The State of Software Supply Chain Security in 2024
In today’s fast-paced software development landscape, managing and securing the software supply chain is crucial for delivering reliable and trusted software releases. With that in mind, it’s important to assess whether your organization is set up to handle the continuous expansion of the open-source ecosystem and an ever-growing array of tools to incorporate into your supply chain.
To help prepare you, we’ve compiled a comprehensive report that combines JFrog’s extensive usage data from millions of users, meticulous CVE analysis conducted by the JFrog Security Research Team, and commissioned third-party polling data from 1,224 professionals in Security, Development, and Ops roles. In this blog, I’ll give you a quick overview of some of our findings. You can also check out the full report here.
Read the ReportThemes from the 2024 software supply chain security report
Four key themes emerged from our analysis:
- An exploding software supply chain. The growing amount of open-source components available is creating an increasingly vast software supply chain (SSC) to contend with.
- Where risk is hiding (and where it’s not). While risk lies beyond the open-source ecosystem, not all reported vulnerabilities are worth spending time remediating.
- Where to focus your security efforts. A security mindset has finally hit the mainstream, but disjointed security approaches are costing development teams about a quarter of working time each month.
- The emergence of AI/ML. Organizations need to be intentional about how they’re leveraging AI-based tools and move quickly to adopt security best practices for model use.
In a nutshell, the overwhelming amount of change and the rate of expansion in terms of the tools, technologies, and languages available today has the potential to put a massive strain on organizations.
Here’s a sneak peek of some of the data available in the report:
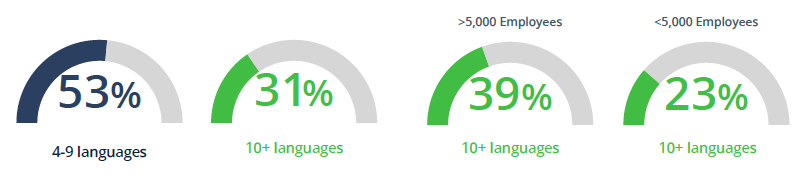
As you can see, about half of organizations (53%) utilize 4-9 programming languages, while a substantial 31% use more than 10 languages. Unsurprisingly, the larger the organization, the more programming languages are likely to be used.
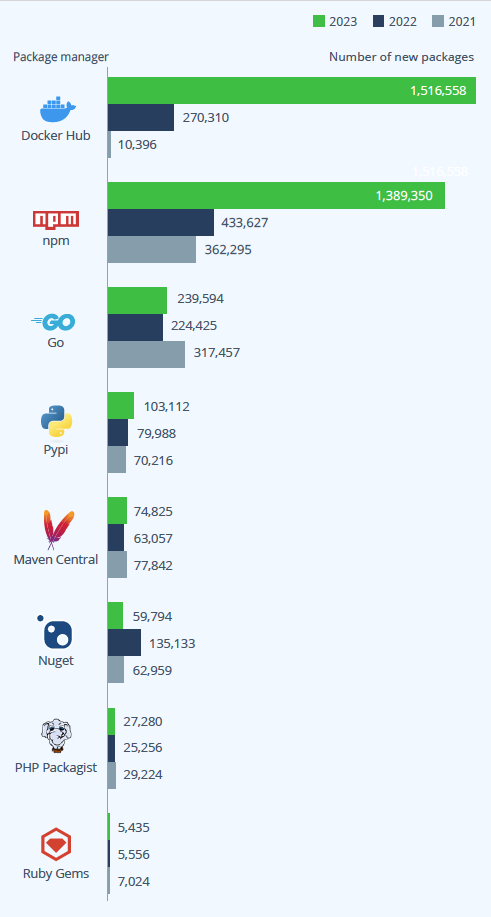
Docker and npm were the most-contributed to package types. PyPI contribution also increased, likely driven by AI/ML use cases. According to JFrog Artifactory usage data, the most popular technologies used in production-ready software are Maven, npm, Docker, PyPI, Go, Nuget, Conan (C / C++), Helm.
The variety of available open-source packages and libraries available is booming, inadvertently creating a world of potential risk for organizations, as we explore further in the report.
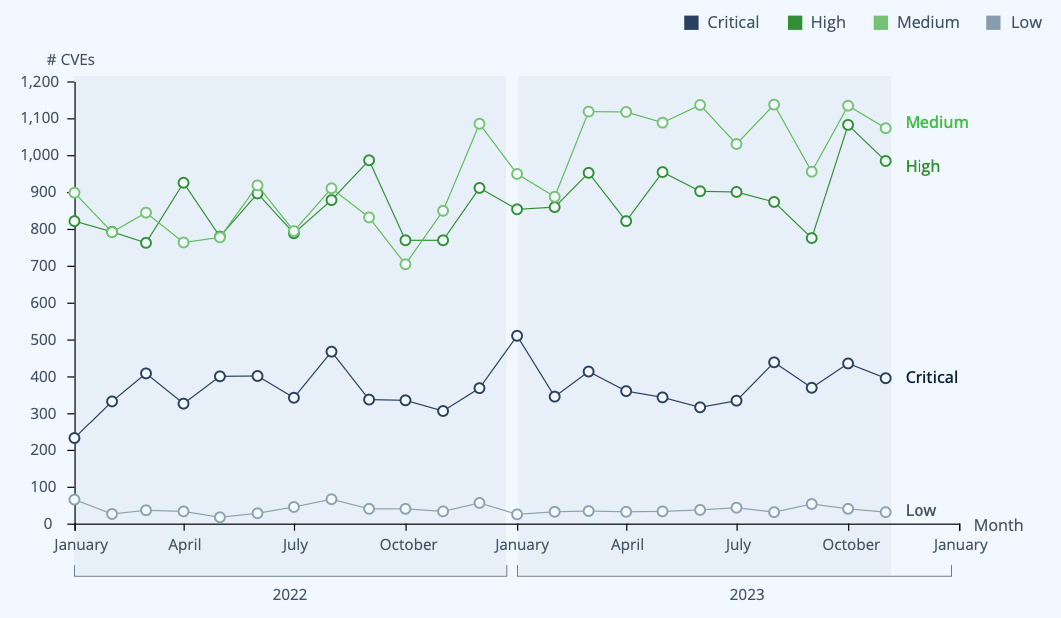
A look at CVEs in the National Vulnerability Database from January 2022 to November 2023 shows that Critical and Low CVEs remain relatively consistent, but medium and High CVEs are increasing. While this may initially cause alarm, a review of over 200 high-profile CVEs created in 2023 by the JFrog Security Research team tells a very different story. See the report to find out why.
In sum
I can’t stress this point enough: the growing complexity of the software supply chain can expose your organization to greater risk than ever. But with the right tools, processes, and best practices, technical leaders will be able to utilize the most diverse software ecosystem we’ve ever seen to their competitive advantage.
To see the complete analysis — including our security findings, a look into the future of AI/ML, plus practical security tips for safeguarding your software supply chain — read the full report. Also be sure to stay tuned for the upcoming webinar where I’ll be discussing the findings in real time.