Proactive Vulnerability Management is a No Brainer for Security, but…
In December 2022, the US Cybersecurity and Infrastructure Security Agency (CISA) identified exploits against vulnerable public-facing applications as the most common initial attack vector for cybercriminals, followed by attacks on external remote services such as VPNs. According to a study by CrowdStrike, exploit activity targeting cloud apps and assets grew 95% from 2021 to 2022, and instances of threat actors directly targeting cloud apps exploded by 288% during that period.
The importance of robust security measures integrated into your software supply chain cannot be overstated. The recent explosion in software development, especially use of open source and third party code, has resulted in a significant number of vulnerabilities that, if left unattended, can result in financial loss and even a loss of business continuity.
Mitigating these vulnerabilities before they are exploited requires a proactive approach that offers a myriad of benefits, ranging from risk reduction and enhanced trust to improving operational efficiency and profitability.
According to the DarkReading’s State of Vulnerability Management Report, The sheer number of attacks has overwhelmed many IT departments with 28% of the organizations cited in the report claiming discovery of 100 or more vulnerabilities each month. Despite the risk these vulnerabilities present, many companies appear unprepared to deal with them effectively, with only 18% of respondents reporting that they have the ability to resolve more than 75% of the detected vulnerabilities.
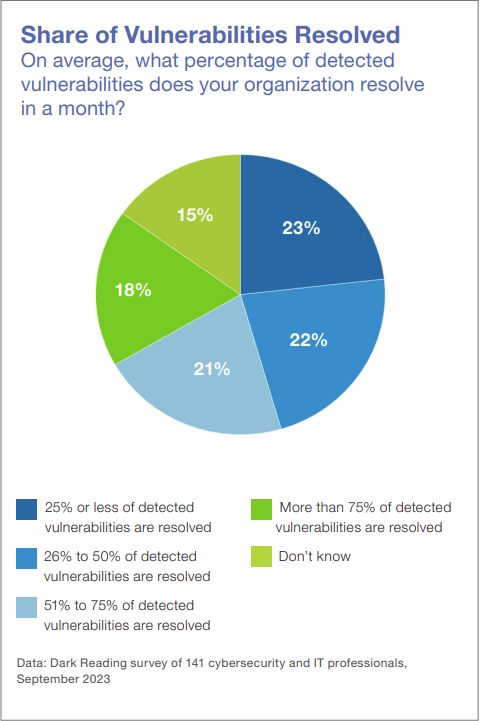
With so many detected vulnerabilities and no remediation, many DevSecOps teams are not only increasing risk, but also building up Security Debt by adding new threats on top of those accumulated in the past. To counter these disturbing trends, Security and DevOps teams need to become proactive in preventing vulnerabilities before they happen – starting with formation of a Prevention Strategy.
Key Benefits of a Vulnerability Prevention Strategy
Implementing an effective Vulnerability Prevention Strategy brings security, operational and economic benefits:
- Reduced risk – Identifying and addressing vulnerabilities before exploitation fortifies defenses, significantly reducing security threats infiltrating the supply chain. This approach minimizes the chance of a breach, thereby reducing Software Development Lifecycle (SDLC) vulnerability.
- Regulatory compliance – Proactive measures aid in meeting stringent security standards and when accompanied by detailed reporting, can be essential for providing compliance data. Commitment to regulatory frameworks helps avoid penalties, increase trust and avoid legal entanglements.
- Enhanced reputation – Implementing proactive security fosters trust among customers and stakeholders, instilling confidence in safeguarding data. This bolsters the organization’s trustworthy reputation.
- Cost-efficiency – Proactive security prevents expensive breaches, minimizing downtime and legal liabilities. Investing in vulnerability identification and prevention is more cost-effective than paying with costly breach down the line.
How to Implement Proactive Vulnerability Prevention
Modern digital society, with all its automated alarms and alerts, has made us so used to responding to incidents only after they happen. That might be OK if I use too much data on my cellular plan, but when it comes to security the potential risk is too great and a proactive stance must be adopted.
Of course this is easier said than done as moving into a preventative mode requires a cultural shift. The cultural shift means adopting a cohesive approach to security, which includes both proactive and reactive methods, from all the way to the left in the coding stage, to all the way to the right after applications have already been distributed. Proactive vulnerability management focuses on identifying, assessing, and addressing vulnerabilities before they’re exploited. This requires continuous automated software analysis. Scanning source code and binaries is essential for monitoring potential vulnerabilities inconstantly evolving software artifacts.
Given that attacks typically target binaries across the software supply chain, scanning these binaries is crucial to identify and fortify against vulnerabilities that might not be uncovered through source code analysis alone.
More importantly, open source and third-party software introduced into an enterprise computing environment carries a high risk of vulnerabilities, which makes implementing an effective risk mitigation strategy for third-party software essential. A successful proactive vulnerability management solution, should block third-party components with vulnerabilities before they enter the software supply chain and offer developers curated safe and secure packages for their applications’ requirements.
From Principle to Practice
To realize a more proactive approach to security, more and more organizations are migrating to software supply chain platforms that provide organizations with a central point of control with complete visibility across their entire development environment. The result is a secure, standardized, and automated process for continuous delivery of high quality trusted software.
For integration of a proactive approach alongside existing reactive methods, point solutions just don’t do the trick. Forward thinking DevSecOps professionals understand that only a software supply chain platform offers end-to-end security that fortifies evolving software artifacts against blind spots not discoverable by source code analysis alone or siloed security tools. Continuous analysis to software development in its production context is the key to ensuring prompt and trusted releases.
When Benjamin Franklin observed that an “ounce of prevention is worth a pound of cure” he was referring to preventing fires instead of fighting them and suffering the damage they wreak. That wisdom also rings truer than ever when it comes to protecting software development environments.
Embracing a proactive stance in preventing software vulnerabilities isn’t just a matter of defense – it’s a strategic decision to safeguard the present, while fortifying and investing in the future.
For more information on the current state of vulnerability prevention check out DarkReading’s recent report.

To see for yourself how the JFrog Platform provides proactive vulnerability prevention, feel free to schedule a demo at your convenience.







