Empowering Kubernetes Security: JFrog’s Seamless Integration with AWS AssumeRole
Security Use Cases for AWS AssumeRole
In the fast-paced environment of cloud-native apps, security and seamless connections are a priority. Many DevOps and SecOps professionals use Kubernetes native features to handle their container security, keeping a tight grip on access and secrets to improve security posture. The integration between AWS AssumeRole and JFrog Access in Amazon Elastic Kubernetes Services (EKS), enhances enterprise security by automating secrets management.
As the cloud computing landscape continues to evolve, there are a significant number of joint AWS/JFrog customers for whom harnessing the power of AssumeRole has become essential. So, what exactly is AssumeRole, and why does it hold such significance in the realm of AWS security?
The Challenge of Manual Handling of Kubernetes Secrets
Traditional methods of handling access credentials and secrets in Kubernetes often require manual intervention, introducing several potential security vulnerabilities that can jeopardize the overall security posture. Here are some common issues that an arise from using a manual approach:
- Human Error – Increases the likelihood of misconfigurations and exposure of sensitive information.
- Insecure Storage – Storage of secrets in plain text files can expose them to unauthorized access.
- Auditing and Logging Gaps – Manual methods lack proper tracking mechanisms making it challenging to identify who accessed or modified sensitive information.
- Static Secrets – Non-Rotating Secrets pose a significant risk which is difficult to maintain using traditional methods.
- Manual Credential Distribution – Manual Provisioning of access credentials can be time-consuming and error-prone, increasing the risk of identity theft.
Addressing these vulnerabilities requires adopting more secure practices that can automate key processes to avoid these and other vulnerabilities.
The AssumeRole-JFrog Automated Solution
The integration of AssumeRole and JFrog Access presents a powerful solution. By leveraging AssumeRole, AWS Identity and Access Management (IAM) users can temporarily assume permissions to perform actions in a secure and controlled manner.
Furthermore, incorporating third-party tools like JFrog Artifactory into AWS environments, enables seamlessly pulling images from the JFrog Docker private registry, thereby tightening access control mechanisms to ensure fluid integration that aligns with established industry practices.
Some of the key benefits of the AWS AssumeRole and JFrog Access solution includes:
- Automated Token Rotation: JFrog Access can now manage token rotation seamlessly within your EKS cluster. This eliminates the need for manual intervention, reducing the risk of unauthorized access due to neglected or forgotten credentials.
- Enhanced Security: With AssumeRole, you can enforce fine-grained access controls, ensuring that only authorized entities have access to your EKS cluster and JFrog Artifactory. This enhances security by minimizing the attack surface and adhering to the principle of least privilege.
- AWS Environment Integration: The integration of AssumeRole and JFrog Access makes your Artifactory repository a first-class citizen in your AWS environment. This means that you can seamlessly fetch images from your Artifactory repository as if it were a native component of your EKS cluster.
AssumeRole JFrog Architecture & Deployment
The diagram below shows the basic architecture of how AssumeRole integrates with JFrog Access to provide enhanced access control:
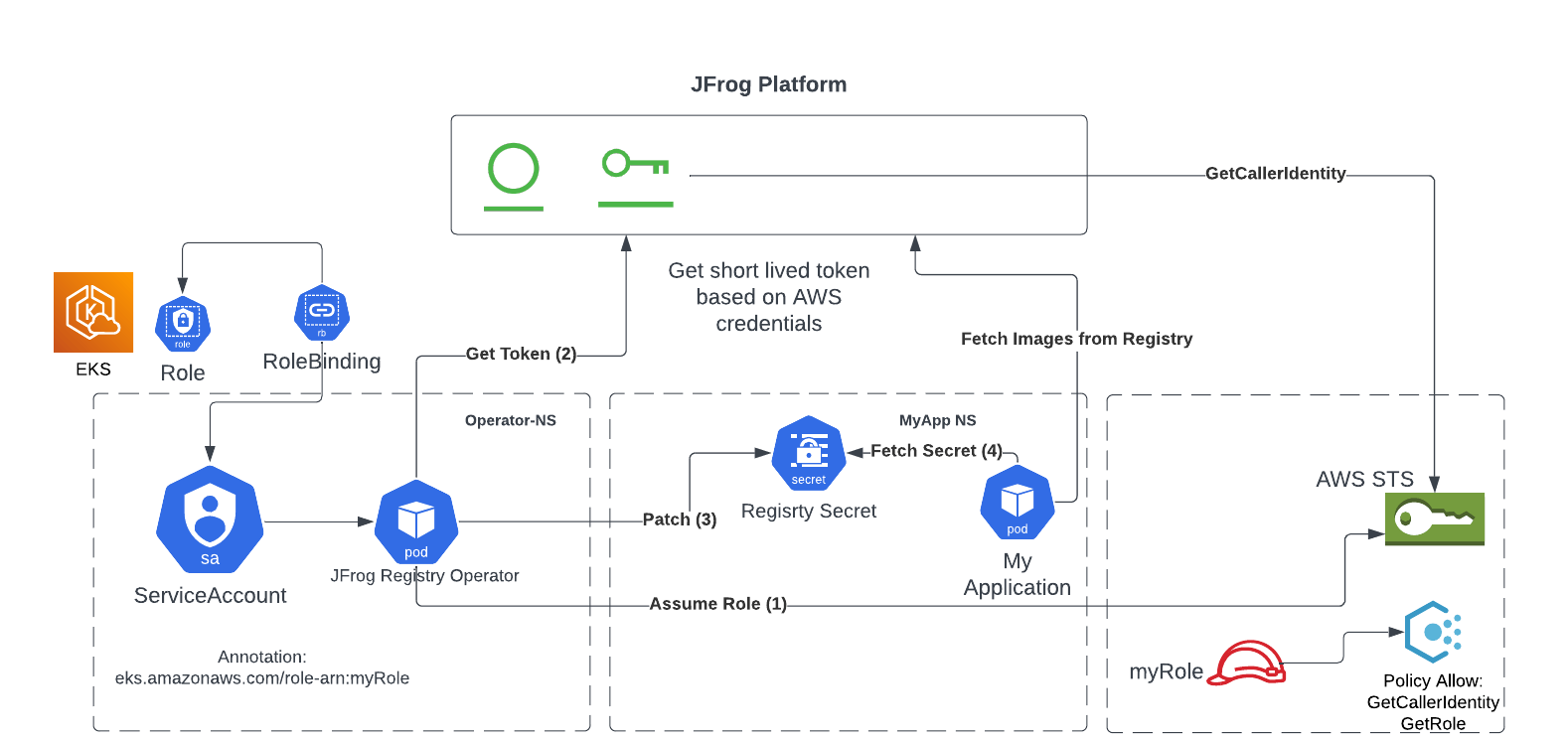
If you are interested in making the move from vulnerable manual secret handling to secure automated secret management, then your journey towards a more secure and seamless containerized future begins here.
See how quickly this powerful capability can be deployed by checking out our step-by-step installation and configuration guide.
Conclusion
The integration of AWS AssumeRole and JFrog Access in your EKS environment marks a significant step towards achieving enterprise-level security and operational efficiency. By automating token rotation, enhancing access controls, and seamlessly integrating JFrog Artifactory into your AWS environment, you are better positioned to manage your containerized workloads in a more secure and efficient manner. Check out the AWS partner page for more information on how JFrog and AWS are making cloud application development more secure and efficient for our customers.
JFrog customers interested in getting started can check out the AssumeRole documentation on the JFrog Knowledge Base.
If you are not a JFrog SaaS customer yet and want to learn more, then sign up for a free trial of the JFrog Software Supply Chain Platform on AWS.








