Announcing JFrog SAST: Build Trust and Release Code With Confidence
Trusted builds need trusted code.
Today’s software applications power almost every aspect of our lives, and ensuring the security of these applications is paramount. Threat actors can cause devastating consequences for companies, leading to financial losses, reputational damage, and legal repercussions. Companies building commercial or in-house applications must adopt robust security measures throughout their software development lifecycle to avoid releasing vulnerable code.
One primary instrument in the application security arsenal is Static Application Security Testing (SAST). In this blog, we’ll delve into what SAST is, why companies need to use it, and how JFrog SAST can help modern software builders eliminate the threats often lurking in their proprietary source code.
SAST drives efficiency and quick releases
Early Detection of Coding Vulnerabilities: Allows organizations to detect security vulnerabilities in their codebase early in development. This proactive approach helps developers fix issues before they make their way into the final product, reducing the cost and effort required to remediate vulnerabilities in later stages.
Reduced Attack Surface: Identifying and eliminating code vulnerabilities with SAST reduces the potential attack surface for malicious hackers, making it more difficult for them to exploit weaknesses in production.
Audit Compliance and Regulations: Many industries are subject to strict audits and regulatory requirements involving data security and privacy. SAST aids in achieving compliance by identifying vulnerabilities that could lead to violations of these regulations.
Cost-Efficiency: Fixing code security vulnerabilities after the software has been promoted through the CI/CD pipeline or deployed can be significantly more expensive than addressing them during development. SAST cuts down these costs by identifying and rectifying vulnerabilities in the early stages of development.
Reputation Protection: A data breach or a security incident can severely damage a company’s reputation. By implementing SAST, organizations demonstrate their commitment to security, which can bolster customer trust and loyalty.
Introducing JFrog SAST
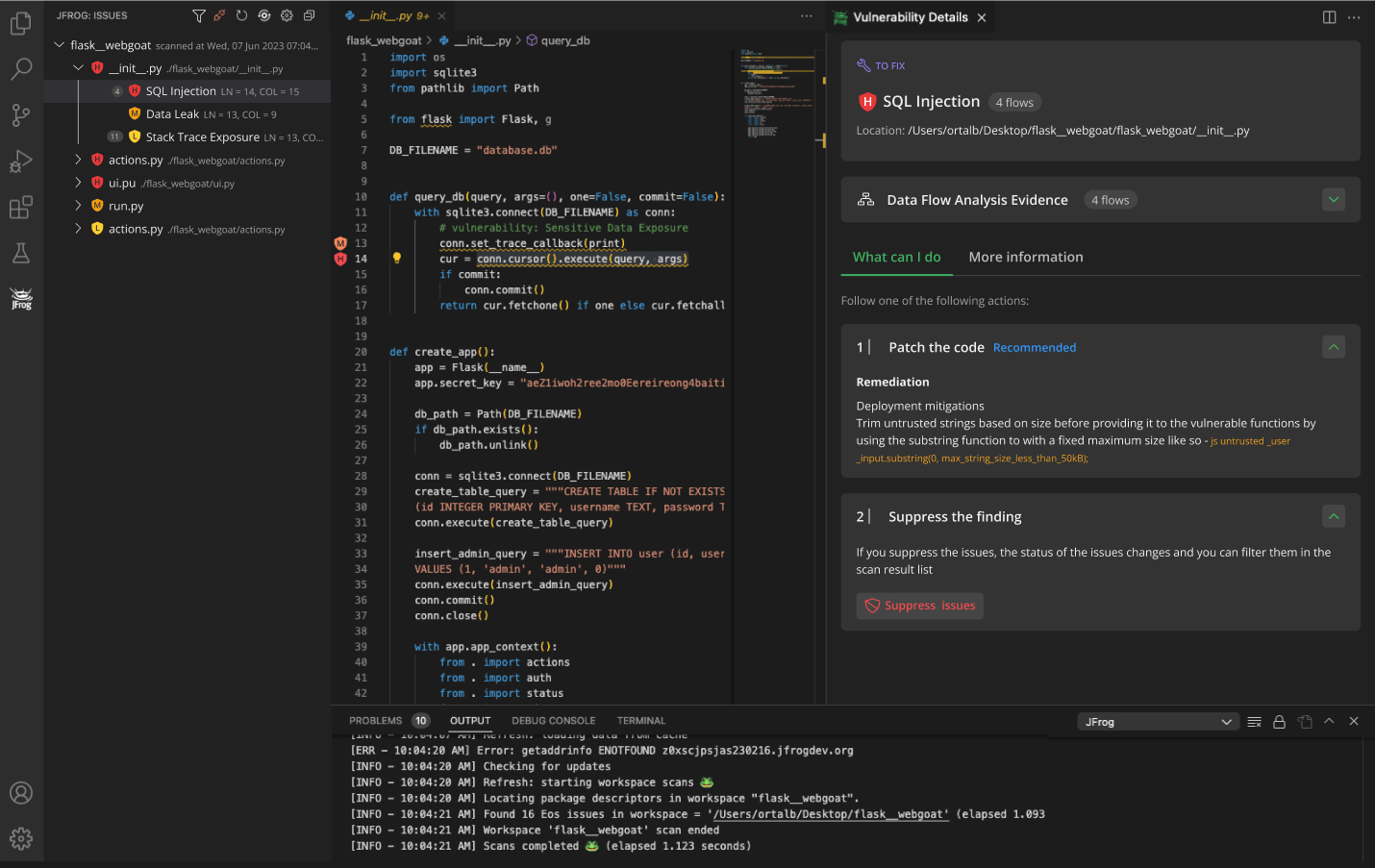
Organizations look to innovate fast and maintain the trust of their builds and releases. They need a source code scanning solution that ensures their developers can commit secure code without slowing down the software development momentum.JFrog SAST enables development teams to write trusted code with a seamless developer-focused experience. Fast and accurate security-focused engines deliver scans that detect 1st party code zero-day security vulnerabilities while minimizing false positives. Avoid slowing down development teams and use a modern and efficient static code analysis solution.
Fast and Accurate for Optimized Development
Seamless Shift Left Developer Focused Experience
Efficiently Find and Fix Source Code Vulnerabilities
Centralized Visibility and Governance
Manage SAST rules and policies centrally, knowing they’ll be applied across development teams seamlessly at scale. Be assured that your development teams utilize code security scanning across the SDLC from code to production.
Conclusion
To truly protect themselves in the ever-evolving landscape of cyber threats, organizations must integrate robust code security practices into their software development processes. SAST offers a proactive approach to identifying vulnerabilities in 1st party code within the early stages of development, reducing costs, ensuring compliance, and safeguarding a company’s reputation.
Legacy SAST solutions limit modern developers, as they are slow to scan, take a lot of time to integrate, and are often inaccurate resulting in many false positives. These false alarms lower developer trust, and often require security expertise to intervene, increasing costs and slowing development velocity.
JFrog SAST is built for the modern developer and eliminates threats like injection attacks, insecure authentication, and code vulnerabilities to create secure and trustworthy binaries (builds and releases). Embracing source code scanning is not just a best practice; it’s a requirement in today’s application security world. JFrog SAST provides developers with a frictionless experience, improving their efficiency and ultimately accelerating the pace of software development.
JFrog SAST is now available as part of the JFrog Software Supply Chain Platform. We invite you to experience how fast and accurate elimination of source code security threats and helps you ship more secure software, faster.
Want to learn more about JFrog SAST?
Sign up for a personalized demo or trial or you can join rewatch the live webinar from October 10th – where we’ll walk you through the SAST features and benefits and show you first-hand how you can easily take advantage of this simple yet effective source code-scanning solution.






