Protect Your Containerized Microservices on OpenShift Using JFrog Xray

In our previous blog, we described how JFrog Artifactory on OpenShift benefits enterprise users when deploying containerized microservices. Now we’ll take it a step further to review the main security challenges facing container content and container registries when developing microservices. We will proceed to discuss how policies are enforced while building and deploying containers on OpenShift.
Let’s review a scenario whereby numerous microservices are running on different nodes, projects, and regions on OpenShift. These microservices run on a pod and include a main container, a sidecar container, and short-lived init-containers. These containers can include rpm packages, Maven packages, npm packages, etc.
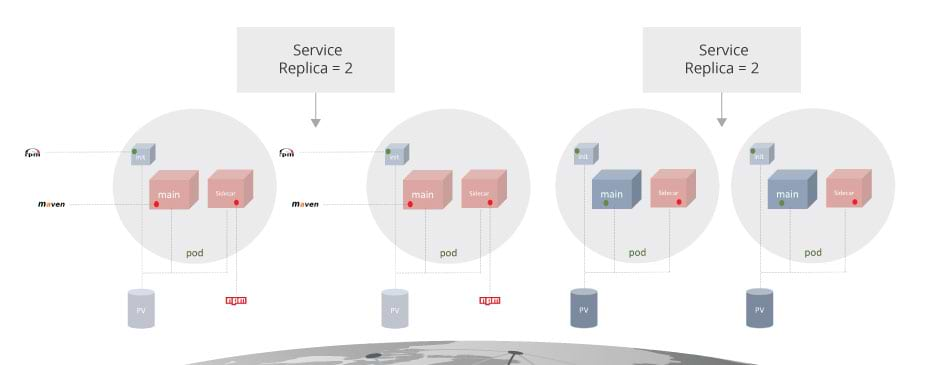
Now let’s say three new security issues were just made public with a high CVSS score. These are the three most important questions you need to ask?
- How many microservices are impacted due to the new security issues?
- How do we trace the CI job that produced the vulnerable binaries (JAR file, WAR file, npm package, Docker image)?
- How can we prevent the damage from spreading the deployment of these vulnerable microservices on OpenShift? And prevent building additional microservices that rely on these vulnerable components?
The good news is that we can get answers to all these questions by using JFrog Xray and leveraging its integration with Artifactory and CI tools.
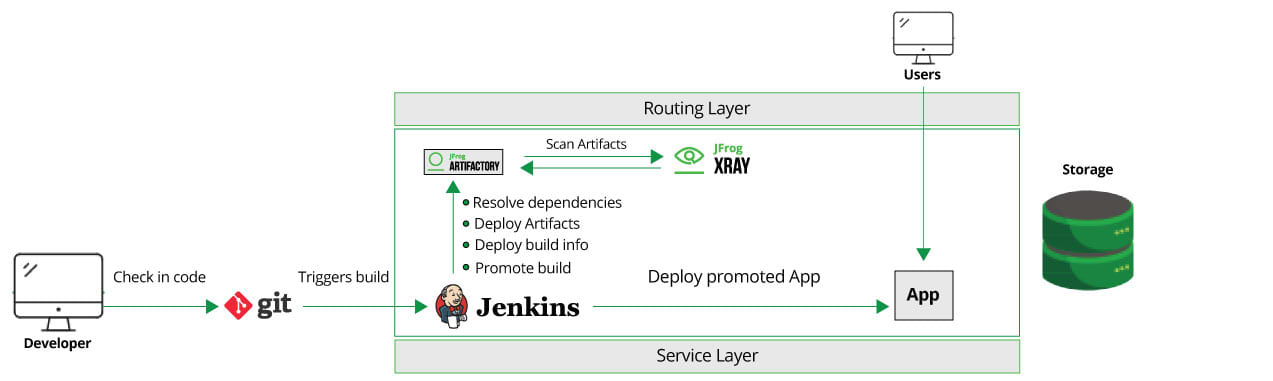
With Xray integration, the resolved dependencies, promoted artifacts and promoted builds are all compliant based on the metadata associated with the artifacts and builds. The metadata includes security issues, licenses, quality, and more.
1. Impact Analysis: Evaluating the number of affected microservices
Xray analyzes how an issue in one component affects all others in your company and displays the chain of impact in a component graph. When a vulnerability is detected, Xray shows you all the microservices that contain the infected artifact so you can instantly understand the impact that any vulnerable layer has on all microservices in your system.
2. CI Jobs: Producers of vulnerable binaries
JFrog Xray has access to a wealth of metadata captured from Artifactory and CI tools such as Jenkins. This metadata, combined with deep recursive scanning, puts Xray in a unique position to analyze the relationships between vulnerable artifacts and the CI jobs responsible for producing those artifacts.
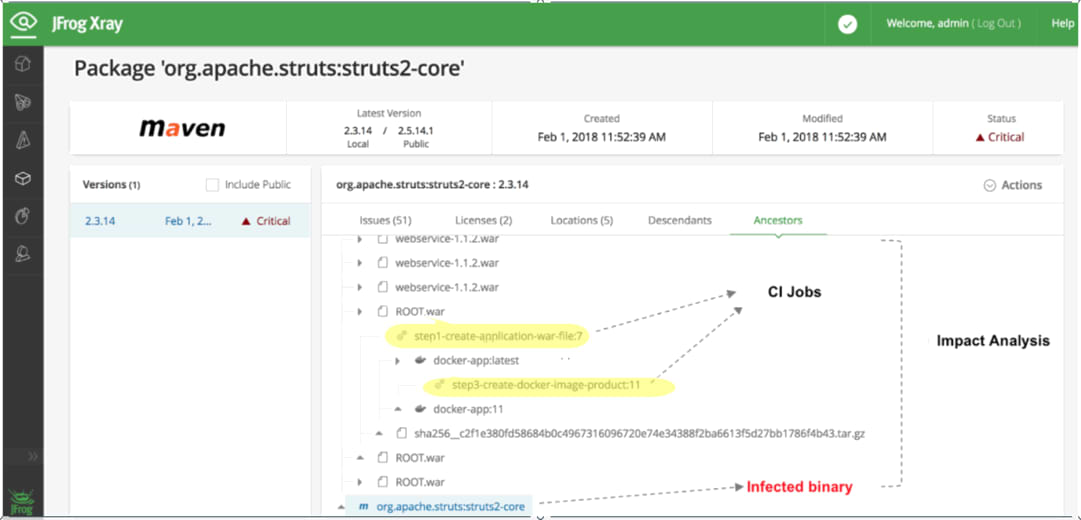
The above image displays Xray Impact Analysis with the following findings:
- The Apache Struts (“struts2-core-2.3.14.jar” file) is infected with a critical vulnerability and is part of a lot of war files (“ROOT.war”, “webservice-1.1.2.war”).
- Xray has identified the CI job “step1-create-application-war-file” and CI job number “7” responsible for building the “ROOT.war” file.
- The “ROOT.war” file is also part of the Docker image layer that is referred by multiple Docker manifest files such as “docker-app:latest” and “docker-app:11”.
- Xray even reported the CI job responsible for producing the vulnerable Docker images that includes the vulnerable WAR file that contains the “Apache Struts” infected file.
3. Preventing the vulnerabilities from spreading across your microservices
You can enforce policies in Xray on multiple levels. For example, while deploying a containerized microservice on OpenShift, and while building the containerized microservice on OpenShift
Different types of policies can also be enforced based on the repository type – Development or Production. For example, if a severity is set to critical, you can prevent users from downloading vulnerable artifacts in development and production repositories for the different file types (Docker images, JAR files or npm packages). These policies prevent vulnerable microservices from being deployed as it fails the deployment once a vulnerability is detected. To help contain the damage, CI integration, security or license scans can be triggered as part of the build, allowing you to fail the build job and prevent vulnerable microservices from being built.
Installing JFrog Xray on Openshift
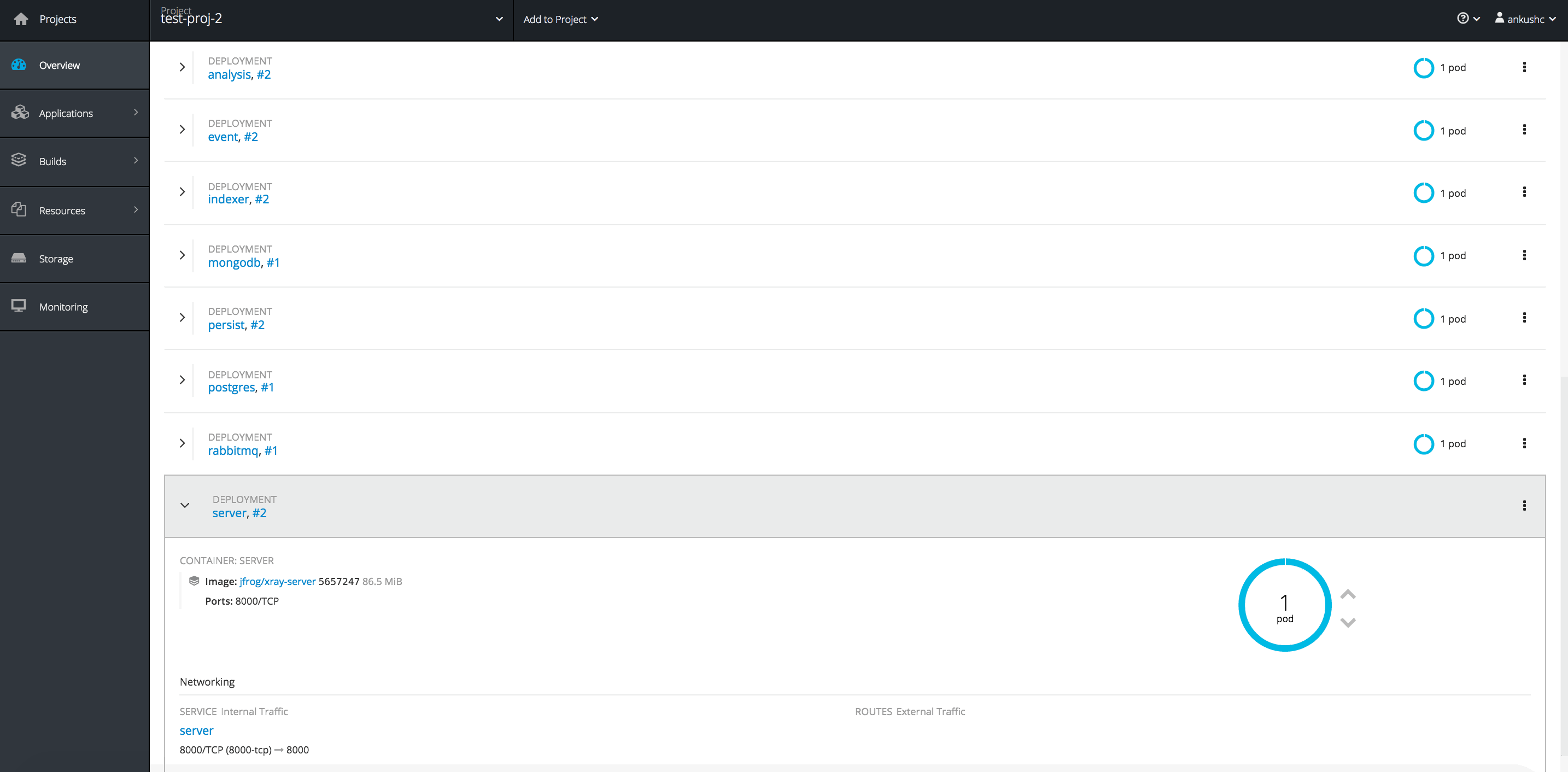
We made it easy for you to install Xray on Openshift by providing a set of templates. Once Xray is installed, you will be able to see eight microservices running on OpenShift.