Meet JFrog’s Newest Board Member – Meerah Rajavel, Citrix CIO and Technology Industry Veteran
As JFrog continues to grow, having solid guidance and the right mix of talent on our board is important to help us reach our goals. We are honored to have recently welcomed seasoned business technology leader, Meerah Rajavel, to our Board of Directors. Meerah’s extensive experience in revenue growth, go-to-market, and business transformation strategies will be key in helping guide JFrog through our next stage of global growth and product expansion, solidifying our leadership in the DevOps and DevSecOps markets.
A business-centric and award-winning technology leader, Meerah currently serves as CIO for Citrix. With over 20 years of experience in enterprise software, cybersecurity, and application performance solutions, she has helped drive profitability, agility, and transformation through the creative use of emerging technologies at large corporations such as Citrix, McAfee, and Cisco Systems, as well as several rapid growth startups. A change agent, mother, wife, and innovative leader with a reputation for supporting women in technology, Meerah will be integral to JFrog’s continued commitment to workplace diversity.
In an effort to help the JFrog community, customers, and partners get to know Meerah a little better, we met with her for a casual Q&A about how she got started, what she finds most appealing about DevOps and DevSecOps trends and how they will impact the market in the years to come, and much more. Here’s what she had to say:
- Tell us a bit about yourself
- Who were some of the mentors that shaped your career growth and why?
- What advice would you give to other females looking to pursue a career in cybersecurity?
- What do you find most appealing about the DevOps or DevSecOps space?
- What best practices do you recommend for companies that are just starting on their digital transformations?
- How did Log4j impact your organization’s workflow and/or what do you see as some of the key takeaways for those still battling Log4j?
- What are some of the key trends you see having the biggest impact on DevOps and/or DevSecOps in 2022?
Q: Tell us a bit about yourself – did you grow up knowing you wanted to pursue a career in IT? How did you come to that decision?
I was born in a small town in the southern part of India. My first exposure to computers happened in 10th grade when my neighbor exposed me to what was then called a ‘home computer’ to demonstrate the computation power. I was immediately impressed by the capabilities and speed of the device. I knew at that moment that I wanted to do something with computers. While I wasn’t necessarily clear on what my career options were at that point, I knew I wanted to be a programmer and decided to pursue a degree in Computer Science Engineering at Thiagaraja College of Engineering in India.
Q: Who were some of the mentors that shaped your career growth and why?
I’ve been fortunate to have amazing mentors throughout my life, both personally and professionally. The first guides in my life – who are still a big influence to this day – are members of my immediate family. My dad always encouraged me to pursue my dreams and not to shy away from opportunities despite any obstacles that might be in the way. My mother was a living example of how a woman can be successful and influential regardless of social constraints that may hinder access. My husband, Raj, has been a key pillar throughout my career. We were married when I was 20 years old – right out of college – and on our wedding day he told me I needed to be an independent woman and that he would do whatever he could to help me reach that goal. When we met through the way of a traditional arranged marriage, I could barely speak English, but he coached and mentored me to approach my career options. Then there’s my daughter, Shay, who has been simply the best source of encouragement anyone could ever ask for.
I also had the pleasure of working with several amazing female professionals throughout my career who each had a profound impact. Sue Stemel was both my manager and a dear friend. She taught me that true leadership required the efforts of both my heart and my mind. Rebecca Jacoby showed me how to be a business-centric leader – always keeping the benefit of the entire company in mind versus focusing solely on your functional metrics. And Patty Hatter demonstrated how to build alliances both within a team and across teams in order to inspire people to do their best work and achieve the best results.

LET’S BE THE TRAILBLAZERS AND BRING OTHERS ALONG WITH US
Q. As an accomplished female leader in IT Security, do you feel the tides have finally turned in terms of equal access to such opportunities or is there still more work to be done? What advice would you give to other females looking to pursue a career in cybersecurity?
While notable progress has been made in terms of female access to IT leadership positions, there is still more work to be done. We saw a sharp increase in the number of IT leadership positions held by women between 1995 and 2000 (11% growth) and today women account for roughly 24% of IT leadership. However, when it comes to female representation in IT security – which also now includes privacy, risk, compliance, and audit positions – women account for only 13% of leadership. This diversification of the ranks in both IT at large, and in security more specifically, is not only important to me as a female IT security leader, but it also just makes good business sense. I think we can all agree men and women tend to prioritize different areas and see varying opportunities for evolution both within a team and a business. Thus, it is advantageous to make certain you have equal measures and voices on both ends. To help with this effort I’d recommend companies consider the following three steps:
- Feed the Pipeline: Establish your own or partner with a local STEM program that offers an ‘early start’ program for young girls interested in math, science, and technology.
- Prevent Fallouts: Implement corporate and peer support programs that provide flexibility, inclusion, and inspire women to remain in the workforce.
- Groom for the Future: Create mentorship programs and internal learning sessions that help inspire and provide guidance to younger female professionals looking to break through the glass ceiling. About 5 years back we started a women’s CXO network – T200 (https://www.t200.org) – with the objective of elevating women in technology. Then in 2021 we launched T200-LIFT, focused on lifting more female leaders into the C-Suite.
Additionally, it’s important to remember that diversity shouldn’t be limited to just gender. Companies today should strive to embrace all forms of diversity – gender, ethnic, religious, cognitive, and sexual.
Q. What do you find most appealing about the DevOps or DevSecOps space in general and – more specifically – what drew you to JFrog?
There’s no question that in the last decade, the digitalization of everything has caused every company – regardless of industry – to become a software company. Whether you’re a high-tech software company or an app-based hospitality business that doesn’t own a single property, a transportation business without a single vehicle in its fleet, or a financial institution that doesn’t have a single branch. From mobile banking and virtual healthcare visits to self-driving cars and automated food prep and delivery services, software applications are embedded into nearly every aspect of the economy and our lives. This ‘app-lification’ of everything is why all companies – regardless of industry – need DevOps.
Traditionally speaking, there are two important aspects of software to keep in mind: manufacturing and distribution. First you need to develop the software, then you need to deliver it. But in today’s increasing threat landscape – with the number and sophistication of cyberattacks growing daily – it’s imperative to have security be a third pillar in the mix. In today’s market, whenever you’re providing a product or service, the expectation is that it’s being done securely. Thus, DevSecOps, wherein security is ‘baked in’ to the development of the software vs. ‘bolted on’ after it’s already in play, is on the rise. I see DevSecOps not as a technology, but rather as a framework that needs to be applied to every piece of software created or updated across every enterprise. This is the secret sauce JFrog offers: the ability to provide secure binary management across the entire software supply chain, which is what enticed me about the opportunity to join their board.
Q. DevOps is often described as an agent for digital transformation. As someone with a great deal of experience in leading large teams and organizations through wide-reaching technological change, what best practices do you recommend for companies that are just starting on their digital transformations?
Before embarking on any digital transformation initiative, it’s wise to align with your business counterparts and make sure you’re collectively approaching it from an inside-out, company-wide perspective – because applying a new technology to a broken process won’t fix the problem.
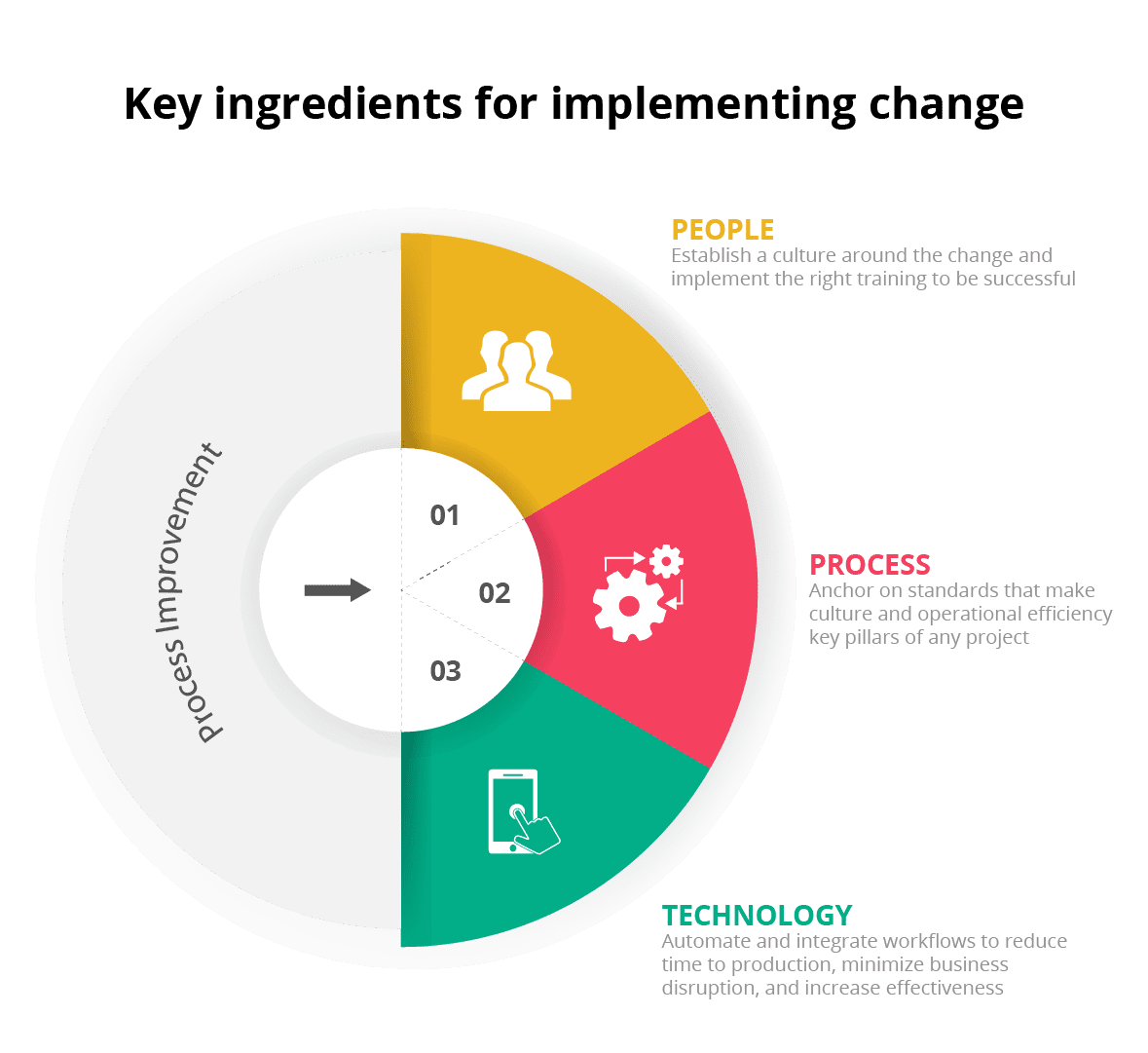
For me, any type of change management needs to be broken down into three key focus areas: People, Process, and Technology. But it’s imperative that you start with the People because without first establishing a culture around the change, it will be difficult to achieve success. This is another reason I am an advocate for DevSecOps; it’s predicated on bringing these three elements together to accelerate the development and delivery of high-quality, secure, software.
When it comes to People, IT leaders trying to implement change need to be mindful of two important elements: Culture and Training. First you must establish a culture that encourages risk taking and organizational success over individual success. Work as a team, win as a team, and no one drowns alone. Second, you should establish training programs that enable individuals to confidently transition to the new systems or way of working and be immediately effective. When there’s too much downtime during a transition, it’s difficult to recover and gain faith in future endeavors.
For Process, I recommend anchoring on standards like safe agile frameworks (SAFe) that make culture and operational efficiency key pillars of any project, to help ease adoption across all areas of the business.
Finally, be sure to invest in the right Technology to help automate and integrate workflows so you can reduce time to production, minimize disruption to the business, and increase effectiveness.
Q. The recent Log4j/Log4Shell vulnerability has had a notable impact on companies of all sizes and government organizations. How did Log4j impact your organization’s workflow and/or what do you see as some of the key takeaways for those still battling Log4j? What can and should organizations do to help minimize their risk around vulnerabilities like Log4j moving forward?
The Log4Shell put a spotlight on the need for DevSecOps and software composition analysis (SCA), which creates a software bill of materials (SBOM) for open-source packages in apps, including license compliance and securing vulnerabilities. Open-source components like Apache Log4j have become pervasive in modern software development, with the majority of modern applications’ codebases made up of such packages. Having an SBOM method allows developers to move more quickly since they don’t need to re-create code that is already freely available and vetted by the community.
Incidents like Log4j are highly disruptive for corporate, technology, and government organizations alike, as this has a chain reaction for which the repercussions have yet to be seen. Additionally, much like any virus, the Log4j vulnerability keeps morphing and changing, which means remediations are going to be both challenging and time consuming.
The Log4j incident will no doubt have a long tail to its impact, but as a near-term tactical approach, I’d recommend security professionals focus on getting a handle on their asset inventory. Leverage free open-source scanning tools provided by vendors like JFrog to help quickly detect the presence and utilization of Apache Log4j in both source code and binaries so you can focus remediation efforts and speed time to resolution. I would also keep in close communication with the commercial off-the-shelf software (COTS) vendors with whom you work for updates on their progress in managing Log4j remediations appropriately.
Longer-term, to help avoid the devastating impacts of Log4j and other viruses in the future, it’s best to incorporate DevSecOps, SCA and SBOM frameworks to all software deployments to help better guarantee the security of your entire software supply chain.
Q. As we approach the end of the year, what are some of the key trends you see having the biggest impact on DevOps and/or DevSecOps in 2022?
When I look at today’s landscape, I see two vectors that will continue to drive the proliferation of DevSecOps in 2022 and beyond – hybrid workplaces and the increasing threat landscape.
We’ve witnessed two major software supply chain attacks in the last 12 months with SolarWinds and Log4j. The first is an example of how easily malicious code can be remotely injected into a simple software update delivered to thousands of enterprises and government agencies worldwide. The second highlights how threat actors are increasingly targeting the vulnerabilities in third-party software components to cause widespread havoc.
Recent research by Forrester indicates 80% of security and business leaders say their organizations are more exposed to risk as a result of remote work. According to the research, over half of remote workers use a personal device to access work data, and 71% of security leaders lack sufficient visibility into remote employee home networks, leading to a large portion of cyberattacks (67%) targeting remote employees.
Circumstances like these are often coupled with the fact that many companies have multiple versions of the same software running inside the company at any given time and aren’t fully aware of what’s in use. As someone who grew up as a software engineer and is now a CIO responsible for a company’s safety and employee productivity, I feel passionately that all these factors underscore the importance of securing the software supply chain and – more specifically – the critical role binary management plays in the software development process.