Customize Xray DevSecOps With Private Data

For some organizations, even the best isn’t quite enough. That’s why JFrog Xray provides a way for you to specify your additional data, to detect even more sensitive issues in your binaries before they can reach production.
JFrog Xray is a tool for DevSecOps teams to gain insight into the open-source components used in their applications. Through deep scanning of binaries in your Artifactory repositories, builds, and Containers – Xray identifies security vulnerabilities and helps assure license compliance with the policies of your organization. With this additional metadata, Xray enables an automated response to violations, such as preventing a download or failing a build.
JFrog Xray uses a high-quality comprehensive vulnerability database that integrates data from multiple leading sources including the NVD, GitHub, Ubuntu, Debian, Red Hat, PHP, and vulnerability data uncovered by the JFrog security research team. JFrog’s security research team ensures it has the most up-to-date and enhanced vulnerability and remediation knowledge.
With such comprehensive DevSecOps data to start with, why would you want to add your own? There are several reasons a company or developer might want to do this:
- You may consider something to be a vulnerability that Xray’s data sources do not.
- You may have access to information about software components not included in Xray’s data sources.
- You may have private (not OSS) libraries for which you have tracked vulnerabilities and want to include them in your Xray security scans.
For such use cases, Xray supports custom integrations of your own vulnerabilities data. With a custom integration, you can enable Xray to look at an external source for additional information about vulnerabilities and licenses. Just like JFrog’s first-party data source, if your server provides information about a software component, Xray will apply the security and license compliance policies you have specified.
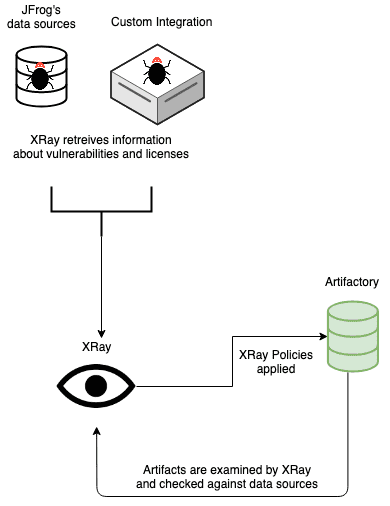
Creating a Custom Integration
Adding a custom integration to Xray is very straightforward, and you can learn all the details, as well as try the files from our Xray custom integration demo on GitHub. For those already familiar with Xray technology, we’ll hit the highlights of that demo here.
There are two pieces to set up:
- Your custom integration REST API
- JFrog Xray
Running the Demo Server
From the root of the project, run the server. The API Key is determined by you, and used by Xray to authenticate with your RESTful API.
go run main.go (<api-key>) [<path-to-db-file>]
Xray Setup
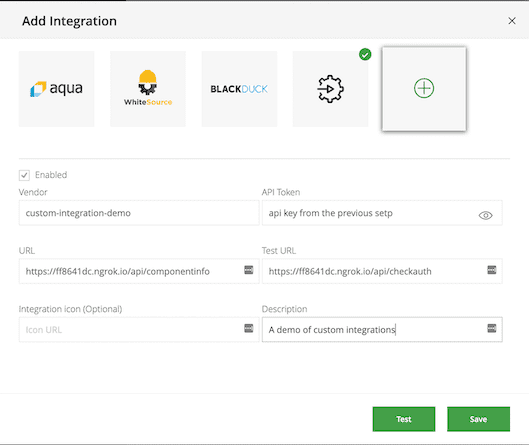
Open the integrations view from the admin panel in the sidebar to create a new integration.
Select custom integration and configure the integration.
Generating a Security Violation
The demo comes with a `json` file for a database. New components can be added to this file to trigger security violations.
{
"component_id": ,
"licenses": [
{
"version": ,
"licenses": [
"Apache 2.0"
]
}
],
"vulnerabilities": [
{
"version": ,
"source_id": "0"
}
]
}
In Xray, scans can be manually triggered for a component. Users can also leverage Policies and Watches, which will enforce specific behaviors when a violation occurs.
Try It Out
We encourage you to explore the JFrog Platform and Xray on your own, start a free trial today.



