JFrog4JFrog: DevSecOps Made Simple
A practical guide for DevSecOps Engineers to maximize your capabilities using the JFrog Platform - your single source of truth for securing the software supply chain.
Developers simply want to write code without interruption, while operations wish to build as fast as possible and deploy without restrictions. On the other hand, security professionals want to protect every step of the software supply chain from any potential security threats and vulnerabilities.
In software development, every piece of code can potentially introduce vulnerabilities into the software supply chain. The complexity only increases with inclusion of more Open Source packages and the ever increasing number of builds and releases.
By sharing how JFrog’s own DevSecOps team uses the JFrog Platform on a day-to-day basis, we can better understand how to secure each phase of the development lifecycle, while enabling full visibility of all software artifacts from coding through to creating a build, distribution, and deployment.
Securing the Software Supply Chain Ebook
How JFrog secures software and speeds up development
Here are the stages of development that we need to secure:
- Coding – Selecting the OSS and third party packages that will be used with in-house code to deliver the software’s functionality.
- Build & Test – Compiling code, including all associated dependencies, into binaries which are made into builds, tested and prepared for release.
- Release – Distribution and deployment resulting in an operating version in the end user’s environment.
Productivity in software production means writing code, building it fast, testing it and securely delivering quality applications to end users. No one wants the security team to discover a critical vulnerability which could result in rewriting code, upgrading OSS packages, re-testing, creating a new build, and ultimately delaying the release.
By the time security discovers most vulnerabilities…
IT IS JUST TOO LATE.
The earlier that vulnerabilities are discovered, the better it is for security, developers, and operations.
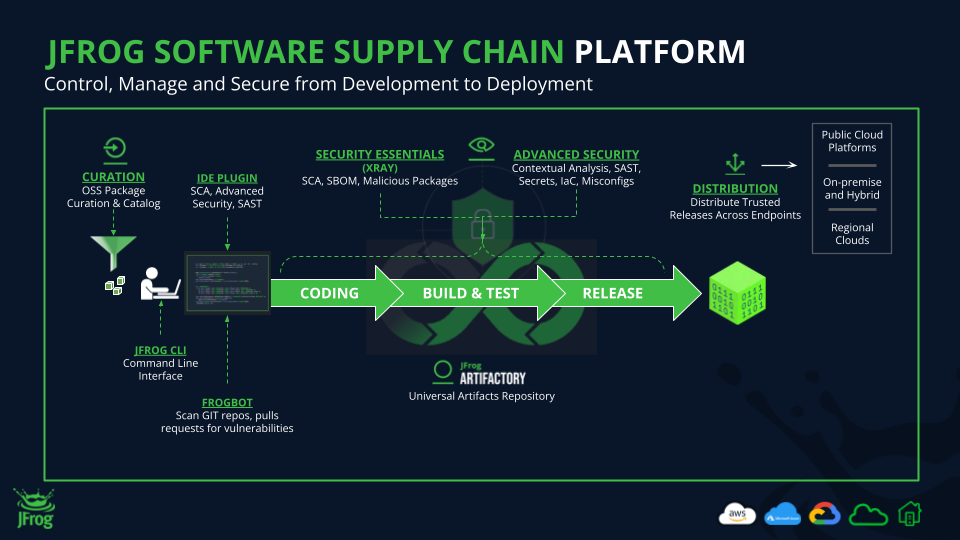
Now let’s take a deeper dive into what’s happening in each phase:
1. Coding Phase
Challenge
Shifting Left is an important trend as the cost of prevention is far less than it costs to remediate an exploited vulnerability after the software has already been released and deployed. Mitigating potential threats as early as possible in the development process helps lower the risk of having a costly and damaging security incident.
Relevant security issues during the Coding Phase include:
- Compatibility with Integrated Development Environments (IDEs)
- Open-source CVE exposures
- Insecure coding practices
- Malicious packages
- License violations
- Standards compliance
JFrog Solution
Integrating your IDE
The earliest step is installing the JFrog IDE plugin on all your software development endpoints. This functionality advises developers about new and existing vulnerabilities before their code is committed to a repository. JFrog IDE plugins are available for Microsoft Visual Studio, IntelliJ IDEA, and Eclipse.
Blocking Malicious Code
We must make sure the development environment remains secure by preventing the introduction of potentially malicious code. For this, we used JFrog Curation which makes it easy to block malicious or risky open-source packages before they can enter the development environment.
Source Code Scanning
Next is finding potential security issues such as secrets, IaC misconfigurations, and other vulnerabilities in our source code. This is where we use JFrog Frogbot which scans pull requests immediately after they are opened but before they are merged into the project.
Benefits
Scanning OSS packages and source code increases awareness and results in saving precious time for developers, as potential vulnerabilities can already be prevented during the Coding Phase. It also helps DevSecOps teams enforce their security vulnerability policy and set the standard in the earliest stage of development.
2. Build & Test Phase
Challenge
Now we must make sure our binaries are stored in a safe environment and scanned to detect potential vulnerabilities. The main security issues during the Build & Test Phase include:
- Scanning binaries
- Secrets exposure
- Compliance violations
- Misconfigurations
- Protection of authentication credentials
During this phase, source code and OSS packages are compiled into binaries, which now become the focus of our security efforts.
JFrog Solution
To store our binaries in a secure and accessible environment, we rely on JFrog Artifactory as our binary repository manager, as it provides control and end-to-end visibility of all of our binaries including dependencies, components, containers, and libraries.
We require both binary and source code scanning so we can detect:
- Critical and High-severity vulnerabilities
- Malicious packages
- Hardcoded secrets
To address these challenges we turned to JFrog Xray for basic security and JFrog Advanced Security for more robust protection.
JFrog Xray
We use JFrog Xray for basic security functionality including:
JFrog Advanced Security
For heavier lifting, we use JFrog Advanced Security including:
Benefits
By continuously scanning repositories for CVEs, we can detect new vulnerabilities, not only for new releases but even for packages from earlier releases that have already been deployed in runtime!
Blocking suspicious third-party and OSS packages (according CISO standart) helps speed up operations by having developers fix potential vulnerabilities before promoting and releasing for distribution to production.
3. Release Phase
Challenge
We must now make sure that no malicious code is injected during the distribution process, based on these potential attacks:
- Build tampering
- Man-in-the-middle attacks
- Compromised repositories
- Counterfeit updates
JFrog Solution
This is where we rely on JFrog Xray and JFrog Distribution working together to protect our software. Distribution provides a secure platform to distribute binaries to multiple locations and update them as new versions are available. Release Bundles are verified by the target destination to ensure that they are signed correctly and safe to use while mitigating the chance of malicious code injection attacks.
Benefits
Implementing security measures in the distribution stage gives us one last gate to secure the release before it is deployed to runtime. If a threat is detected after build&test, we can still implement a policy to stop the vulnerable package from being deployed from that point on.
Summary
Protecting each phase of development, results in an end-to-end DevSecOps solution. With full visibility of security issues across the entire software supply chain, the JFrog Platform not only provides monitoring and alerts, but more importantly presents insights into security posture based on overall data and analytics including key KPIs and performance criteria.
This is why the JFrog Platform makes DevSecOps day to day operations cost-efficient, effective and more importantly – simple. Come check it out by taking a tour, booking a demo or starting a free trial at your convenience.








