Don’t waste time on irrelevant false positive alerts in your source code
Scan your code for security vulnerabilities directly from your terminal and focus on the ones that actually count, with Contextual Analysis and JFrog CLI.
Are you tired of using security tools that generate endless results, making it impossible to identify actual risks? Do you struggle with inefficient prioritization due to a lack of context, making the process of assessing and remediating vulnerabilities a time-consuming nightmare? Look no further than JFrog’s Contextual Analysis, available as part of the “jf audit” command in the JFrog CLI.
Contextual analysis designed for developers
As developers assume greater responsibility in building secure applications, it is crucial to proactively evaluate your code for vulnerabilities.
Instead of having to revisit completed features due to security violations, avoid unnecessary disruptions; Take a proactive approach by conducting code scans in advance in your local development environment, saving yourself the context switches and inconveniences.
Optimize your efforts with JFrog’s Contextual Analysis, empowering you to prioritize the most critical issues rather than wasting time on CVEs that aren’t applicable to your code base..
Additionally, get pre-written remediation code snippets crafted by JFrog’s top-notch security experts that will save you a ton of time.
Contextual Analysis is one of the most advanced security capabilities available, and now it’s available at your fingertips with the “jf audit” command with JFrog CLI.
> Contextual Analysis is currently available for Python and Javascript code only, directly from within VS Code and IntelliJ IDEA, as part of JFrog Advanced Security. Support for additional languages will be coming soon.
> The difference between the jf audit and scan commands:
jf audit – This command uses your package manager to build the project’s full dependency tree and scan all its components.
jf scan – This command scans all files in a specific directory and reports all identified vulnerabilities.
-
- Learn more about scanning dependencies in your sources using JFrog CLI >
How contextual analysis works
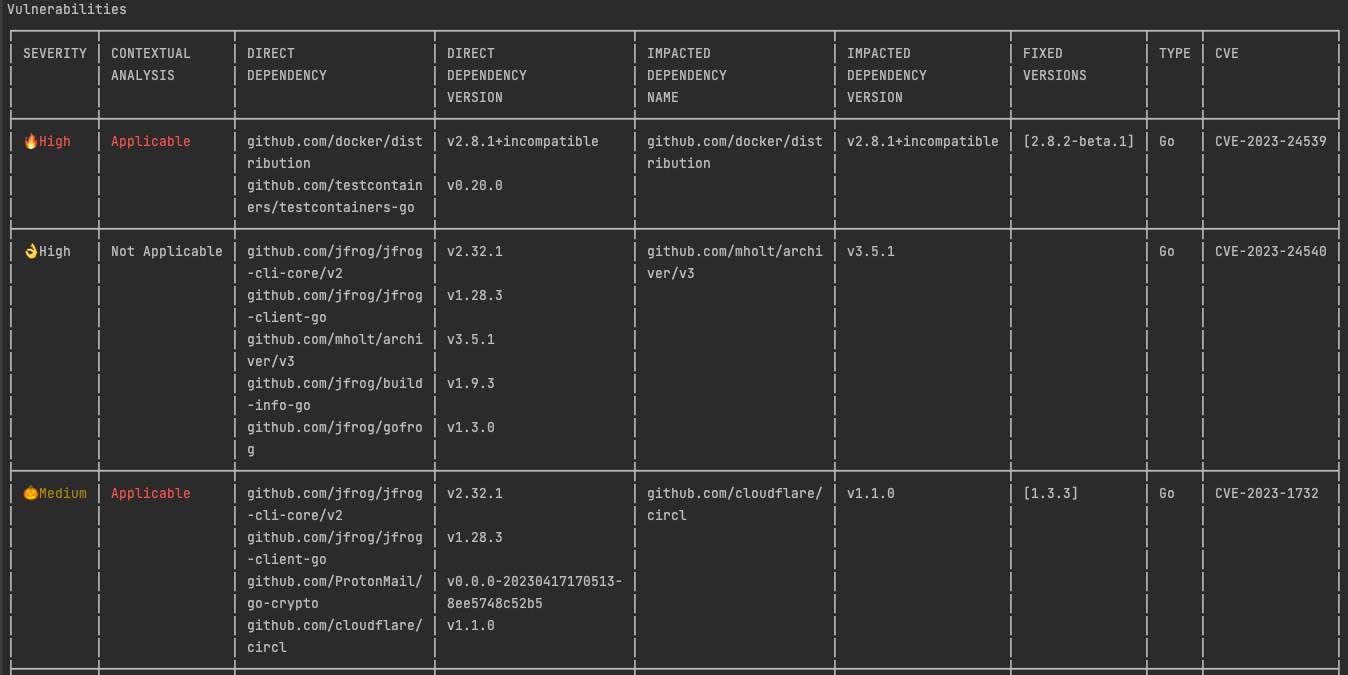
JFrog’s cutting-edge analysis engine deeply scans your source code to determine the applicability of identified CVEs, helping you focus on the critical vulnerabilities and avoiding wasted time on irrelevant ones.
The Contextual Analysis engine takes into account specific attributes and configurations from your code, and provides concrete and actionable recommendations that prioritize critical issues discovered.
Get started
Give it a try with these simple steps:
- Start an advanced security trial with the JFrog Platform.
- Install JFrog CLI.
- Support for Contextual Analysis was introduced in JFrog CLI 2.38.0. If you have an earlier version of the CLI, please update.
- From your terminal, run the “jf c add” command and enter your JFrog Platform connection details.
- Change directory to the root directory for your source project.
- Run the “jf audit” command.
- See the results.
The “jf audit” command generates a table in your terminal that includes the complete list of CVEs identified in your project. The “Contextual Analysis” column indicates which CVEs are actually applicable to your code and which aren’t. CVEs that are not applicable to your code can be given a lower priority in your planning.