JFrog KubeXray Extends Deep Scanning Security to Kubernetes Runtime

Most security measures are designed to keep gremlins from getting loose. Identifying an application’s risks early means you can prevent or limit its deployment into your system. With that knowledge, any gremlins in your containers that might do damage can be safely kept behind the fence built by your policies.
But what can you do when the gremlins have already escaped? How can you make sure that container applications that are already running in Kubernetes pods comply with your current knowledge of risk and policies?
To solve that problem, JFrog offers KubeXray, an open source software project that extends the security of Xray, our universal binary analysis tool, to the applications running (or about to run) in your Kubernetes pods. Using the metadata that Xray generates by scanning container images, KubeXray can enforce your policies on what has already been deployed.
KubeXray monitors all of your active Kubernetes pods to help you:
- Catch newly reported risks or vulnerabilities in applications that are currently running in all Kubernetes pods
- Enforce your current policy on running applications, even after you have changed those policies
- Enforce policy for running applications that have not been scanned by Xray, and whose risks are unknown
In this way, KubeXray helps you corral your loose gremlins back to safety.
Background
Since most applications rely heavily on dependencies from package managers and open source repositories, they are vulnerable to either malicious or unsecure code from these sources.
The Javascript community was roiled very recently when they learned that the popular event-stream package in npm had been updated with a malicious package that targeted a bitcoin wallet platform. In the three months before it was discovered and reported, the package had been downloaded nearly 8 million times.
While such incidents from community sourced package managers are infrequent, they aren’t uncommon. A year prior, 39 malicious packages were found and removed from npm.
Xray, the JFrog universal binary analysis tool and policy engine, scans container images in an Artifactory repository to identify known vulnerabilities reported from a variety of sources. It performs deep recursive scans to check all of an application’s components for both known risks and license policy compliance, and populates metadata for the images.
DevOps administrators can configure policies to limit or prevent deployment of those container images by Kubernetes according to the level of risk indicated by what Xray’s scans find. In this way, vulnerable or non-compliant applications can be kept from running, or limited in what they are allowed to do when they are launched.
What KubeXray does
Where Xray detects risks and applies policy to container images before Kubernetes deploys them to pods, KubeXray detects risks and applies policies to Kubernetes pods that are already running or about to run.
KubeXray monitors events from the Kubernetes server and from Xray, and enforces current security policy for all of the pods Kubernetes runs. KubeXray listens to these event streams:
- Deployment of a new service
- Upgrade of an existing service
- A new license policy, such as a new license type disallowed for runtime
- A new security issue
When an issue is detected, KubeXray responds according to the current policy that you have set. You can select one of the following possible actions:
- Scaledown to 0. The desired state of a service is updated to 0, making it inactive while it can still be queried
- Delete the corresponding Kubernetes resource that’s pointing to a vulnerable container image(s)
- Ignore and leave the pod running
KubeXray also understands the variation between different Kubernetes resources (StatefulSets & Deployments) and permits different policy actions to be applied for each.
While KubeXray primarily extends Xray’s deep scanning security to running Kubernetes pods, it also provides some policy control for pods that haven’t been scanned by Xray, such as container images that were deployed from a repository other than Artifactory. For pods that haven’t been scanned by Xray, and whose risks are therefore unknown, you can specify a separate policy action to be taken.
How KubeXray works
KubeXray monitors every pod running in a Kubernetes cluster and uses the Xray metadata, when and whether available, to determine the policy action.
- For every pod (running or scheduled to run) on Kubernetes, KubeXray checks against the Xray metadata for vulnerabilities or license issues. If any risks are found, KubeXray will apply the corresponding policy action.
- If any of the container images in a Kubernetes pod (running or scheduled to run) is not recognized by Xray — because it wasn’t scanned, or because it wasn’t deployed from Artifactory — then KubeXray will apply the current policy action set for an unknown risk.
Any time a new policy gets added or updated on Xray, or a new vulnerability is reported, KubeXray detects this change and checks if there are issues with existing pods. If any risks are found, KubeXray will apply the current policy action.
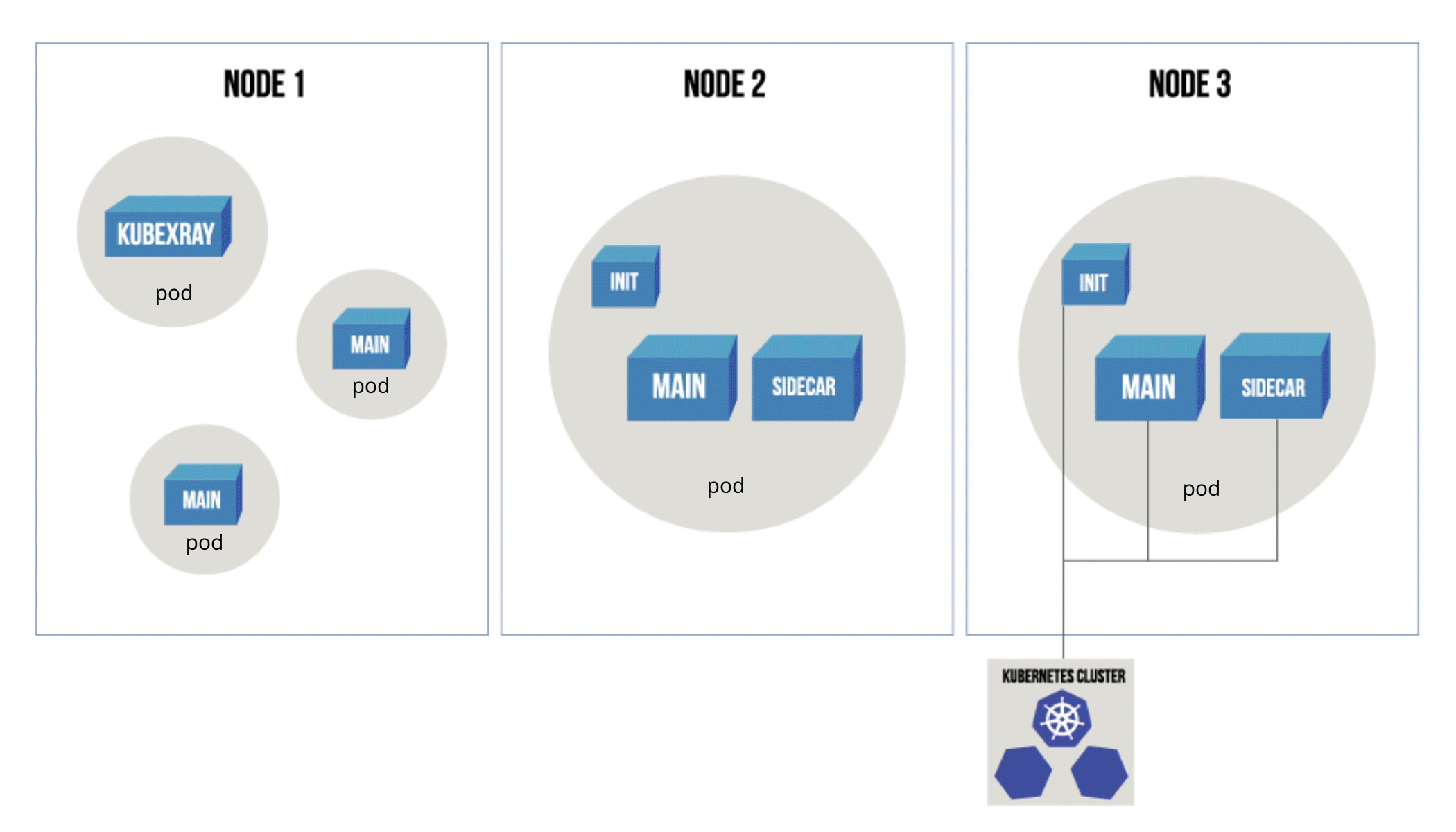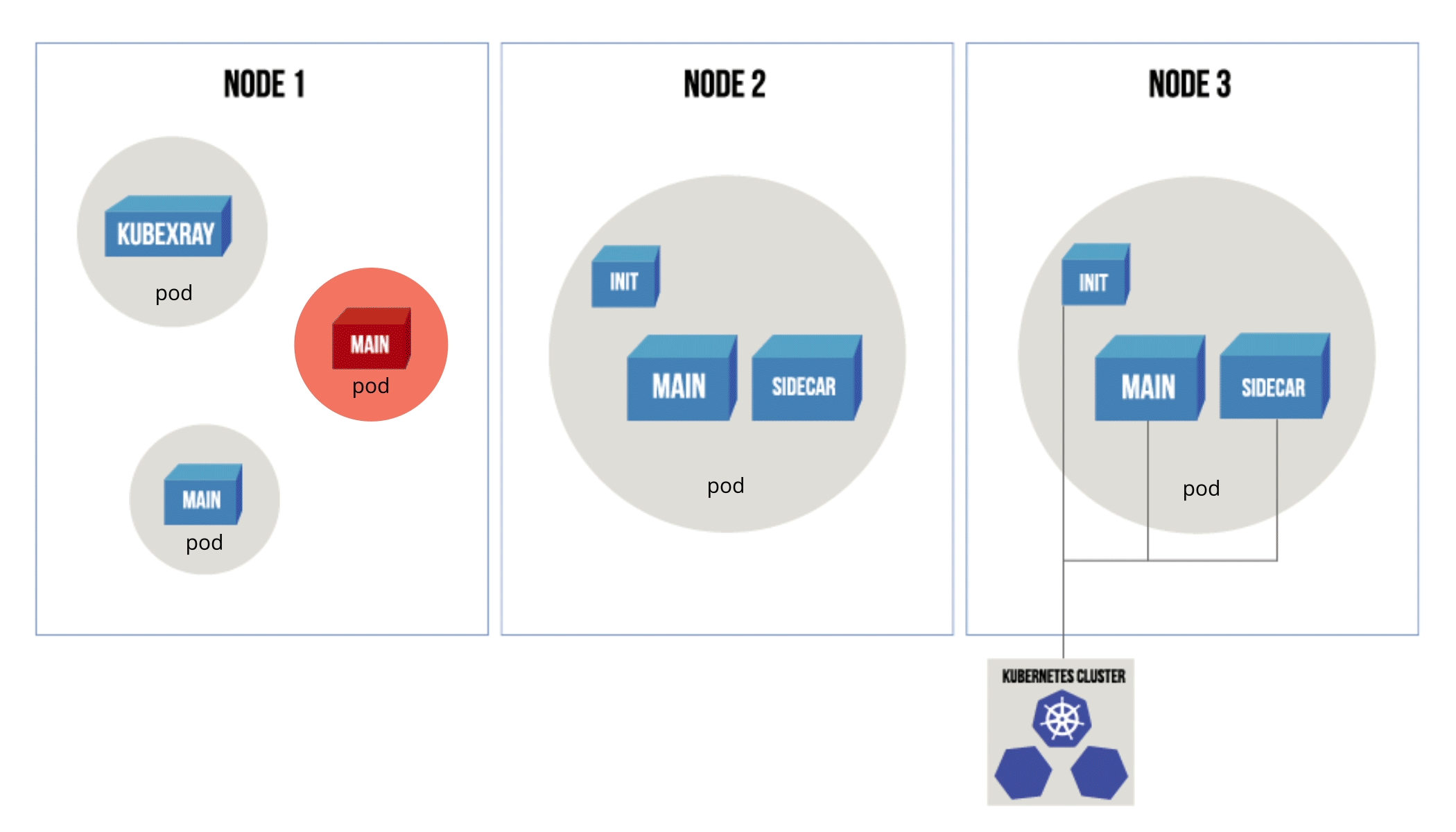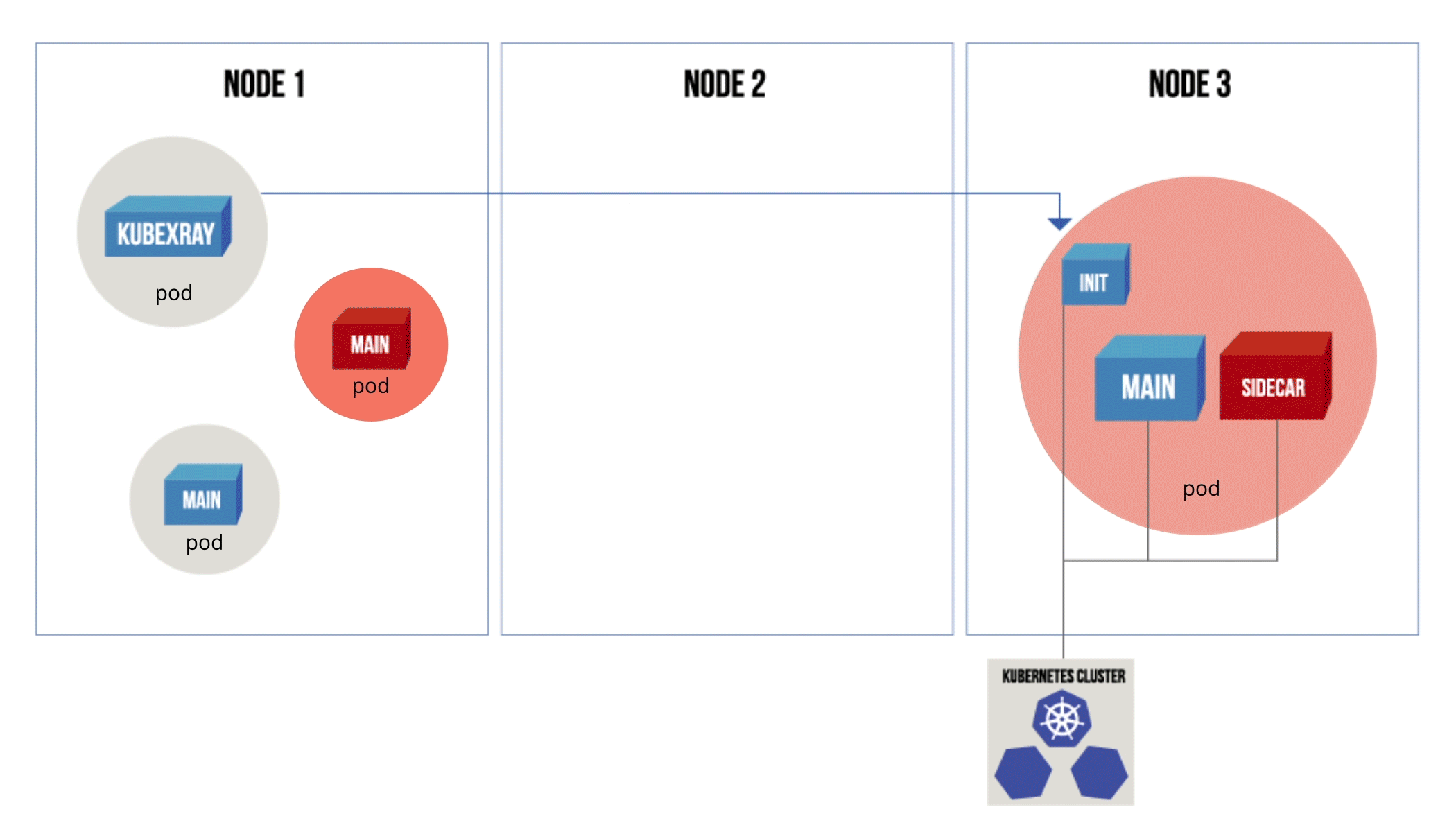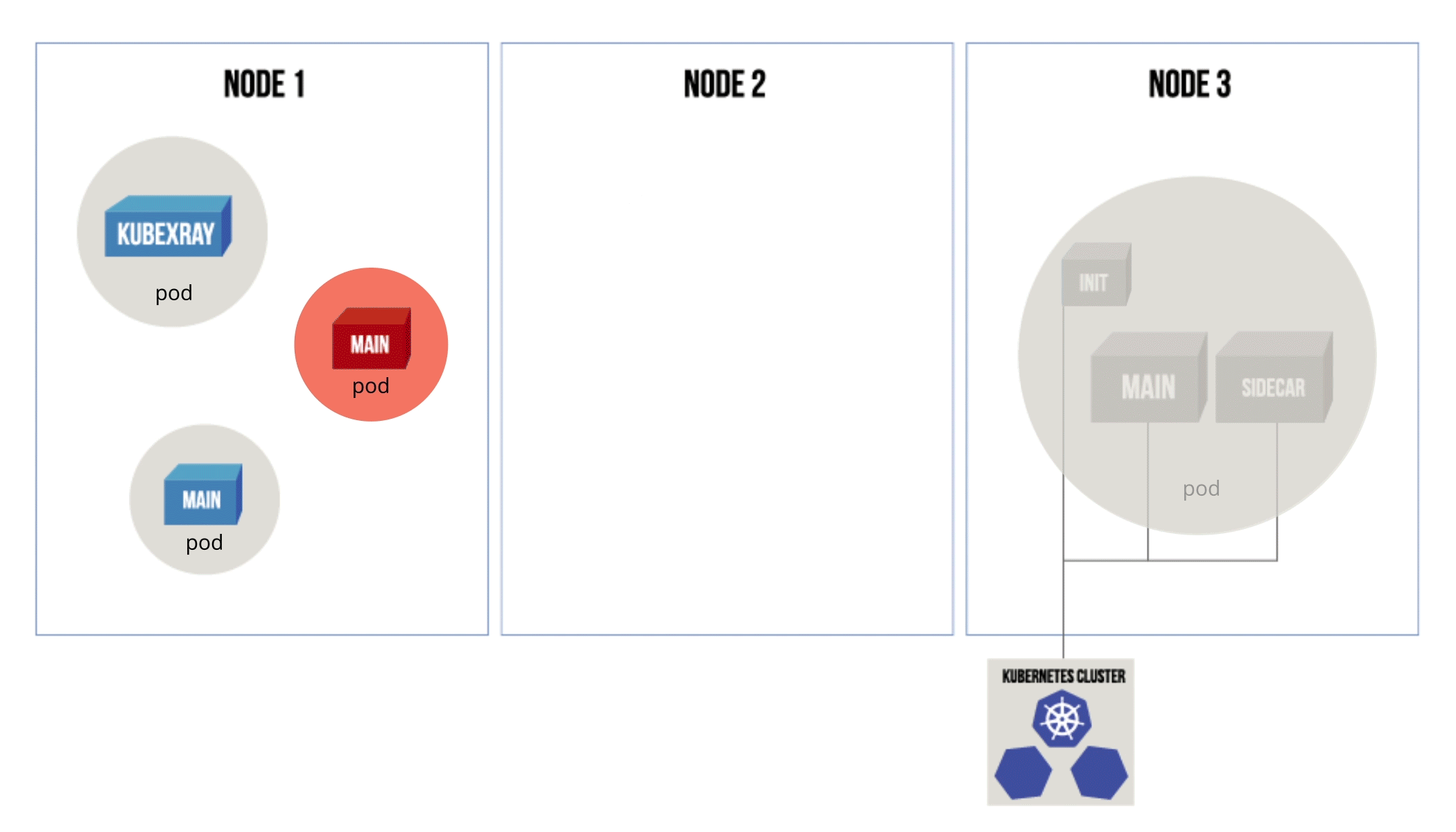
Figure 1: Diagram showing the effect of each policy action (ignore/delete/scaledown) on a vulnerable pod.
KubeXray applies the policy action according to the risks found and the policy as the DevOps administrator has configured it.
Policy actions are set In a values.yaml file. You can configure policy actions (scaledown, delete, or ignore) for the following conditions:
- Unscanned – deployments that have not been scanned by Xray. You can also specify a whitelist of namespaces; deployments that occupy these namespaces will have no policy action applied.
- Security – deployments that have security issues due to vulnerabilities.
- License – deployments whose licenses are out of policy compliance.
Each of the above conditions provides separate policy action settings for Deployments and StatefulSets.
Using KubeXray
The KubeXray tool is an open source software project that can be found in and installed from its Github repository.
To use KubeXray, you must have:
- A licensed and running copy of Artifactory
- A licensed and running copy of Xray
- A running Kubernetes cluster
- Kubectl installed and setup to use the cluster
- Helm installed and setup to use the cluster
Also, as part of your Xray installation, you must have an xray_config.yaml configuration file with properly configured Xray server connection settings.
A Helm chart provided in the JFrog Helm repository makes it easy to install or upgrade JFrog KubeXray into your running Kubernetes cluster. To custom configure your KubeXray installation, see the Read.me documentation.
Once you install KubeXray, you can set your policy actions in the values.yaml file for unscanned, security, and license conditions.
That’s all you need to get JFrog KubeXray monitoring your Kubernetes pods, and bring your security and licensing gremlins under control.
As an open source software project we look forward to continuing to enhance KubeXray for more robust operation and features, and to welcoming the developer community to making improvements.
Are you new to JFrog products? Use a free trial of Artifactory and free trial of Xray to give KubeXray a try.



