Secure Access To Your Software Development with GitHub OpenID Connect (OIDC) and JFrog
Find out how the latest JFrog Integration with GitHub OIDC can help your development teams boost security with ad-hoc, fine grained token creation
Modern software development requires a seamless connection between multiple software development tools – particularly those used for code management and storing your software artifacts. Connecting between these tools often involves managing a variety of tokens, permissions, passwords, and keys, which if not handled correctly can expose organizations to potential security threats. The best solution is to take management of this sensitive data (aka secrets) out of the hands of engineers and let technology handle it. JFrog has done this with its recent integration of OpenID Connect (OIDC) with GitHub Actions. This valuable integration allows for a seamless Passwordless authentication experience, dynamic access control, and enhanced security for repositories.
What is OIDC
In simple terms, OpenID Connect (OIDC), is an identity layer built on top of the OAuth 2.0 framework. It allows third-party applications to verify the identity of the end-user and enables users to securely log into a website or application and then access other websites or applications without the need for separate usernames and passwords. This is done by establishing trust between the applications, ensuring a secure and streamlined authentication process.
Benefits of OIDC
Organizations and developers alike benefit in a variety of ways, including:
Passwordless experience – Eliminate the storage of basic credentials, permanent tokens, or API Keys in GitHub Secrets, thereby mitigating security risks. Storing such sensitive information in static locations poses a threat, as any compromise could lead to unauthorized access.
Dynamic Token Generation – Efficiently manage the lifecycle of tokens with automated token generation and short-term lifespans. This reduces the likelihood of outdated or unused tokens lingering in the system and minimizes security risks associated with long-lived credentials.
Consistent Access Control Policies – Ensure that access control policies are consistently applied with a fine-grained permission model. Organizations can enforce the principle of least privilege, granting only the necessary permissions for specific operations, contributing to a more secure environment.
Improved Developer Experience – Create seamless, efficient, user-friendly, and secure developer workflow by eliminating the need to handle and manage tokens manually.
Implementing GitHub OIDC in Your JFrog Platform
JFrog’s integration of OIDC with GitHub Actions enables users to establish a trust relationship between their GitHub Actions and the JFrog Platform.
The result is a more efficient and secure token management system, eliminating the need for manual token creation for each GitHub Action.
A full example workflow file is available here >
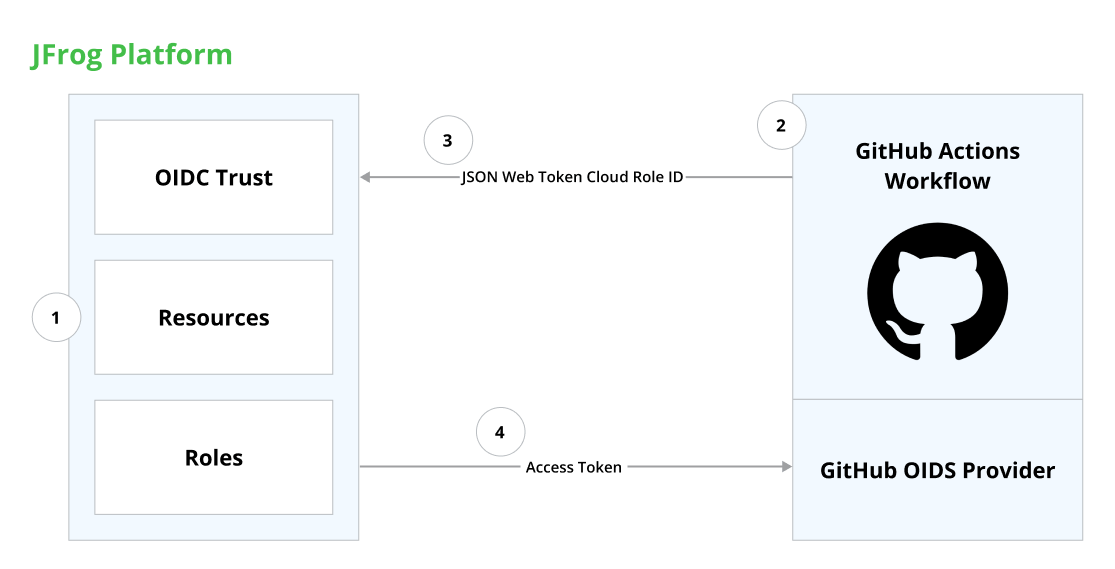
- In your JFrog Platform, create an OIDC trust between JFrog and your GitHub workflow(s) that need access to the JFrog Platform.
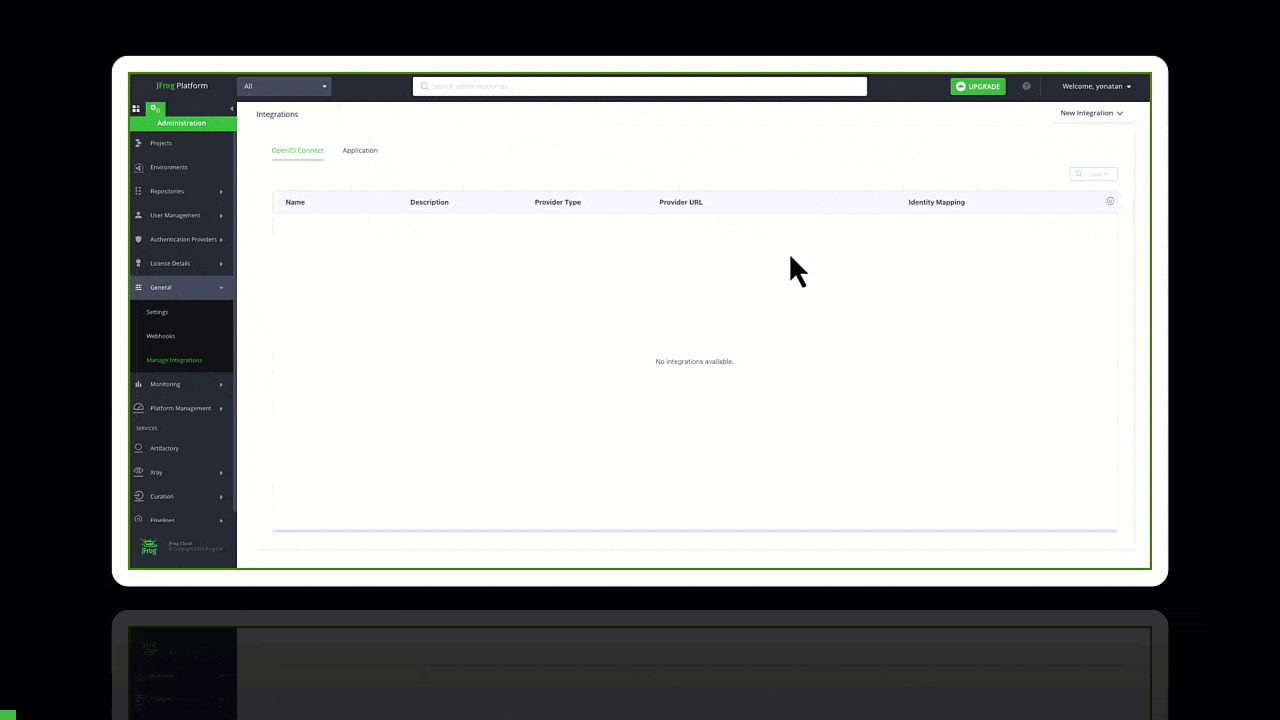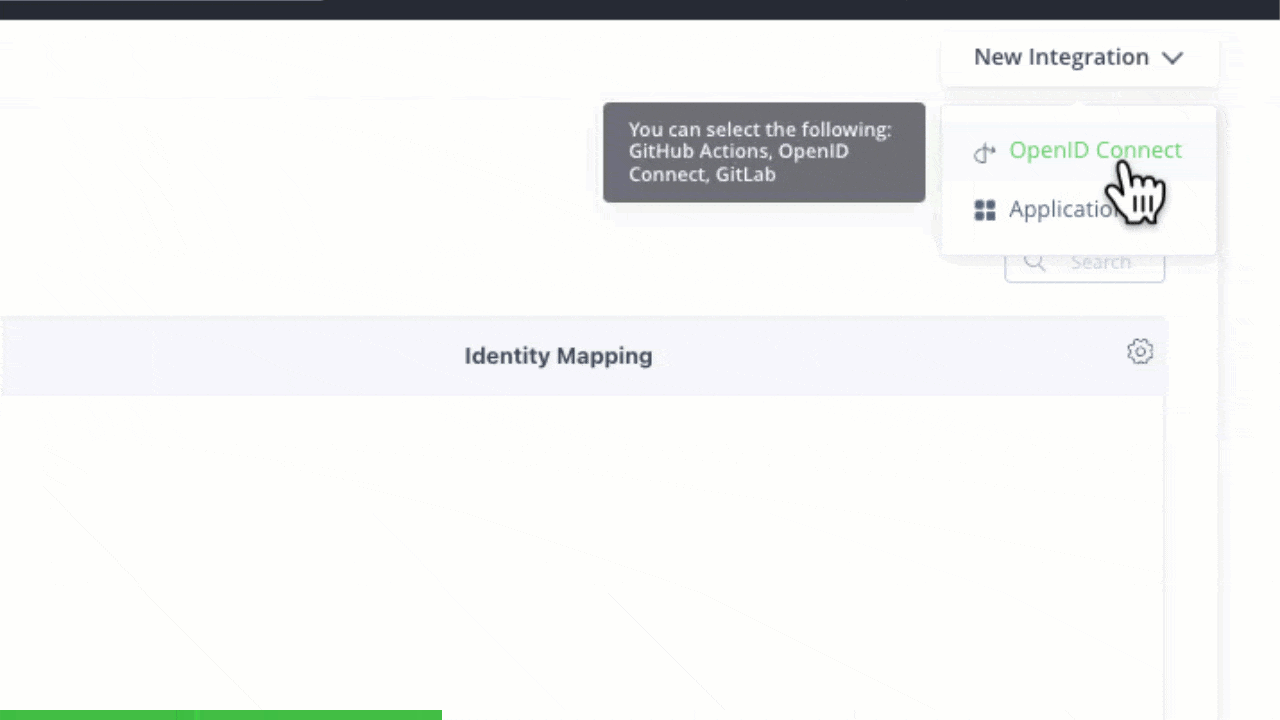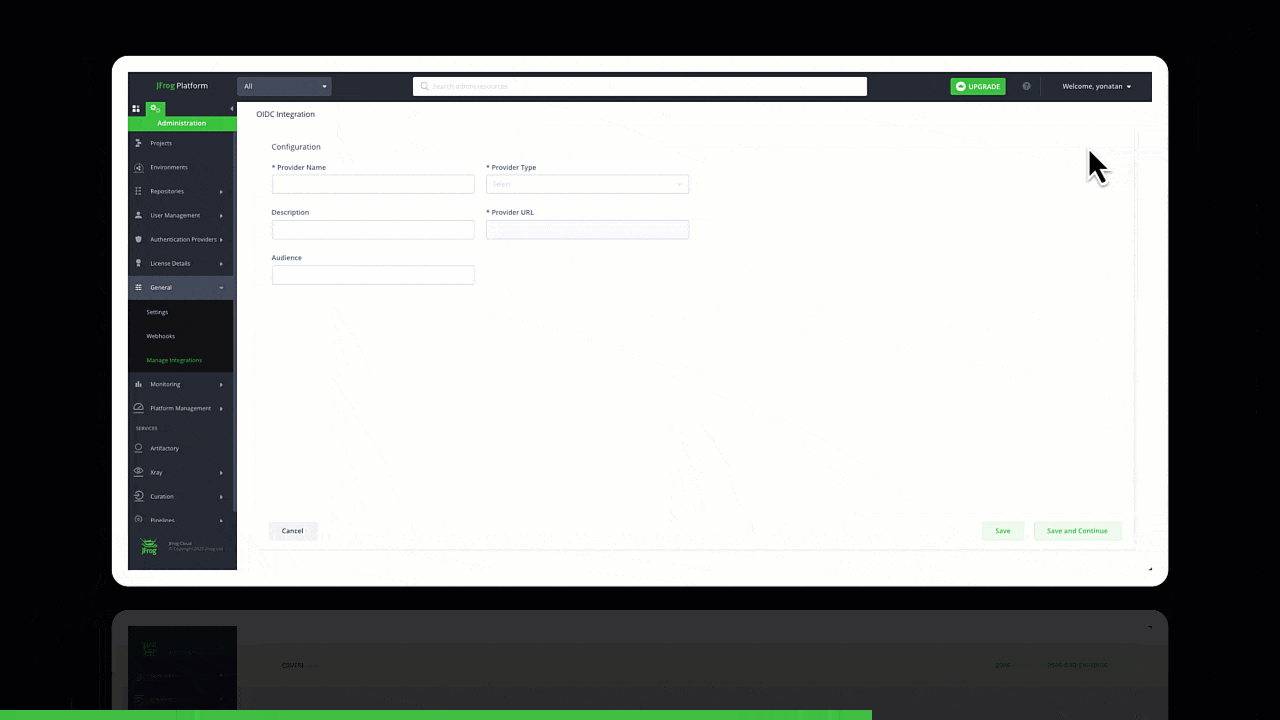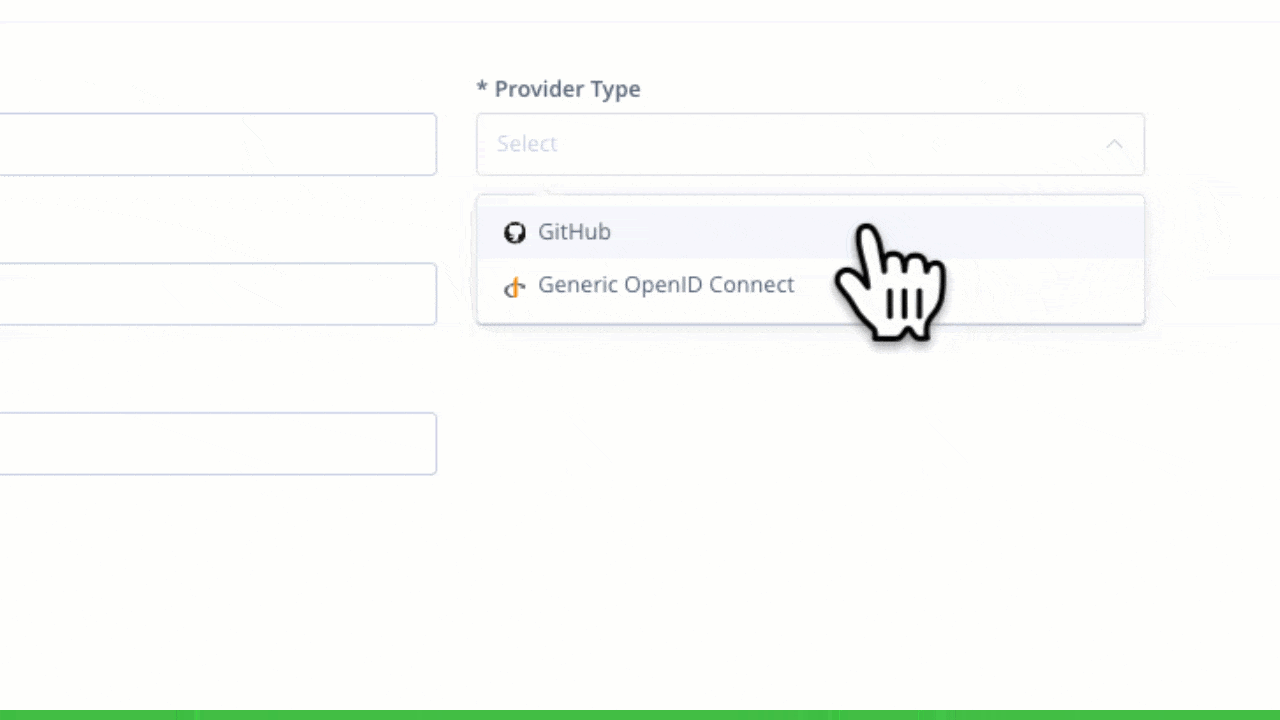
First, select OpenID Connect from the New Integration in your JFrog Platform.
Creating a new GitHub OIDC integration
Configuring trust between JFrog and GitHub Workflows
- Whenever your job runs, GitHub’s OIDC Provider auto-generates an OIDC token. This token contains multiple claims to establish a security-hardened and verifiable identity about the specific workflow that is trying to authenticate.
- Include a step in your job to request this token from GitHub’s OIDC provider and send it to the JFrog Platform. At this step, the JFrog Platform will verify the ID Token from GitHub by utilizing a certificate supplied from GitHub’s JSON Web Key (JWK)
- Once the JFrog Platform successfully validates the claims presented in the token, it then provides a short-lived access token that is available only for the duration that was configured when created the identity mapping
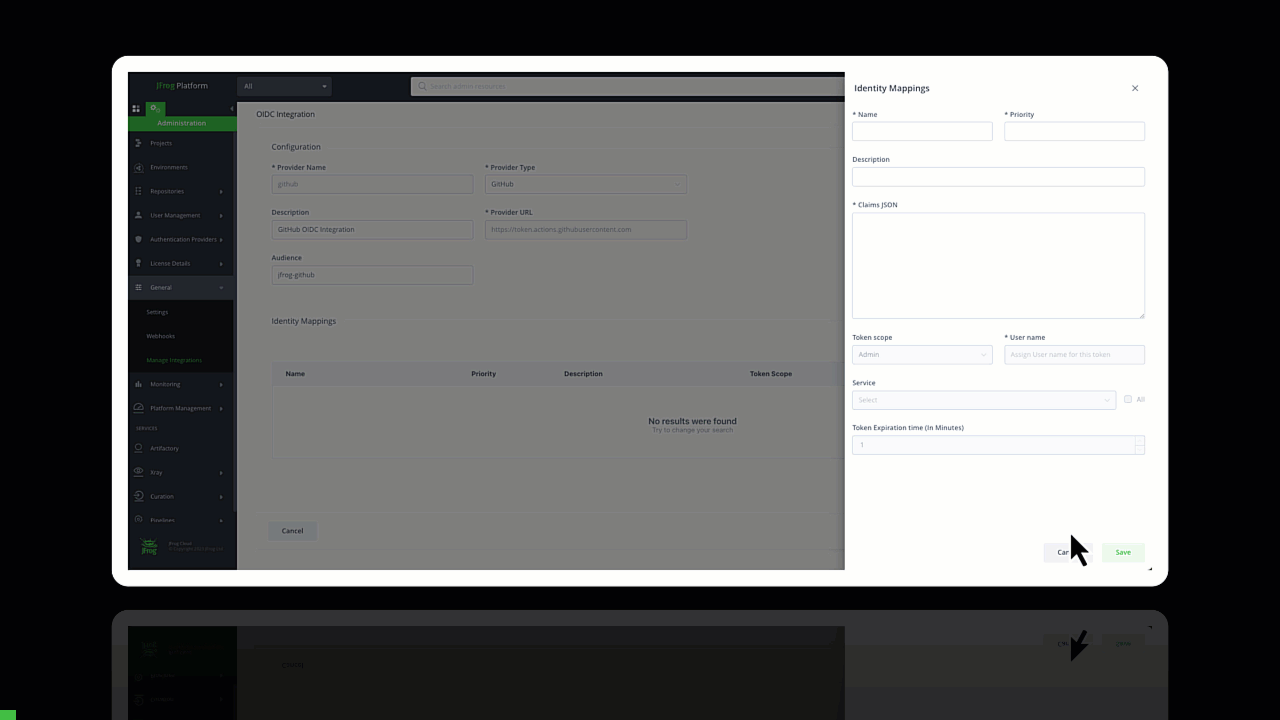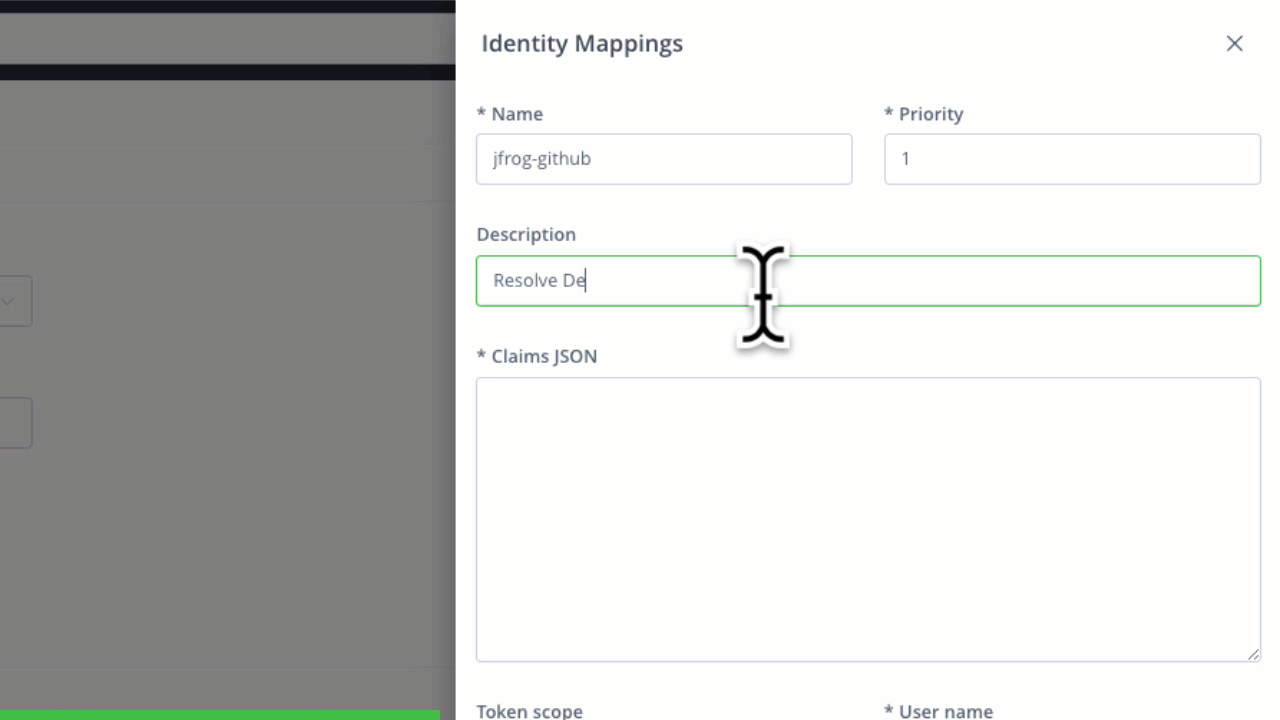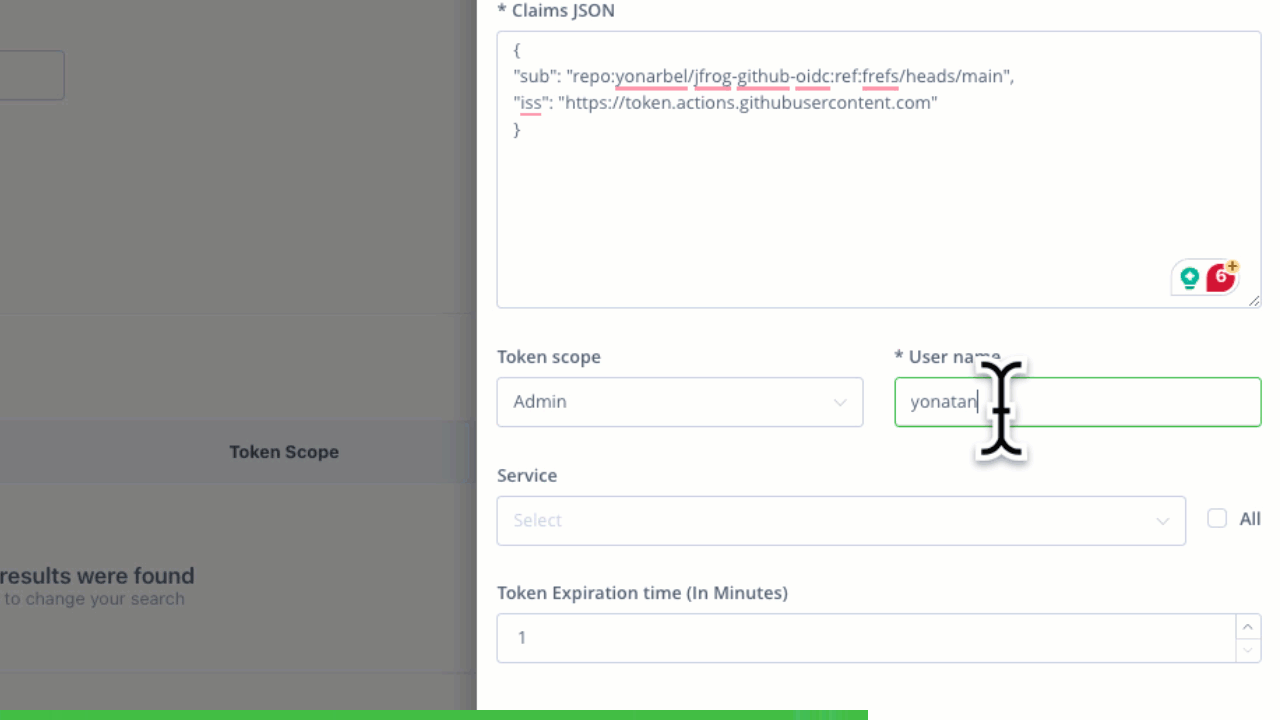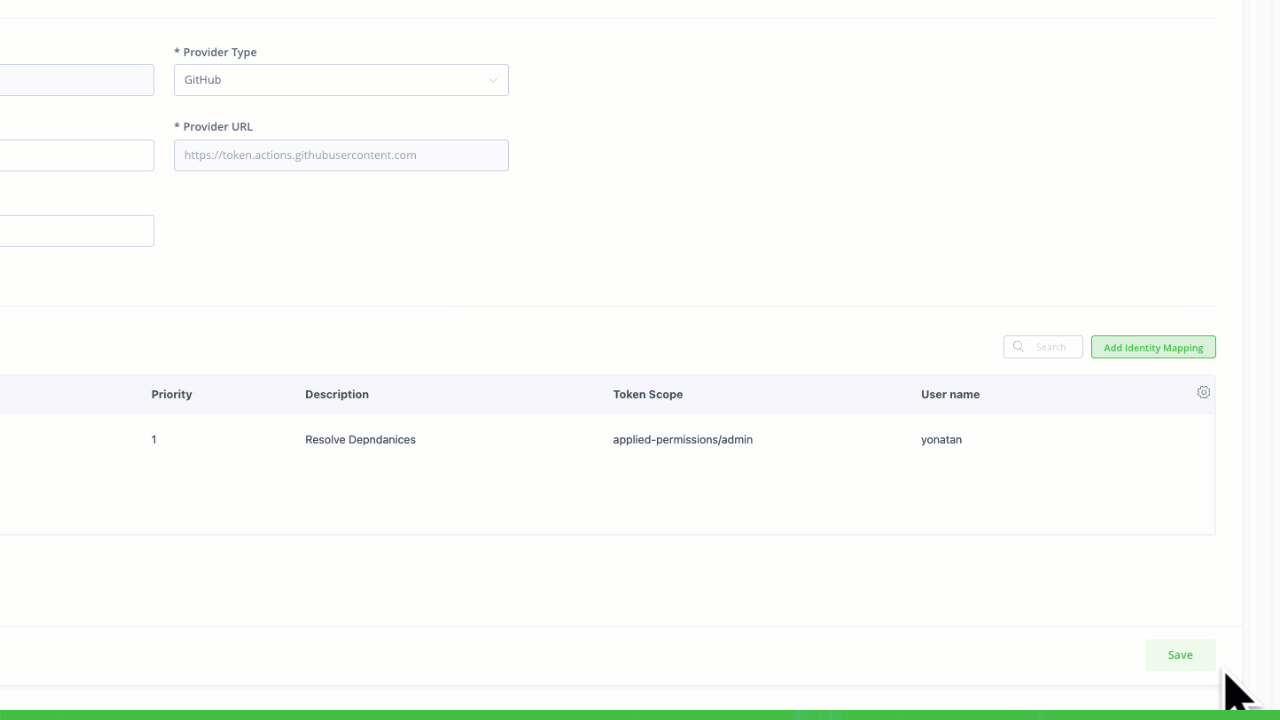
Identity Mapping
JFrog’s identity mapping feature enables users to validate access requests based on the claim JSON, fostering a nuanced understanding of operations. This ensures that tokens are granted based on specific criteria, such as user roles or project requirements. Additionally, the system allows the creation of multiple identity mappings.
Working with JFrog CLI? Implement OIDC with JFrog CLI in just a few easy steps. Just include the following code in your workflow file:
- name: Setup JFrog CLI
uses: jfrog/setup-jfrog-cli@v4
env:
JF_URL: <YOUR_JFROG_INSTANCE_URL>
with:
oidc-provider-name:<CONFIGURED_INTEGRATION_PROVIDER_NAME_ON_JFROG_PLATFORM>
oidc-audience: <CONFIGURED_INTEGRATION_AUDIENCE_NAME_ON_JFROG_PLATFORM>Step-by-step JFrog CLI documentation is available here >
(See the“Connecting to JFrog using OIDC” section)
Get Started and Improve Your Access Control Today
JFrog’s integration of OIDC with GitHub Actions is another way in which you can improve security and secrets management for your software development. As organizations continue to prioritize security and efficiency in their DevOps workflows, this functionality sets the stage for a new and secure way of JFrog repository management and the handling of sensitive data.
For more information and to get started check out our technical documentation.




 Creating a new GitHub OIDC integration
Creating a new GitHub OIDC integration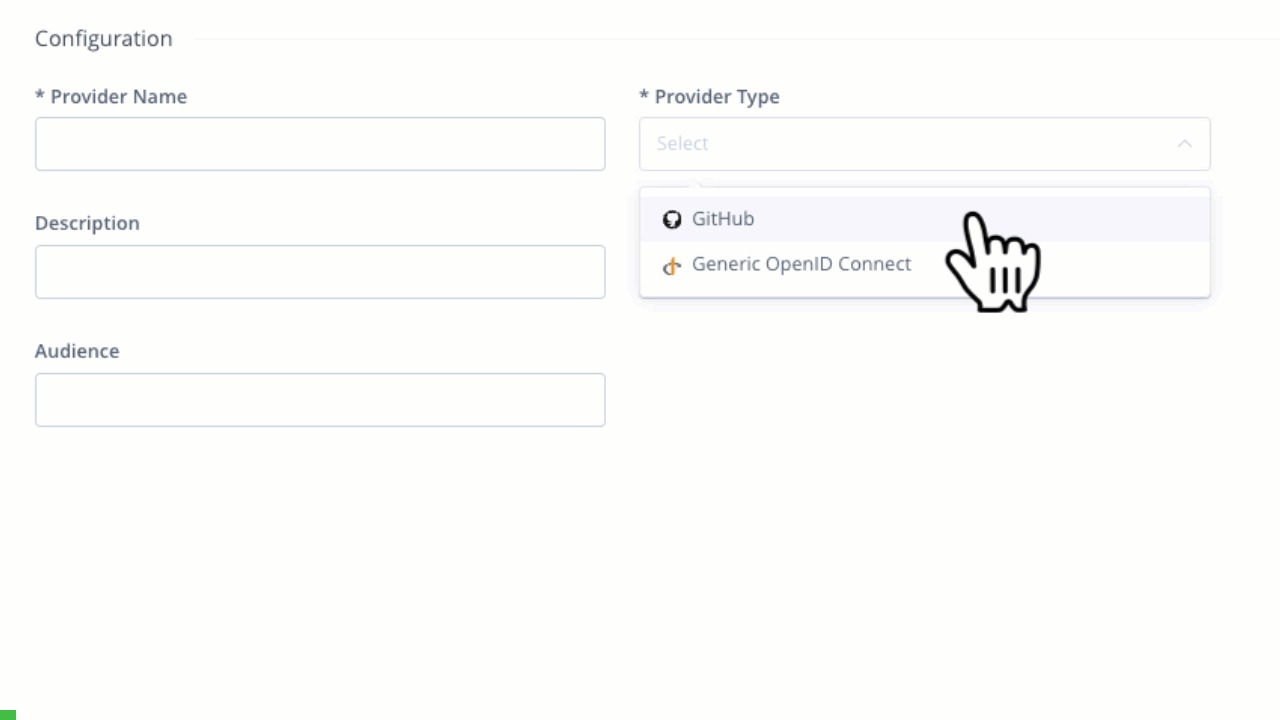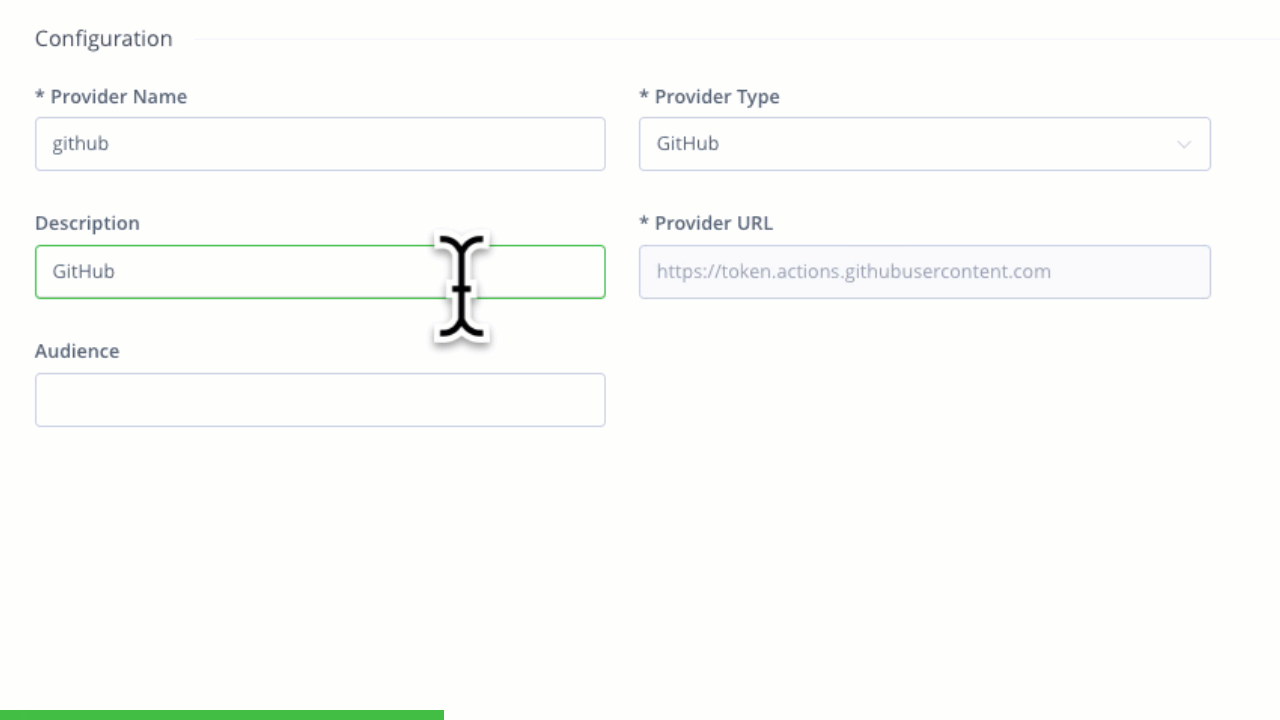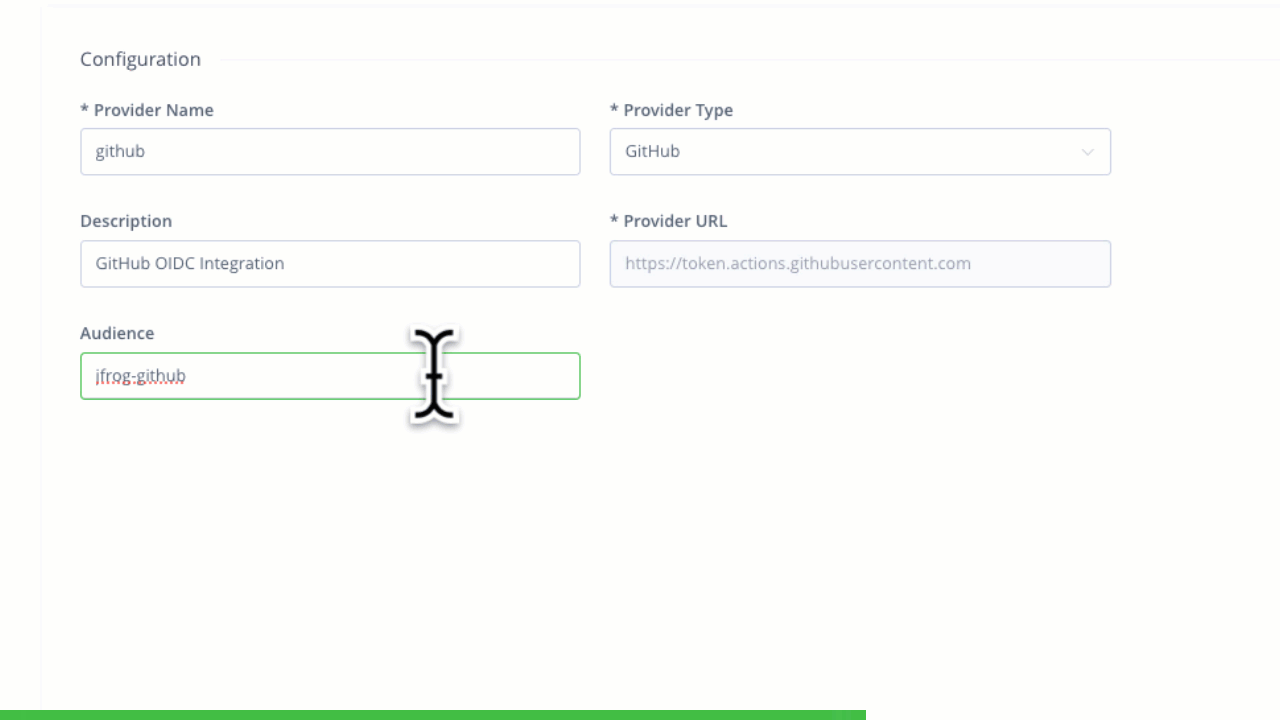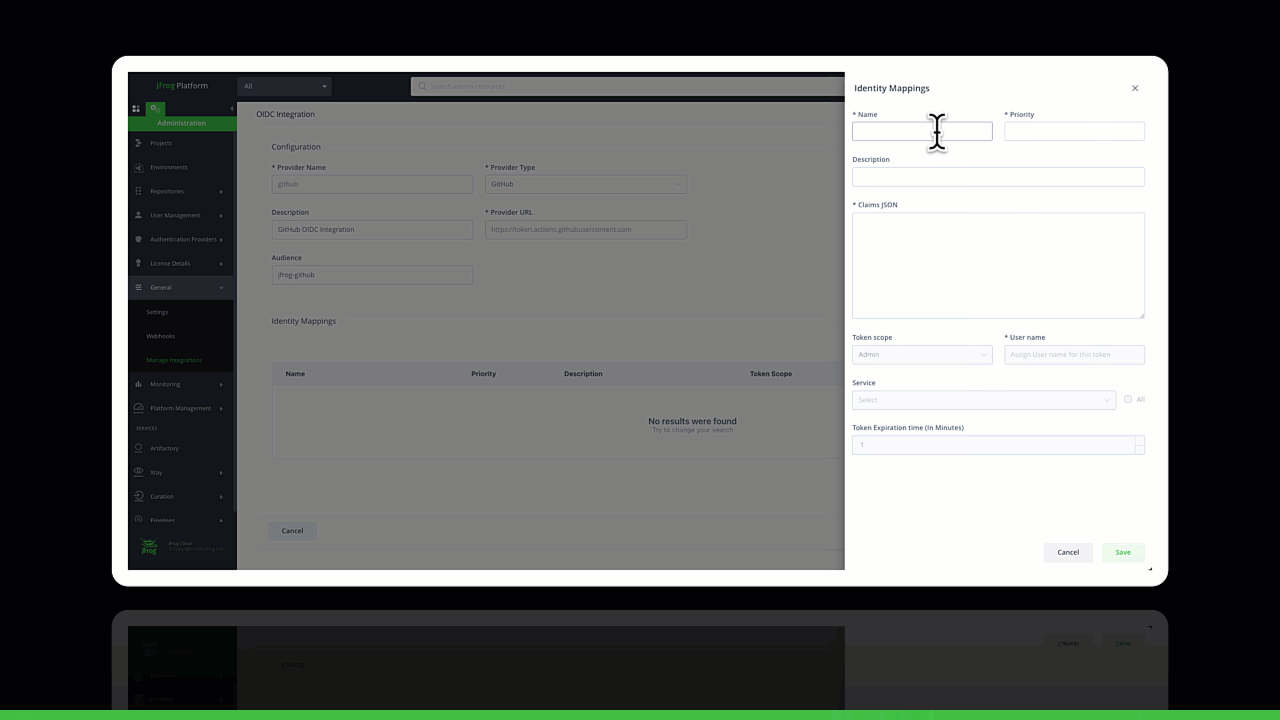 Configuring trust between JFrog and GitHub Workflows
Configuring trust between JFrog and GitHub Workflows

