JFrog’s Advanced Security Scanners Discovered Thousands of Publicly Exposed API Tokens – And They’re Active
Read our full research report on InfoWorld
The JFrog Security Research team released the findings of a recent investigation wherein they uncovered thousands of publicly exposed, active API tokens. This was accomplished while the team tested the new Secrets Detection feature in the company’s JFrog Advanced Security solution, part of JFrog Xray.
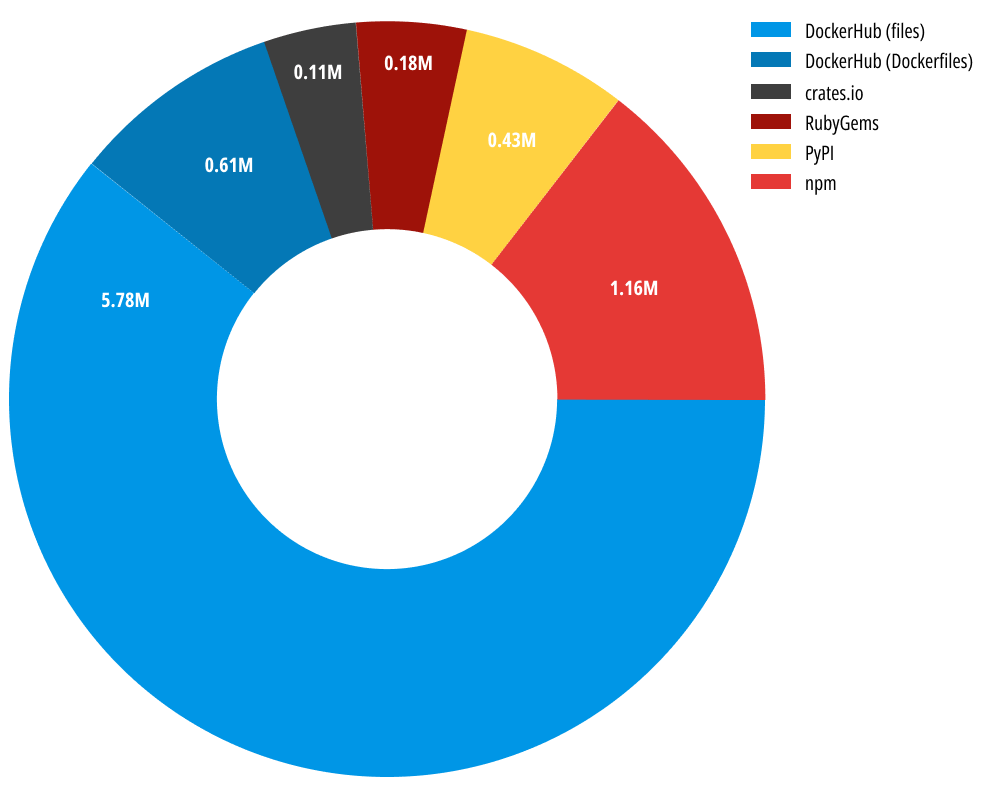
The team scanned more than eight million artifacts in the most common open-source software registries: npm, PyPI, RubyGems, crates.io & DockerHub (both Dockerfiles and small Docker layers). Each artifact was analyzed using the Secrets Detection scanners to find and verify leaked API tokens. For npm and PyPI packages, the scan also included multiple versions of the same package to try and find tokens that were once available but removed in a later version.
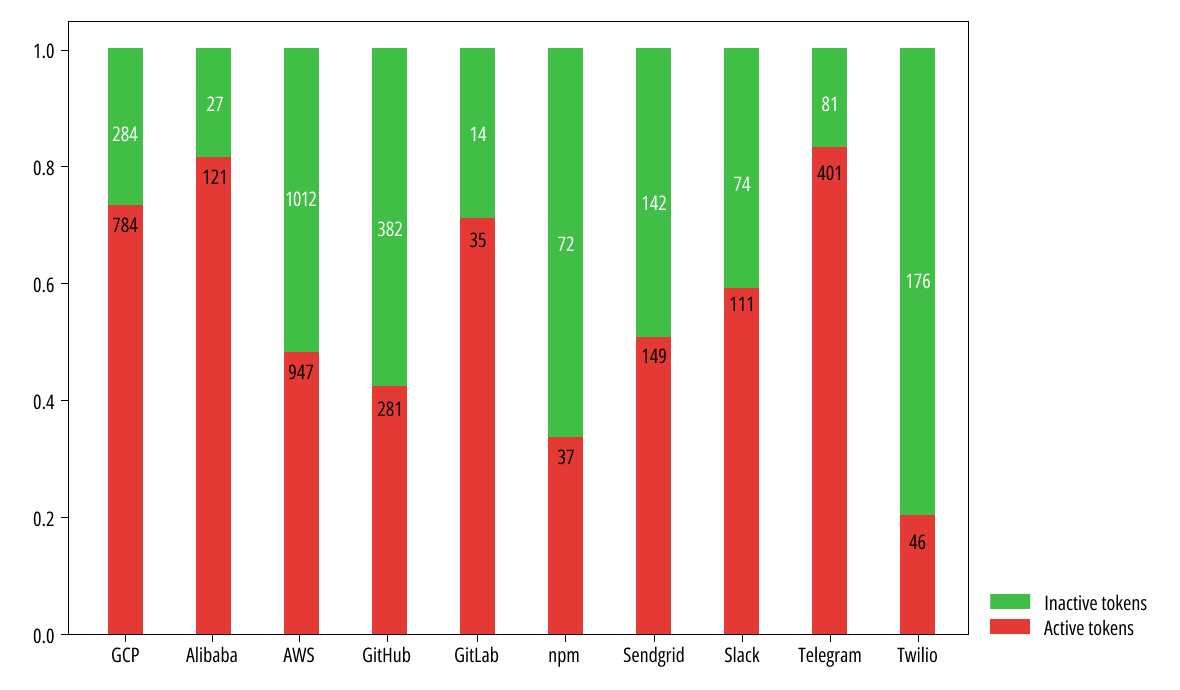
After scanning all supported token types by Secrets Detection and verifying the tokens dynamically, AWS, GCP, and Telegram, API tokens were the most leaked tokens (in that order). Interestingly, AWS developers seemed more vigilant about revoking unused tokens, with 47% of AWS tokens found active, unlike GCP, which boasts an active token rate of ~73%.
Although the initial goal of their research was to find and fix false positives using JFrog Advanced Security, the research team uncovered more active secrets than expected, which prompted the detailed analysis. To complete the analysis, the team privately disclosed all leaked secrets to their respective code owners (ones who could be identified), offering them a chance to replace or revoke the secrets as needed.
Secrets Detection uncovered disclosed secrets in the source code, like plaintext API keys, credentials, expired certificates, or passwords, often forgotten and left exposed unintentionally. These secrets threaten software’s integrity, allowing bad actors to access confidential information, data, or private networks.
Read the in-depth JFrog Security research findings and the five best practices they recommend for safely storing tokens in this InfoWorld article, and stay tuned for more examples of how the new features of JFrog Advanced Security can help safeguard your software supply chain.




