From zero to breach in seconds: Why you need to focus on software supply chain security now
AppSec themes and highlights from RSA Conference 2023
The RSA Conference 2023 addressed several key issues and trends in the cybersecurity industry. Generative AI was a key topic of discussion, with attendees, executives and policymakers seeing its potential in both offense and defense in the cybersecurity arms race. The White House’s National Cybersecurity Strategy was also a topic of conversation across panels and keynotes, proposing new regulations to establish baseline standards of cybersecurity and increased public-private collaboration in cybersecurity defense and threat disruption.
In this article, we sum up the three major themes from RSAC, plus trending topics covered during our 1:1 conversations with the attending DevSecOps community.
AI is a double-edged sword in software development
Modern organizations with modern infrastructures are working at high speeds to develop mission-critical applications. To keep pace, developers are relying on AI and ChatGPT to help them write code, which can inadvertently introduce malicious packages and CVEs into their software. AI can also feature as part of the solution with machine learning algorithms being utilized as part of the vulnerability identification automation. While AI can play an important role in software development, its risks shouldn’t be overlooked and should be utilized with caution by software development teams.
Enterprises favor platforms over point solutions
Attendees and security experts emphasized the increasing complexity of the cybersecurity landscape and the proliferation of point solutions. However, they agreed that platforms were a better option for enterprises, as they help minimize ‘tool sprawl’. It is becoming evident that the era of relying on point solutions for securing the software supply chain is over. A prime example is that even the most technically savvy teams are struggling to connect disparate complex security solutions into their DevOps and software supply chain workflows. Complexity can result in unintended gaps in coverage and poses its own security risk. A platform solution can also facilitate tool consolidation.
Security expertise embedded into the software supply chain
Another conversation point in some of the keynotes and panel sessions was the talent shortage in cybersecurity being a major concern. Many executives and policymakers expressed a need for startups to develop solutions that make advanced cybersecurity accessible to the non-expert and less resource-intensive for smaller businesses and everyday users to deploy.
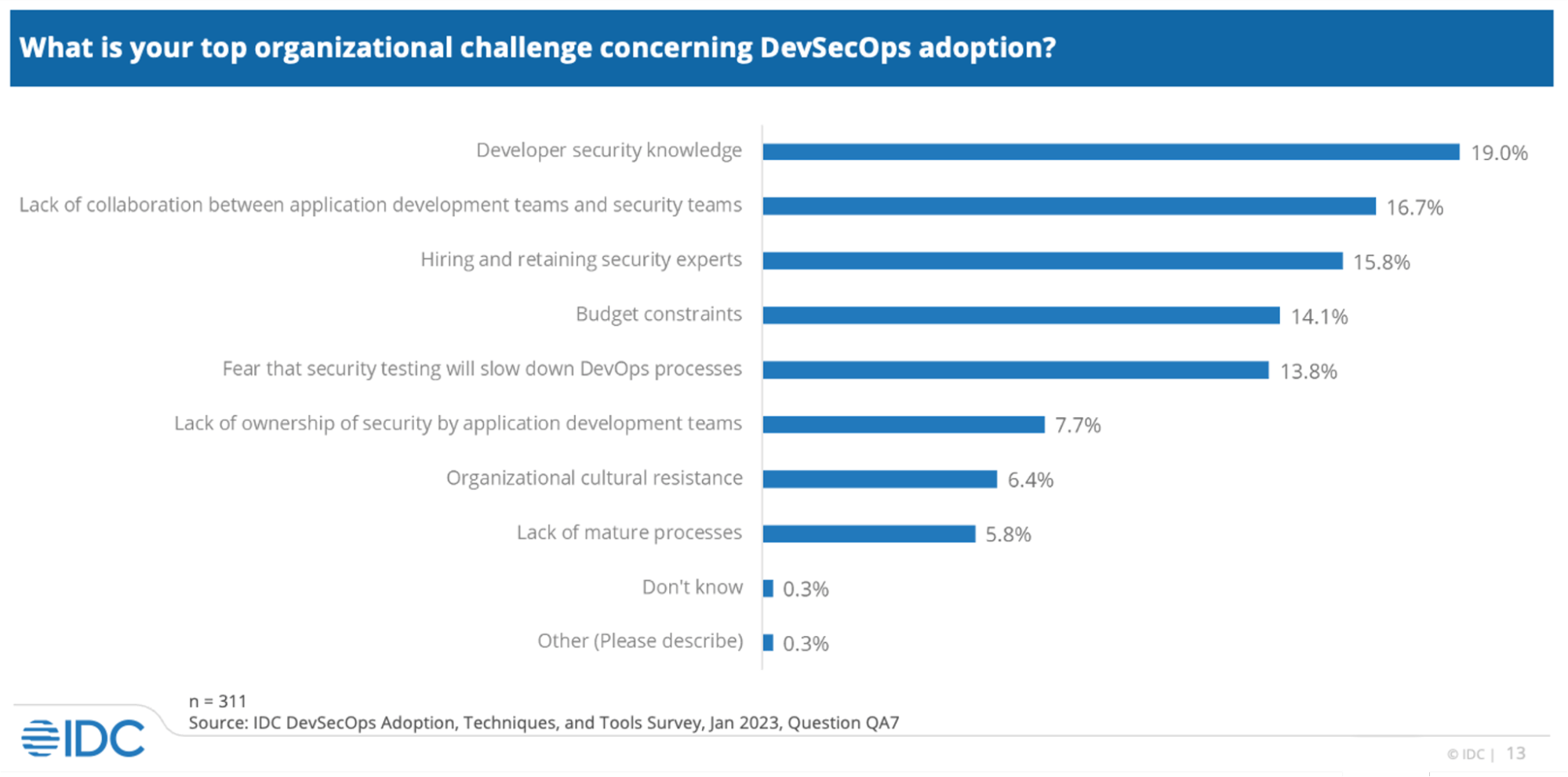
“As organizations attempt to shift security earlier in the SDLC, developer security knowledge constrains their ability to do so. Collaboration between development teams and security, as well as hiring/retaining those with security skills, continue to be challenges.” *
Feedback from the community
In between keynote sessions, we had the opportunity to chat with attendees and here are some notable themes that came out of those 1:1 connections.
Developers, product security and DevOps engineers are struggling with:
- Too many vulnerabilities to fix (inc. false positives)
- Heavy manual efforts needed by security experts
- Developers use OSS from public repositories and other unreliable sources
- Using multiple AST security tools with possible blindspots
We were able to demonstrate how to address these pain points and how we approach software supply chain security from a different and contextual perspective. We understand that source code analysis is not enough to truly analyze the context of CVEs and uncover true contextual understanding. It can only be achieved by looking at the software binary, which contains much more information than source code alone.
Here are the top three security features that most resonated with attendees:
- Contextual analysis to reduce false positives and remediation workloads with a focus on exploitable CVEs. This involves detailed analysis of the vulnerability, and their applicability to the application. The capability also delivers specific remediation advice to the fingertips of users.
- Cover beyond source code and CVEs, and identify hidden vulnerabilities with binary-focused secrets detection.
- Understand the impact and blast radius of vulnerabilities with the JFrog Platform, giving you a true understanding of what you need to fix.
JFrog was recognized by Cyber Defense Magazine for having the Most Comprehensive DevSecOps offering – winning the Global InfoSec Award for 2023. Cyber Defense Magazine received over 4,300 entries for this award from companies worldwide who manage, create, and offer information security products and services. Less than 10% of the nominees were picked as WINNERS for having an incredibly innovative product with a focus on preventing tomorrow’s breaches today. Congratulations team!
We’re very proud of our Security team & the extraordinary innovation delivered in JFrog Xray + JFrog Advanced Security, which won the Global InfoSec Award for Most Comprehensive #DevSecOps solution at #RSA2023. Congratulations Frogs & to all who were recognized this year! pic.twitter.com/H6TSHDZ8nz
— JFrog (@jfrog) April 27, 2023
With 600+ vendors, 700+ speakers, and 26,000+ attendees, RSAC ‘23 was a major indicator that protecting our data, infrastructure, networks, applications, and identity is a common goal within the developer, DevOps, and security communities. The JFrog Software Supply Chain Platform was built to meet modern demands across developers, operations and security teams.
Learn more: Register for the upcoming webinar Trusting your Software Supply Chain Security with DevOps Agility – May 16th.
Join us at swampUP 2023: Register for the upcoming DevOps and DevSecOps in-person user conference – Sept 13th, in San Jose, CA. Experience practical demos, learn security best practices, like how to shift-left, and hear from leading tech experts and industry peers so you’re ready for what comes next.







