JFrog Unveils First Runtime Security Solution to Deliver Complete Software Integrity and Lineage from Code to Cloud
Complete software lifecycle security enables organizations to simultaneously shift left & right, helping developers save time with quick threat detection and risk remediation
When it comes to software supply chain security, we all do everything we can to prevent insecure software from being released into production. Hence we see software supply chain security shifting left to discover potential threats as early as possible in the software development lifecycle.
But what happens when vulnerabilities are only discovered after an application has been distributed to its operating environment? Unfortunately, it is actually in that phase, where threats are most difficult to discover and left unchecked – can actually do the most damage.
That is why it is so exciting to announce the release of JFrog Runtime, which enables fast discovery of vulnerabilities and helps remediate security incidents in runtime environments where applications are already serving customers, and failure to detect potential threats, could have a severe negative impact on business results.
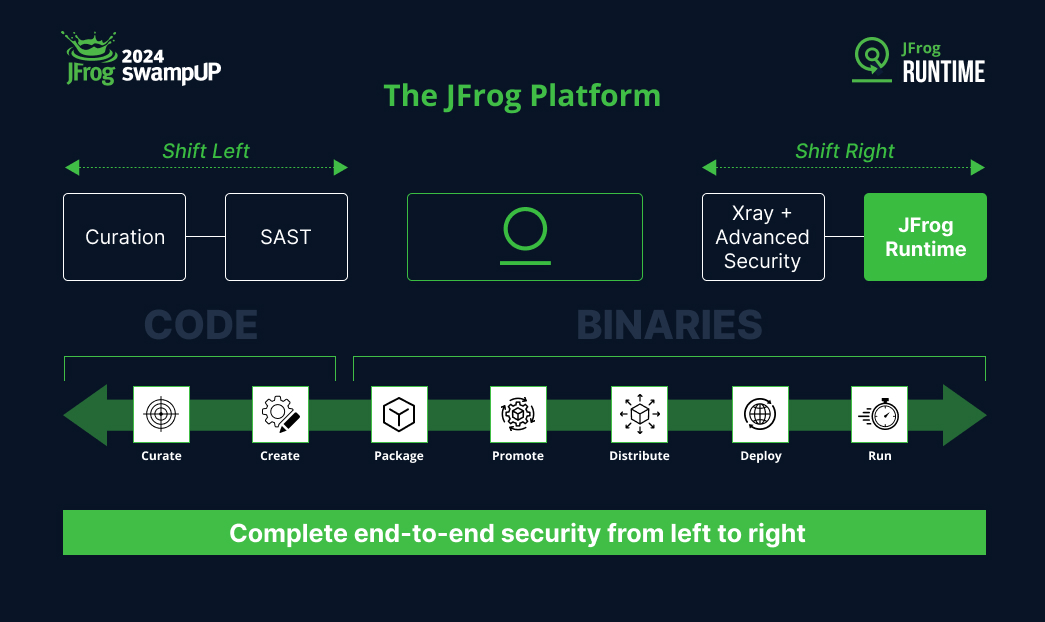
Introducing JFrog Runtime
Runtime is the shift-right solution that bookends JFrog’s end-to-end, shift-left and shift-right, secure software supply chain management platform.
Runtime security tackles the fundamental issues of application security by overseeing and safeguarding applications while they are active. It continuously examines the behavior, data flow, and operational environment of the application to detect, notify and possibly remediate security threats as they occur.
This enables a fast response to attacks and vulnerabilities while the application is running. Unlike static security practices implemented during the development stage, Runtime enables developers to improve the robustness of applications and allows operational and security teams to handle threats more efficiently, leading to an enhanced security posture and cost savings.
JFrog Runtime reduces friction between Development, DevOps and Security teams, offering comprehensive analysis of containers in cloud environments. Natively integrated with JFrog Artifactory, Runtime enables teams to monitor clusters, identify and remediate vulnerabilities, verify image integrity, and ensure compliance with industry standards.
Reduce Risk by Closing the Window of Exposure
In cloud, self-hosted and hybrid environments, runtime security can help establish a dynamic baseline that tracks how behavioral patterns shift over time. Using this baseline, runtime security can identify deviations in internal container processes, file system activities, and other areas that stray from the established norm. This is particularly effective in environments that experience rapid growth and require on-demand scalability.
By providing a single source of truth, the Jfrog Platform with Runtime security allows DevOps and Security teams to easily identify the source and owner of a vulnerable package, and suggest the fastest and most efficient way to mitigate risks.
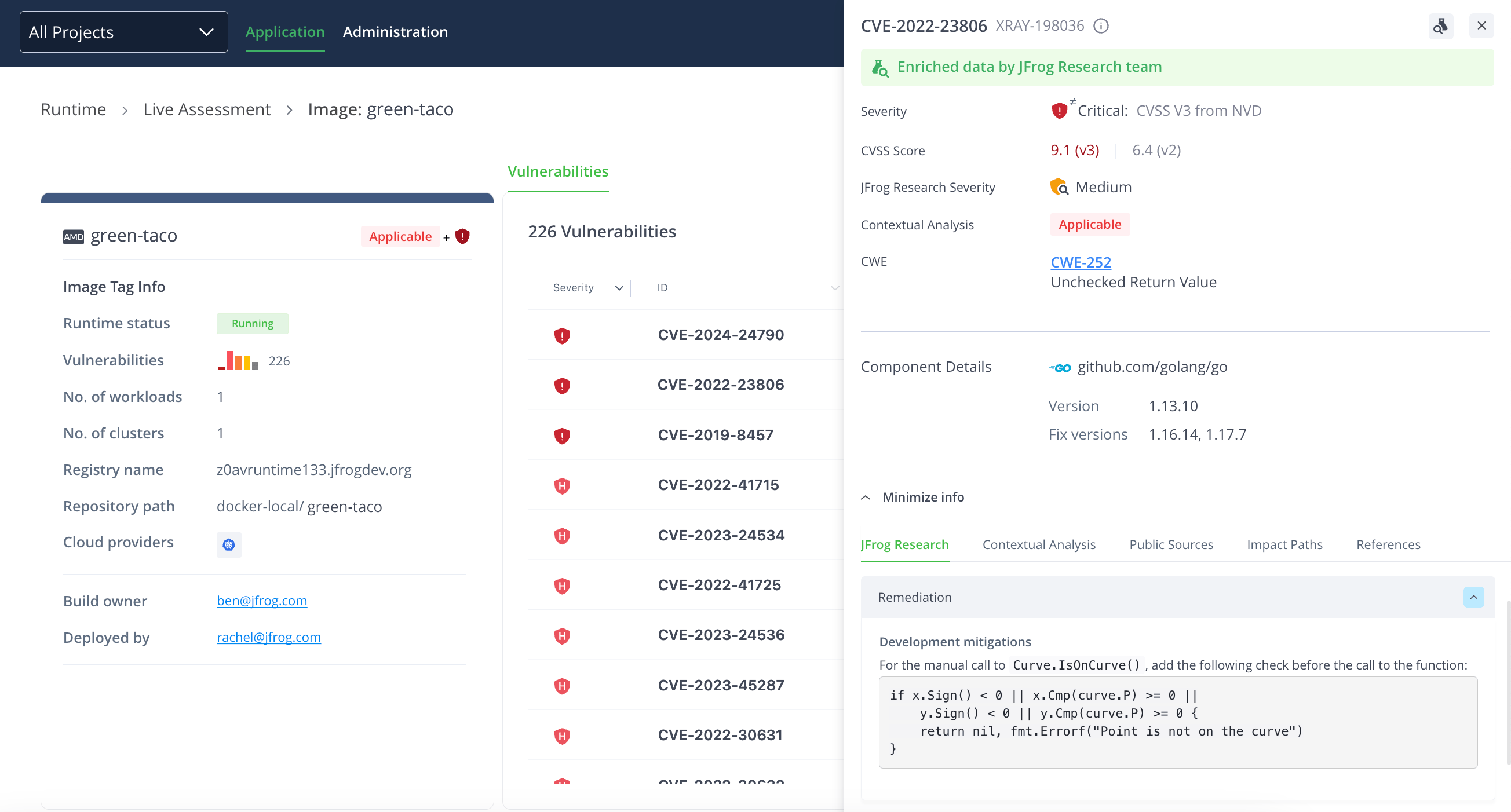
Gain Real-time Visibility into Runtime Vulnerabilities
By continuously monitoring and comparing the runtime activities of applications and services against the established norms, teams can identify and respond to unauthorized actions, privilege escalations, and other potential incidents.
Having a centralized view into runtime environments, with rich data and comprehensive context, enables security professionals to quickly and accurately identify and respond to security incidents as they happen.
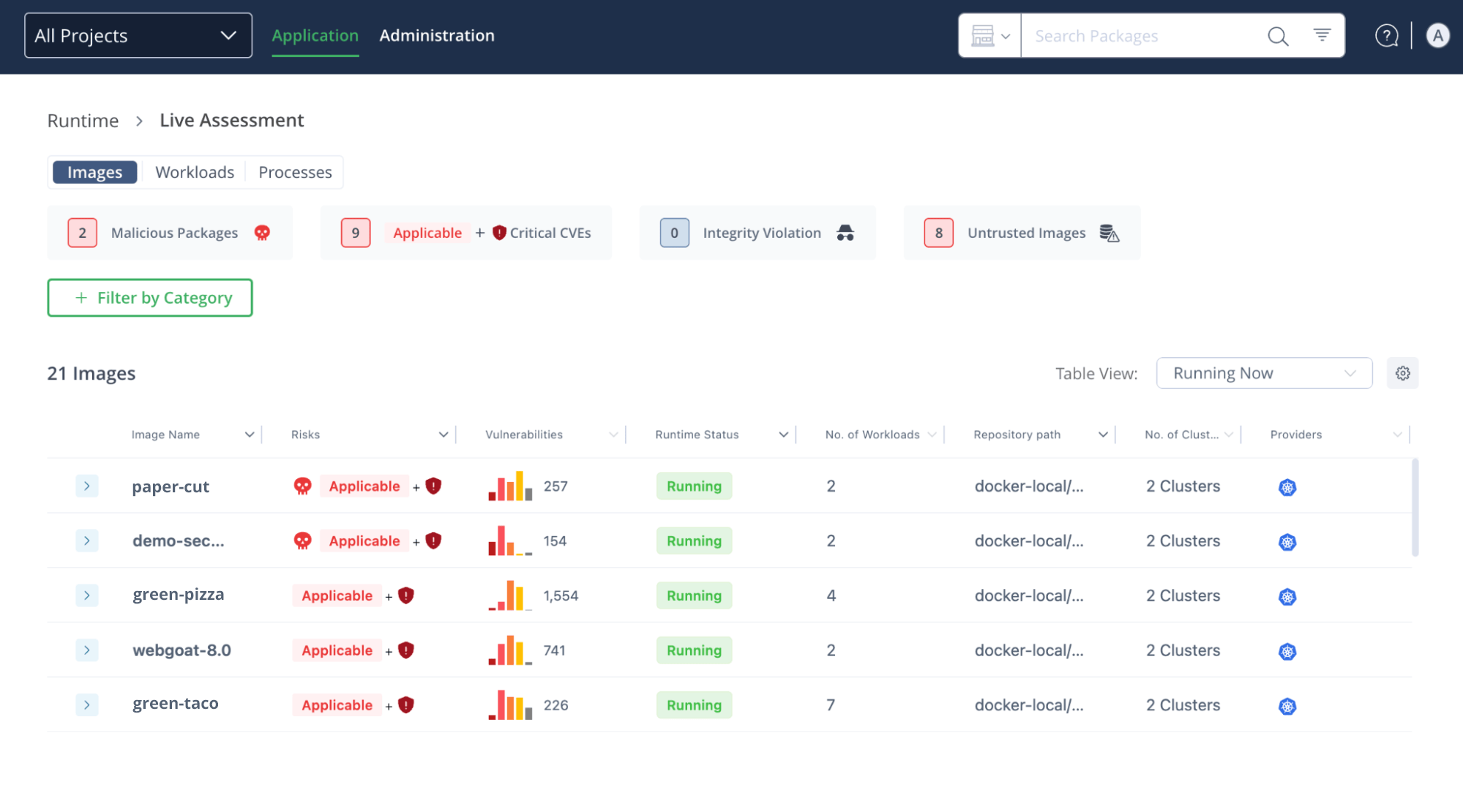
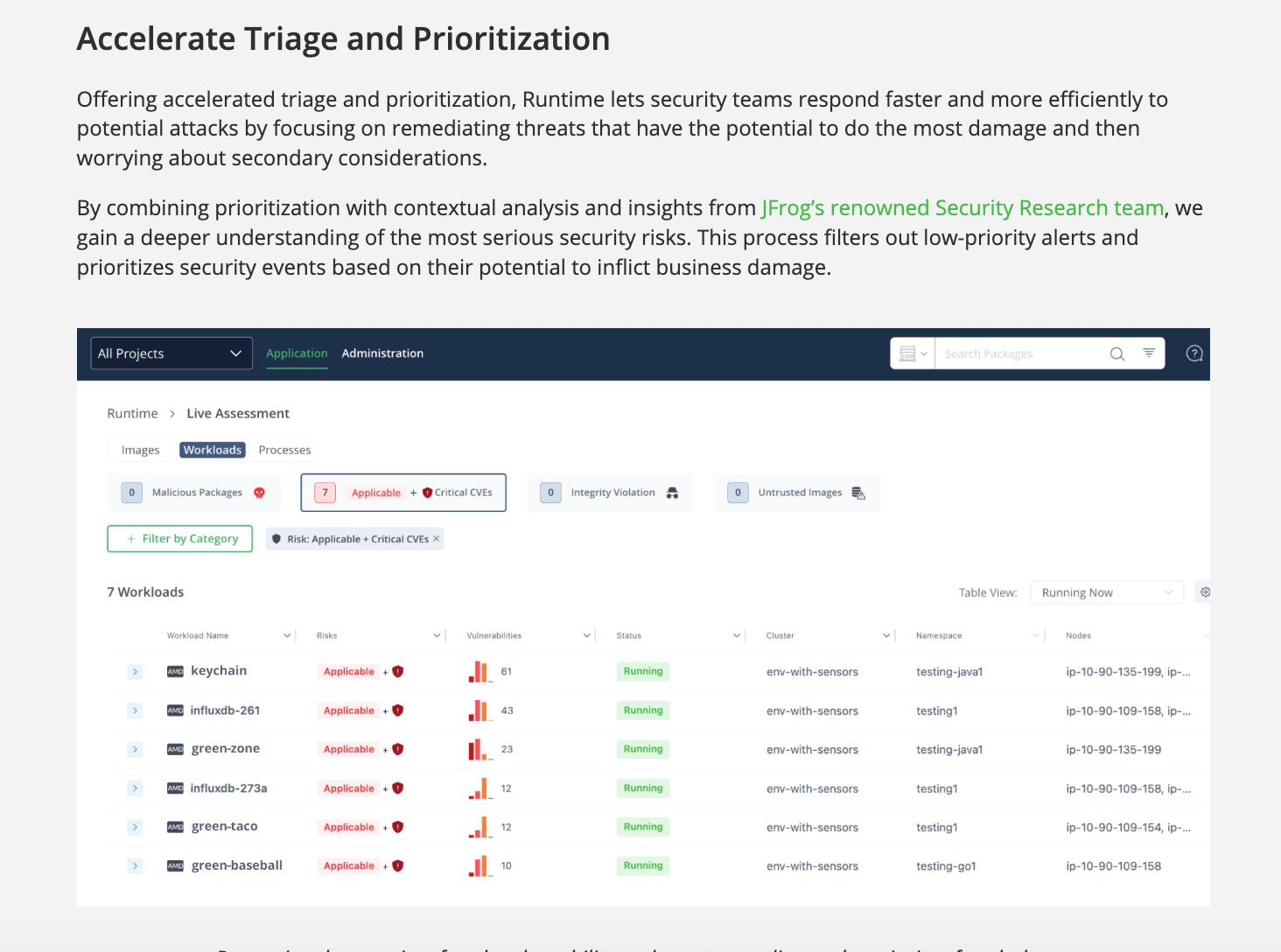
Accelerate Triage and Prioritization
Offering accelerated triage and prioritization, Runtime lets security teams respond faster and more efficiently to potential attacks by focusing on remediating threats that have the potential to do the most damage and then worrying about secondary considerations.
By combining prioritization with contextual analysis and insights from JFrog’s renowned Security Research team, we gain a deeper understanding of the most serious security risks. This process filters out low-priority alerts and prioritizes security events based on their potential to inflict business damage.
Verify Application Integrity in Production
With seamless integration between the software supply chain and production environments, Runtime validates software lineage and alerts on modifications and introduction of untrusted sources.
By continuously monitoring and analyzing the behavior of applications in real time, Runtime can track the execution of applications to ensure they operate as expected and have not been tampered with or altered from their intended state. For example, unexpected changes in file access patterns, unusual outbound network traffic, or unauthorized changes to application code or processes can all signal a potential violation of application integrity.
Want to learn more about JFrog Runtime?
If your organization wants to enhance software development security while increasing efficiency, then you are invited to a live demo of JFrog Runtime, where we can guide you through all the features and benefits mentioned above, while taking a dive deep into how you can leverage the JFrog platform to secure your organization’s software supply chain.