What’s New with JFrog Artifactory and Xray
TL;DR
Get the latest on self-hosted Docker rate limits, cutting through violation noise and new package type support.
Without doubt, 2020 has been one of the most challenging years for everyone in recent history, but especially for those in the world of DevOps. JFrog has strived to continue developing and innovating at the same pace, to give our customers an even better end-to-end DevOps experience, and help customers maintain their drum-beat of on-time releases.
Let’s take a closer look at some of the new features we’ve recently introduced in the JFrog Platform.
Docker rate limits for self-hosted users
As you are probably aware, Docker announced new consumption-based limits on container images pulled from Docker Hub. Specifically, anonymous free users are limited to 100 pulls per six hours, and authenticated free users to 200 pulls per six hours.
JFrog’s partnership with Docker ensures that cloud users of the JFrog DevOps Platform, including those who use the free subscription (available on AWS, GCP, and Azure), won’t face Docker Hub image-pull limits.
Docker Registry functionailty is now optimized in JFrog Artifactory to accommodate the latest rate limit changes announced by Docker by optimizing the following features:
- Use of HEAD requests
- New Default Retrieval Cache Period
- Enhanced Logging and Messaging
- Use of the Digest Header (Docker Content Digest)
Take action on license violations and vulnerabilities
JFrog Xray reports enables you to easily triage and take action on the results of Xray scans of your open source packages, builds and artifacts. Each report provides a snapshot of your OSS risk from a particular point-in-time, and displays information in a visually insightful way.
The scope of a report can be configured by filtering by vulnerable components, impacted artifacts, scan dates, CVE ID or CVSS severity score. For remediation purposes, you can also configure reports to display ‘all vulnerabilities’, ‘ones with a fix’ or ‘doesn’t have a fix’.
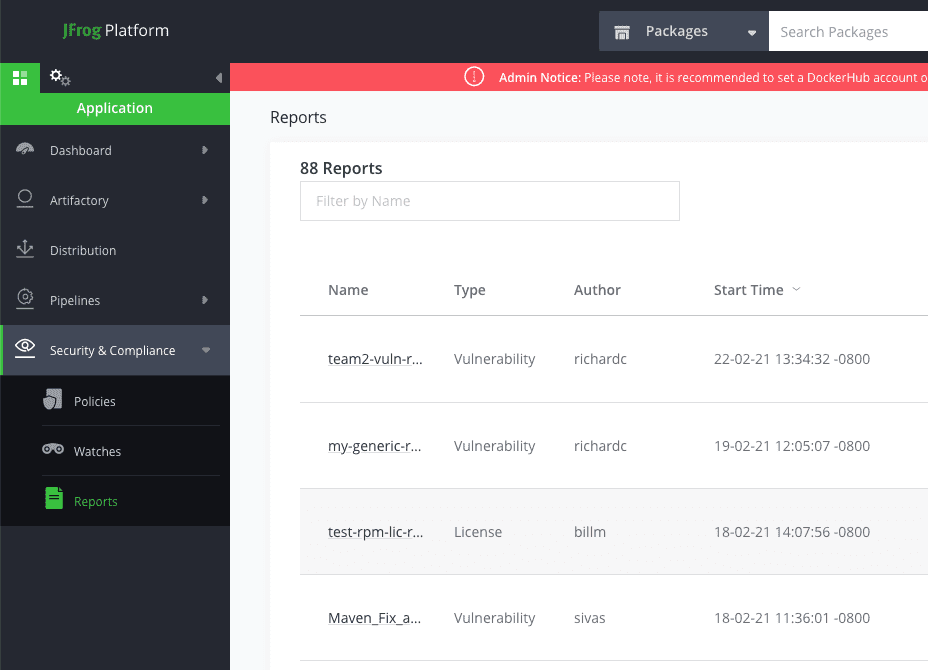
JFrog Xray Reports
Types of reports
The different available reports include:
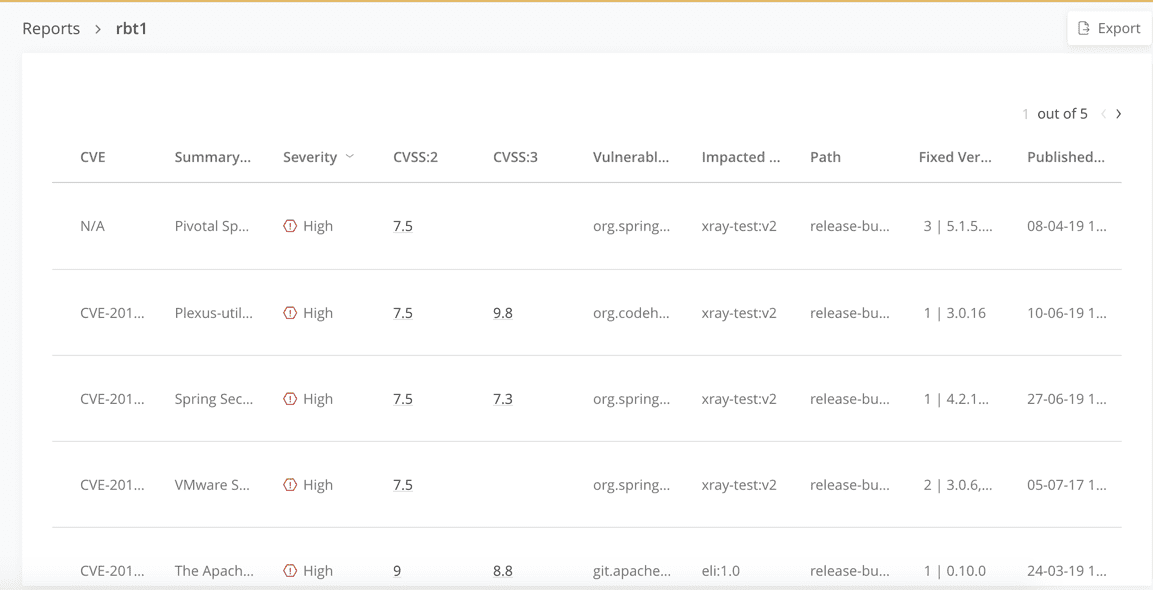
- Vulnerabilities Report, JFrog Xray provides vulnerability scanning of your artifacts, builds, and software distribution (release bundles), as well as criteria such as the vulnerable component, CVE record, CVSS score, and severity.
- License Due Diligence Report, provides all of your components and artifacts, with their relevant software licenses, enabling you to verify that the components and artifacts you’re using comply with your corporate license guidelines. It lists all of the license types associated with each component, as well as unknown and unrecognized licenses.
- Violations Report, provides you with information on security and license violations for each component found in the selected scope. Including the type of violation, impacted components and artifacts, and severity. Its scope is also defined with advanced filters.
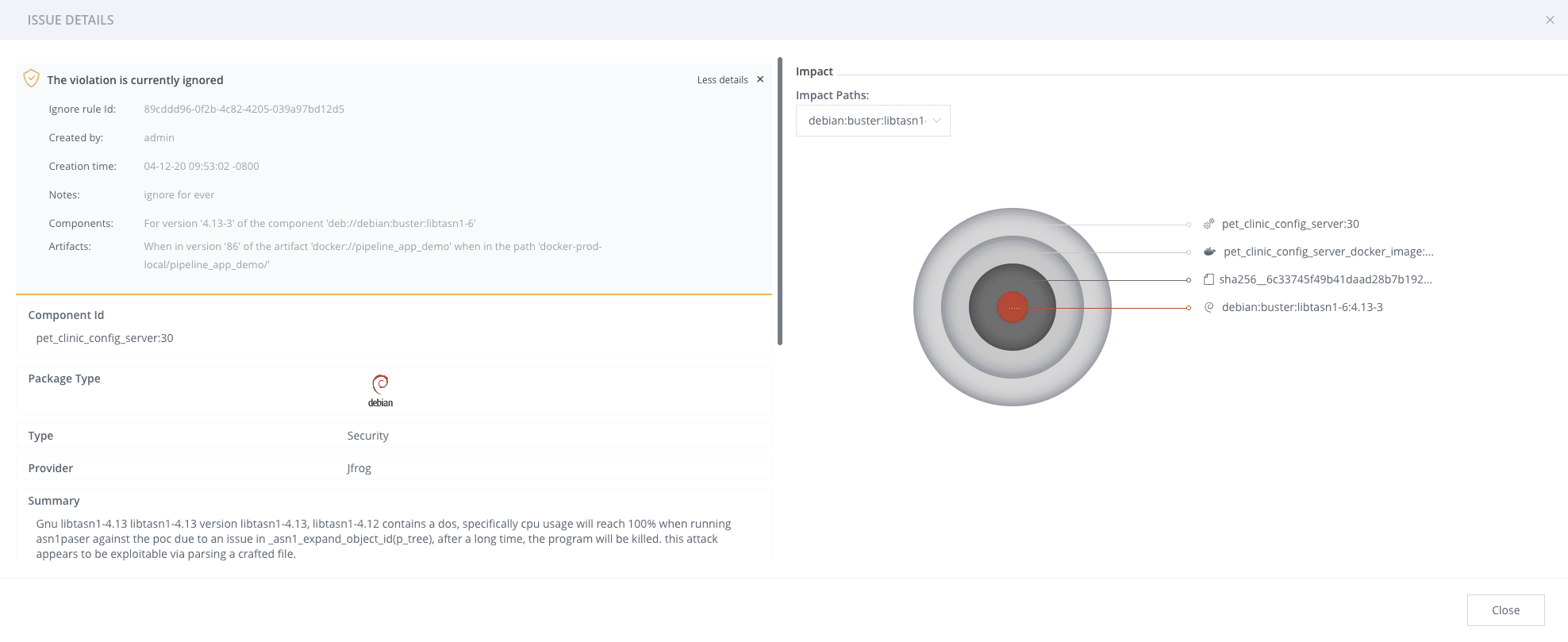
One of the unique features of Xray reports is the impact path of a vulnerable component. A component can appear in multiple places within a build image or in multiple builds. Xray will show you all places where a vulnerable component is impacting your software.
Vulnerabilities Report Example
Permission management for reports
A new permissions role has been added to the JFrog Platform to support this new functionality. It enables permission restrictions on who can create, edit and share reports, and can be assigned at an individual user or group team level.
Manage security violation noise
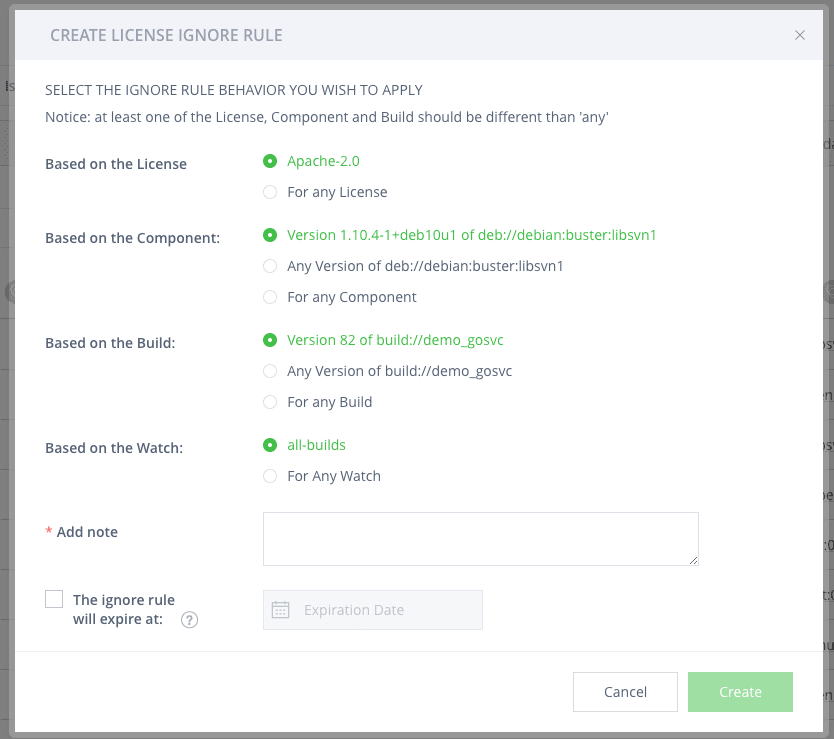
JFrog Xray ignore rules allows you to whitelist, ignore or accept security violation rules, in order to filter out unwanted violation noise. The rules can be approved to be ignored by different teams and users for reasons such as:
- You’re aware of the vulnerability and can protect against it.
- Your environment doesn’t meet the requirements for this violation.
- That vulnerability is not a show stopper and you’ll handle it later.
- Stop unimportant violations to fail your build or block downloads.
Setting up an ignore rule in JFrog Xray
Granularity of ignore rules
The Ignore Rules feature offers you broad flexibility and granularity, allowing you to ignore violations based on vulnerability/license, component, artifact or watch. As such, you can get very specific about what you want to ignore. For example, this can be set to a specific component, a specific license or a specific component version number.
Time-based ignore
Ignore rules can be set up to run for a certain period of time, meaning, for example, that you can ignore certain violations for 3 weeks while you ramp up development, after which they will again be enforced.
Set policies to act with a permissive approach
This means that if a component with multiple licenses has one license that fails to comply with a policy rule, but it has at least one other permitted license type, it will go through the scan without triggering a violation.
Alpine Package Technology Support

OCI Image Support

RubyGems Bundler Support

Helm V3 Support

Whether you’re developing cloud-native applications on a public cloud or you’re operating your own self-hosted DevOps infrastructure; you can benefit from these recent enhancements to the JFrog Platform to utilize new package technologies, minimize your risks and costs of using Docker Hub, as well as secure your software releases by detecting and managing vulnerabilities and license violations with JFrog Xray.
Try these new features in JFrog Artifactory and Xray, for free, Self-Hosted > or in the Cloud >