Automate DAST in DevSecOps With JFrog and NeuraLegion
NeuraLegion’s VP Oliver Moradov takes us through how you can use JFrog and NeuraLegion to automate AppSec testing in your pipelines.
The days of long release cycles are well and truly behind us — it is simply not feasible in our agile development world, with developers delivering software and more features at an unprecedented scale and speed.
With DevOps, we have multiple development teams running multiple concurrent builds, which is great, but security testing has not kept up. To shift security left to achieve DevSecOps, you need a DAST (Dynamic Application Security Testing) tool that can keep up with this pace.
Legacy DAST tools are slow, inaccurate and not built for modern applications, which makes it hard for developers to use, understand and trust their output. This results in a reliance on slow, expensive manual security testing, whether by internal or external teams, and creates release bottlenecks.
You either have to wait until the manual security checks and validations are complete (never going to happen), or accept the risk and deploy. This results in significant vulnerabilities in production as issues are only remediated months after a software distribution is completed (if at all), and you end up with a pretty unsurmountable technical and security debt.
Read on to learn how you can improve the security of your applications by automatically running DAST as part of JFrog Pipelines with NeuraLegion. We’ll explain how NeuraLegion’s NexPloit complements JFrog Xray, the JFrog DevOps Platform’s universal software composition analysis (SCA) solution for identifying open source vulnerabilities and license compliance violations.
We also invite you to watch “Putting the Sec in DevSecOps,” a recent joint webinar from JFrog and NeuraLegion. NeuraLegion CTO Bar Hofesh and JFrog Developer Advocate Sven Ruppert do a deep dive into AppSec testing automation, and into our companies’ combined solution.
Automated Security Testing as Part of Your JFrog Pipelines with NeuraLegion
NeuraLegion’s NexPloit, an innovative, AI-powered and developer-focused DAST scanner, removes the pain points and limitations of legacy DAST tools. It delivers AppSec testing automation for your DevOps and CI/CD pipelines, so you can test your web apps and APIs.
Key features include:
- Seamless integration into your pipelines (like JFrog)
- Developer friendly, using proprietary Smart Scanning to remove complicated test setup and configurations so you can carry out the right tests against your target
- Testing of every build / commit, making sure scans can complete at the speed of DevOps while effectively identifying security vulnerabilities
- Removal of false positives in an automated manner to avoid delaying (and annoying) developers (and the security team) by having them waste hours sifting through false positives
- Clear and effective remediation guidelines
NeuraLegion’s integration with JFrog Pipelines means you can have security testing automation on every commit, as part of your deployment pipelines. Getting set up is a breeze. Check out our example below to start getting security compliance on every build!
Integrating and Configuring JFrog and NexPloit
For this example, we will use a vulnerable application in a GitHub repository and set up a JFrog pipeline. We will run an initial security scan using NeuraLegion’s DAST scanner NexPloit against the target, where JFrog will break the build as per our setup. Following another commit, JFrog will automatically scan for security issues on the new build.
You will need to set up a free NexPloit.app account to run the security tests. You will also need JFrog Pipelines. You can try it out with a JFrog free cloud trial, which also includes JFrog Artifactory and JFrog Xray.
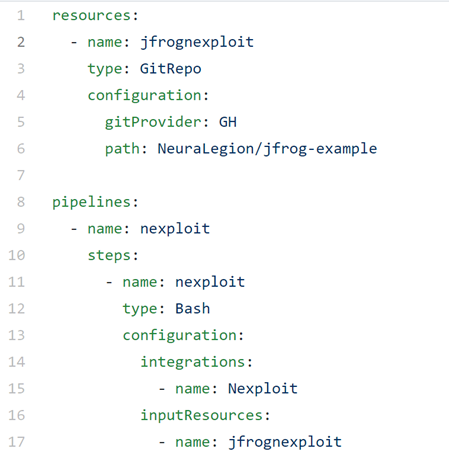
The code repository for this example contains a publicly available repository of a sample vulnerable application and the corresponding JFrog Pipeline YAML file. Feel free to use this target as a test project.
This YAML file contains the configuration for the security scanning, and the pipeline itself (called nexploit), with details of the repo and execution steps.
We can see a Git repository as a JFrog resource, and can use this repository for any events, such as pushing a new commit, as a trigger to run a security scan.
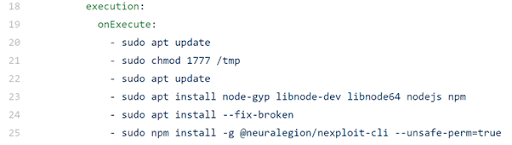
The execution steps are:
- Set up our environment (NodeJS)
- Install NexPloit CLI utility – to use the Nexploit API, enabling you to run, poll status and stop scans
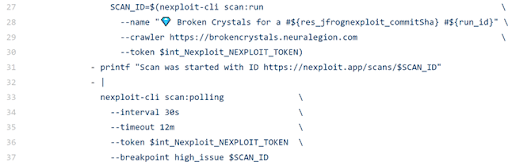
We then have details of the scan setup, detailing:
- A crawler will be used on the target to detect the attack surface
- NEXPLOIT_TOKEN – a token required to use the Nexploit API (see below how to get this)
- The length of the scan
- Breakpoint – in this instance the build failing on detection of a high severity vulnerability
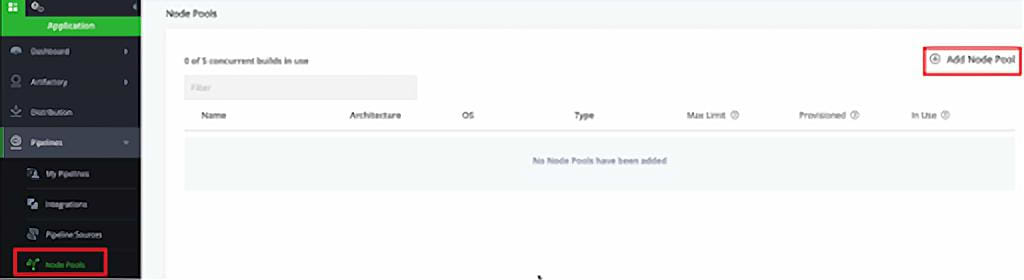
First things first: Let’s set up an automatic scan in JFrog Pipelines.
Go to Node Pools > Add Node Pool, and configure.
Next steps: We need to add our integrations. If you haven’t already, our GitHub and Nexploit.app integrations need to be added.
Integrating GitHub with JFrog Platform
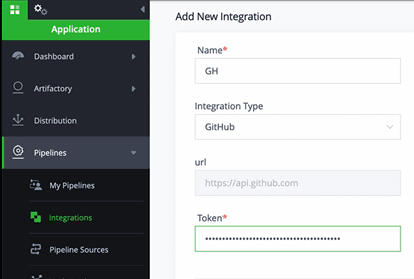
Let’s get the GitHub Token.
In GitHub, go to Settings > Developer Settings > Personal Access Tokens > Generate New Token
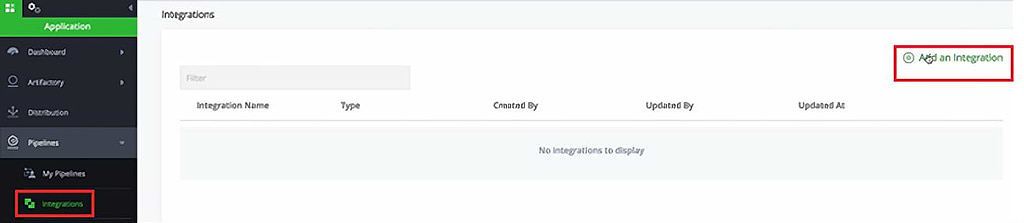
Copy this token and in the JFrog Platform go to Integrations > Add an Integration
Now give the integration a Name, Type and add the Token
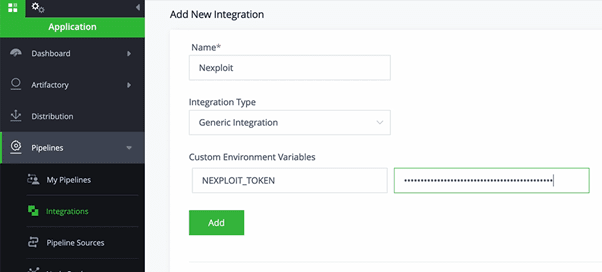
Integrating NeuraLegion’s Nexploit.app with JFrog Platform
We follow the same process with a ‘Generic Integration’ type. You’ll need to generate a NEXPLOIT_TOKEN via your nexploit.app account.
In nexploit.app, go to User Settings > Create New API Key > Select All > Create and copy the token. This can be used in the JFrog Platform to set up the integration:
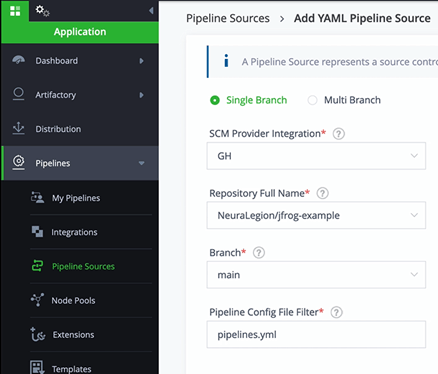
Now let’s go to Pipeline Sources > Add Pipeline Source > From YAML
Select your GitHub Integration for SCM Provider Integration, Repository Name with JFrog configuration and the Branch, before selecting ‘Create Source’.
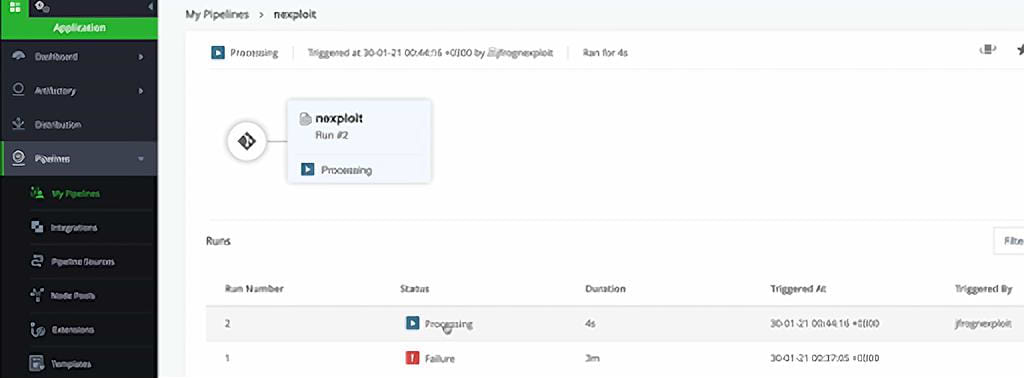
You’re now ready to build and run a new scan!
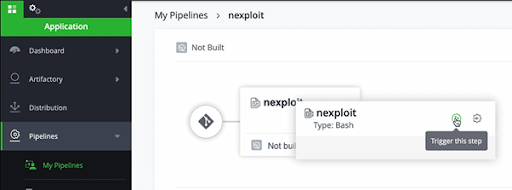
Go to: Pipelines > nexploit > nexploit > Trigger this step
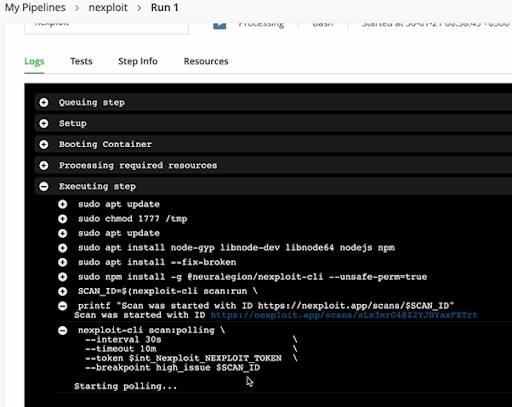
You will then get a view of your current CI process.
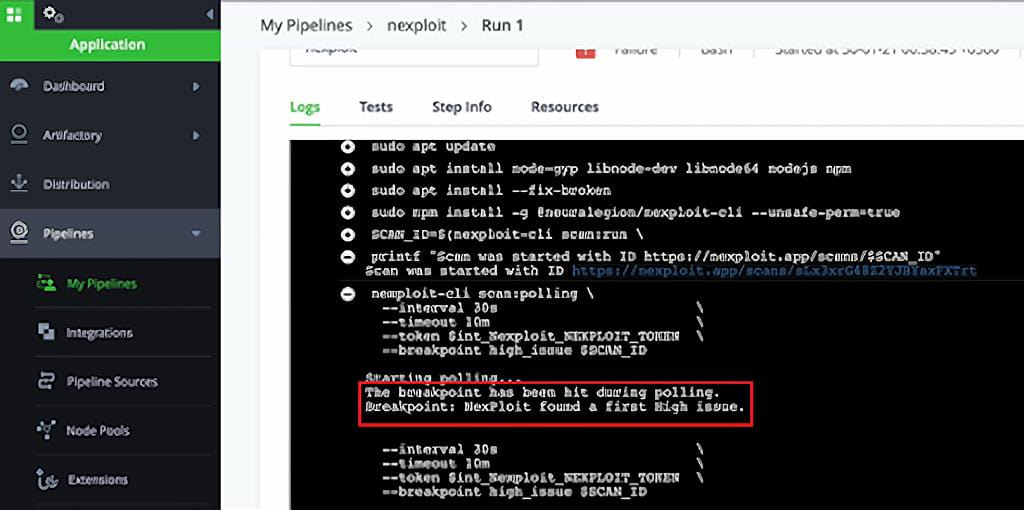
In the image above, we can see the DAST security scan has started and we are polling the results.
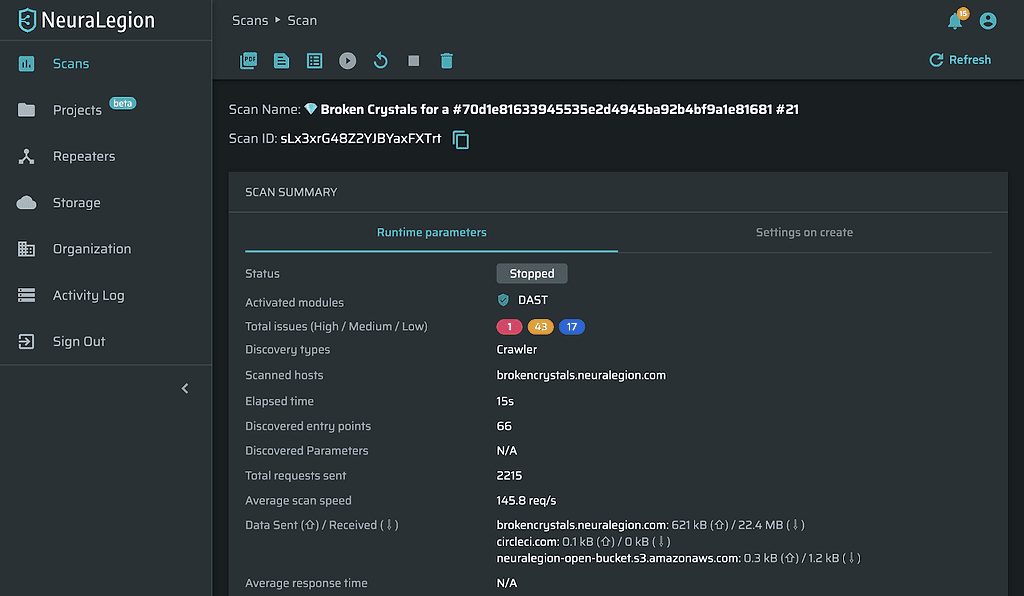
We can now look at the security scan status and results via the NexPloit dashboard on the nexploit.app to check the status, using the link provided.
We can see that the scanner has already detected a number of automatically validated security issues on the target that are ready to be fixed without the need for any manual validation.
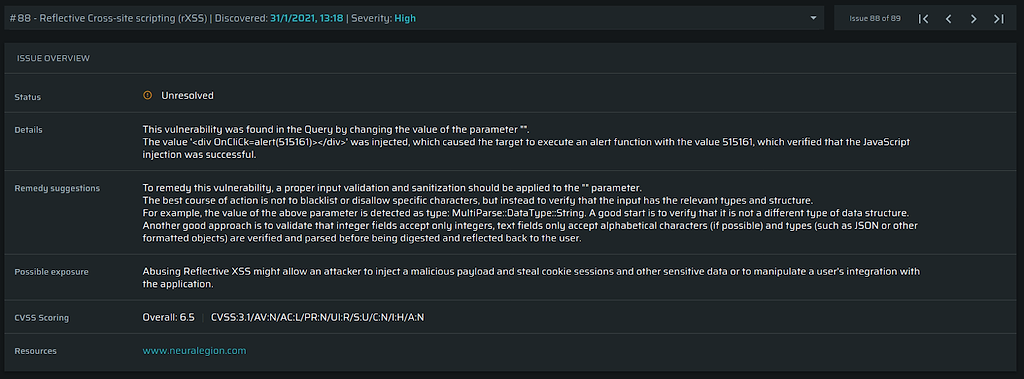
The results provide developers with everything they need to understand the issue, how to replicate it, and more importantly, how to fix it, with remediation guidelines:
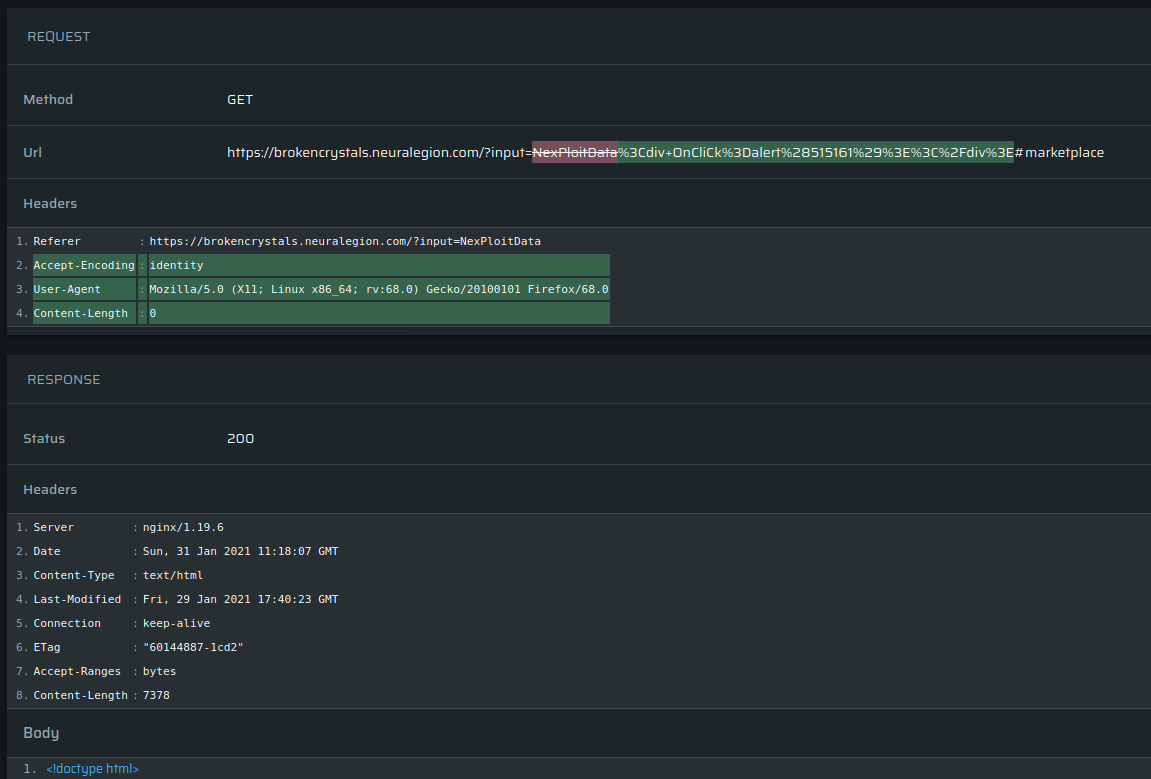
The Request, with a diff-like view (what was added/deleted) is provided, as well as the Response, Headers and the Body.
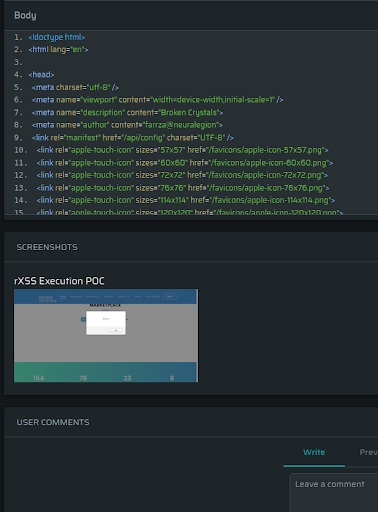
In this particular example of a Cross-site Scripting (XSS) issue, we also provide additional evidence in the form of a screen shot as a proof of concept, so you know the vulnerability is there:
Nexploit integrates with JIRA so a ticket can be automatically raised with each issue detected, or you can use the JIRA and JFrog Pipelines integration.
On detection of the High severity issue, the build is failed and the scan is stopped.
The scanner is set to automatically scan every time there is a change committed in the repository, enabling developers to run an automated, comprehensive and dead accurate security scan on every commit.
Security Testing … at the Speed of DevOps
As you can see, connecting NeuraLegion’s DAST AppSec scanning into your JFrog pipeline is simple and straightforward. You can also continue to use your other CI integrations such as Jenkins (via NeuraLegion or JFrog), and ticketing systems like JIRA.
Whether testing your webapps or APIs (SOAP, REST, GraphQL), the results produced are organized in a developer-friendly way so you can understand the vulnerabilities with everything needed to remediate and fix them, with fully validated results and no false positives.
With JFrog and NeuraLegion, you can now create end-to-end deployment pipelines in minutes and have security testing as an integral part, without slowing you down, without causing too much noise, and resulting in secure products being deployed with a streamlined DevSecOps process in place.
Watch the webinar, where we look at JFrog Pipelines and JFrog Xray, and offer a demo of NeuraLegion’s platform, so you can start to shift security testing left.
If you want to get started today, you can integrate NeuraLegion into your JFrog CI/CD pipeline with a free NeuraLegion account.