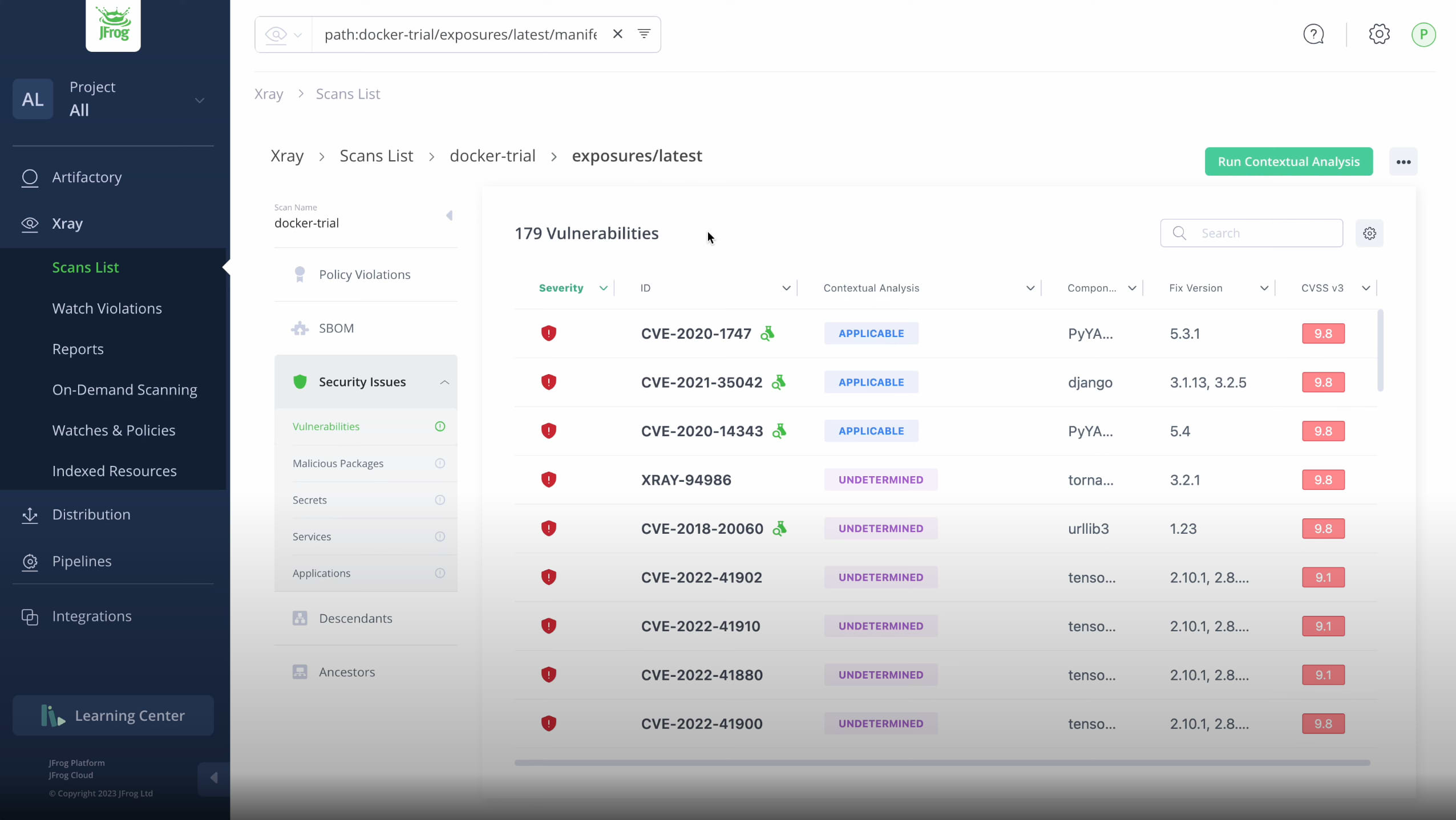
Software Composition Analysis for source code and binary files
Identify and resolve security vulnerabilities and license compliance issues in your open-source dependencies with enhanced CVE detection. Detect, prioritize & mitigate license compliance issues, and accelerate clearing. Automatically generate and export industry-standard SPDX, CyloneDX (VEX) SBOMs. Speed remediation with up-to-date proprietary details and fixes on high-profile CVEs from JFrog’s Security research team.

Detect hidden risks in AI-generated code and copied snippets
AI-coding assistants are writing your code, but are they also hiding vulnerabilities and license risks within it? We've extended our analysis beyond package scanning to find these threats directly inside your code snippets. Secure the code you write and the code AI generates for you.

Keep malicious packages out of your software development lifecycle
Discover and eliminate unwanted or unexpected packages, using JFrog’s unique database of identified malicious packages. The database is sourced with thousands of packages identified by our research team in common repositories alongside continuously- aggregated malicious package information from global sources.

Enforce policies to block operationally risky packages
Automate risk management to eliminate package maintenance issues and technical debt. Enable seamless package blocking with customizable policies based on soft attributes, such as the number of maintainers, maintenance cadence, release age, and the number of commits.

Shift as far left as possible
Scan packages early for security vulnerabilities and license violations using developer-friendly tools. View vulnerabilities with remediation options and context directly in your IDE. Automate your pipeline with our CLI tool for dependency, container, and on-demand vulnerability scans. Early scanning minimizes threats, reduces risk, speeds up fixes, and saves costs.