate the deployment of a defender of each host that comes online, so that container environments can safely scale across hundreds of servers.
Gaining container cybersecurity for your Docker Images
Twistlock provides defensive protection by scanning your Docker images and tags them with metadata that Artifactory can use to swiftly notify developers of problems that need to be fixed. The Twistlock Container Security Console provides visibility of registered containers and the risks within them. Through this tool, administrators can configure the security environment for containers, choose settings to enforce, detect vulnerabilities and prevent attacks. In this blog post, we will show you how to quickly set up Twistlock to work with Artifactory.
Integrating Artifactory in Twistlock in 3 quick steps
The following “Hello, World!” example shows how to integrate Artifactory and Twistlock and how they can work together.
Prerequisites
- A valid license of Artifactory is required to use this integration with Twistlock. Click to get your free trial of Artifactory.
- Get your trial version of Twistlock.
Step 1: Add Artifactory to Twistlock
Twistlock integrates directly with Artifactory and is easy to use.
- Access the Twistlock Container Security Console and select Defend > Vulnerabilities > Registry > Add New Registry Settings.
- Enter the registry information and click Add.
- Proceed to save the complete integration.
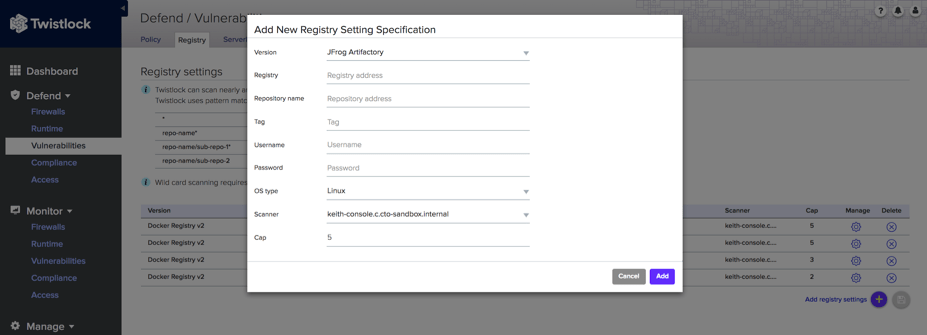
Once integrated with Artifactory, Twistlock can be set up to recognize, scan, and report on images in the Docker registry.
Step 2: Build and push the Docker Image
In this example, the “hellonode” image includes a simple “Hello, World!” for a JavaScript node.js runtime built using Jenkins. Once it passes a test cycle, it can be pushed to Artifactory, which then hosts the Docker registry.
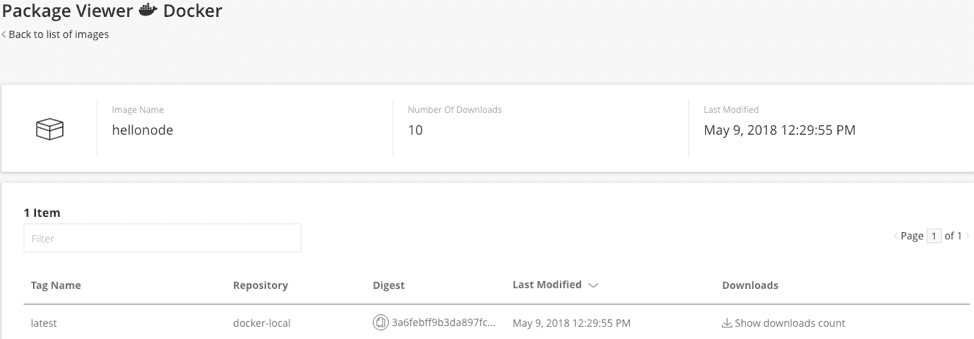
Step 3: View scanned registry information
Once added to the registry, Twistlock recognizes the “hellonode” image and scans it for vulnerabilities.
To view all of the scanned images and their detected vulnerability and compliance information in the Twistlock Container Security Console select Monitor > Vulnerabilities > Registry.
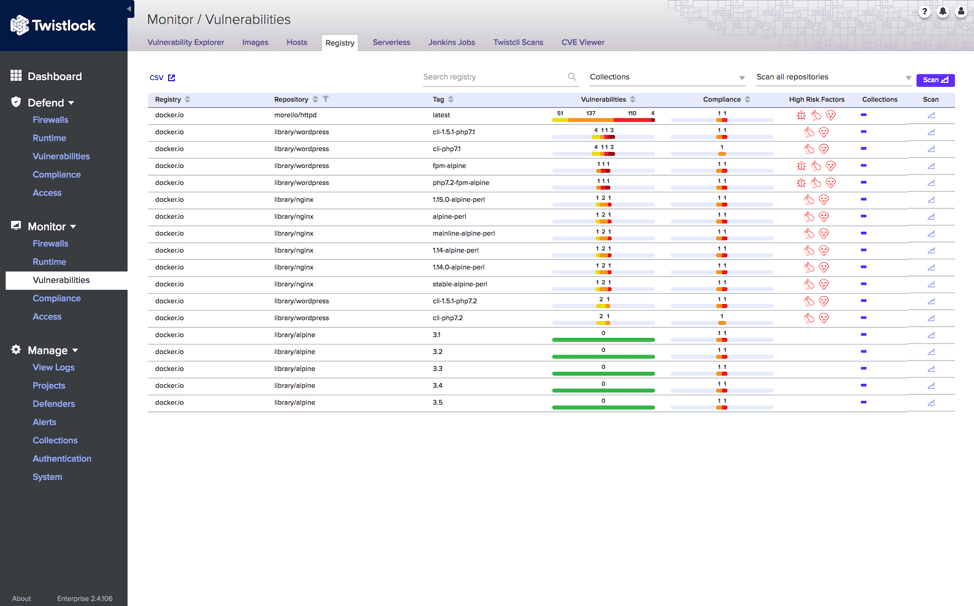
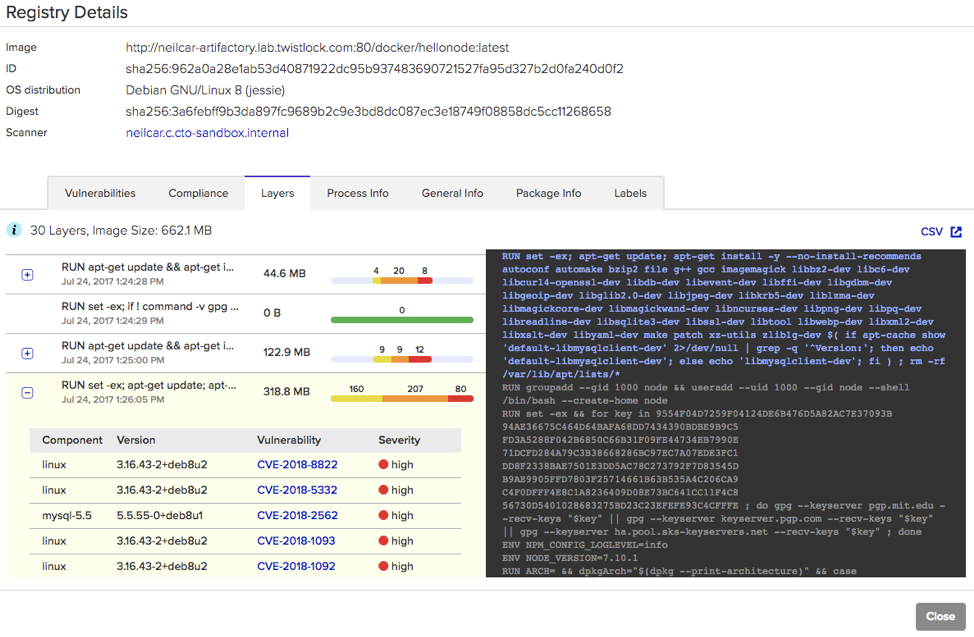
In the Registry Details tab, let’s take a look at the information in the Twistlock Container Security Console regarding your hosted Docker images in Artifactory.
To view and explore further information about items in the Artifactory registry, click on any listed image to view the risks associated with the image that was identified by the Twistlock scan in the Vulnerabilities tab, before deploying the image to the Docker nodes.
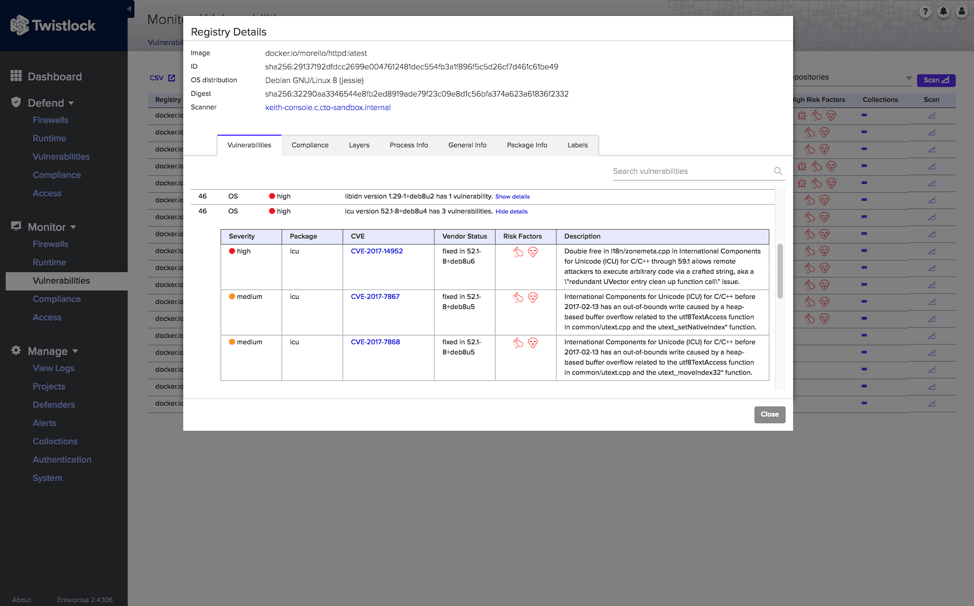
Shown above, you can view the expanded vulnerability details for the highly vulnerable image called morello/httpd:latest which displays the exact CVE, vendor status with fix information, risk factors, and a description of the vulnerability.
The Layers tab provides a layer-by-layer breakdown of the specific vulnerabilities the image contains.
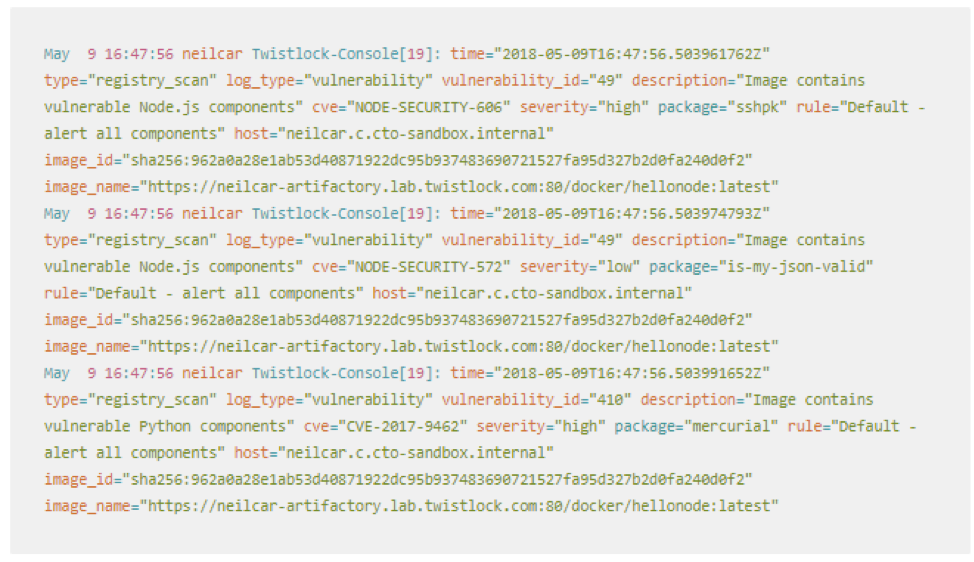
This data is also available via Syslog so that it can be integrated into security operations.
Ahoy! Your Artifactory hosted Docker containers are now ready to be shipped!
Just to sum up, when using Artifactory as a Docker registry in your DevOps workflow, Twistlock can help you to quickly assess and respond to the risk of unresolved vulnerabilities in the images being shipped.



