How to protect your secrets with Spectral and JFrog Pipelines

Thousands of secrets leak daily on public git repositories, including over two million corporate secrets in 2020 alone.

This can happen to anyone! For example, in January 2021, an Amazon cloud engineer accidentally committed almost a gigabyte worth of sensitive data that included their own personal documents, as well as passwords and cryptographic keys to various AWS environments on his personal GitHub repository.
Another example is the SolarWinds breach, one of the biggest data breaches in recorded history which began with a poorly selected password exposed on a public GitHub server.
When we are developing an application we would like to do everything we can to protect our data and our code. We are humans and humans (usually) make mistakes, and when combining this with a lack of education on security best practices we can easily expose our secrets. Therefore, we may want to use a secret scanner to search for any sensitive information such as private keys, API secrets and tokens, etc.
Spectral (aka SpectralOps) offers secret scanning solutions that can easily integrate with JFrog Pipelines. It does so by looking at file names, extensions, and content, attempting to match them against a list of signatures. Spectral can monitor, classify, and protect your code, assets, and infrastructure for exposed API keys, tokens, credentials, and high-risk security misconfigurations in a simple way.
This blog post will go through the 3-steps on how to do this.
Step 1: Configure DSN in SpectralOps
First, we need to configure the DSN in JFrog Pipelines from the SpectralOps platform.
- Click on Sources and select the Private and Public Repositories.
- Copy the SPECTRAL_DSN and save it for later. It should look like this:
https://<Team Key>@get.spectralops.io
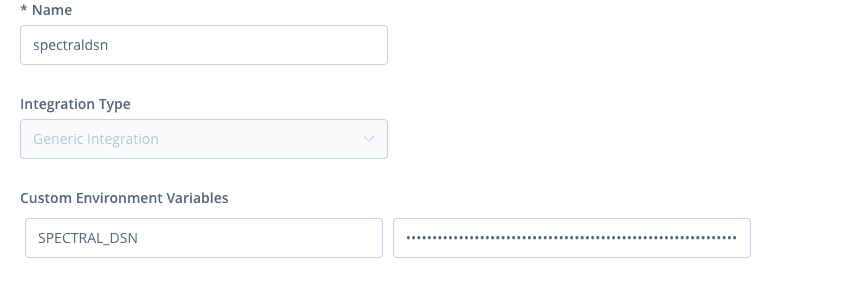
- In the JFrog Platform, go to Administration > Pipelines > Integrations and click Add an Integration.
- Select Generic Integration and add the SPECTRAL_DSN you saved above.
Step 2: Run your build
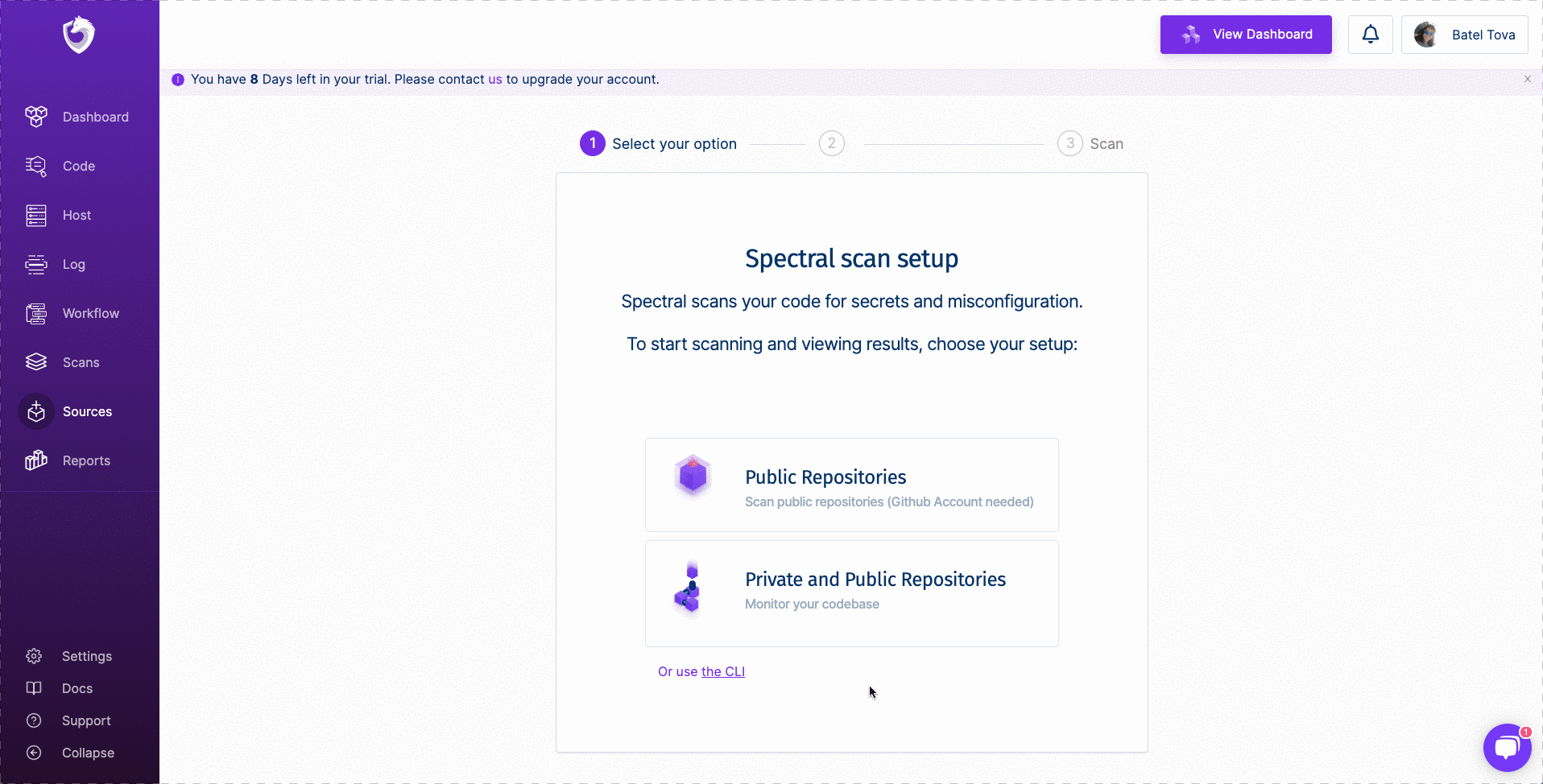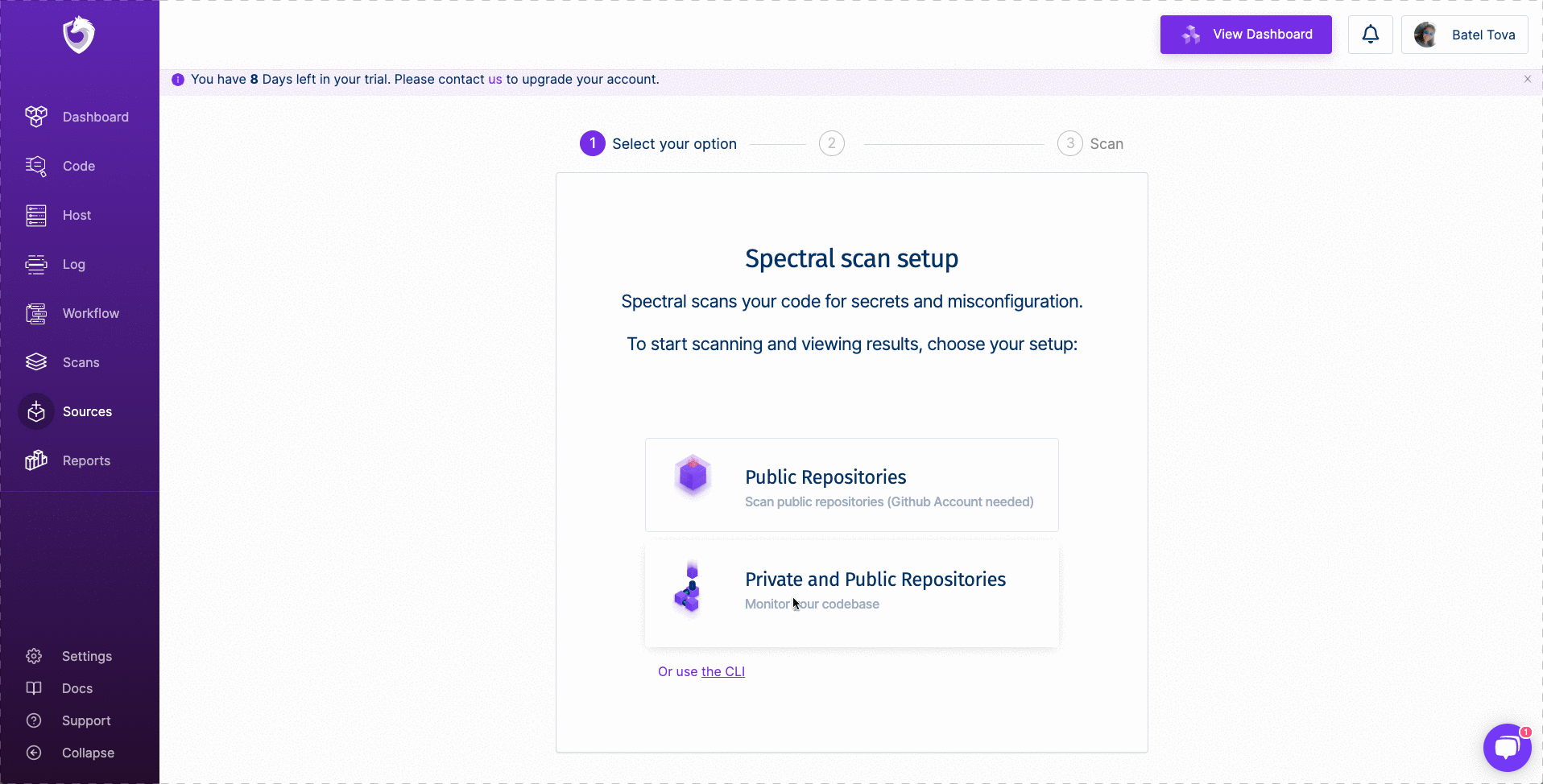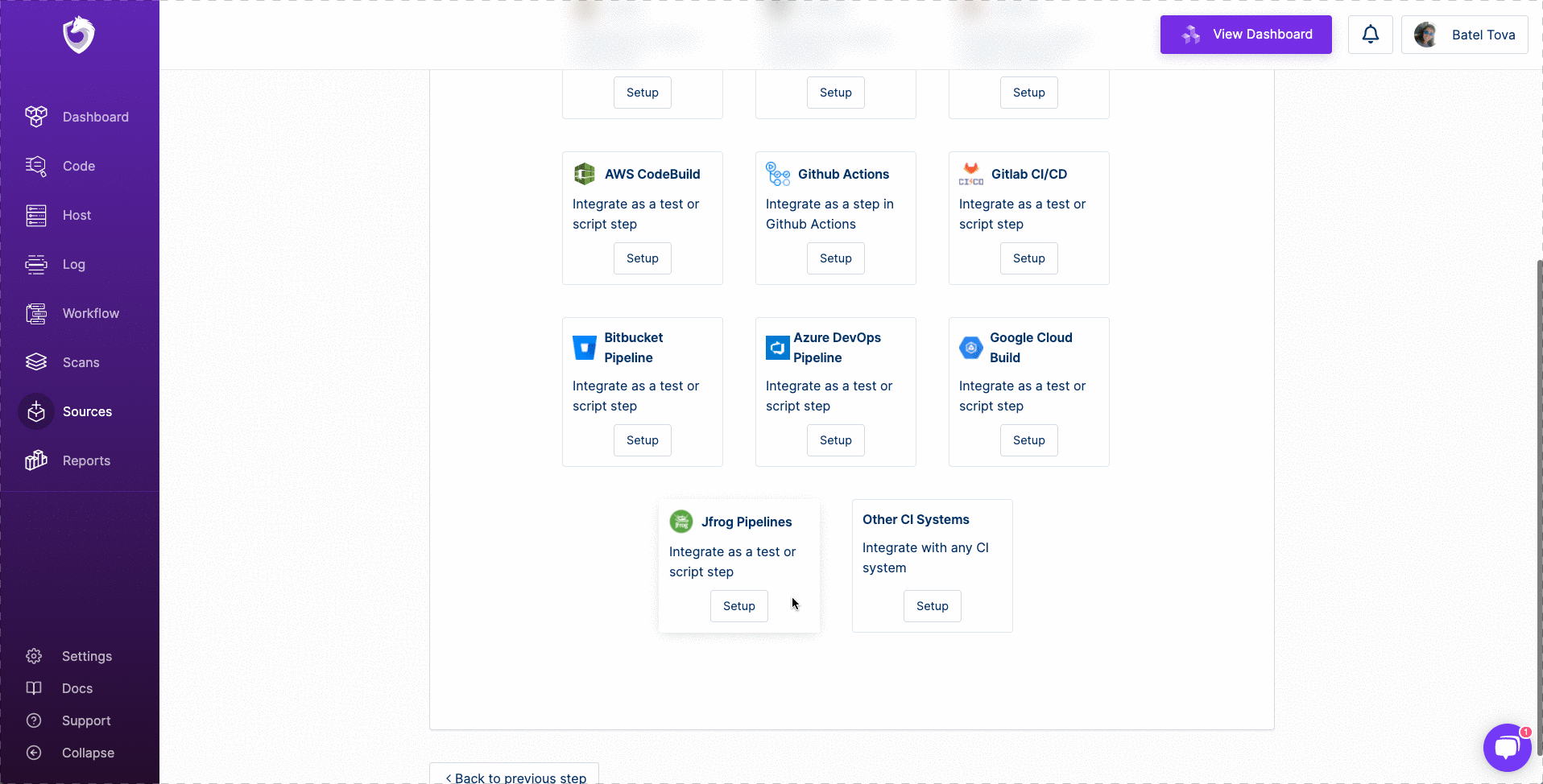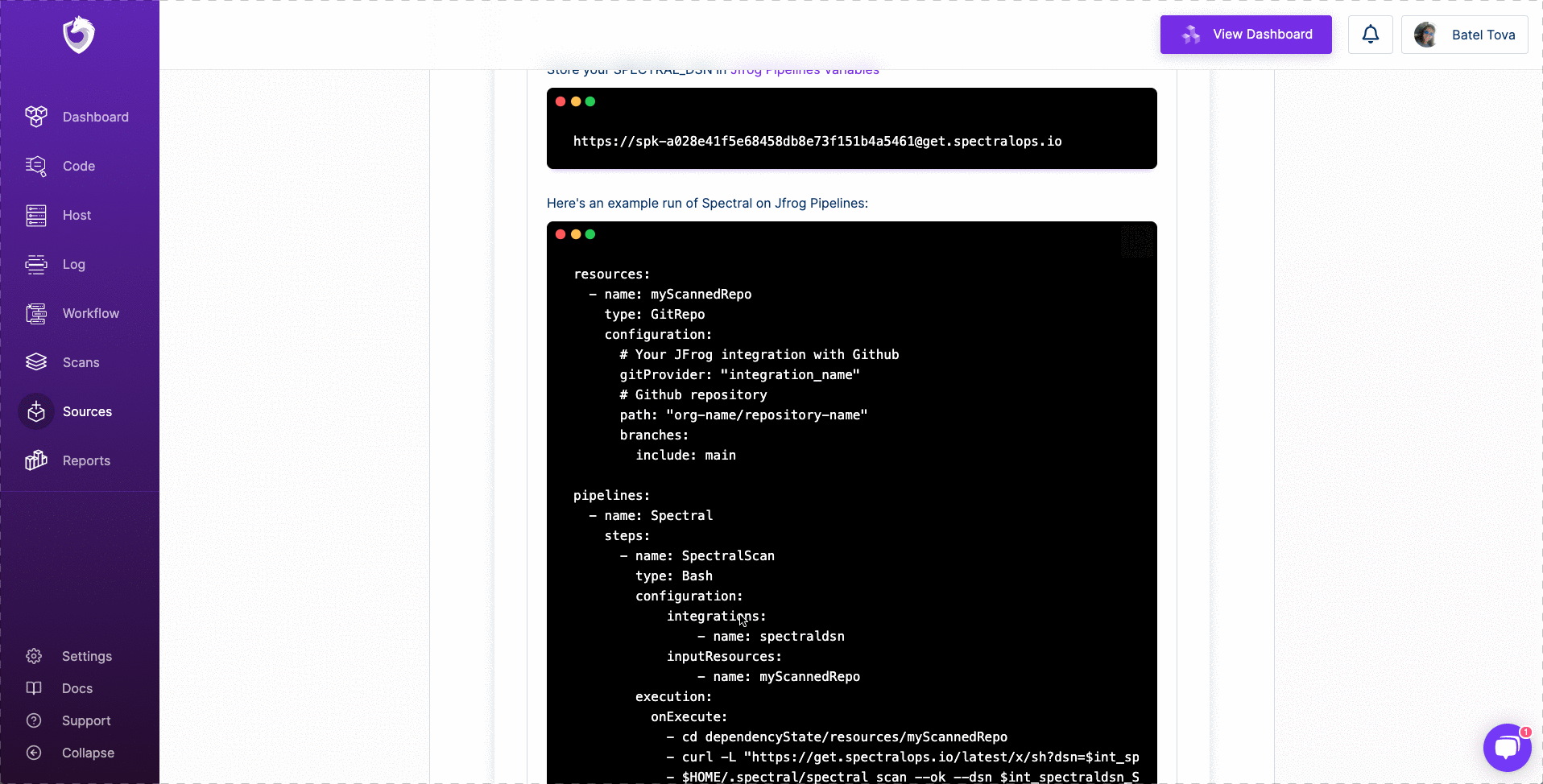
resources:
- name: myScannedRepo
type: GitRepo
configuration:
# Your JFrog integration with Github
gitProvider: "integration_name"
# Github repository
path: "org-name/repository-name"
branches:
include: main
pipelines:
- name: Spectral
steps:
- name: SpectralScan
type: Bash
configuration:
integrations:
- name: spectraldsn
inputResources:
- name: myScannedRepo
execution:
onExecute:
- cd dependencyState/resources/myScannedRepo
- curl -L "https://get.spectralops.io/latest/x/sh?dsn=$int_spectraldsn_SPECTRAL_DSN" | sh
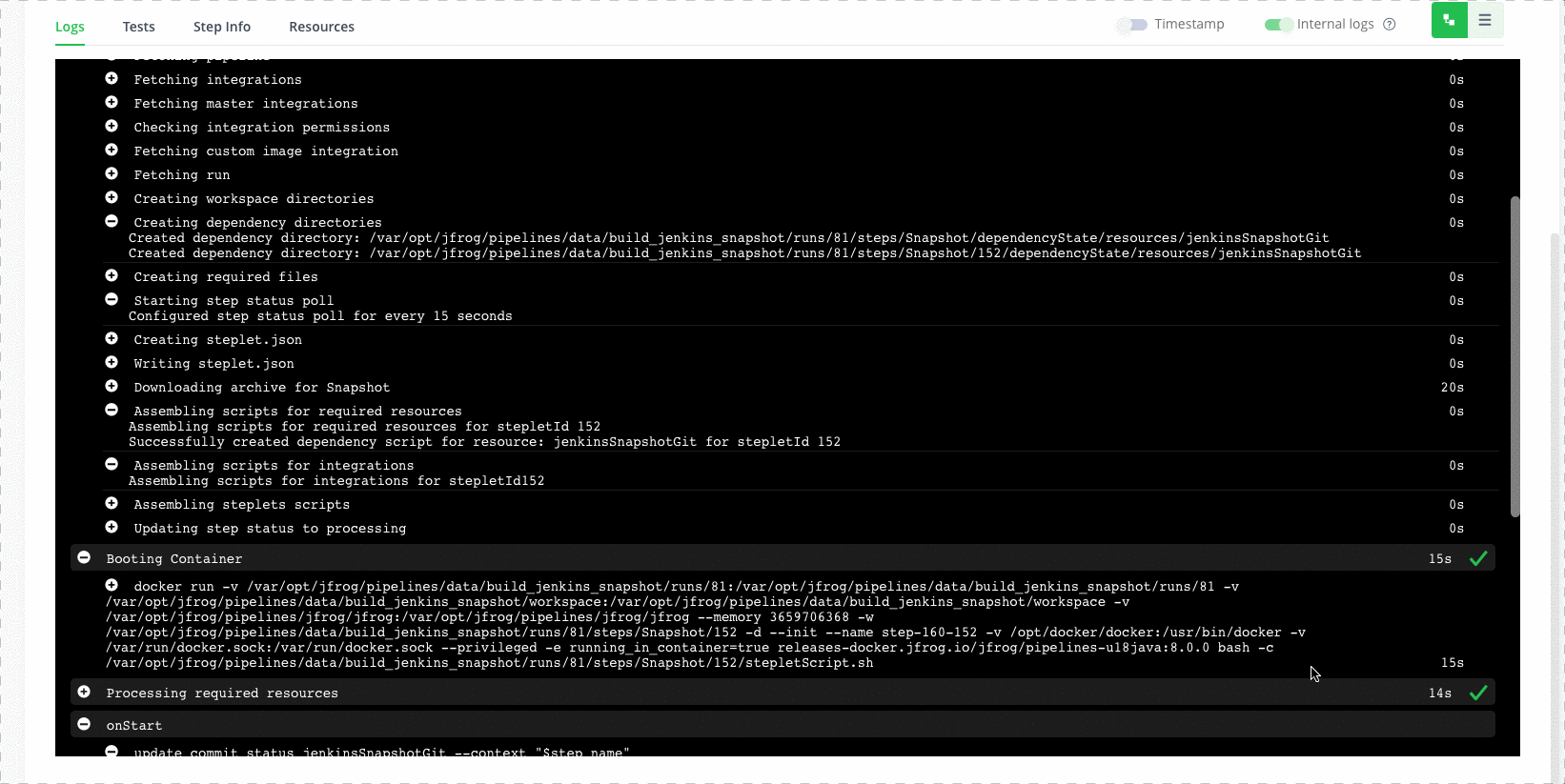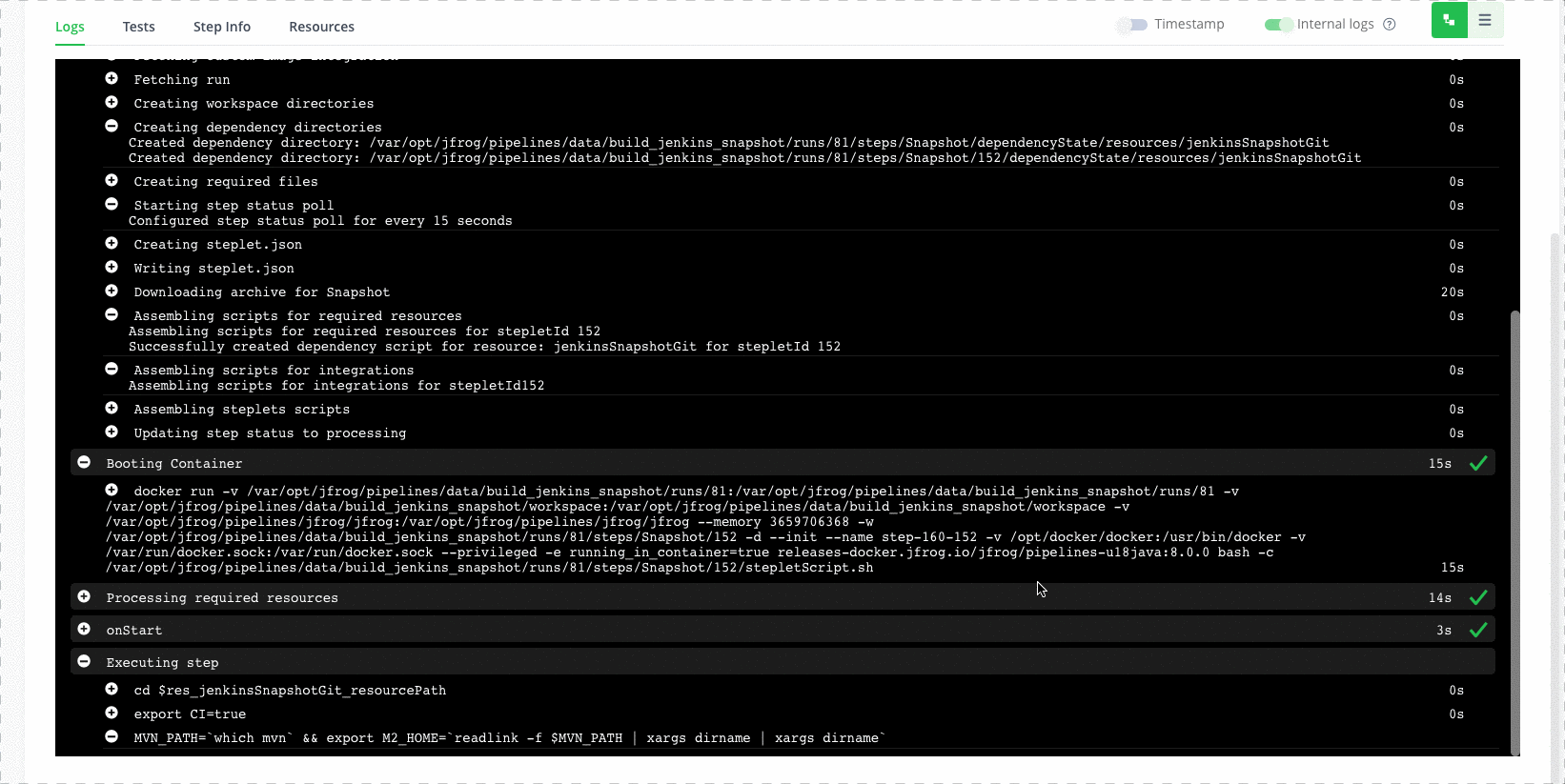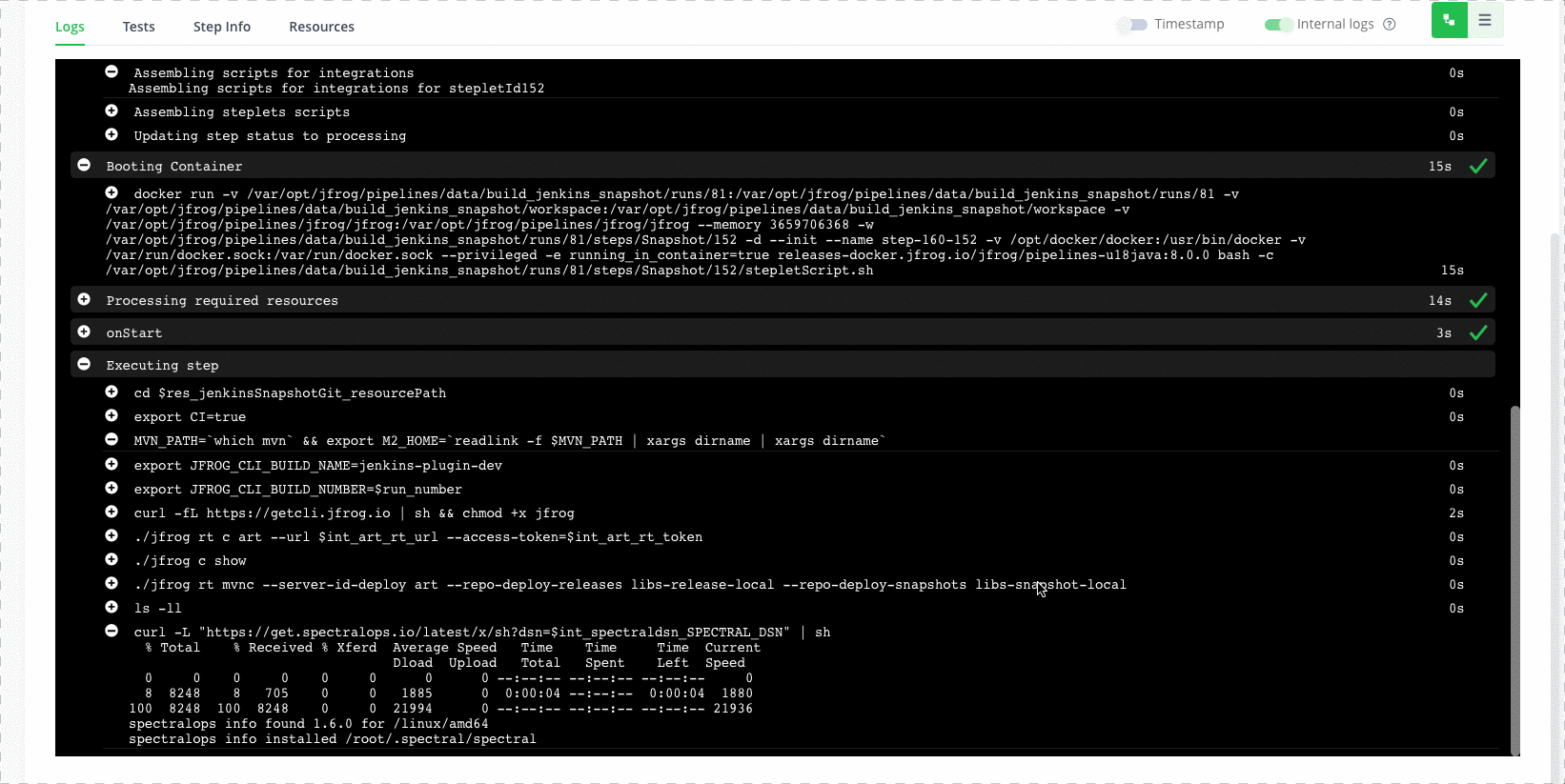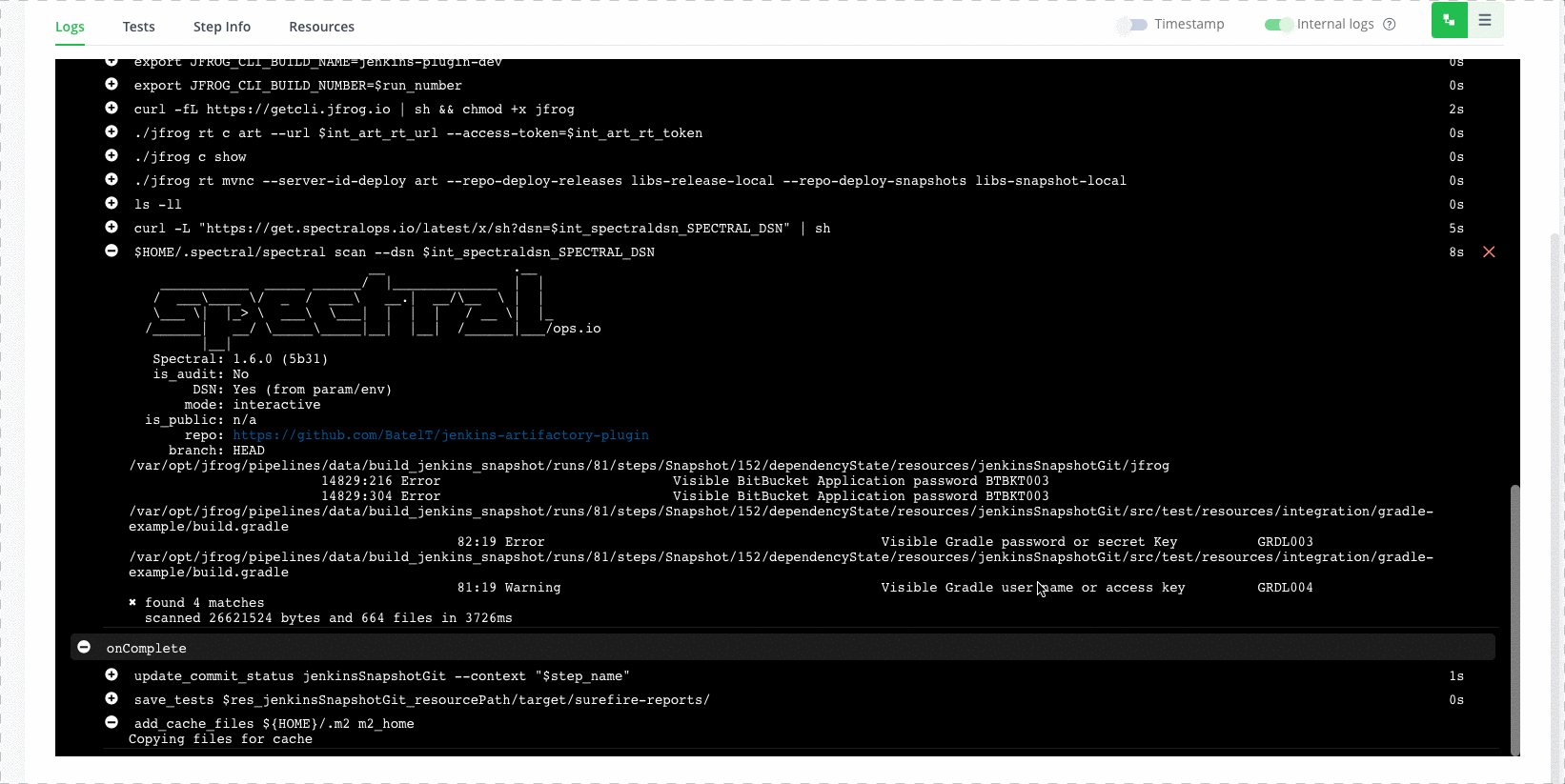
- $HOME/.spectral/spectral scan --dsn $int_spectraldsn_SPECTRAL_DSN
In case any secrets are found, the Spectral integration will fail your build.
*Note: If you don’t want to fail the build, use the flag scan –ok. For example: $HOME/.spectral/spectral scan –dsn $int_spectraldsn_SPECTRAL_DSN scan –ok
Step 3: Review issues
Now we can get more information about the issues, in the SpectralOps platform, under the code tab.
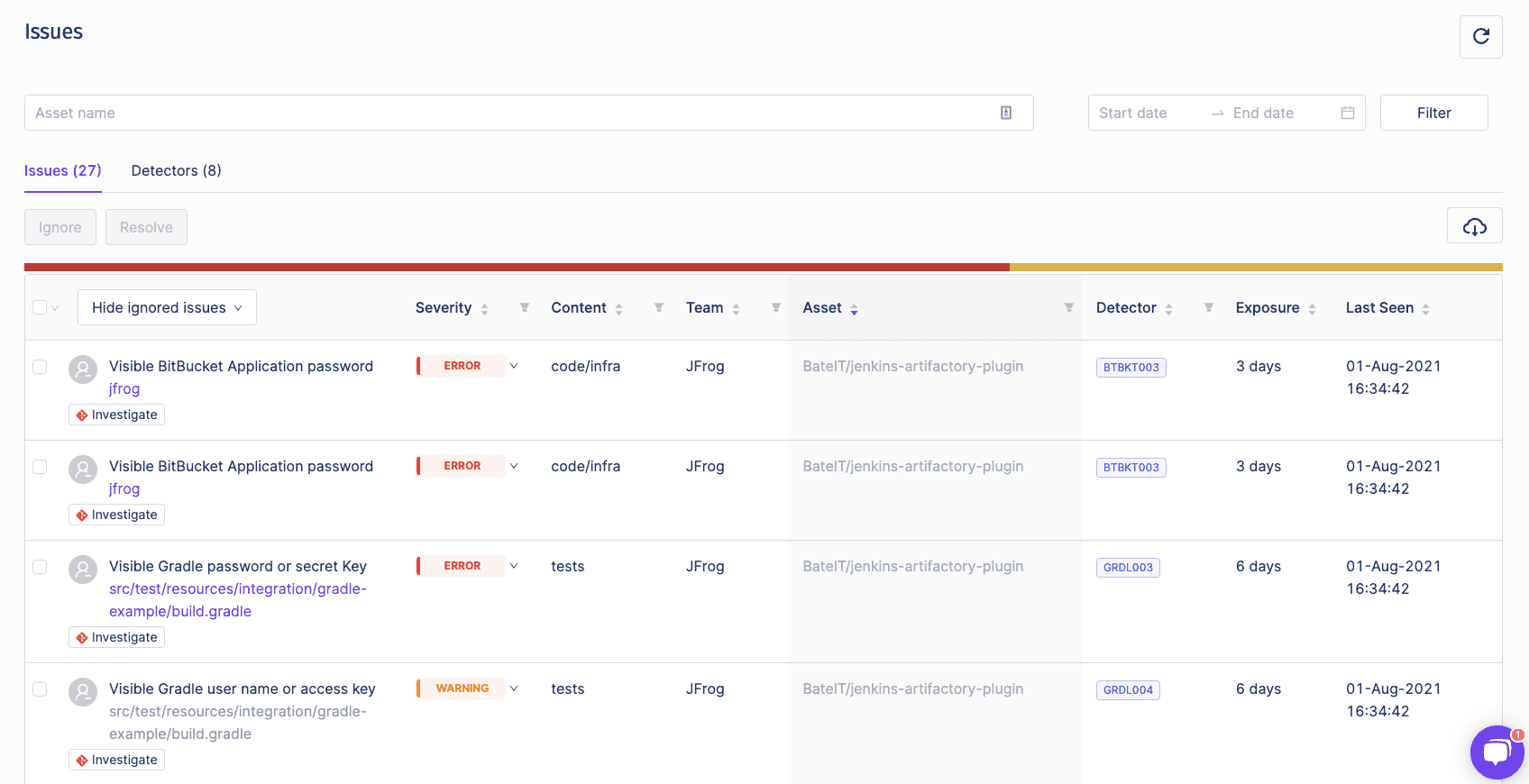
Now we can be rest assured that our secrets are safe, and there are no leaks in our git repositories.
See what other integrations are supported with JFrog Pipelines, and try it out for yourself!




