SSDLC program
To ensure the safety of the JFrog Platform for our customers, our security team implemented a wide security program that integrates with the software development lifecycle (SDLC) of the company.
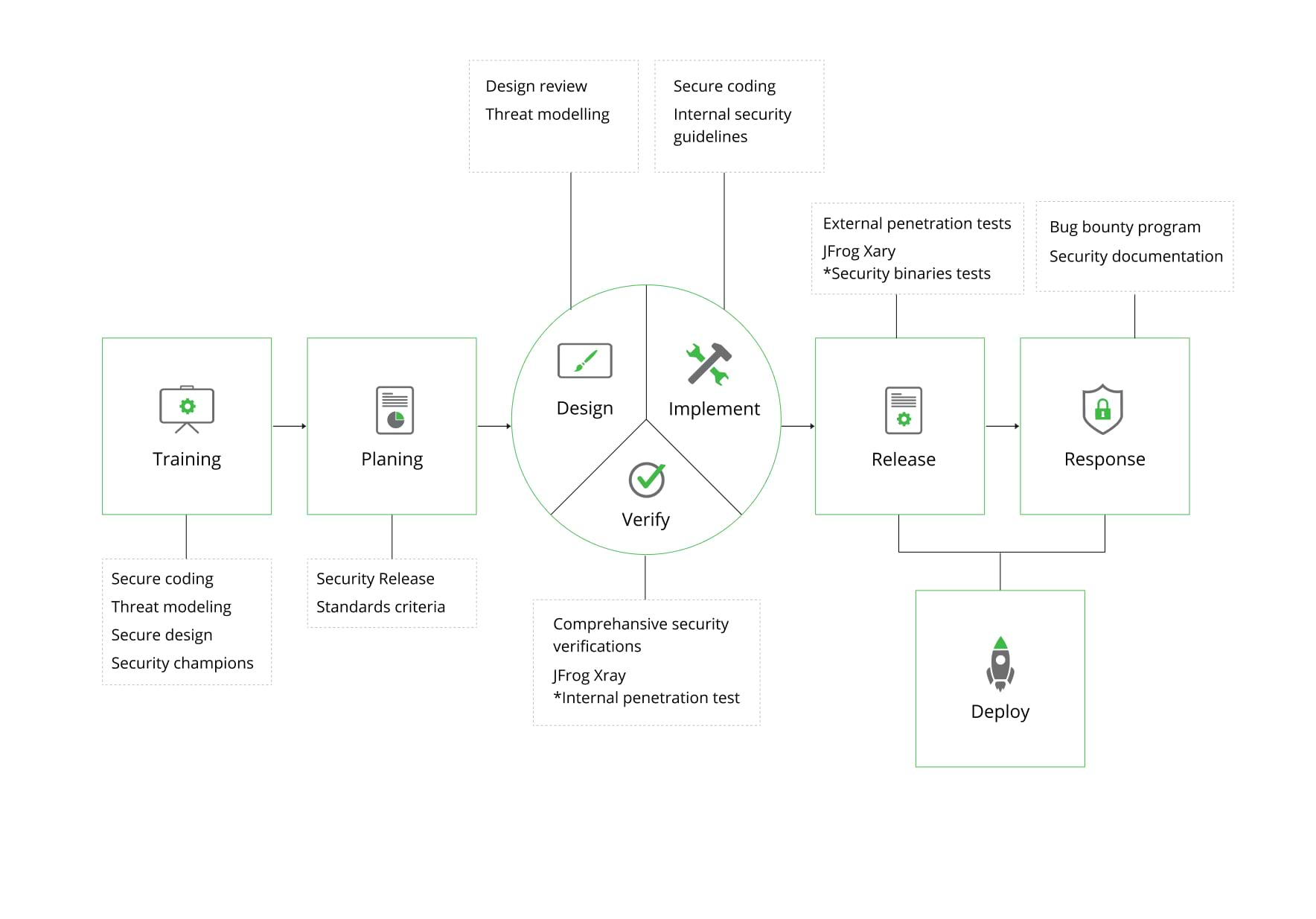
Secure Development Training
JFrog’s R&D teams regularly receive relevant training which increases their awareness, knowledge and capabilities to design and develop features more securely.
Security Champions Program
JFrog’s R&D Security Champions are responsible for establishing the application security posture within the R&D teams and increasing the effectiveness of JFrog’s application security program, while strengthening the relationships between internal teams and security leads. The Security Champions Program enables security to scale throughout R&D and help to build a top-notch application security culture at JFrog.
Security Risk Analysis
Secure Design
The goal of JFrog’s security design review process is to identify security improvements for JFrog applications’ development as early as possible to prevent weak design decisions.
JFrog’s engineering teams follow secure design principles, such as “least privilege” and “fail safe”, from the earliest stages of JFrog software development process.
Threat Modeling
Threat modeling is a core element of the JFrog secure development lifecycle. It’s an engineering technique we adopt to help us identify threats, attacks, vulnerabilities, and countermeasures that could affect our applications. We use threat modeling to shape our applications’ design, meet our security objectives, define security requirements and reduce risk.
Security Testing
Static application security testing (SAST), or static analysis, is a testing methodology that analyzes source code to find security vulnerabilities that make applications susceptible to attack. SAST tools scan an application before the code is compiled.
SAST tools give developers real-time feedback as they code, helping them fix issues before they move the code to the next phase of the SDLC. This prevents security-related issues from becoming an afterthought.
DAST (Dynamic Application Security Testing) solutions evaluate application inputs and outputs, focusing only on the attack surface. DAST solutions test running binaries to find vulnerabilities that SAST tools can’t, such as those found in dynamically generated code.
JFrog incorporated SAST and DAST tools as part of our development lifecycle and runs SAST and DAST scans every time code is checked in, as well as when code is released.
JFrog Xray – Software Composition Analysis (SCA)
JFrog Xray is a universal software composition analysis (SCA) solution that natively integrates with Artifactory to give developers and DevSecOps teams an easy way to scan binaries. It proactively identifies vulnerabilities in source code and license compliance violations before they manifest in production releases, offering unique application-security value.
JFrog Xray continuously scans the JFrog Platform to secure all packages stored at a binary level and helps to achieve control and trust earlier in software release cycles by automating security workflows as part of our CICD pipeline.
JFrog Xray natively integrates with Artifactory to deliver a primary hub for secure software packages, which include open-source binaries that have been downloaded by developers.
We’re strong believers in the “shift left” approach, in which detection and remediation of security and compliance issues start early and continue throughout the SDLC, as opposed to when the code is ready to be shipped to production.
Using our own JFrog Xray product, the JFrog security team performs continuous, multilayer analysis of our containers and software artifacts to detect vulnerabilities and license compliance issues across our internal CICD pipeline.
JFrog’s internal policy will cause builds to fail when certain security vulnerabilities are detected, and our engineering teams remediate the vulnerabilities according to the terms of our internal SLA, which is aligned with industry standards.
Read more about disclosing and fixing security issues that have been found in JFrog products.
Penetration tests
To complete our development lifecycle, our products and features are pentested on an ongoing basis, both internally, by the JFrog application security team, and externally, by third-party top experts.
Bug bounty
The JFrog security team manages private bug bounty and private vulnerability disclosure programs, hosted on HackerOne, as part of our commitment to improve our product security.
Click here for more information on how to report security issues to JFrog.
Change Management
The JFrog security team keeps track of and reviews all changes to our products to ensure their high quality and alignment with our business objectives. JFrog’s security team runs secure code reviews on selective changes in order to adhere to our security and compliance requirements.
Web App and API Protection
As part of our multi-layer protection approach, JFrog uses a cloud provider-managed DDoS mitigation service. JFrog utilizes a next-gen WAF, an API protection, advanced rate limiting and bot protection.




