Scan your software packages for security vulnerabilities with JFrog Xray
3 easy to use commands to scan your binary files, Docker images and open source dependencies for security vulnerabilities and license violations
Scanning your packages for security vulnerabilities and license violations with SCA Tools should be done as early as possible in your SDLC, and the earlier the better. This concept is also known as “Shifting Left”, which helps your organization comply with security policies and standards early on in the software development process.
As developers, this may seem like a hassle, but with JFrog CLI it’s easy! With a simple JFrog CLI command line, you can quickly scan your dependencies directly from sources, on your local machine, on-demand, and get a violation report detailing any violation that’s been detected. Giving you insights into what’s really inside your code.
Setting up your environment
Before we get started, we’ll need to set up your free JFrog Platform and JFrog CLI using the latest developer friendly setup. This will take less than a couple of minutes to complete.
Mac or Linux
If you’re using Mac or Linux, you can get started using the curl utility:
curl -fL https://getcli.jfrog.io?setup | shWindows
If you’re using Windows, run Powershell:
powershell "Start-Process -Wait -Verb RunAs powershell '-NoProfile iwr https://releases.jfrog.io/artifactory/jfrog-cli/v2/[RELEASE]/jfrog-cli-windows-amd64/jfrog.exe -OutFile $env:SYSTEMROOT\system32\jf.exe'" ; jf setup* Existing JFrog Platform users can configure their server with JFrog CLI by running the following command anywhere on their machine: $ jf c add <server-id>
3 Security Scan Commands
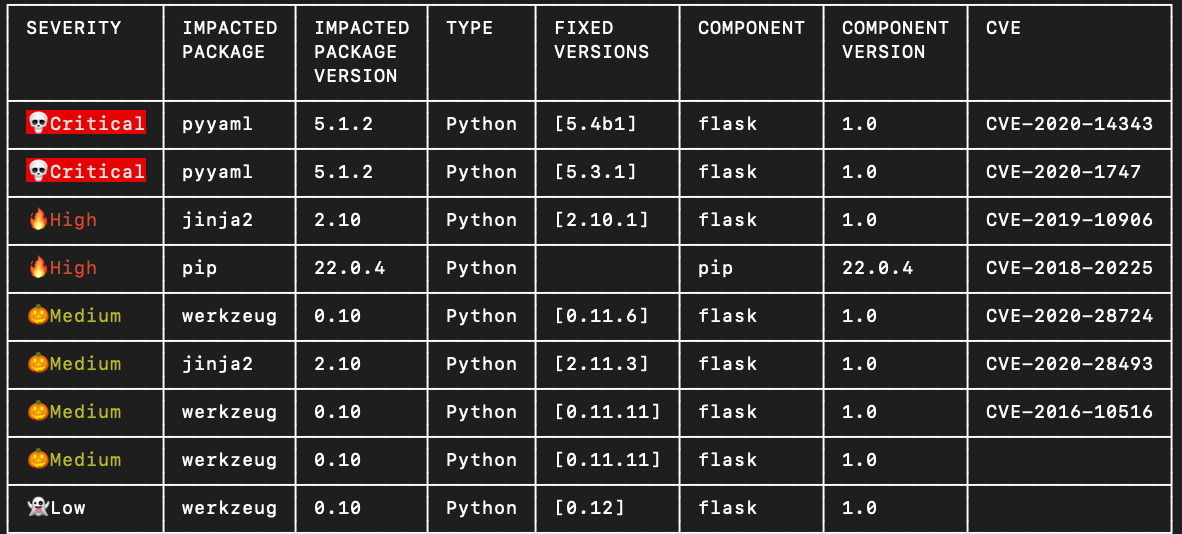
Running any of these scan commands directly from your terminal will return a complete security report outlining all of the detected security vulnerabilities.
Additional Reference: This can also be returned in a JSON format for automation purposes. To modify the format type, provide the format option: –format=json/simple-json. Additional options are available using –help or in the Xray documentation.
Let’s go through each of the commands.
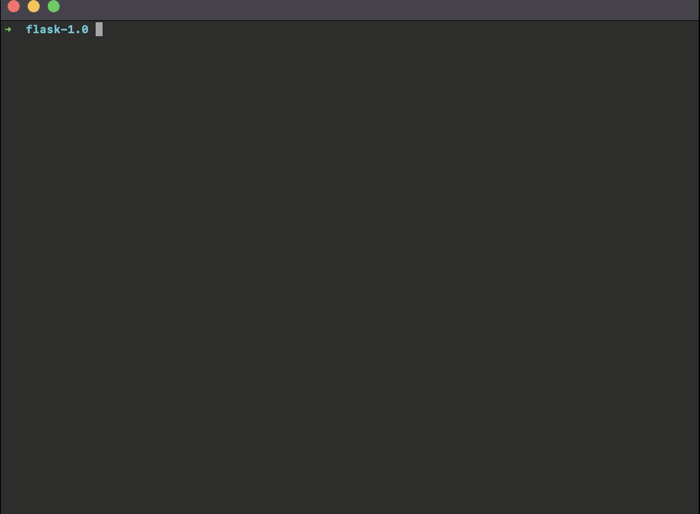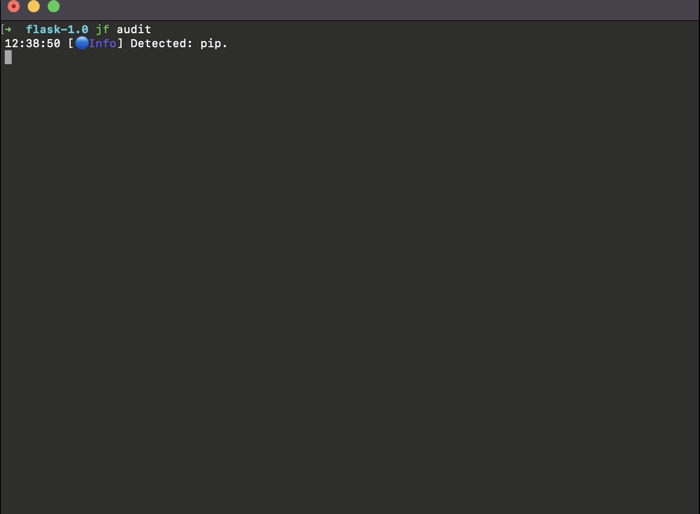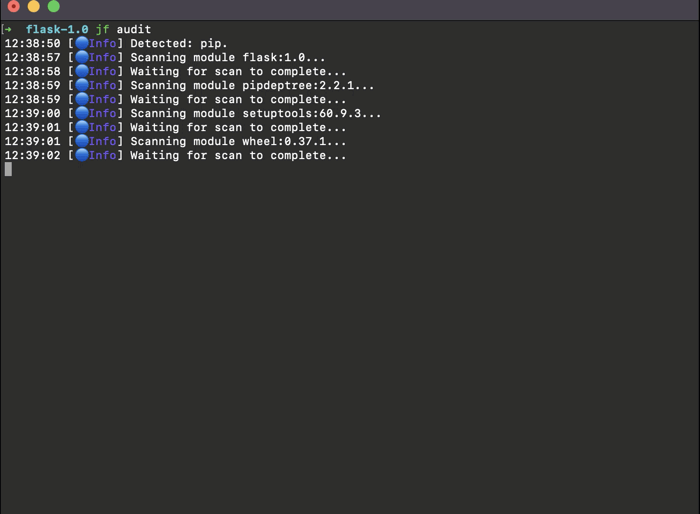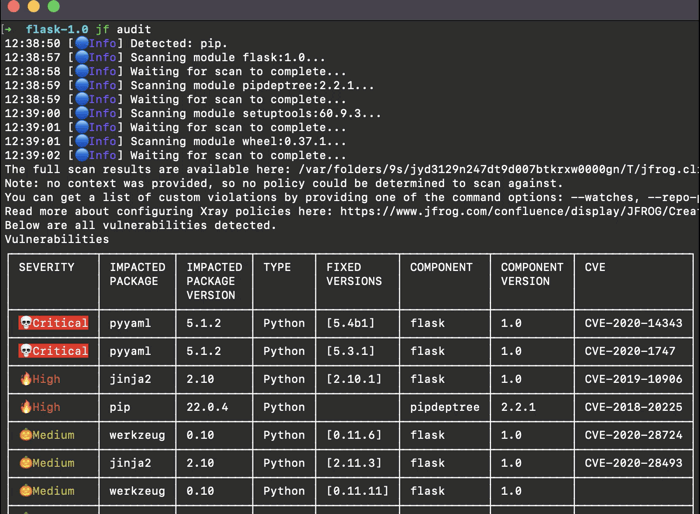
1. Audit
We’ll start with scanning your project dependencies directly on your sources.
The Audit command uses your package manager to build the project’s full dependency tree and scan all its components.
$ jf audit* The command will detect the package manager used by the project automatically.
Support for this command is available for Maven (Version 3.1.0 or above), Gradle, npm, pip, pipenv, Go, NoGet, .net.
2. Docker Scan
To scan our images, we’ll run the following ad-hoc container image scanning using the CLI.
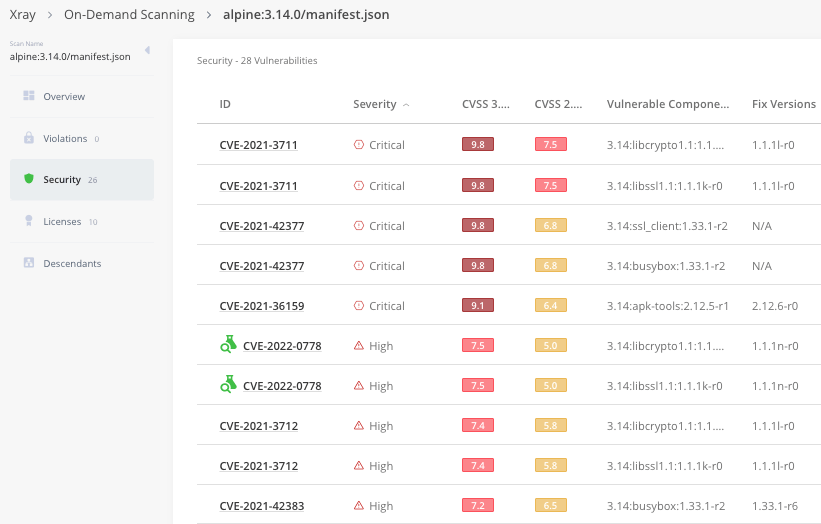
$ jf docker scan You can also view the scan results as part of the security section in the JFrog Platform.
3. On-Demand Binary Scan
To scan all files in a specific directory and report all identified vulnerabilities, run the following on-demand binary scan command pointing to a binary in your local file system.
$ jf scan "path/to/files/*"Keep exploring
Building your software securely during development will save you valuable time by not having to find and fix vulnerabilities after you’ve already compiled your code.
There’s so much more that can be done with JFrog CLI! The JFrog CLI project and its dependencies are all open source, and you can even develop and share your own plugins.
Ask questions or let us know what other functionality you’d like to see, in the project’s Github issues section.