3 Key Considerations for Securing Your Software Supply Chain
An organization’s software supply chain includes all the elements involved in developing and distributing software, such as components, tools, processes, and dependencies. Each link in this important chain presents the potential for security threats.
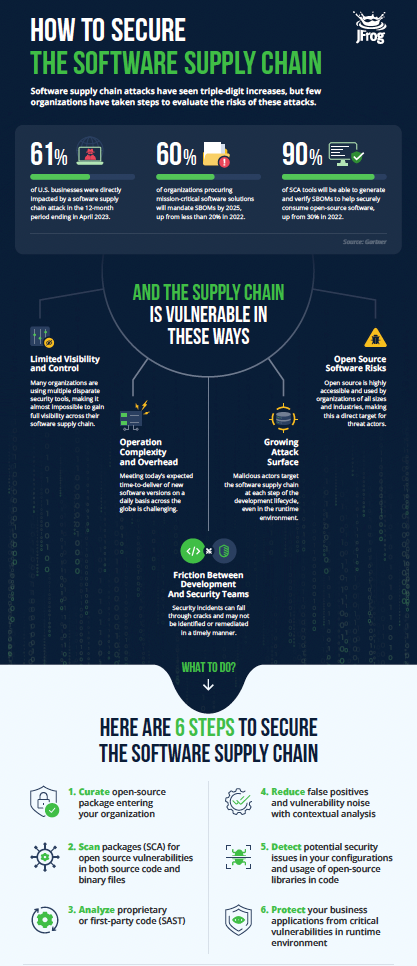
Recent research conducted by Gartner shows a major increase in attacks targeting code, tools, open-source components, and development processes, particularly in areas where organizations lack visibility. Further, the financial implications of software supply chain attacks are substantial, with an average cost of $1.7 million.
Keep reading here to learn the key considerations and requirements for securing your software supply chain. For a deeper dive into the topic, download our ebook: 3 Key Steps to Secure Your Software Supply Chain.
Download the eBookWhy the software supply chain is vulnerable
There are multiple reasons why an organization’s software supply chain may be vulnerable to attackers. The biggest and most common reasons include:
- Limited visibility and control: Many organizations are using multiple disparate security tools, making it almost impossible to gain full visibility across their software supply chain.
- Operational complexity and overhead: Meeting today’s expected time-to-deliver of new software versions on a daily basis across the globe is challenging.
- Growing attack surface: Malicious actors target the software supply chain at each step of the development lifecycle, even in the runtime environment.
- Open source software risks: Open source is highly accessible and used by organizations of all sizes and industries, making this a direct target for threat actors.
- Friction between development and security teams: Security incidents can fall through cracks and may not be identified or remediated in a timely manner.
How to secure the software supply chain
The severity of attacks on software supply chains and the associated costs is only expected to grow in the future. Because of this increasing pressure on organizations, there are three key best practices that have become crucial:
- Curate all open-source packages at point of entry. Curating open-source packages at their point of entry helps mitigate potential risks, especially in light of the extensive use of open source software.
- Apply security consistently and at every phase of the software development lifecycle. Applying security measures throughout the software development lifecycle ensures comprehensive protection since you’re taking both a proactive (shift left) and reactive (shift right) approach to software supply chain security.
- Promote tighter collaboration between DevOps and SecOps. Fostering closer collaboration between DevOps and SecOps teams is increasingly important to address security challenges effectively, whereas an inharmonious relationship can cause tension and leave critical gaps in security coverage.
Next steps
As attacks on the software supply chain increase, the associated consequences become more serious. To mitigate these risks, the best practices outlined above are now more important than ever.
To learn more about how to apply these three key steps to secure your software supply chain, and read about how Hitachi Vantara maintains a consistent security posture by applying these best practices, download the ebook. Or, for a more condensed read, check out the infographic: