Adding Helm Chart Security Mitigation Notes to ChartCenter
UPDATE: As of May 1, 2021 – ChartCenter central repository has been sunset and all features deprecated. For more information on the sunsetting of the centers read the Centers deprecation blog post
Earlier this year, we launched ChartCenter, our newest community platform to help Kubernetes developers find Helm charts. This new free Helm central repository was built with chart immutability in mind— meaning every version of a Helm chart and every version in ChartCenter will always be available even if the original source goes down. Immutability becomes especially important as HelmHub became deprecated – many of the chart and versions that could be found there continue to exist on ChartCenter and each version includes a wealth of metadata around Helm chart dependencies, application version, Helm version, and how many other charts are using this version.
Among ChartCenter’s top features is free vulnerability information. For every chart version, ChartCenter uses JFrog Xray to scan for vulnerabilities, then calculates a CVE score of high, medium, low, and unknown using the CVSS 2 ratings.
Vulnerabilities Revealed in ChartCenter
The CVE (Common Vulnerabilities and Exposures) list is a public list of reported vulnerabilities sponsored by the Department of Homeland Security (DHS) Office of Cybersecurity and Information Assurance (OCSIA). Many cybersecurity companies use CVE as well as other more proprietary databases to help organizations have a clear understanding of their issues. CVE makes it easier to share information about known vulnerabilities across organizations by creating a standardized identifier for a given vulnerability or exposure. CVE enables organizations to set a baseline for evaluating the coverage of their security tools. CVE’s common identifiers help organizations to see what each tool covers and how appropriate they are for your organization.
By navigating to the security tab on each chart page, users can see vulnerability details including CVE ID, Description, Component, and Image where the issue is located.
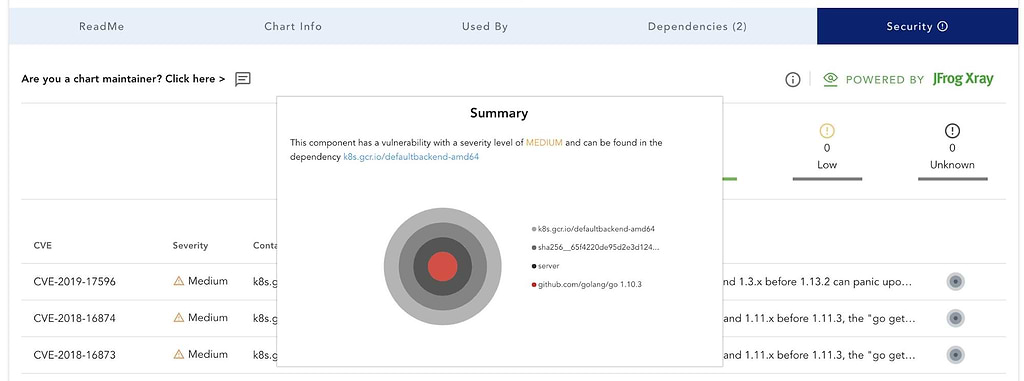
Mitigation Notes
As we tested this security feature, we got feedback from various community members that many of these vulnerabilities are in third-party components that the chart maintainer doesn’t have any control of and it would be better if we gave the maintainer the ability to provide some context to the end-user around which CVEs actually effect the application.
To strike the correct balance and give both chart maintainers and users tools to empower their decisions, we created a feature we call “Mitigation Notes”. While many tools such as ClaireOS and DockerHub also provide container scanning for free, JFrog’s ChartCenter was the first place to see it all easily in one view and have this information available on a UI that empowers users to see these issues through multiple versions of a chart. This made us realize that the right thing to do would be to give organizations some way to engage with users about the security of their charts.
This issue prompted us to build a new feature for Helm chart maintainers that would enable them to engage users directly on the ChartCenter UI. This solution would also need to continue providing transparency to the chart users about the security of the overall application. Getting this balance right has been an interesting adventure. We started by making all medium, low, and unknown CVE details continuously available to the public, but high vulnerability data can only be accessed once community users register and login to our center.
Providing Maintainer Notes
Providing your mitigation for CVEs can be done using a security-mitigation.yaml file. Once a user provides us this information, an icon appears next to each CVE on the security tab.
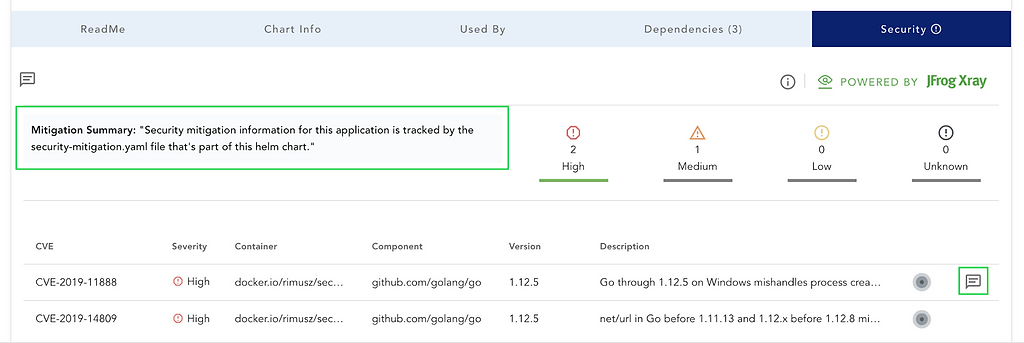
When you click the icon, you see a note like this:
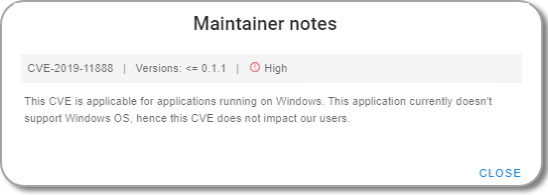
Mitigation and Advisory Examples
If you’re a developer who is new to providing this kind of advisory to users, just know that there are plenty of companies that can provide examples. Many of these companies have their own processes for mitigating security vulnerabilities in their code and sometimes they build a dedicated page or portal on their sites to make this information available. Below are examples of businesses that have company-standard mitigation advisories in place to handle security risks and a brief overview of their policies. These examples could be used for your own security mitigation.
Drupal: Drupal’s Security team manages security advisory public announcements to inform site owners about a reported security issue in Drupal core or a contributed project. Their advisory also provides developers steps needed to remediate the issue. Learn more about Drupal’s security advisory process.
Microsoft: Microsoft has an exploitability index: Microsoft evaluates the potential exploitability of each vulnerability of Important or critical severity associated with a Microsoft security update and then publishes the exploitability information as part of the monthly Microsoft security update details. If after publishing the details Microsoft determines that the Exploitability Index Assessment warrants a change, it will change the assessment and notify customers through technical security notifications. You can see what this looks like in this example.
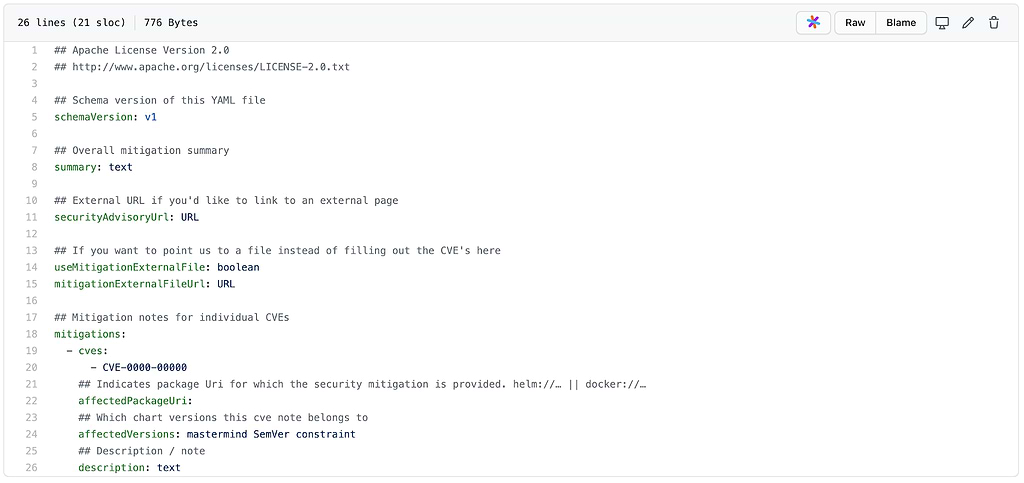
ChartCenter Mitigation YAML
Once the YAML file is filled out, you can include the file in the next version of your Helm chart and we’ll add your mitigation notes to the ChartCenter UI. Alternatively, you can email us your security-mitigation.yaml file directly as long as you can verify that you are the owner of the Helm Chart (i.e. your email is included in the repository info for the chart).
The security mitigation spec supports 3 use cases:
- Ability for producers to provide overall and/or CVE specific mitigation information.
- Ability for producers to point security to a mitigation website that is hosted externally on a wiki or webpage.
- Ability for producers to point to externally hosted
security-mitigation.yamlfile.
| Field | Description | Type |
summary |
Overall mitigation summary that applies to all chart versions | text |
securityAdvisoryUrl |
Link pointing to a mitigation information hosted externally such as wiki, web page, etc. | url |
useMitigationExternalFile |
true means security-mitigation.yaml is hosted somewhere else. false means the content of the current file represents security mitigation information. Default value: false |
true/false |
mitigationExternalFileUrl |
If set to true, then this parameter points to a url of externally hosted security-mitigation.yaml |
url |
mitigations: cves |
List of CVEs for which mitigation notes are being provided. | CVE-YYYY-NNNN |
mitigations: cves: affectedPackageUri |
Indicates package Uri for which the security mitigation is provided. Currently we support only two package uri:
Docker |
uri |
mitigations: cves: affectedVersions |
SemVer Constraint from Masterminds/semver as used on Chart.yaml for kubeVersion specifying which versions should use the mitigation information. |
Example: “> 1.2.x |
mitigations: cves: description |
Mitigation notes at CVE level. | text description |
Next Steps
If you are a Chart Maintainer, learn more about how you can activate the mitigation notes feature in our UI. Then fill out the security-mitigation.yaml file. For any additional question, please email us at chartcenter@jfrog.com.




