Content-Driven Component Analysis
JFrog Xray was first released one year ago. Our first post about it highlighted what makes Xray more than just another security scanning tool. Over the last year, we have introduced more differentiating features like download blocking, integration with more security vulnerability providers like Aqua Security, BlackDuck, and integration with your CI/CD pipeline to keep your builds safe, “diff”ing component graphs and a whole lot more. In the end, all of these features went towards generating useful and meaningful alerts that would point out issues and vulnerabilities in the software components you are using. While this worked well, our observations over the past year and many sessions we had with customers brought to light an improvement we could make in the workflow.
Content-Driven Workflow
The previous workflow was event-driven. An event in Artifactory triggered a scan which triggered alerts. But this resulted in stateless alerts that aggregated many issues each of which could impact many components. From our customer sessions, we discovered that, often, the Xray user was interested in a specific component; a new tool, build or dependency introduced to the code base. So they wanted an easy way to find that component, and see if it had any issues or vulnerabilities. This spawned content-driven component analysis; a new workflow that we added in Xray 1.8 that goes like this:
Enhanced search –> Component drill-down –> Examine issues
Component Analysis Starts with Enhanced Search
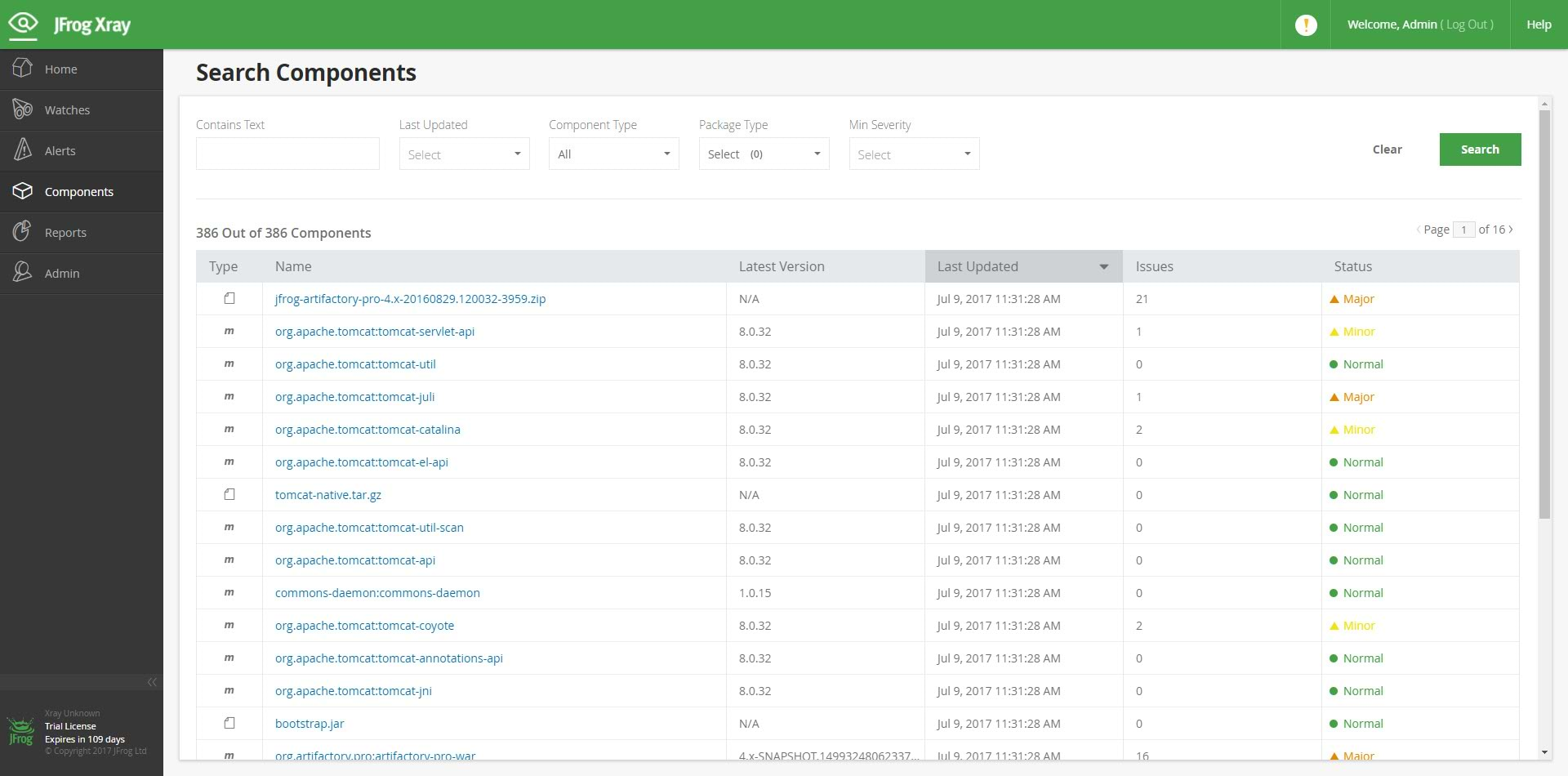
The new component search lets you provide more parameters than before to let you filter results and hone in on the exact component you are looking for. You can search by component type (build, package or file), creation date, modification date, minimum severity, name and more.
Enriched Component Display
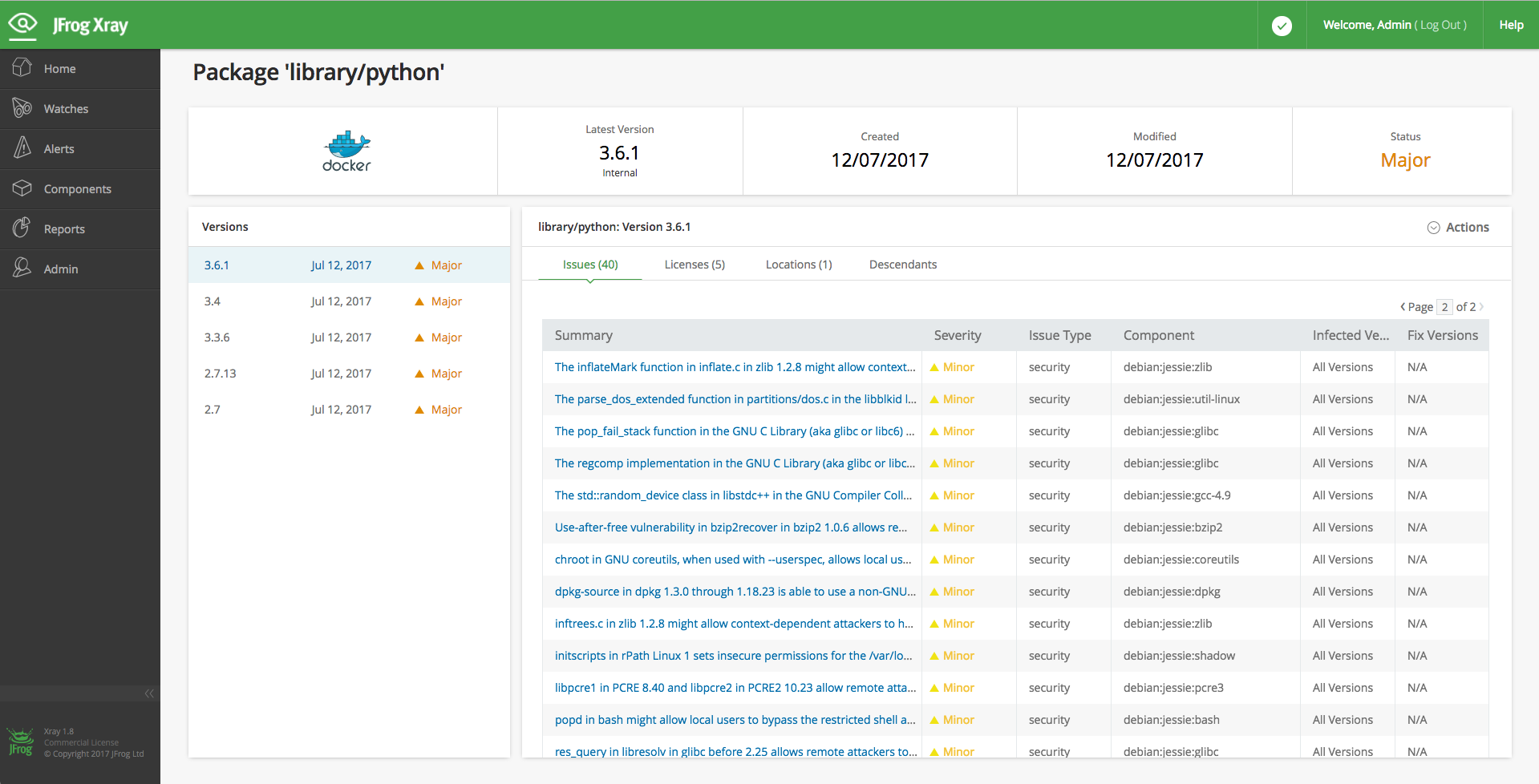
Once you have narrowed down your search results with enhanced search, you can select the component you’re interested in and drill down to get an enriched set of details including all versions, issues and vulnerabilities per version, top issue severity and more.
Get a Quick Fix Version
When you go to the doctor, you don’t only want to find out what’s wrong with you; you also want the cure. The Xray 1.8 enriched component display does just that. In addition to providing the full range of versions infected with a vulnerability, it also provides the “Fix Version” – a recommendation for remediation by upgrading to the version in which the vulnerability has been fixed.
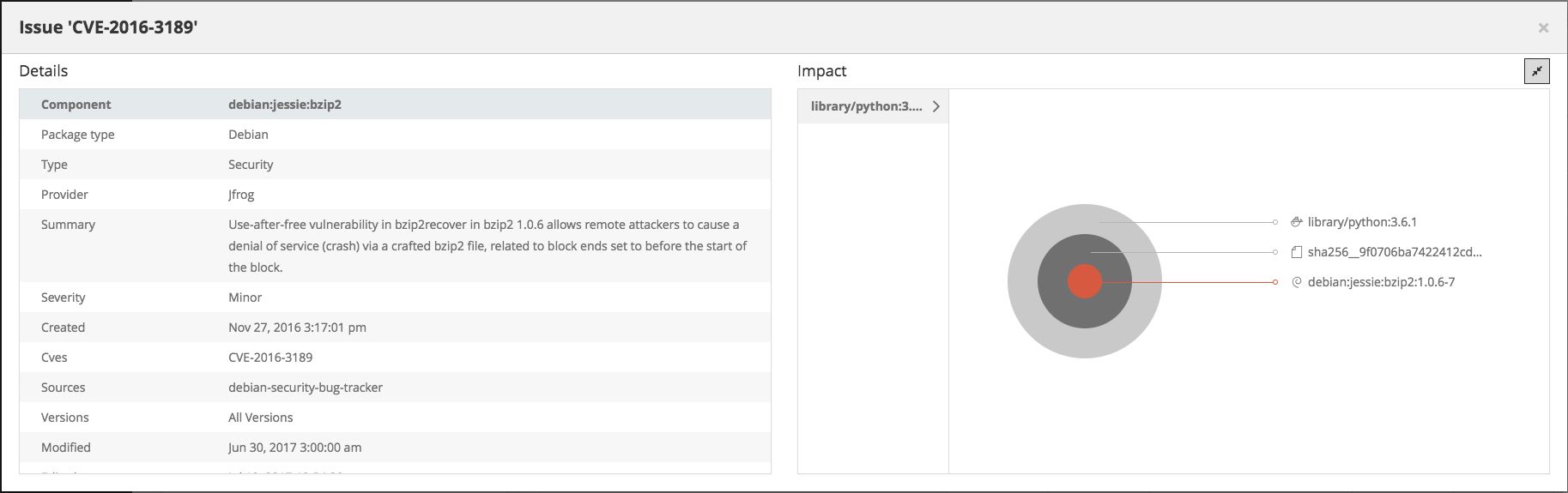
Get Up Close and Personal with Your Issues
From the enriched component display, you can select any issue to view detailed information on it as well as a full impact analysis to see all other components in your system that are impacted by the issue.
What Else?
While the new content-driven component analysis is a big step forward in managing security for your binaries, that’s not all that Xray 1.8 has to offer.
Garbage In, Gold Out
The raw data that Xray starts out with could well be compared to garbage. Between the different sources, and the varying quality of data, it takes quite some processing to turn that data into a coherent vulnerability and issue database. In Xray 1.8, we made many improvements to the algorithm and heuristics that correlate and match data from different sources providing greater and more accurate details about vulnerabilities. In the case of Maven components, we have completely replaced the vulnerability data and even manually curate vulnerabilities before adding them to the database. The result is a more coherent and accurate database that provides better coverage with fewer false positives – Gold.
Team Player for Continuous Integration
This version also extends Xray CI/CD integration to TeamCity, so you can scan builds and fail them if they are discovered to have infected components. Keep your eyes open for a future post with more details about this.
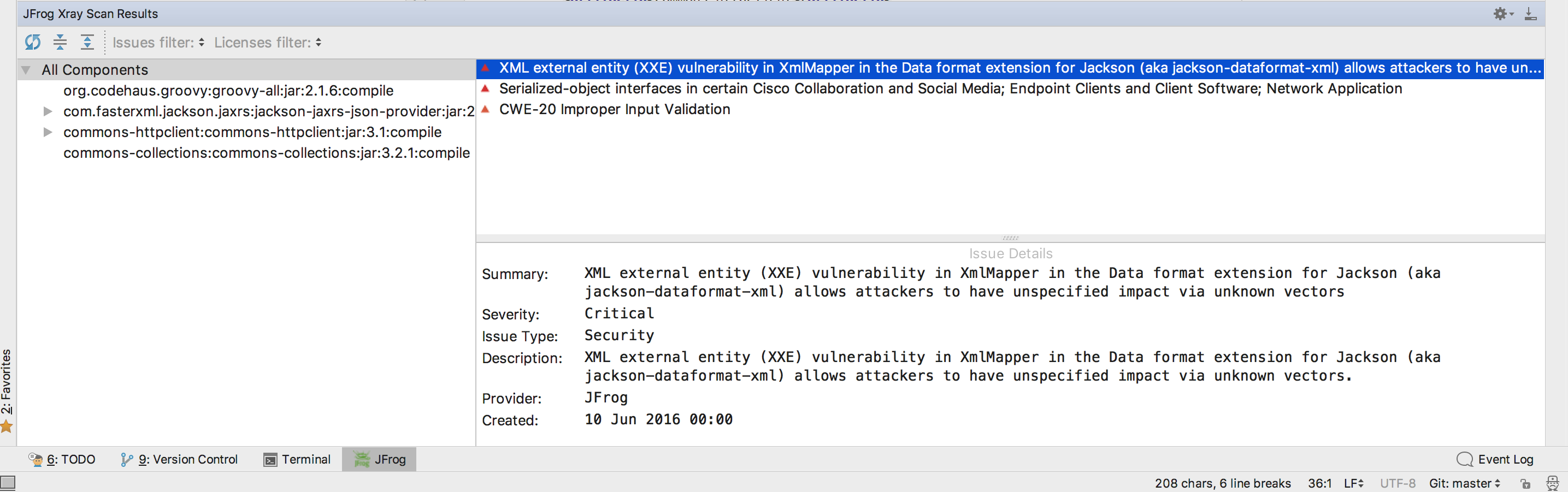
Nip Those Vulnerabilities Right in the IntelliJ Bud
Prevention is better than cure. We all know that, so we want to detect vulnerabilities as early on in the development process as possible. Xray already handled production systems with continuous binary analysis, build time with CI/CD integration, and now brings vulnerability analysis to the development phase. Through direct integration with IntelliJ IDEA, developers can see a complete analysis of any Maven components they include in their software. This gives the developer the privilege, and also the responsibility, to assess whether to use an infected component or not. Keep your eye out for a post on this too.
So that’s it. Well, not quite. We’ve also dramatically improved scanning performance, especially for Docker images, which improves Xray’s responsiveness on the whole. A full repository scan can be orders of magnitude faster. And then, of course, there are the usual bug fixes. To get all the details, have a look at the release notes.
Using Xray already? Great. Want to use content to drive out vulnerabilities. Download the latest version.
Not using Xray? Go ahead, give it a try.