Pyrsia: Decentralized Package Network that Secures the Open Source Supply Chain
Accelerate how you build, share, and consume open-source packages
State of Supply Chain Security
Supply chain security has received a lot of attention in recent years. And rightly so. Software vulnerability exploitation attacks have been a key tool in the hands of the hackers to hamper businesses, compromise sensitive data, and a cause of general sense of fear around open source software.
Many of these attacks have manifested because of weak practices that rely on outdated tools and human interventions. At best, the teams tasked with protecting the business software are left to deal with attacks on their systems via some vulnerability exploits in open source software – equifax apache struts, Log4j and the Solarwinds Hack are a few well known examples. In reality there are many more that do not get so much attention, but still end up causing a lot of damage to businesses and people.
At JFrog we recognize that improving the security and trust of open source software is critical for securing our software development and supply chain. This is the main reason Pyrsia was established. Pyrsia is a decentralized package network that provides a solution for a key part of the supply chain by:
- Building trust for the open-source packages being used as dependencies in software development through certified and peer-verified builds.
- Providing a decentralized package network that understands package coordinates, semantics, and discoverability, and which continues to work even though there are local outages.
If the open-source supply chain was compared to an electric power delivery system, it would be analogous to the power grid that supplies distributed electricity to consumers and businesses worldwide. Individuals, small businesses, and enterprises all depend upon reliable delivery of clean power from upstream production sources. The distributed nature of the power grid makes it possible to have a reliable source of power that efficiently distributes electricity production. Without this critical infrastructure it would be impossible to keep production working globally.
Similarly, open-source software plays an essential role in the supply chain of modern software development. Proprietary software is typically composed of 90% or more open-source dependencies, with heavy usage on packages provided from one or more central repositories including Maven Central, PyPI, RubyGems, NPM, Docker Hub and others. Outages in these upstream repositories have the potential to produce disruptions in the software supply chain that range from developer productivity to CI/CD build failures to interruption of production releases. Worse yet, security issues in central repositories can have a devastating impact on downstream systems, especially where malicious packages have been injected.
Pyrsia aims to secure the software supply chain of open-source dependencies by creating a system that secures open-source builds and distribution by design.
Establishing and Verifying Trust in Packages
Today, trust in packages is based on the service(s) that built and/or host those packages. Whenever such a service goes down or is attacked it makes the entire network downstream unstable. Either you cannot continue to build and release software or have the risk of systems with the compromised packages. We trust the service provider to fix and provide secure packages. The provenance and validity of packages is not verifiable by a third party and identifying vulnerable packages is a manual process. Our security vulnerability team at JFrog has identified thousands of malicious packages showing that this model is easy to exploit.
Pyrsia solves this problem by applying automation to both building and verifying trust in the packages hosted and produced on the network. Pyrsia also aims to provide resilience which prevents developers from losing productivity and downstream failures in CI/CD systems that delay software releases.
Pyrsia consensus – how does it work?
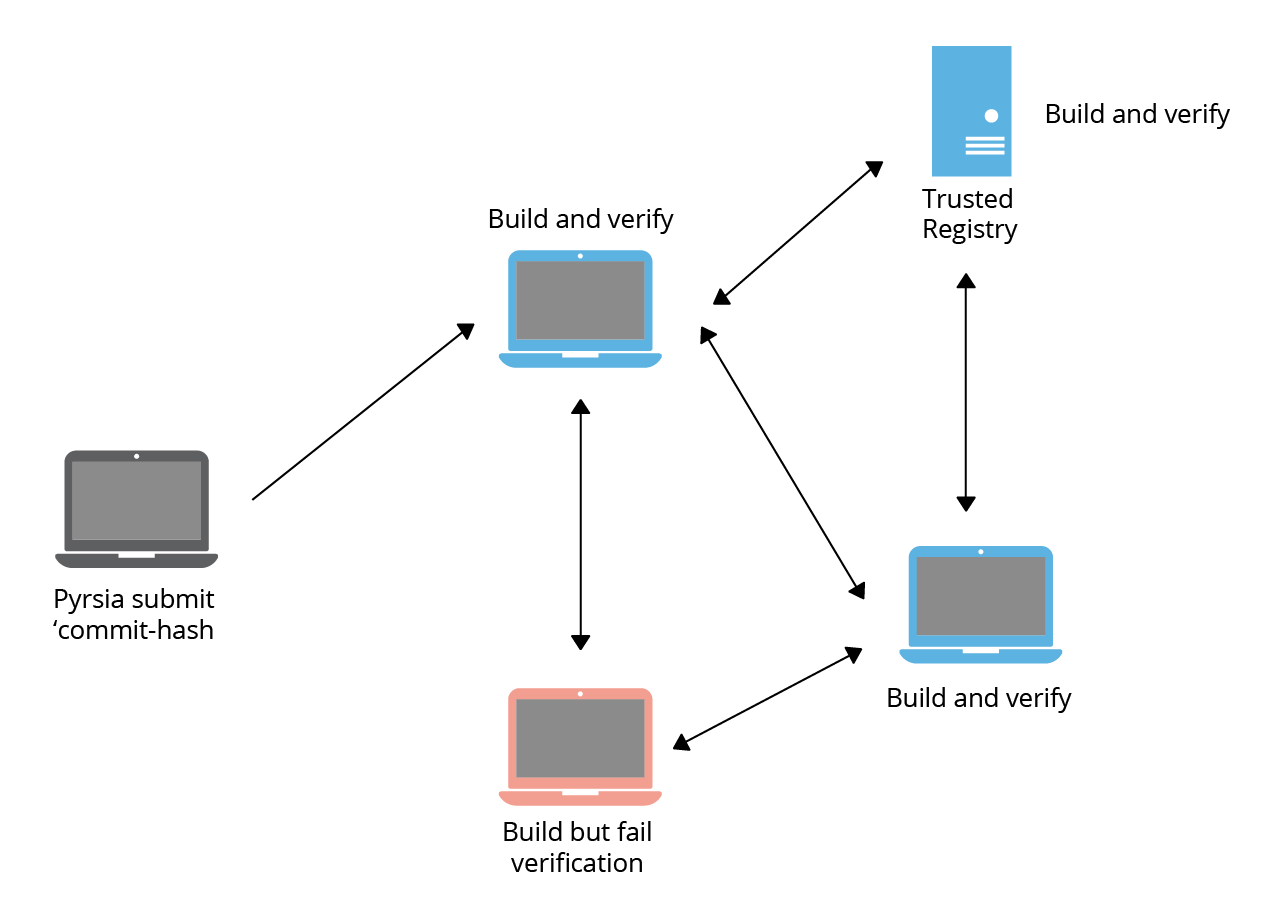
The Pyrsia network works on random consensus across the network. Each package submitted to the network gets built by a random selection of nodes which build and produce the output package independently. The result is then verified by consensus among these nodes. If the verification succeeds the package is then committed to the network and available to be downloaded and deployed.
Random selection allows independent verification of builds and also provides a safety net against network attacks.
The Goals of Pyrsia
- Focused on building and distributing open source codebases – source code must be available and accessible at a public location
- Easy to install and use Pyrsia software with a first-class command line interface that enables developers to gain the benefits of Pyrsia without the need to rewrite existing scripts, docker files etc.
- Efficient usage of resources for running Pyrsia nodes where contributors are able to dedicate resources to the network based on their constraints
- Ability to work offline where dependencies have been previously synchronized and cached locally
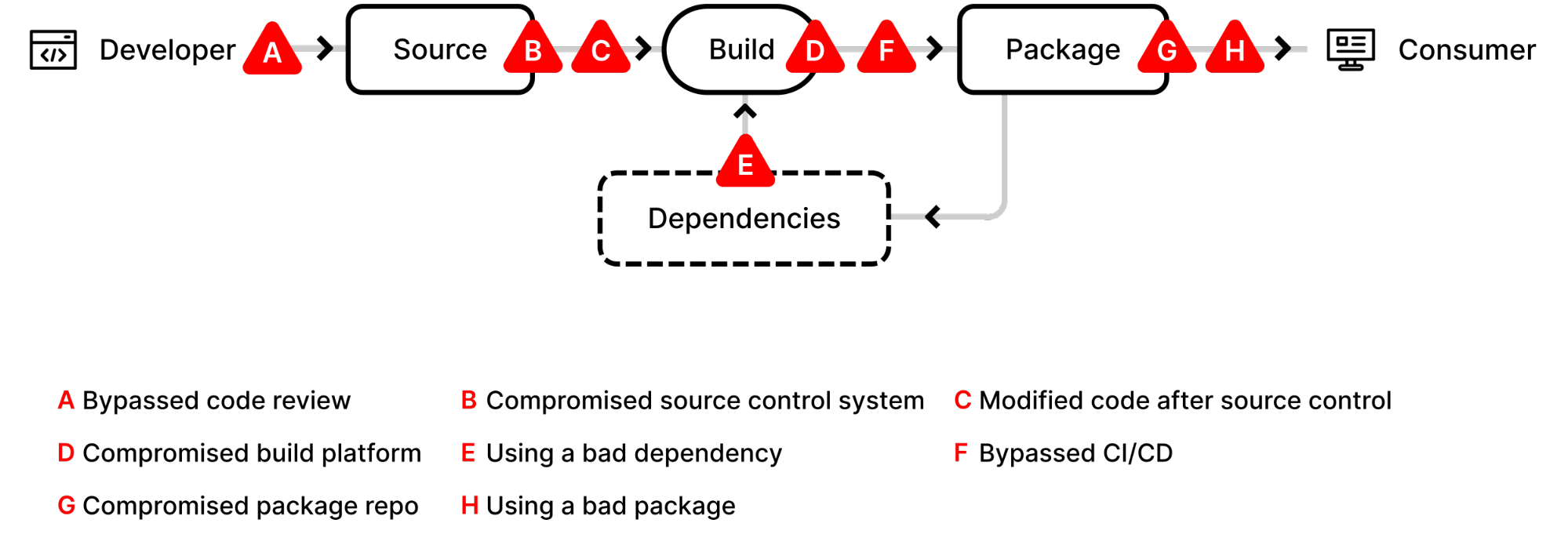
- Pyrsia addresses the following supply chain threats for all open source software as shown in the diagram below.
- C- Modified code after Source Control
- D – Compromised Build Platform
- E – Using a Bad Dependency
- F – Bypassed CI/CD
- G – Compromised Package Repo
- H – Using a bad package
Pyrsia does not attempt to:
- Re-invent technologies and software that already exist in other open-source projects.
- Invest in security research on signature technology to sign software packages.
- Support Pyrsia-like functionality for closed source projects.
How can I use Pyrsia today?
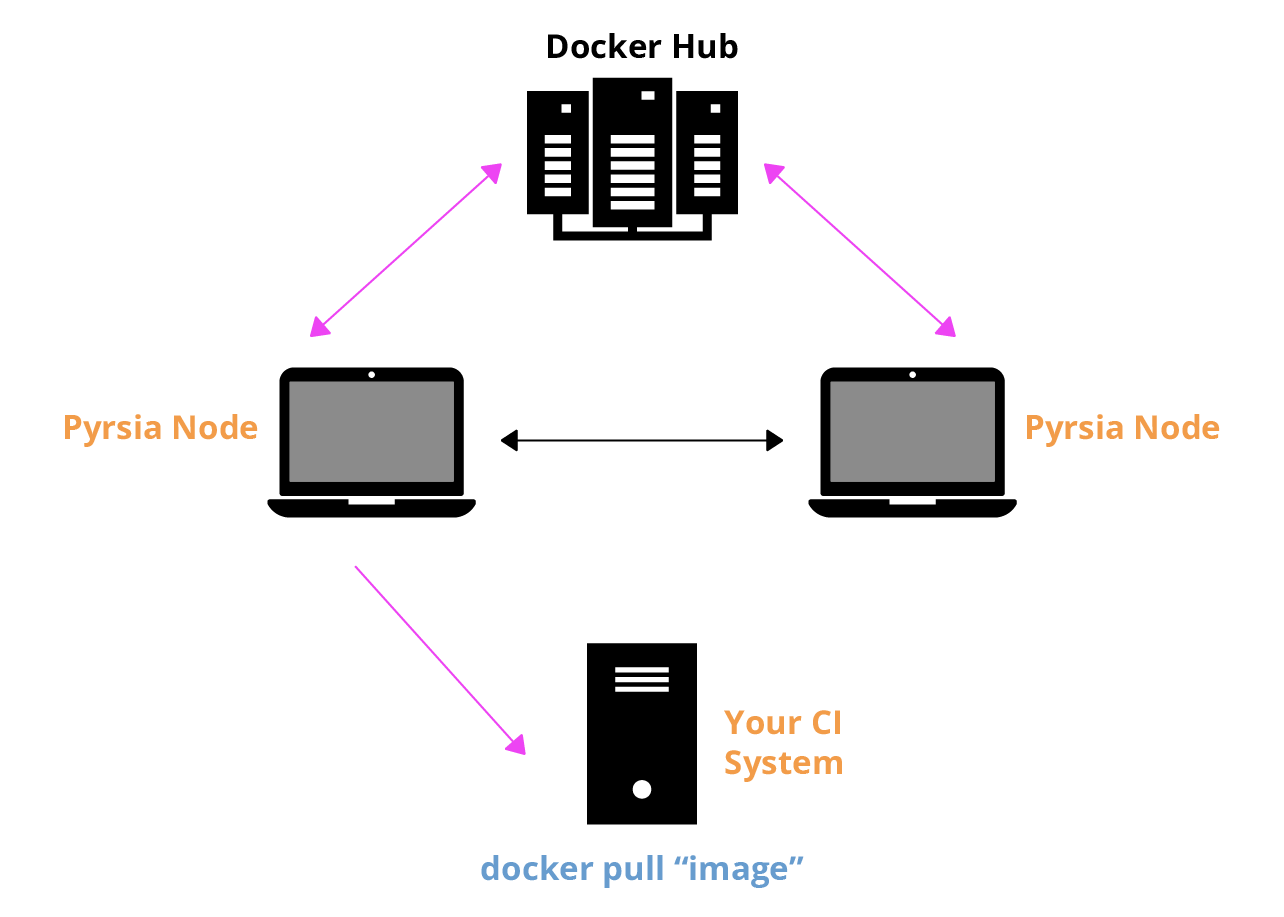
Pyrsia has started with building a P2P network that you can plug easily into your CI system. Pyrsia currently supports distributing Docker images over the P2P network with Docker Hub as the trusted registry. With this in place, Pyrsia gives you the ability to make your CI system resilient to any network failures/partitions that might happen. Additionally, you will get the benefit of having the images downloaded faster since they would be cached on the network (or a node near you) for better throughput.
The following diagram shows the setup that Pyrsia will enable and support. Pyrsia will provide a way of serving open source verified Docker images transparently. Once you have this setup you will not need to modify your CI system.
3 Easy Steps to Get Started
You can get started with Pyrsia by following these 3 easy steps:
- Download the installer for Pyrsia.
- Start all the Pyrsia node and connect to the network
- Configure your docker daemon on CI systems to also use Pyrsia as a registry mirror.
Detailed instructions can be found on the Pyrsia website.
Now you’re all set! Continue using docker pull as usual and now the images that are on the Pyrsia network will be served by the Pyrsia nodes. Also, on subsequent runs of your CI flow if the images are unchanged you will have them on the Pyrsia nodes and will save you the hop to Docker Hub as well. This will work for all images that are verified on dockerhub and are in the default namespace.
For all other Docker commands – since the images are not in the Pyrsia network they will be downloaded from Docker Hub (as usual) and you will still have the same experience as before.