Helm Chart Security Mitigation: Talking Back to CVEs in ChartCenter

UPDATE: As of May 1, 2021 – ChartCenter central repository has been sunset and all features deprecated. For more information on the sunsetting of the centers read the Centers deprecation blog post
If your Helm charts could talk, what would they say to potential users? Would they boast of the power in the Kubernetes apps they deploy? Would they warn of their dangers? Would they offer advice?
In JFrog’s new ChartCenter, a community repository of publicly available Helm charts, that’s exactly what they’ll do. ChartCenter reveals to users what known risks lie within the container images deployed by every Helm chart.
JFrog ChartCenter can also help you advise users of your Helm chart about the importance of those risks or how best to mitigate them. It’s a great innovation of ChartCenter that we think all Helm chart authors should use — and you can help us to help you.
Vulnerabilities in Kubernetes Apps
Your K8s app only appears to be a single thing, like a Matryoshka, or nesting doll traditional in Russia. The Helm chart is the outermost shell of deployment configurations for the container images inside, appearing to be a solid entity. But that K8s Docker image within can contain many layers and dependencies. And each of those might carry its own hazards, unseeable from the outside.
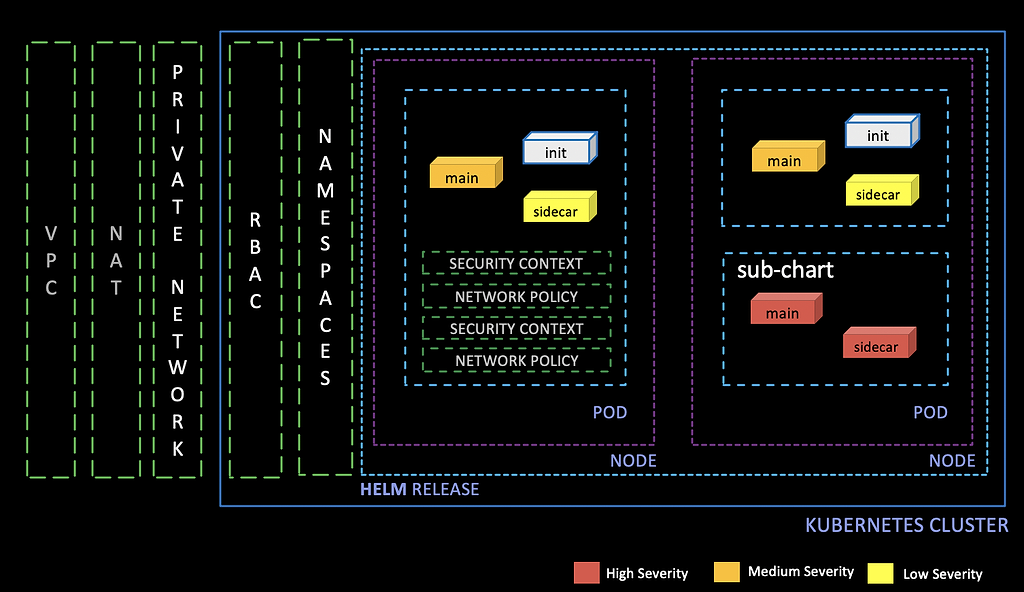
Yet many of these dangers are knowable, identified in the public Common Vulnerabilities and Exposures (CVE) list of the U.S. National Vulnerabilities Database (NVD). Maintained by the National Institute of Standards and Technology (NIST) since 2005, the free NVD is used by numerous cybersecurity products and services.
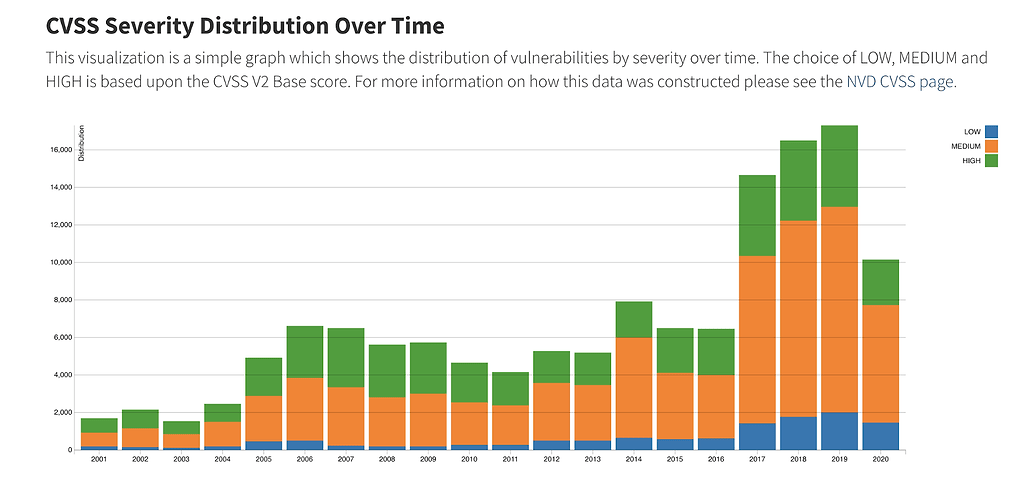
These risks aren’t declining, either. As open-source components become ever more available, number and severity of CVEs registered on NVD has grown dramatically:
How can you know which ones are in your Kubernetes app? That’s how JFrog ChartCenter can help.
ChartCenter Reveals CVEs
JFrog ChartCenter’s offers the community a rich UI to search among thousands of Kubernetes-ready packages across many public repositories. But ChartCenter is much more than a catalog. Powered by Artifactory, it’s a repository of Helm charts that holds immutable versions. So a user’s Helm CLI can pull all the public Helm charts they use from a free single source of truth.
ChartCenter also performs a vulnerability analysis of the entire set of a Helm chart’s dependent container images, powered by the deep-recursive scanning of JFrog Xray. The CVEs associated with those images are revealed in ChartCenter’s rich UI, so users can readily learn of and assess the security risks of any K8s app before they deploy it.
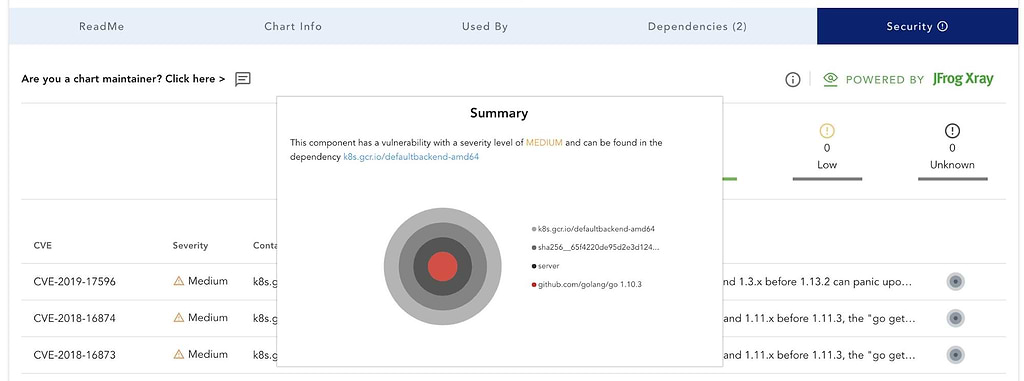
ChartCenter shows vulnerability details for medium, low, and unknown severity vulnerability by default, but we have chosen to give maintainers control over what level of detail they’d like to make available to the community for high-severity vulnerabilities.
Security Mitigation Notes
While it’s good for a user to know that a vulnerability exists in your K8s app, that might not be the whole story.
For example, a security risk in one dependency may be mitigated by the presence of another component. Or perhaps the vulnerable feature isn’t being used, so isn’t a threat. The problem might only occur in a narrow set of circumstances that aren’t relevant to your app. Or the danger may be able to be neutralized by a recommended configuration.
We believe that full transparency of your Helm chart means you should get your say, too. That’s why JFrog’s community engineering team has proposed a new specification for Helm chart security mitigation notes, and invites you to provide them.
To encourage your participation, ChartCenter will not display high severity vulnerabilities for a chart until mitigation notes with at least one high-severity CVE have been submitted to ChartCenter by a chart maintainer.
This enables Helm chart authors to annotate their charts with notes about the CVEs flagged by their dependencies, letting users know whether and when to be concerned, or if they can mitigate the risk. It helps you to say in response to a CVE, “Yes, but…” and engage in a type of dialogue with the users of your chart.
How to Annotate Your Helm Charts
To provide security mitigation notes, a Helm chart can include a security-mitigation.yaml file that can include any or all of the following information:
- Overall (summary) mitigation information for chart consumers
- Mitigation information for each CVE, for each affected package and version
- The URL for a mitigation website hosted externally on a wiki or webpage
- The URL for an externally hosted mitigation file
For example, the following security-mitigation.yaml file provides summary and individual CVE mitigation information for the Helm chart rimusz/security-sample-chart:
schemaVersion: v1
summary: Security mitigation information for this application is tracked by the security-mitigation.yaml file that's part of this Helm chart.
mitigations:
- cves:
- CVE-2019-1010022
affectedPackageUri: helm://rimusz/security-sample-chart
affectedVersions: <= 0.1.5
description: This security mitigation information for CVE-2019-10100 applies to the specified affectedVersions of charts.
- cves:
- CVE-2019-11888
affectedPackageUri: docker://docker.io/rimusz/security-sample-app
affectedVersions: <= 0.1.1
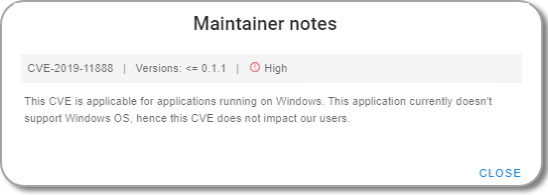
description: This CVE is applicable for applications running on Windows. This application currently doesn't support Windows OS, hence this CVE does not impact our users.
When you provide a mitigation notes file to ChartCenter with at least one high-severity CVE referenced, it will be included in ChartCenter and high-severity CVE information will be made available to chart consumers.
Once processed by ChartCenter, the referenced CVEs will indicate a mitigation note is available:
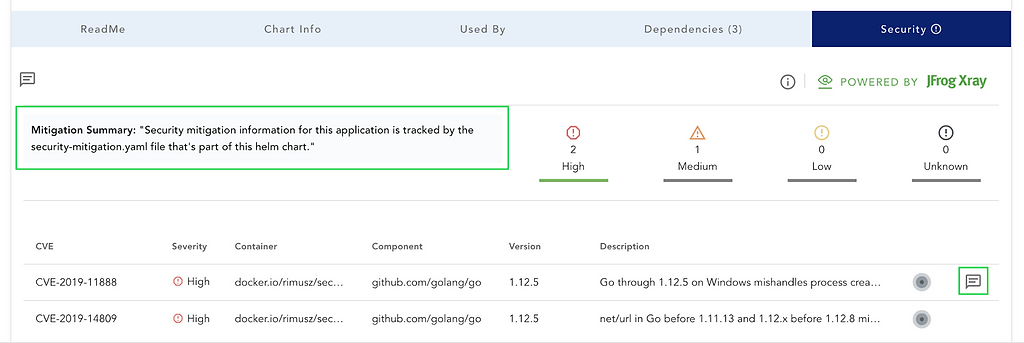
Click the icon to display the notes:
Keep Talking
This system of mitigation notes is a proposed standard, and still subject to revision, community feedback. For further technical details, see our specification on GitHub.
In the meantime, we invite you to give it a try, producing security-mitigation.yaml files for the public Helm charts you maintain! We welcome your feedback at chartcenter@jfrog.com.



