Level Up Your Container Security: Introducing the JFrog Kubelet Credential Provider
Editors Note: the JFrog Kubelet Credential Provider now supports Google Kubernetes Engine (GKE), Azure Kubernetes Service (AKS), and Amazon EKS including projected tokens (KEP-4412 enhancement). This blog is updated to reflect these capabilities.
Amazon EKS, GKE, and AKS are fully managed, compliant Kubernetes services that simplify running, managing, and scaling containerized applications. These services automatically handle the availability and scalability of the Kubernetes control plane, allowing teams of any size or skill level to focus on building and deploying production-ready applications across diverse environments, including cloud, on-premises, and at the edge. As organizations scale their usage of managed Kubernetes clusters, they also need to consider how to handle security and operations, especially when downloading the software components (artifacts) for their deployed applications.
JFrog is excited to release a new capability, the JFrog Kubelet Credential Provider, that makes it safer and easier to get your container images from JFrog Artifactory to Amazon EKS, GKE, and AKS, which leverages the latest capabilities from Amazon Web Services (AWS), Google Cloud, and Microsoft Azure. Instead of using long-lived, static passwords, this new plugin uses temporary, identity-based credentials. This means you can now pull your images to your Amazon EKS, GKE, and AKS worker nodes more securely and with less hassle.
This improvement removes significant friction points, ensuring enterprises can fully optimize their use of Artifactory within Amazon EKS, GKE, and AKS environments for enhanced security, greater stability, and an overall optimized user experience for deployment pipelines.
Security and Operational Issues in Traditional Credential Management
The Problem Today: The current deployment model for applications hosted in private registries outside of cloud providers’ built-in registries rely on including an imagePullSecret within the deployment configurations. These secrets typically hold long-lived authentication artifacts, like passwords, API keys, or access tokens, required to authenticate against the private registry. While functional, this traditional method introduces security vulnerabilities and significant operational overhead that modern enterprise organizations are increasingly unwilling to accept.
- Security Risk: These passwords sit as static secrets in your Kubernetes etcd database, creating an unnecessary attack surface. Because of this major security flaw, more organizations are starting to outright prohibit using static, long-lived secrets for registry authentication.
- Operational Headaches: Managing these secrets is a massive headache. You often need one per namespace across a large cluster. If an access token is revoked or expires, you must manually update secrets across all relevant namespaces, requiring complex CI/CD logic and substantial resources just for secret rotation.
The JFrog Kubelet Credential Provider: A Standardized Solution
Based on our customers’ feedback, JFrog is excited to launch the JFrog Kubelet Credential Provider for Amazon EKS, GKE, and AKS. This crucial upgrade trades in static secrets and replaces them with secure, ephemeral (short-lived), identity-based credentials. This integration enhancement removes operational friction, offering better security, greater stability, and letting our joint customers deploy new workloads much faster.
Here’s what some early customers are saying:
“The demo definitely showed what we’re looking for in a way to make that authentication easier.” – Automotive manufacturer
“The proposed solution is definitely closer to our preferred approach with having this managed completely at the cluster level as opposed to an individual namespace with exposure to the secret.” – Global hospitality brand
“Nobody wants to manage secrets anymore.” – Enterprise IT company
How It Works: Identity Over Passwords
Our solution isn’t a custom workaround; it’s based on the established, built-in Kubernetes feature called the Kubelet Image Credential Provider. This is the same standard used by Amazon Elastic Container Registry (ECR), Google Artifact Registry, and Azure Container Registry for their native registry authentication. Additionally, the JFrog <> Cloud Provider token exchange mechanism does not require other security compromises that some other solutions require, such as exposing access to the Kubernetes api server externally.
The biggest win? No more Kubernetes secret creation or management is required. This new flow delivers truly passwordless access from your Managed Kubernetes to Artifactory.
The Passwordless Credential Flow:
- Image Pull: A new pod needs an image from Artifactory.
- Kubelet Interception: The Kubelet on your managed Kubernetes worker node matches the image host with the pattern configured for the JFrog provider.
- Plugin Run: The Kubelet executes the configured plugin binary:
jfrog-credential-provider. - Token Exchange Magic:
- With node based identity, the provider uses the native cloud vendor identity mechanism for getting the node’s verified identity (either an IAM Role for AWS or OIDC for all three cloud vendors) and exchanges that proof of identity with Artifactory.
- For AWS, the new projected tokens enhancement is also supported and instead of basing the token exchange on the node’s identity, the identity used for the exchange is based on AWS IAM roles for service accounts (IRSA) mechanism and on the deployed workload ServiceAccount.
- Short-Lived Token: Artifactory returns a newly generated, short-lived token intended for the registry authentication.
- Pull Image: The Kubelet uses the temporary token to securely pull the image and complete the deployment.
Quick Comparison of Credential Management:
| Feature | Traditional imagePullSecrets |
JFrog Kubelet Credential Provider |
|---|---|---|
| Credential Type | Long-lived passwords/API Keys/Tokens | Short-lived, ephemeral Artifactory Tokens |
| Storage Location | Kubernetes etcd, CI/CD secrets vault | None (Dynamically generated on the node and cached inside the kubelet process memory) |
| Security Risk Profile | High (static exposure risk, complexity of rotation) | Low (Dynamic, Identity-based) |
| Operational Effort | High (Manual rotation, multi-namespace management) | Negligible (Automated via Kubelet/Node Identity) |
| Foundation | Kubernetes Secrets API | Kubernetes Kubelet Credential Provider Standard |
Getting Set Up: Deployment and Identity
AWS
Deployment Made Easy (Using Amazon EC2 Launch Templates): Since the setup requires specialized access to the underlying host file system and Kubelet configuration, the most robust method for deployment is during the bootstrapping process via Amazon EC2 Launch Templates. This ensures every new worker node automatically gets the jfrog-credential-provider binary installed.
To configure the Kubelet to use the plugin, you can either:
- Use the plugin utility:
./jfrog-credential-provider add-provider-config, and calling it during the launch template commands. - Manually inject the configuration JSON via launch template commands.
The plugin can also check JFrog releases for the latest minor version and auto-update the binary (though this can be disabled).
For IRSA (AWS), or OIDC based authentication, as is the case with GKE and AKS, we recommend using our helm charts (see on https://github.com/jfrog/jfrog-credentials-provider/tree/main/helm).
Ways to Authenticate (Identity Exchange):
EKS
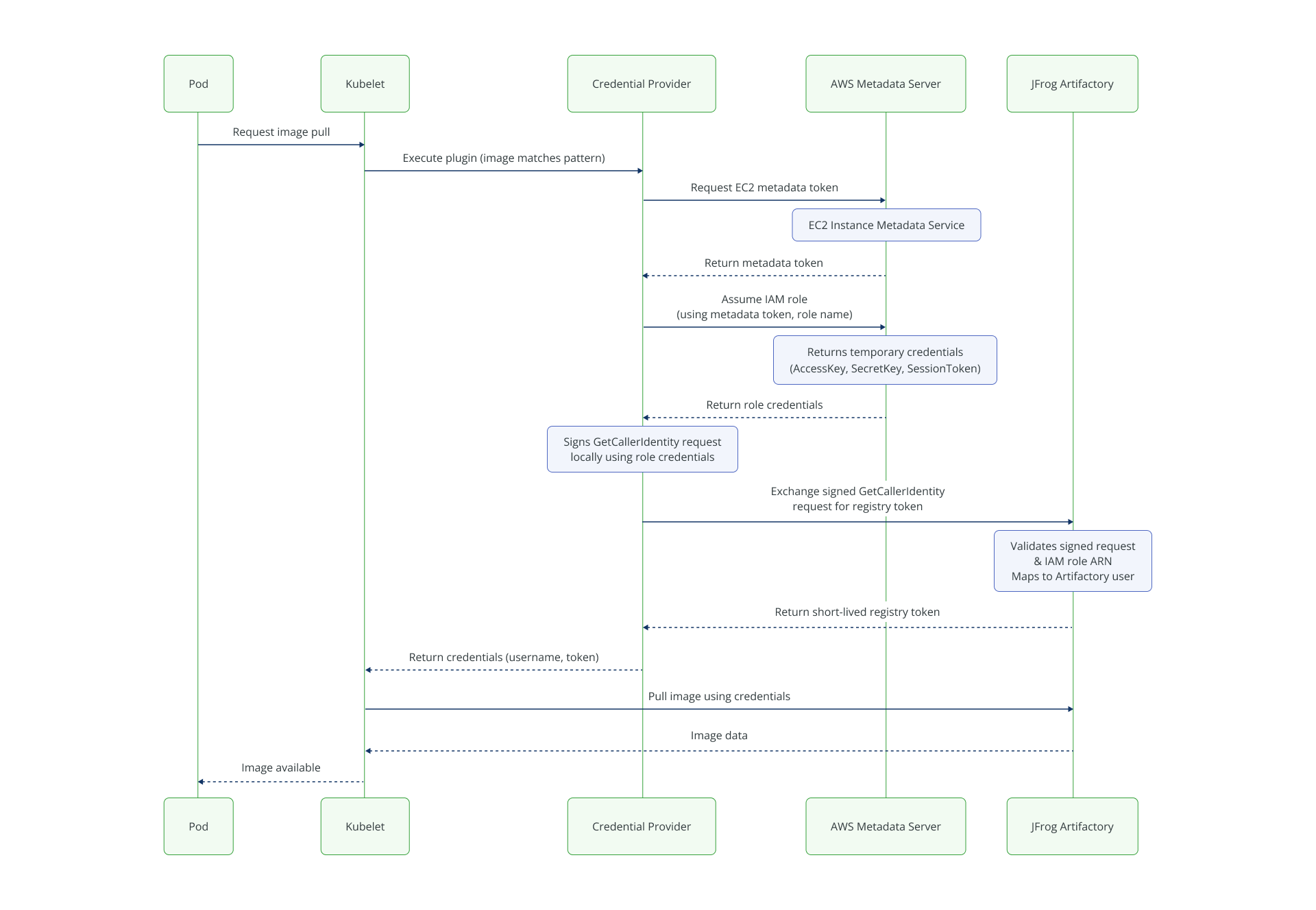
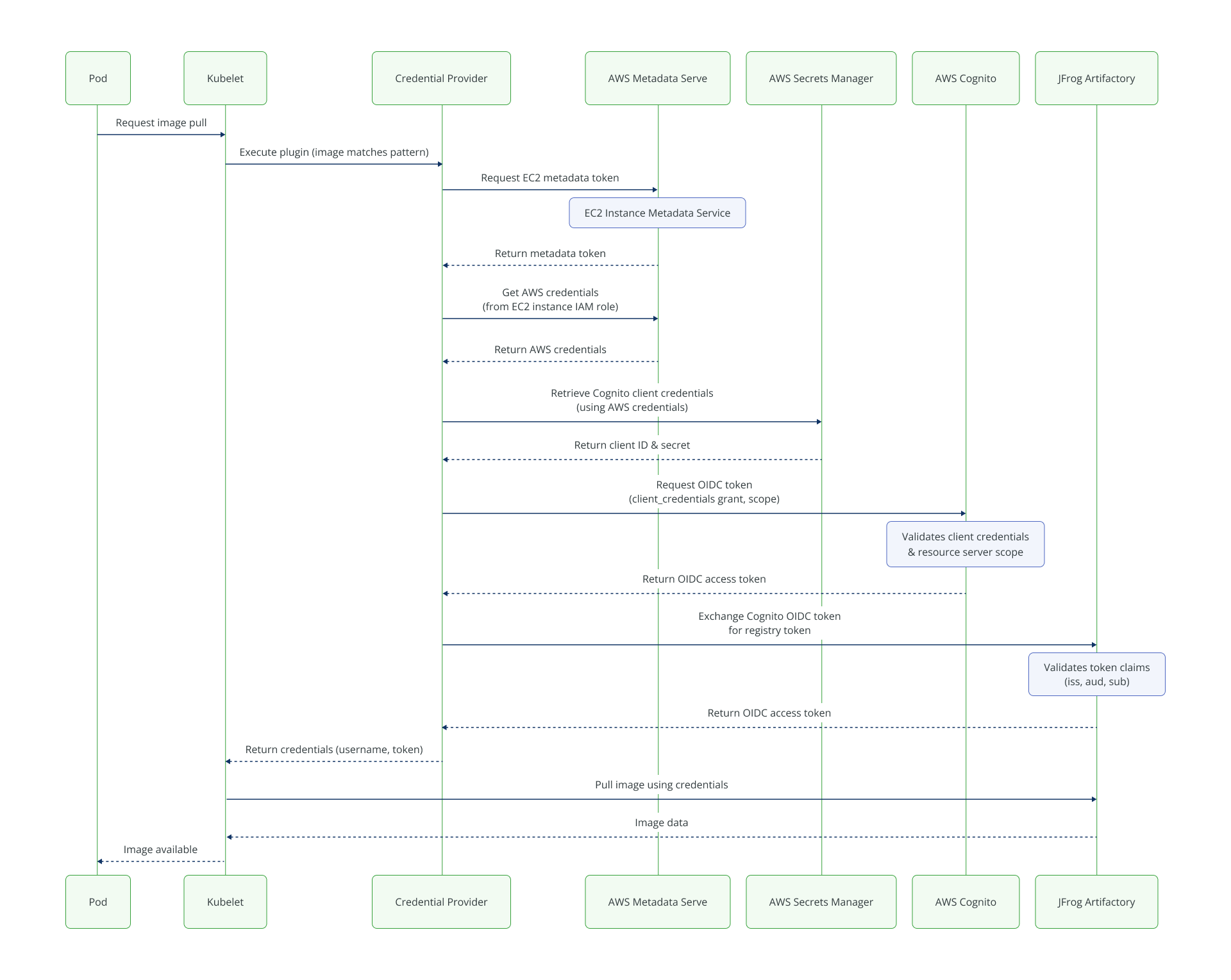
The provider supports three paths to exchange your trusted AWS identity for a temporary Artifactory token:
| Authentication Flow | Key AWS Services Used | Prerequisites |
|---|---|---|
| 1. IAM Role Assumption | IMDS, IAM Roles, AWS STS | Node must be allowed to assume an IAM role with permissions for STS get caller identity and get role operations. |
| 2. Cognito OIDC | AWS IMDS, AWS Cognito, AWS Secret Manager | Cognito resource set up, AWS secret with client ID/secret created, and Node must be allowed to access both. |
| 3. Projected Tokens | IMDS, IAM Roles, AWS STS, IRSA | Workload (IRSA) role must be allowed to assume an IAM role with permissions for STS get caller identity and get role operations.
Node should be allowed through RBAC to Get and List ServiceAccounts and request their token audiences (request-serviceaccounts-token-audience) |
Launch template flow (EKS)
Alternative setup: Projected Tokens
GKE
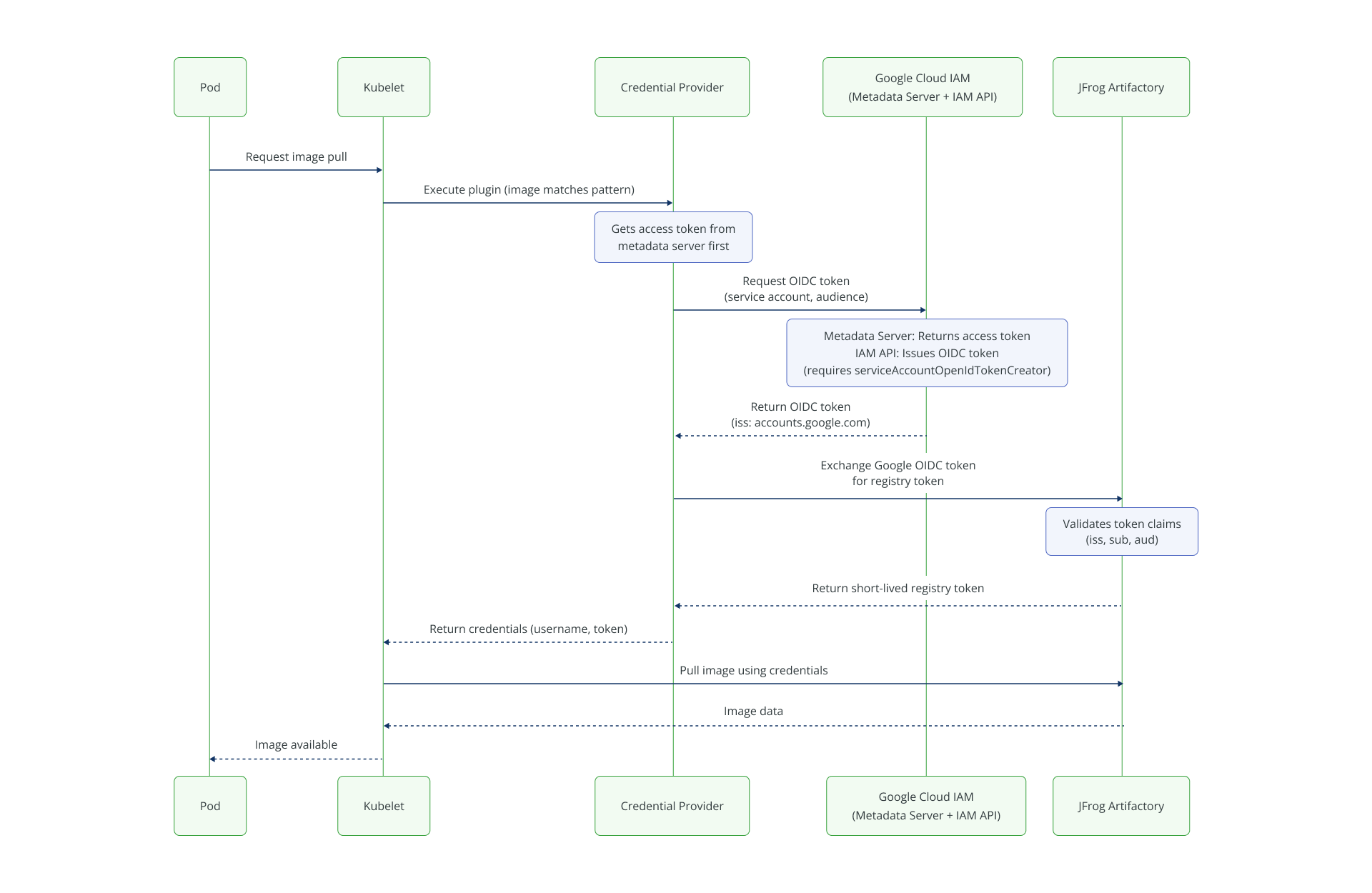
The provider supports identity exchange based on OIDC for retrieving a temporary Artifactory token:
| Authentication Flow | Key GCP Services Used | Prerequisites (Node Permissions) |
|---|---|---|
| 1. OIDC Exchange | Metadata server, IAM credentials service, Google OIDC | Nodes’ service accounts must be enabled for OIDC |
OIDC flow (GKE)
AKS
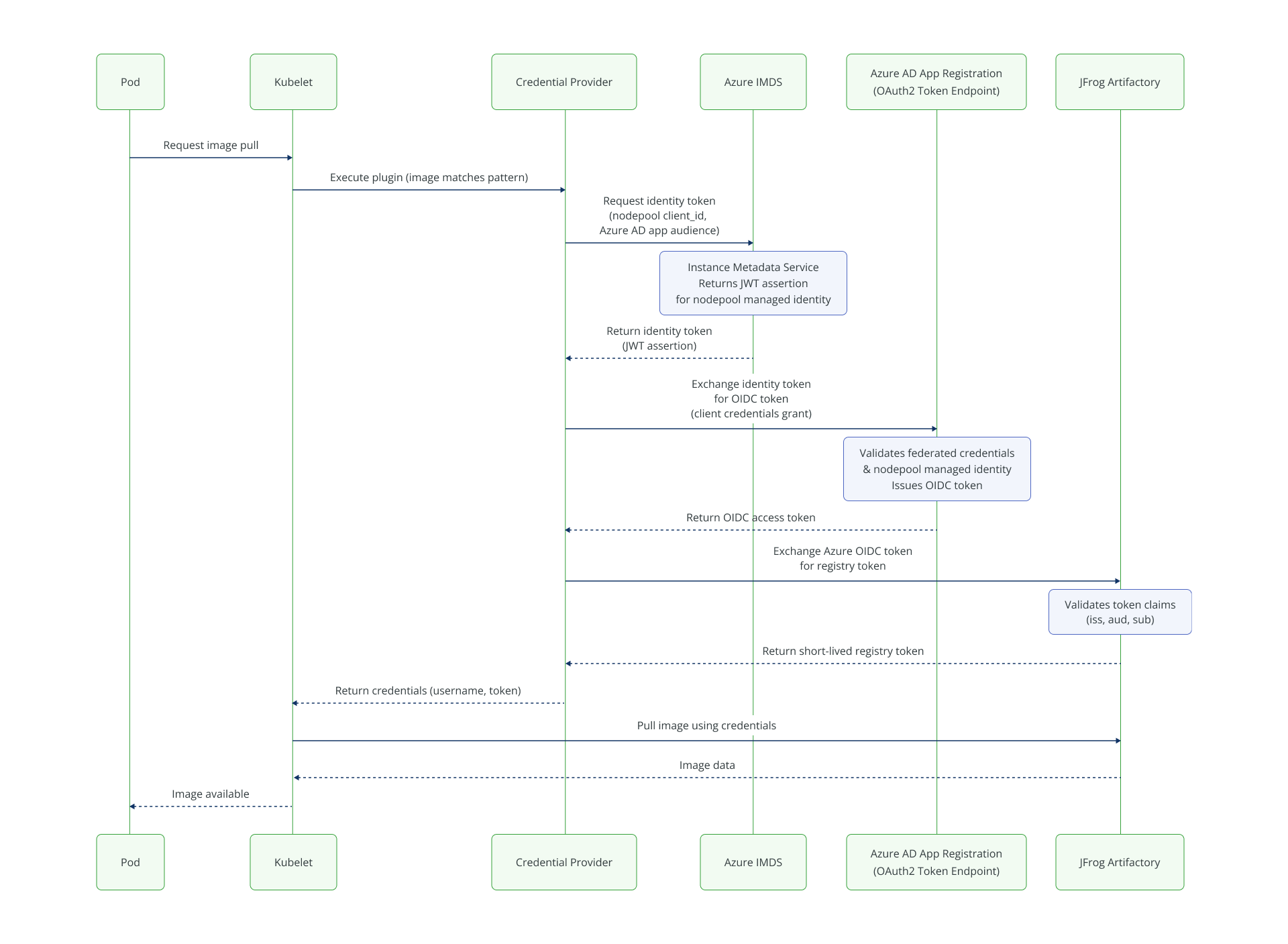
The provider supports identity exchange based on OIDC for retrieving a temporary Artifactory token:
| Authentication Flow | Key AKS Services Used | Prerequisites (Node Permissions) |
|---|---|---|
| 1. OIDC Exchange | Metadata server, Azure Registered Applications with federated credentials | Nodes’ identity allowed for a registered application through the application’s federated credentials |
OIDC flow (AKS)
Strategic Benefits and Operational Gains
The shift to the JFrog Kubelet Credential Provider delivers transformative benefits across security, operational efficiency, and user experience.
Enhanced Security Posture (Identity over Secrets)
The security posture of managed cloud Kubernetes cluster deployments is dramatically enhanced by moving away from long-lived passwords and static API keys. The replacement of these persistent credentials with short-lived and dynamically generated tokens minimizes the attack surface and the potential blast radius in the event of a cluster compromise. The solution enforces the principle of least privilege by linking image pull access directly to the validated infrastructure identity of the worker node (its IAM role or OIDC context). By embedding the cryptographic proof of identity within the artifact pull process, the risk of external or internal credential theft is effectively neutralized.
Operational Efficiency and Speed of Deployment
The core customer-requested functionality delivered by this plugin is the removal of management friction. Operators are liberated from the continuous, tedious, and often error-prone tasks associated with managing Kubernetes secrets, rotation schedules, and ensuring correct namespace-specific configurations. This elimination of secret management reduces operational friction, ensuring greater stability and allowing for significantly faster workload deployments. This efficiency is especially critical for large joint customers who need to rapidly deploy new workloads on a managed Kubernetes cluster without inheriting the complexity and security issues that were previously unavoidable.
Optimized User Experience (UX)
By streamlining the use of JFrog Artifactory with Amazon EKS, GKE and AKS, the integration offers an overall optimized user experience (UX) and delivers greater stability throughout the deployment pipeline. Developers and DevOps teams can focus on application delivery rather than infrastructure credential plumbing, trusting that the underlying infrastructure identity mechanisms will securely and automatically handle artifact authentication.
Looking Ahead (Roadmap and Fine Print)
- Future Granularity: We plan to support KEP-4412 (projected service account tokens) for GKE and AKS. This means we can restrict image pull access right down to the specific pod identity instead of the entire node group, drastically improving least privilege enforcement.
- Current Limit: Currently, the highly secure AWS Bottlerocket EC2 image is NOT supported. This is because Bottlerocket’s architecture blocks the required plugin deployment mechanism.
Ready to Go Passwordless?
By moving deployment processes from fragile, long-lived secrets to robust, dynamic, identity-based authentication, you achieve new levels of security and speed.
Ready to get started? Check out the open-source development on GitHub: github.com/jfrog/jfrog-credentials-provider
Learn more about JFrog’s partnerships with AWS, Google Cloud, and Microsoft Azure: jfrog.com/cloud-partner/