The Importance of Prioritizing Product Security
Achieving comprehensive security for the products delivered and deployed by organizations is becoming more difficult, due to a variety of factors. A key one is the growing volume, variety and complexity of software and connected devices in use. Another is the overwhelming risk of inherited software supply chain exposures. The result: Companies struggle every day to provide software with optimal security and protection against malicious activities, takeovers, data theft, and commercial sabotage.
With more opportunities than ever for malicious actors to exploit product software security vulnerabilities, manufacturers, vendors, device deployers, and end users face the devastating consequences of lack of security hygiene in the software’s lifecycle.
Our goal in this blog post is to shed some light on the importance of prioritizing secure software development and product security. We’ll also provide actionable advice on the strategy, methodology, and tactics for implementing product security within your organization. While product security is relevant for any organization that delivers hardware or software products, we highlight the specific need and challenges for device vendors.
In today’s climate, especially since the onset of COVID-19, how we work, where we work, and how we operate our facilities have changed significantly. As remote operations and connectivity become standard for the products we deliver and consume, it’s time to rethink the way we secure our software.
To defend against sophisticated attacks, we need to secure products across their entire lifecycle and consider the complete product context and characteristics, such as type of connectivity, software type and underlying operating system. If the traditional approach to cybersecurity focused on securing the network, now, with the proliferation of first-party and supply chain attacks, we must complement network security with product security in order to secure every layer of the organization’s attack surface.
While it plays a vital role in every stage of the product life cycle, product security is a relatively new concept that is not yet well-defined.
Trends in Product Security
At the end of 2018, there were an estimated 22 billion connected devices, a number expected to grow to 50 billion by 2030, according to a recent study by Statista. Every device is at risk for cyber-attacks, and malicious actors are taking advantage of this reality.
Following are a number of trends that are raising the focus on product security for connected and IoT devices.
- Market Demand
Demand for product security has grown across multiple industries, notably consumer electronics, healthcare, and automotive. As seen in the recent US Cybersecurity Improvement Act and ENISA guidelines on securing the device supply chain, these industries are becoming heavily regulated. Additionally, there is a demand from consumers for safer connected products that offer them peace of mind, especially devices for fitness, home automation, transportation, and healthcare.
- Device Evolution
Devices are evolving and modernizing, and their software is starting to resemble, in many ways, server applications and mobile applications. The sheer volume and complexity of these connected devices are expanding the attack surface.
- Emerging Threats
New risks are constantly being introduced by threat actors. A particularly concerning one involves vendor software supply chains. Supply chain risks include intentional backdoors or “bugdoors” (intentional backdoors disguised as bugs) as well as unintentional, known CVEs or other security issues. Whether intentional or not, there is also typical malware like botnets and ransomware that can reside inside open-source and third-party code to which the receiving side has no access.
- Security Solutions
Many layers of device security solutions are aimed at assessing and enforcing security of the network for connected devices from the network. While this is important, network-based security solutions are implemented when devices are already deployed, so they are not always sufficient. They cannot protect against many types of threats, such as software supply chain risks that introduce vulnerabilities into the network through compromised devices or code.
Challenges in Securing Devices
Security stakeholders are faced with the difficult feat of navigating a complex reality.
- Security Challenges
Securing connected devices creates significant overhead for device manufacturers and asset owners. Traditional tools that analyze and identify threats create too many false positives, causing security and engineering teams to waste valuable time and effort, delaying time-to-market. On top of that, there are regulations and standards that impose new technical requirements to comply with.
- Business Challenges
From the business side, device manufacturers and software vendors aim to deliver more products with shorter time to market, without spending too much time and effort on security.
- Organizational Challenges
Security stakeholders and developers are often at odds. Developers want to deliver fast, and security stakeholders will slow down the process, especially due to false positives from traditional security tools.
Product Security – Technology Challenges
Additional challenges for securing embedded devices, connected devices, and IoT include technical hurdles:
- Identification: Low-level compiled code, unique exploits, vulnerability chaining methods, and fragmented software supply chains all make identifying security issues complicated.
- Prioritization: The tremendous amount of security issues, diversity among security standards in various regions and industries, lack of dedicated product security experts, and miscommunication between security and development teams make it hard to focus on what really matters: the vulnerabilities with impact potential.
- Post-deployment: Lack of visibility into deployed devices, slow and ineffective software update process, and strict operation requirements limit the security remediations available for deployed devices.
Implementing Product Security Throughout the Device Life Cycle
The first step in implementing product security is understanding its need and creating awareness across the organization. It requires buy-in from senior leaders and ideally a centralized function to guide the process and ensure actions are taken. During the design phase, it is paramount to create product-specific security requirements to know what to test against later.
In the development phase, throughout the SDLC and CI/CD processes, you must ensure that each new artifact is tested against the set of requirements from the previous phases. In the pre-release phase, it is important to embrace a gatekeeping mechanism to make sure that the device or software within it ships with no exploitable issues.
Last, but not least, in the post-deployment phase, we must ensure there is ongoing vulnerability monitoring and runtime device security. Additionally, it is imperative to keep up with new threats, as well as implement incident-response and problem-resolution programs across all devices in the field.
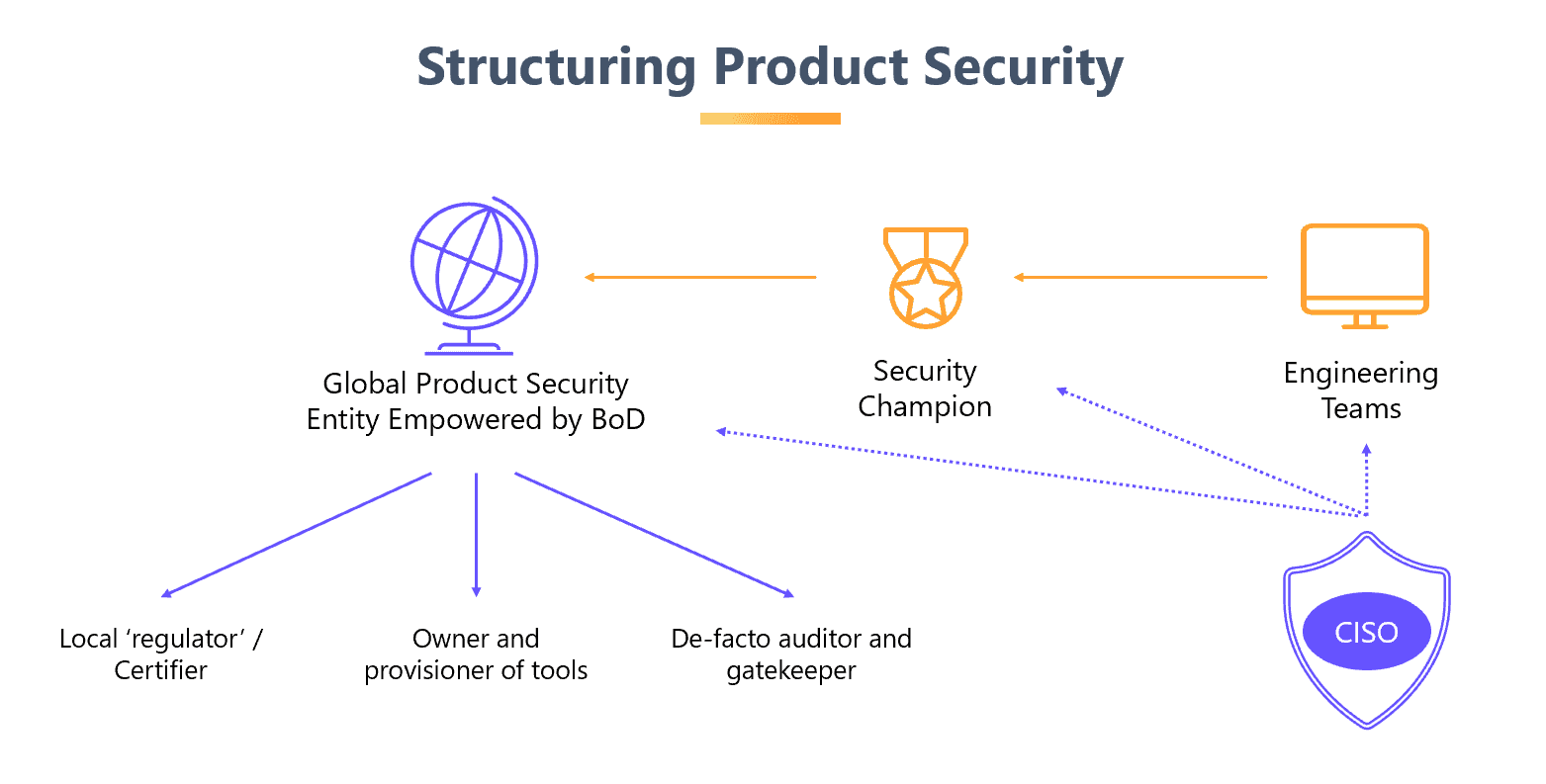
Structuring Product Security
Organizations often struggle with the critical task of creating the right structure for product security. Finding the right mechanism between the management, developers, and security stakeholders is not easy. Our recommendation is to invest heavily in building a global entity that not only defines the processes but becomes the de-facto regulator and enforcer for product security. The success of this structure is highly correlated to whether the executive layer empowers the global team with the proper budget and authority.
Conclusion
Setting up a robust product and software security process will not happen overnight, but with proper intentions, planning, and cooperation from all involved parties, it is achievable and scalable for organizations of all types and sizes.
For more information about JFrog’s security offerings, please visit the JFrog Security page.