Leveraging Shift Left and Shift Right for End-To-End Application Security
Despite organizations’ best efforts, security threats are on the rise, with malicious actors continuously evolving their tactics. Unfortunately, the situation is only intensifying as hackers from all walks of life leverage artificial intelligence (AI) and machine learning (ML) techniques.
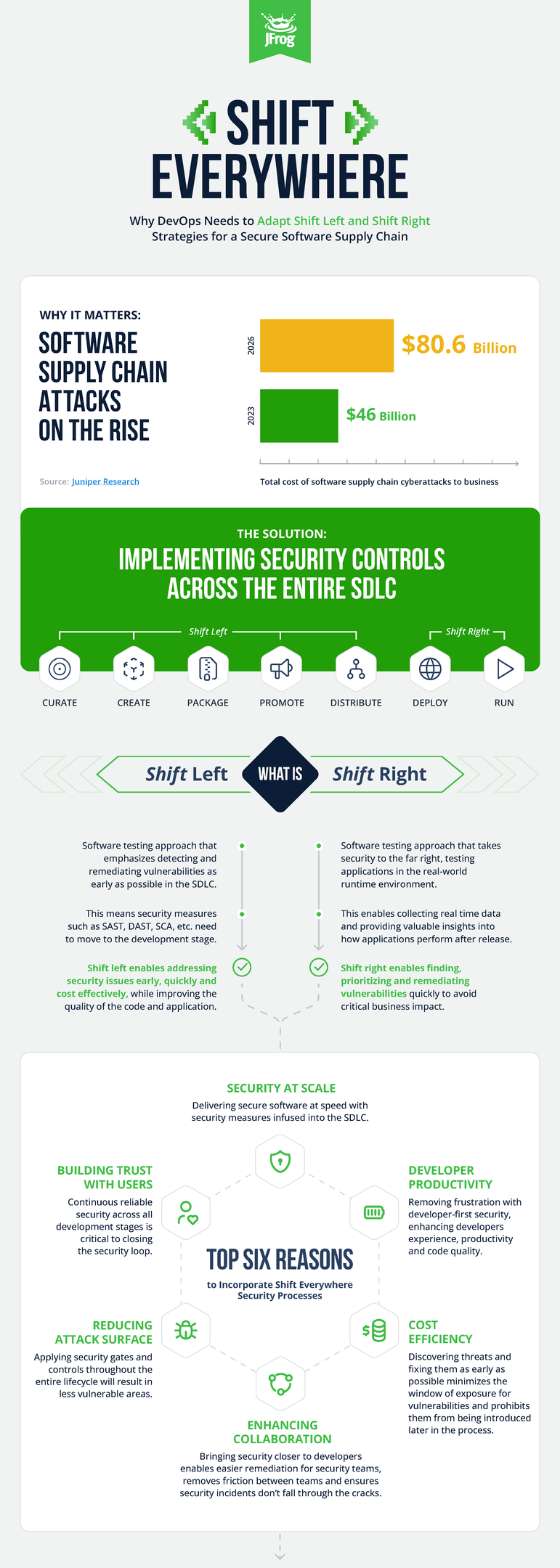
To combat these threats, security teams need to implement gates and controls throughout their entire software development lifecycle. True end-to-end security involves adopting a combination of both proactive (shift left) and reactive (shift right) approaches to secure applications at every stage of development.
While the concept of shift left is more widely known, it’s also evolving. Generative AI tools like Copilot are being used more heavily by developers to help them write more code, faster, and more securely. Alternatively, shift right involves protecting the production environment, which depending on your deployment strategy, can include containerized applications and cloud-native deployments.
For more on this topic, download our eBook: Shift Left and Right: The Key to Securing Your Software Supply Chain End-to-End.
Download the eBookWhat is shift-right security?
Shifting security testing to the right focuses on the continuous testing of applications running in a production environment, establishing ongoing security checks, and preventing vulnerabilities that were detected after deployment from being included in the next update. While the concept of shift-left security is more well-known, shift-right security is of equal importance when it comes to protecting the software supply chain, end-to-end.
It specifically emphasizes security measures during the runtime and deployment phases, aiming to improve the user experience and make sure there aren’t any issues before software updates are released. This involves monitoring production environments, detecting and responding to security incidents, and continuously improving the security of their software based on real-world feedback. Shift-right security acknowledges that vulnerabilities may remain or emerge in production environments, expanding the attack surface to include issues like misconfigurations, vulnerable container images, and runtime exploits.
What is shift-left security?
On the other hand, the concept of shifting security to the left involves integrating security practices early in the development lifecycle, reducing the likelihood of introducing vulnerabilities into your development environment. Representing the leftmost edge, software developers drive shift-left security through secure coding practices by preventing insecure code from getting compiled into a software binary.
The goal is to minimize the attack surface by preventing vulnerabilities early on, such as risky coding practices and authentication weaknesses. Finding and fixing bugs early on in the process also reduces the costs and complications associated with remediation.
Shift-left vs. shift-right
Shift-left and shift-right security are two distinct approaches that integrate security practices at different stages of the software development lifecycle. Shift-right takes your security practices all the way through the production environment and into runtime, while shift-right covers the earlier parts of the process.
While shift-left security practices catch issues early, shift-right testing provides critical protection for deployment and the runtime environment, making sure the application works as intended under all circumstances. Embracing both shift-left and shift-right approaches is the most effective strategy for securing the software supply chain.
Securing the software development lifecycle end-to-end
The software development lifecycle (SDLC) is a framework outlining an efficient process for all stages of software development, including cost and time considerations. Throughout the various stages of software development, new vulnerabilities can emerge, making it essential to implement continuous security measures. Applying security practices across the entire SDLC helps mitigate risks and ensures that software releases are both efficient and safe.
Next steps
The increasing security threats to organizations’ software supply chain are a pressing concern, especially with the advancements in artificial intelligence and machine learning. To address this issue, it’s critical to implement comprehensive security controls throughout the software development lifecycle. This entails adopting a proactive shift-left approach as well as a reactive shift-right approach. By combining these approaches to security, organizations can effectively safeguard their applications at every stage of development.
For more information about how to apply a shift-left and shift-right approach to software supply chain security, check out our ebook. Or, for something a bit more condensed, check out the infographic: Shift Everywhere.