Bring Xray Out of the Box with Dependency and Binary Scanning
Shifting left security means you, the developer, catching and fixing vulnerabilities and license violations early in the SDLC. That’s why Xray scans binaries pushed to Artifactory by your builds, and alerts you when there are issues with your dependencies.
But catching them earlier, even before checking in code, can be important for developers shifting left. So we’ve begun to extend the capabilities of Xray, enabling you to perform on-demand scanning of either your source code or binaries in your local file system directories from the JFrog CLI.
Here are some of the reasons why these use cases are required:
- Not all of your binaries are stored in Artifactory
- Discover any vulnerabilities/licensing violations in a build before uploading to Artifactory
- A security person may need to scan a binary sent to them for verification
- Organizations want to only deploy approved binaries into Artifactory
With these JFrog CLI facilities, developers, security teams, or others can help keep vulnerabilities and license violations out of your applications long before they are made part of Artifactory’s single source of truth.
Xray Dependency Scan
JFrog Xray now provides the capability to scan vulnerabilities in your source dependencies and license violations using the JFrog CLI. The easy to use command line tool, empowers you to scan a source directory that can be run anywhere and anytime, without the need to compile, test or deploy to Artifactory, saving valuable time to address any issues.
Once actioned through the CLI, Xray will scan your dependencies the same way it does for Artifactory repositories. The command returns a detailed scan report containing the details of any vulnerabilities or license violations discovered in your dependency structure. This feature offers the following benefits:
- Developer visibility as they code to become aware of any vulnerabilities or license violations in a build before uploading into Artifactory
- Run ad-hoc security scans without uploading to Artifactory
- Adhere to organizational standards, where binaries and sources need to be approved before uploading to Artifactory.
| Still in an early phase, these additions to the JFrog CLI currently support source scanning only for Maven, Gradle, and NPM packages. |
How does it work?
To begin scanning from your command line, you must first change directory to the top-level directory that contains your source files. Then you can run the JFrog CLI command to perform the Xray dependencies scan on your files.
You can only perform an audit on one type of project at a time. For example, to perform a scan of Maven projects in your source code and report all vulnerabilities:
$ jfrog xr audit-mvn
You can also apply your Xray policy rules to your scan by specifying the watches, project, or repository path where those policies have been applied in Xray. For example, to apply the set of policy rules used in “watch1” to your Maven project scan:
$ jfrog xr audit-mvn --watches "watch1"
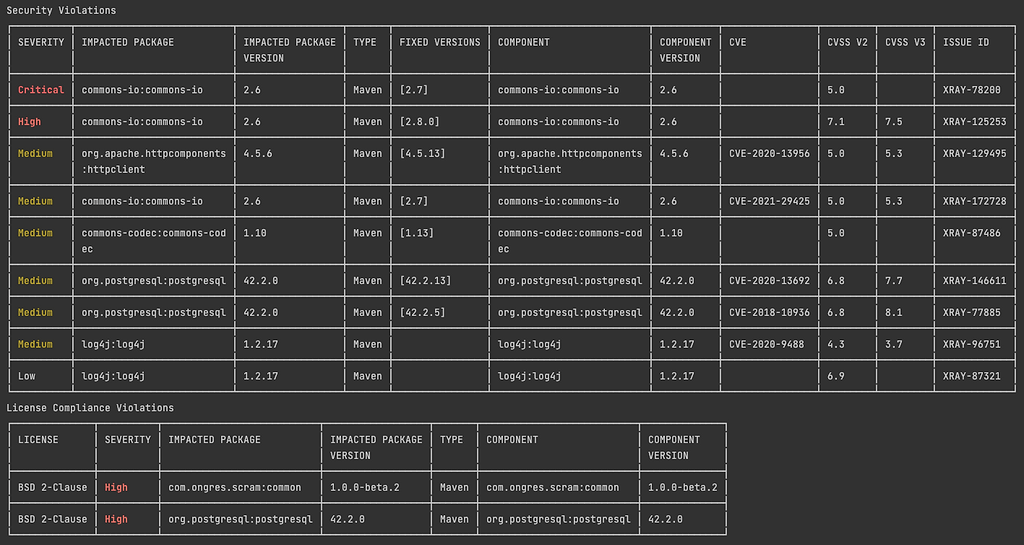
When complete, it will by default produce a report of referenced dependencies that violate those security and license policies:
If you prefer, the JFrog CLI can produce the report as a JSON file instead, which you can read with another tool of your choosing.
Xray On-Demand Binary Scan
Individually as a developer or collectively as an organization, you may wish to code and build your software securely during development, since it could save you time not having to find and fix vulnerabilities after you’ve compiled. Like the previous new scanning feature you will also need to use the JFrog CLI to activate any on-demand binary scanning.
All you need to do is point to a binary in your local file system and you’ll receive a report that contains a list of any vulnerabilities and licenses violations for that binary. The JFrog CLI encapsulates a closed source component that contains the logic of extracting a binary and composes a component graph from the binary, similar to the way Xray scans your binaries in Artifactory. For more information, see Xray Security and Compliance. The CLI returns a detailed scan results report that contains the details of vulnerabilities, violations, and licenses discovered in your binary.
Currently binary scanning is supported for all package types, except Docker which will follow very soon.
How Does it Work?
The procedure to perform an Xray on-demand binary scan is very similar to the source file scan. For example, to apply the policy rules used in “watch1” to binaries in your local file system:
$ jfrog xr s "path/to/files/" --watches "watch1"
This command will produce a security and license violations report similar to what was shown above. Similarly, you can produce the report as a JSON file instead.
Shifting “Shift Left” Leftward
These features are only two of the ways that we’ve continued to enhance Xray in the current release, making vulnerability and license compliance scanning even more accessible to developers. For more features, including the latest API enhancements, see the Xray release notes.
If you aren’t yet using Xray yet to ensure your software releases are more secure, get started with a free JFrog cloud account!