Tour Terraform Registries in Artifactory
Why should you keep Terraform module, provider, and backend registries in a binary repository manager like Artifactory? Because, like your builds, packages, and other artifacts, your Terraform files are a key part of your software supply chain.
Terraform is a widely used open source infrastructure-as-code (IaC) software tool to manage the entire lifecycle of cloud service infrastructure. By codifying cloud APIs into declarative configuration files, Terraform enables a uniform way to provision, adjust, and tear down infrastructure in a cloud provider, across many instances.
By keeping your Terraform modules, providers and state files in Artifactory, they become part of your software supply chain’s secure circle of trust, protected through the JFrog Platform’s authenticated access, checksum verification, and fine-grained permissions management. Artifactory can proxy remote Terraform Modules/Providers with caching to keep you independent of the network and the remote resource.
Incorporating your Terraform artifacts with your packages and build metadata in Artifactory, you gain the most direct traceable path of what is being delivered into production.
Taking the Terraform Tour in Artifactory
For this tour, we will focus on the two type of Terraform artifact registries in Artifactory:
- Terraform – Which allows users to create repositories for both Modules and Providers
- Terraform Modules – a set of one or more Terraform configuration (`.tf`) files in a single directory. Each file uses a declarative language to tell Terraform how to manage a given collection of infrastructure.
- Terraform Providers – Terraform plugins that enable users to manage an upstream API to configure a cloud platform or service.
- Terraform Backend – a remote state storage provider with important management features. Terraform state files (terraform.tfstate) map real world resources to your configuration, keep track of metadata, and to improve performance for large infrastructures.
Artifactory supports local repos for Terraform backend repositories, and all the below types of repositories for both Terraform module and Terraform provider registries:
- Local Repositories – Private registries that are accessible only within your organization’s network.
- Remote Repositories – A proxy of an external registry (such as the public Terraform registry) that provides a cached version for locality and availability.
- Virtual Repositories – A logical repository that encapsulates any set of local and remote repositories of the same package type, accessed from a single URL.
Artifactory Terraform Repositories
In this example, we will see how a Terraform module can be published to Artifactory using Jfrog CLI.
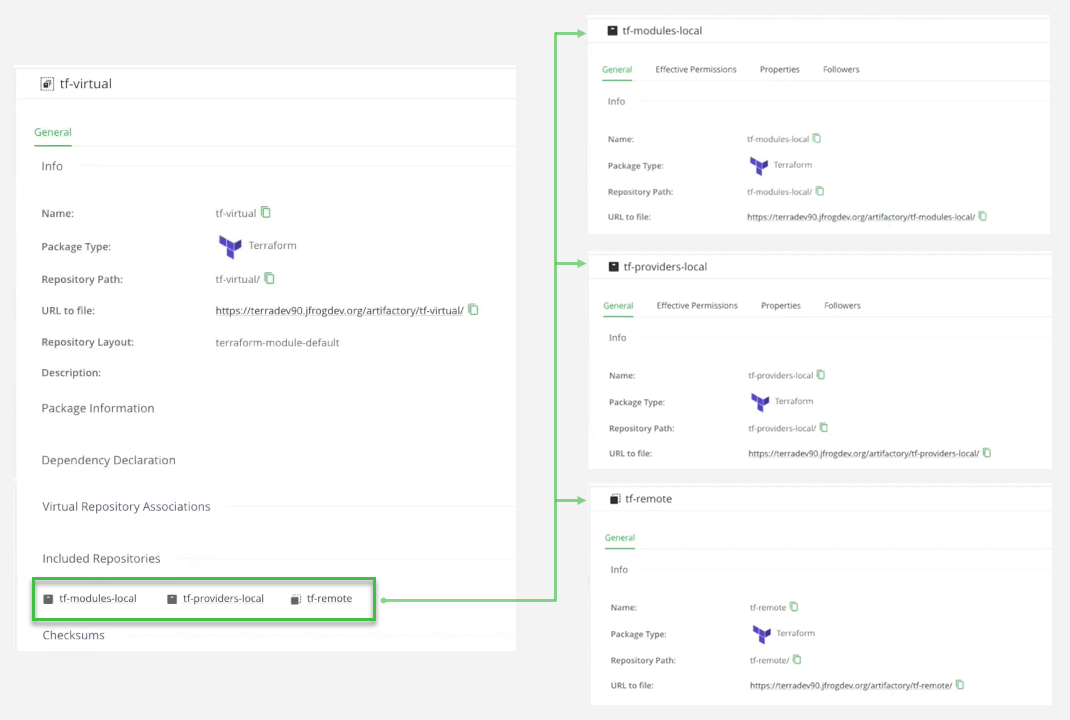
We have established these Terraform repositories in Artifactory:
- tf-modules-local – a local repository of privately published Terraform modules.
- tf-providers-local – a local repository of preferred or custom Terraform providers.
- tf-remote – a remote repository that proxies the public Terraform registry maintained by Hashicorp.
The virtual Terraform repository tf-virtual aggregates all three of the above Artifactory repositories, providing read and write access to the group through a single URL. The virtual repository is configured to resolve requests from the local repositories first, so that a module or provider from the public Terraform registry will be provided only if a local version isn’t available.
Publishing Terraform Modules to Artifactory
On our developer workstation, we have a monorepo of Terraform modules for use with AWS.
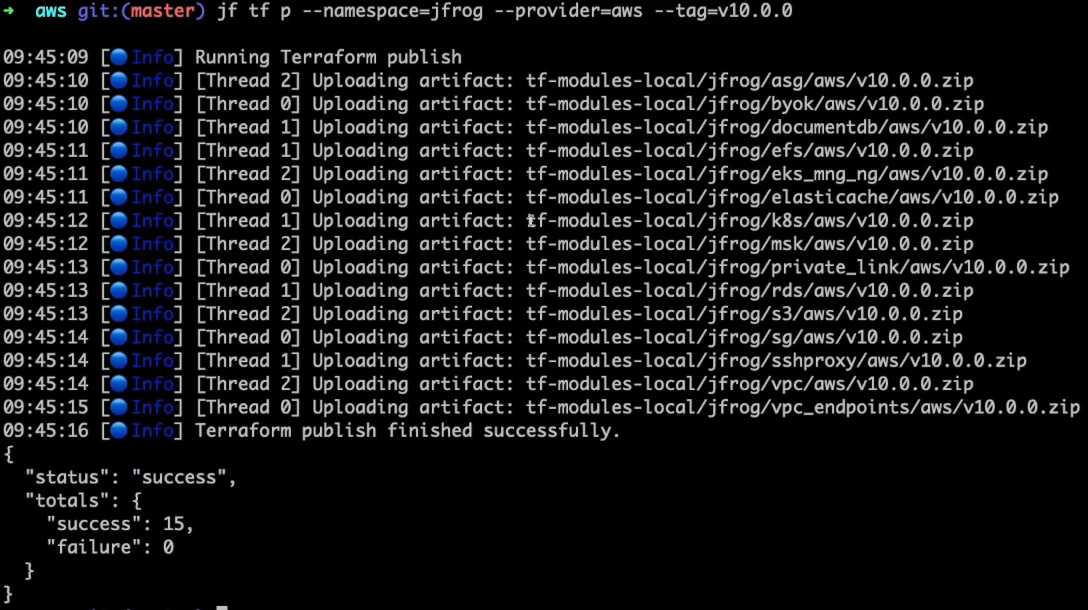
Using the JFrog CLI, we can publish these modules to Artifactory:
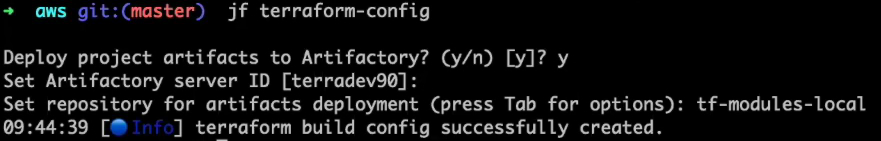
- Configure for publishing to the tf-modules-local repository. This will create a `.jfrog` subdirectory that contains the requested configuration information.
- Publish modules from the current directory to Artifactory. You must specify the namespace, provider, and tag.
All modules are published to Artifactory with the tag specified in the JFrog CLI command line.
Viewing Terraform Modules in Artifactory
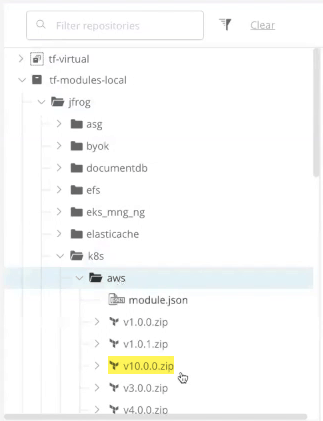
In the JFrog Platform UI, you can browse through all of your published modules and providers. Here, we can see our Terraform modules in Artifactory.
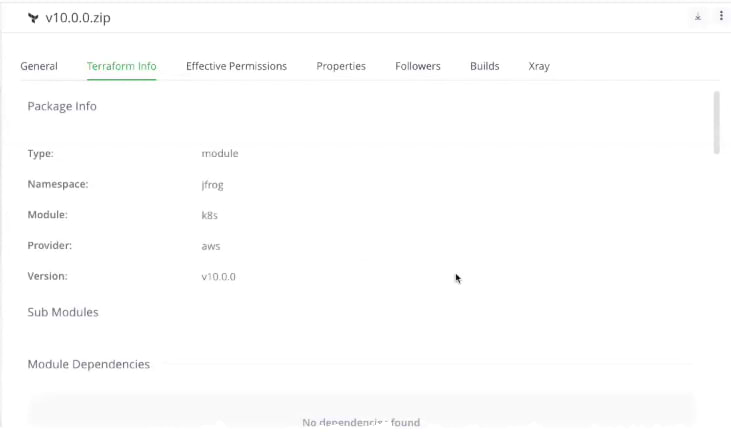
Within the JFrog Platform UI, we can view the information about any of the published modules, including its provider and dependencies. Additionally, you can view the module’s inputs, outputs, and even the `Read.Me` file.
Using Published Terraform Modules
To make use of our published module, we create a `main.tf` Terraform file that resolves modules and providers from the tf-virtual path for the Artifactory virtual repository:
terraform {
required_providers {
aws = {
source = “terradev90.jfrogdev.org/tf-virtual/aws”
}
}
}
module “efs” {
source = “terradev90.jfrogdev.org/tf-virtual__jfrog/efs/aws”
}By accessing the AWS provider through the virtual repo, any preferred or customized version of that provider in the tf-providers-local repository will be used. Otherwise, it will resolve to the latest version available in the tf-remote proxy of Hashicorp’s Terraform registry.
Before we can run a terraform action, we must obtain and save the API token from Artifactory through the standard `terraform login` command of the Terraform CLI. You must Approve the Terraform CLI authorization when prompted by Artifactory.
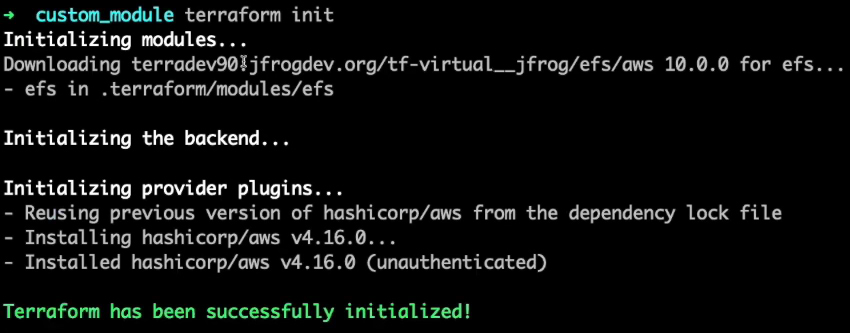
With access to Artifactory now authorized, we can use the `terraform init` command of the Terraform CLI to execute `main.tf` in our current directory.
Since no specific version of the EFS module was specified, Terraform defaults to the latest version we just published to Artifactory (v10).
Artifactory Terraform BE Registry
Artifactory has a local repository implementation that supports Terraform remote backends. It’s easy to migrate your existing backend solution to Artifactory and enjoy many benefits including:
- Support for multiple workspaces
- Built in State locking mechanism
- Built in secure state encryption storage
- Full state files history including publish time and user who created it
- SmartDiff between state files to easily monitor changes
Migrating an Existing Workspace to Use Artifactory Backend
Let’s look at how to migrate an existing kubernetes workspace to use the Artifactory backend. For this example we’ve already created the Terraform backend repository tf-backend in Artifactory.
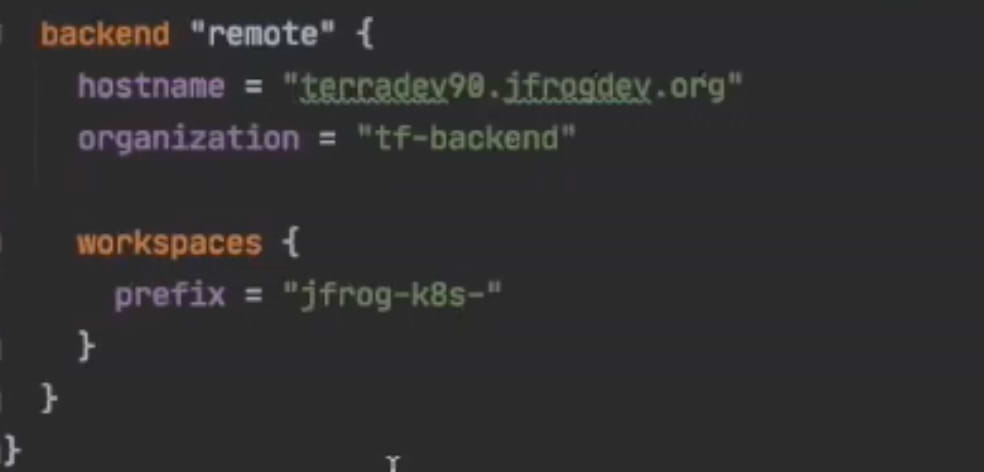
First we will configure our backend to point to the Artifactory TF backend repository.
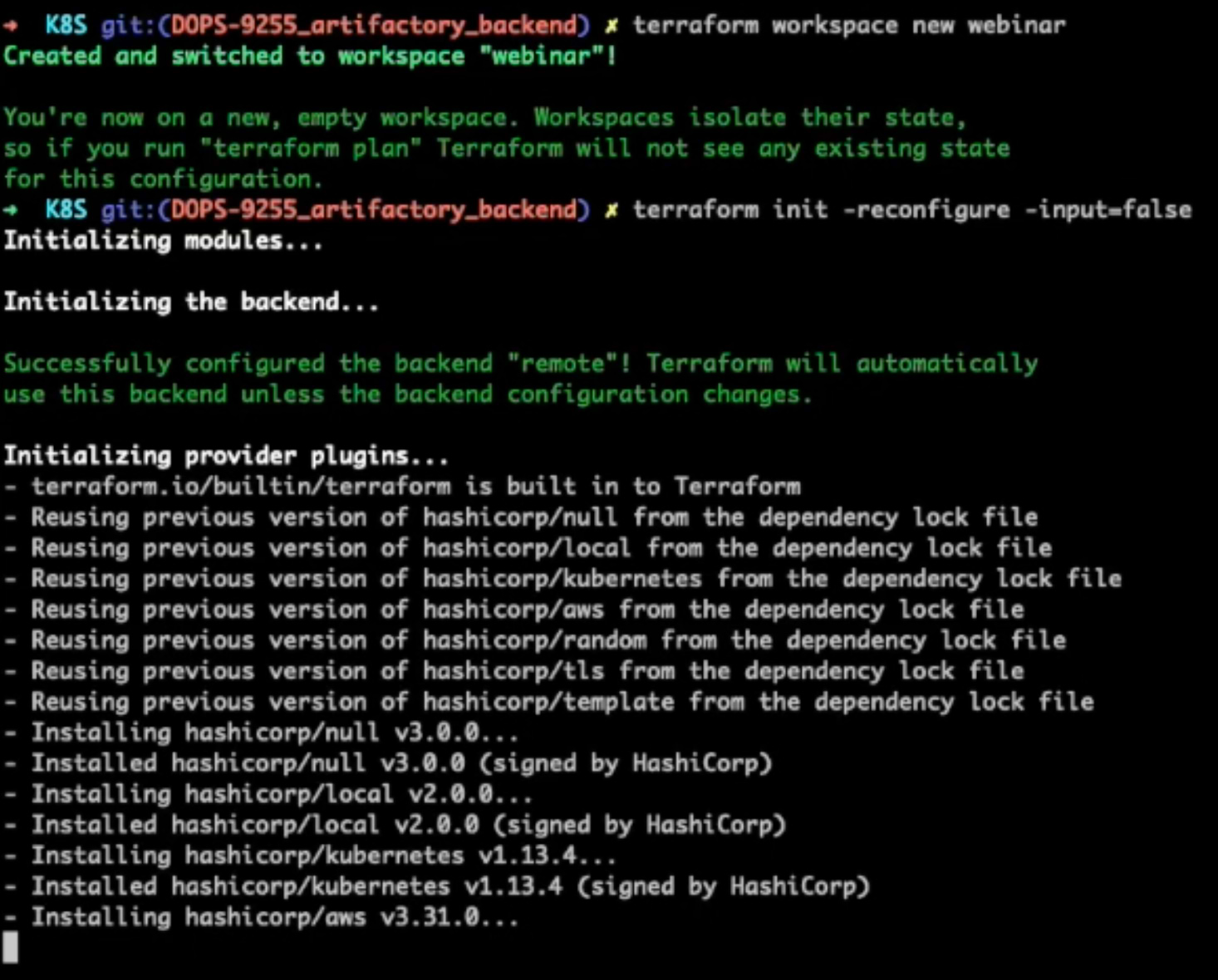
Next we will create a new workspace and run ‘terraform init’. Note, we already have the token for the Artifactory domain from the previous terraform login (see above), so we don’t need to login again to get the token.
Now we’re ready to import our existing state to Artifactory by running the ‘terraform state push’ command.
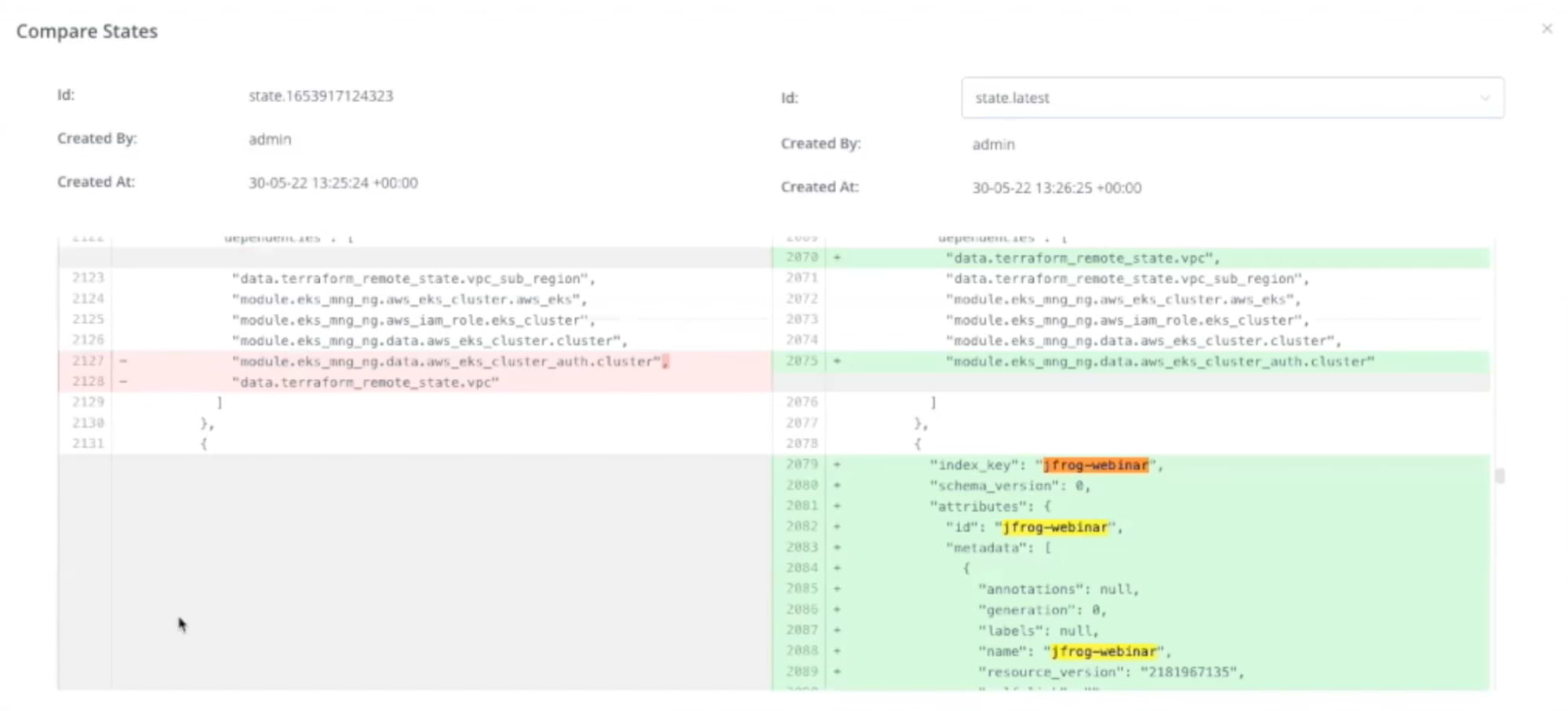
Managing State Files and Comparing Changes
With our state file migrated to Artifactory we can now see how Artifactory makes it easy to manage state files and compare changes between versions.
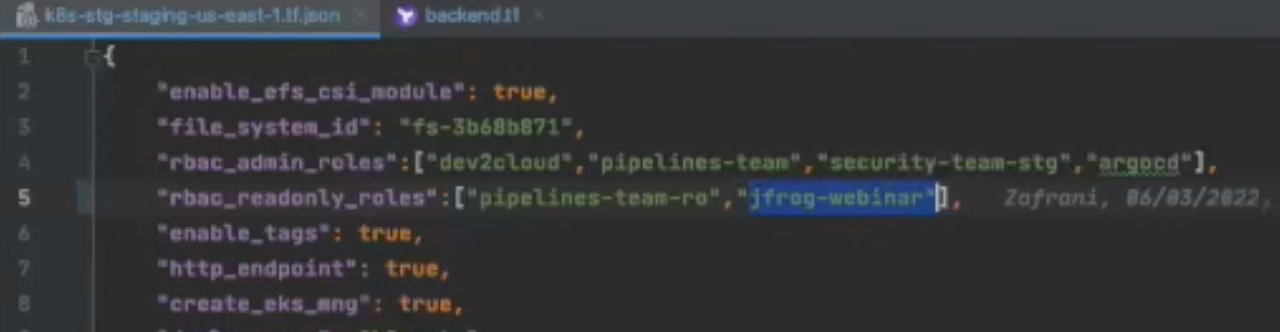
First we’ll edit our existing module adding an additional RBAC rule.
Then we’ll use the ‘terraform plan’ command to preview the changes followed by ‘terraform apply’ in our workspace to apply the changes and create a new state file in Artifactory.
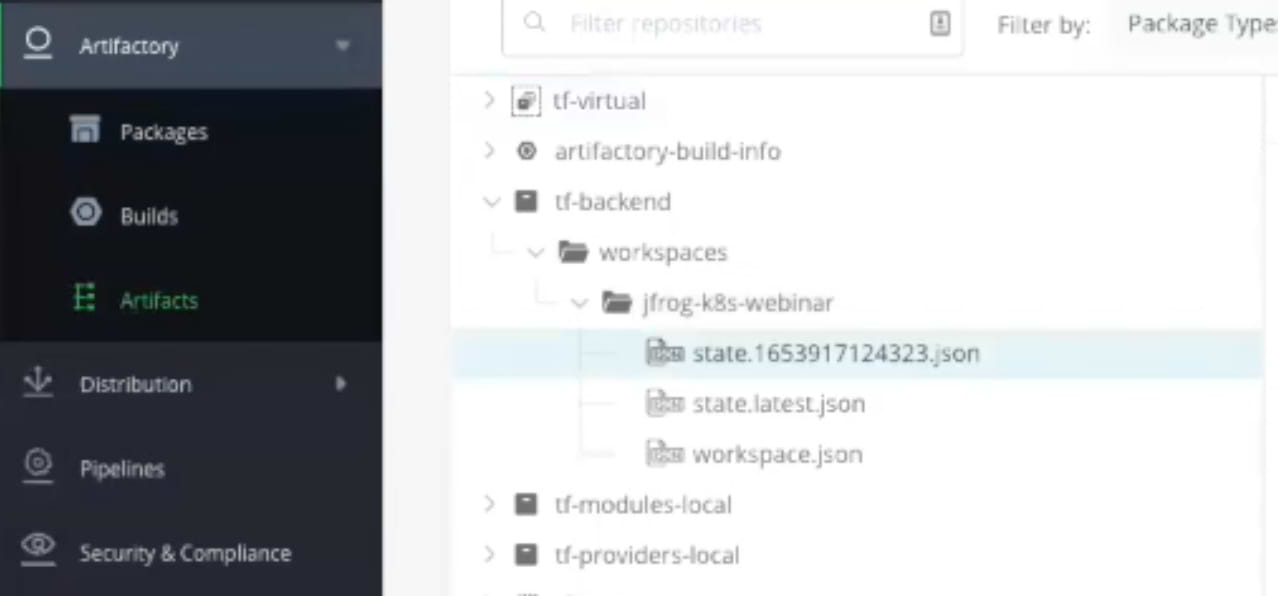
If we head back to Artifactory we can now see both the state.latest.json of our current active state and the state.timestamp.json of our previous state within the tf-backend repository and the jfrog-k8s-webinar workspace
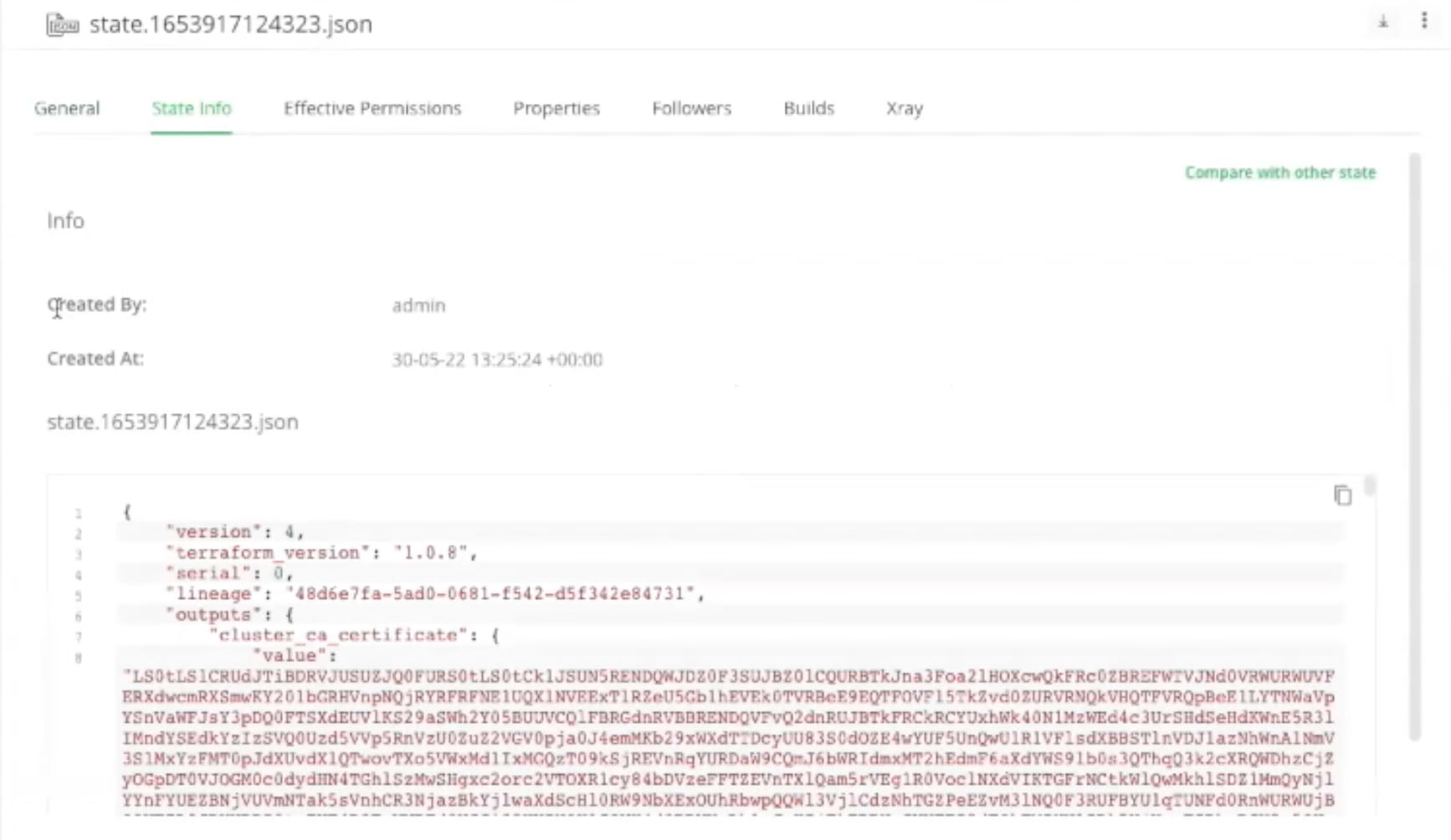
By selecting a state file we can see important information about that file such as who created it, when it was created, and compare it with other states
State Locking
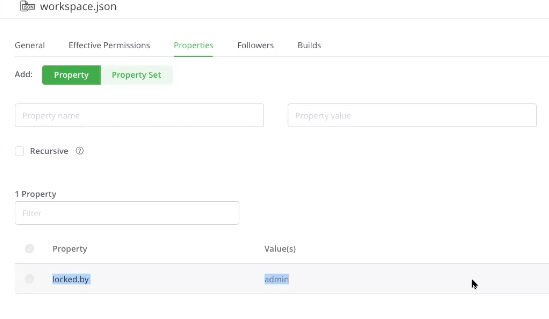
Artifactory provides built-in state locking mechanism. A property called locked.by is added with the value of the user performing the configuration change to the workspace and any other user will be denied updating the workspace during this time and the terraform client will return an error with the message that it is currently locked by the user . Lock will be released once the changes to the workspace is completed
Supply Chain Shapes Clouds
Taking charge of your Terraform registries with Artifactory puts the principles of the JFrog DevOps Platform’s proven binaries-centric approach for successful software delivery to work to further accelerate cloud native development.
These best practices of software supply chain management enabled by the JFrog Platform can be used with your cloud configuration management procedures to empower developers even more.
Don’t just take our word for it. Try it yourself for free.