Everything is software now!
JFrog Saas solution offers top-notch security for both JFrog products and infrastructure.
As JFrog SaaS solution is dynamic, scalable, and portable, it requires special security controls for workloads and data while at rest and in transit. These security controls allow our end users to scale efficiently.
Customer Account Segregation
Each customer account is deployed with a unique ID to guarantee adequate separation.
Each customer account is granted with its own unique and narrow role, based on least privilege principle. We grant just the permissions which are required to perform tasks and access shared resources, such as databases and cloud object storage.
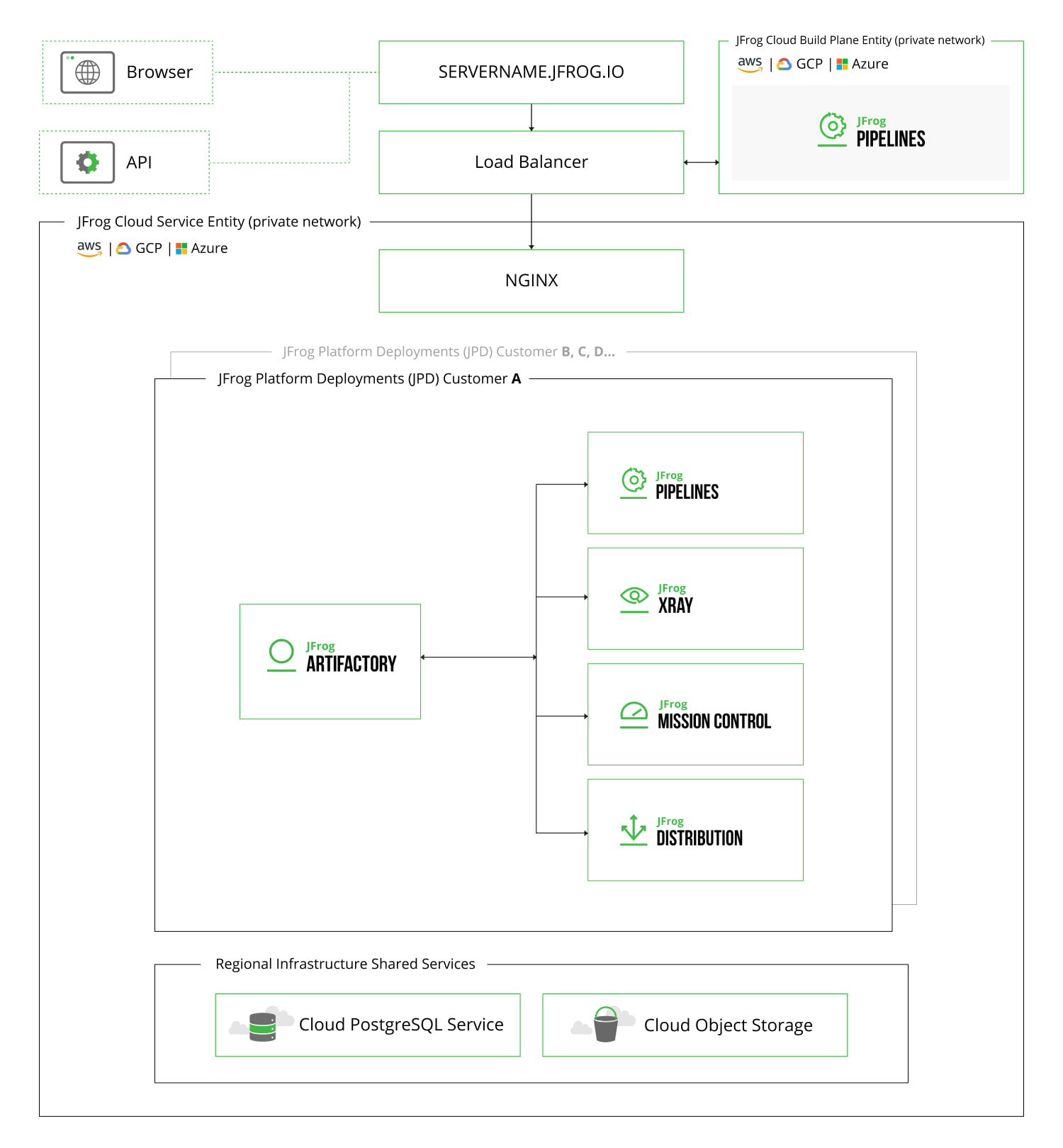
The default and automatic deployment of JFrog SaaS solution is on a shared environment including the following resources:
- The load balancer is a shared component at the region level.
- The applications’ database schema and role are dedicated for each customer. The applications’ database is a cloud provider managed service, shared at the region level.
- Each customer has its own unique role with permissions for their own files. The applications’ filestore is a cloud provider managed service, shared at the region level.
- Each customer has compute resources with limited quotas. The applications’ compute is a cloud provider managed service, shared at the region level.
- Network policies are implemented to prevent direct traffic across different customers.
Data Center Security
JFrog’s production environment complies with top-tier providers with the highest data privacy, security standards and practices.
Find out more information about the security of the Amazon, GCP & Azure cloud platforms.
Cloud Protection
As part of our multi-layer protection approach, JFrog uses a cloud provider-managed DDoS mitigation service. JFrog utilizes a next-gen WAF, an API protection, advanced rate limiting and bot protection.
Cloud security hygiene
Cloud security scanning tools (including next-gen CSPM solutions) are used regularly to enforce security best practices.
Least privilege
JFrog has defined access roles for each system and service based on least- privilege principle.
Preventive protection
JFrog has defined global cloud security policies at the organizational level to prevent the creation of misconfigured resources.
IaC security
Infra as Code is used as a crucial pillar that aligns DevOps, Security, and compliance for infrastructure management processes.
Image & container hardening
All JFrog application images are constructed using hardened base images and deployment configurations for maximum security.
Images are being scanned using JFrog’s Xray as part of our CI build process.
Architecture
JFrog SaaS solution has a well architected, secured, high-performing, resilient, and efficient infrastructure for JFrog products and workloads. JFrog supports hybrid solutions for customers wishing to combine self-managed with SaaS solution, on any of the three major cloud providers: Google Cloud Platform (GCP), Amazon Web Services (AWS), and Microsoft Azure.
JFrog offers a multi-tier architecture for your deployment including high-availability systems, backups and more.
Real Time Platform Status
JFrog communicates the status of our platform and its incidents https://status.jfrog.io/.