Definition
The software supply chain is an aggregation of all the people, processes, and technologies involved in producing or updating a piece of software. Common components include: source code, third party code, open-source libraries, dependencies, toolchains, infrastructure, and more.
Overview
Understanding Software Supply Chain Security
Software supply chain security refers to the security measures and practices implemented throughout the software development lifecycle (SDLC) to protect the integrity, confidentiality, and availability of software products and services. It encompasses all stages of the software lifecycle and can be applied to both in-house and open source software development.
The goal is to provide better assurances and observations around what goes into your software (i.e. where it came from and how it was built). This could include things like signing commits, signing your artifacts, and producing a software bill of materials (SBOM), which documents all of the components that are in the final product that’s being packaged up to be delivered to customers. For open source projects, it’s about knowing what’s in your source code and container images, so that you can quickly figure out critical information in the event of a vulnerability, such as where the vulnerability occurs in your architecture, what container image introduced it, and which build team is responsible for maintaining that package. Having these pieces of information at the ready enables teams to take swift action to remediate potential vulnerabilities and secure their software supply chain.
The importance of software supply chain security
The need for software supply chain security measures has grown in recent years due to increasing reliance on third-party components when building and deploying applications. Reuse of third-party resources, including open source components, can reduce the amount of code developers have to write from scratch. However, as explained above, any security risks that exist within the external resources will become risks for the applications that use them.
Known vulnerabilities in proprietary applications can also become vectors of attack. This was the case, for example, during the infamous SolarWinds breach, which exposed users of the commercial SolarWinds platform to potential data exfiltration.
Understanding software supply chain security is crucial for several reasons:
- It helps mitigate the risks associated with software vulnerabilities and attacks. Vulnerabilities in software can be exploited by malicious actors to gain unauthorized access to systems, steal sensitive data, or disrupt operations. By securing the software supply chain, devsecops teams can reduce the likelihood of these vulnerabilities being introduced and exploited.
- Software supply chain security is essential for maintaining compliance with industry regulations and standards. Many industries, such as healthcare, finance, and government, have strict regulations regarding the security of software used in their operations. By implementing robust software supply chain security measures, organizations can demonstrate compliance with these regulations and protect themselves from potential legal liabilities.
- Software supply chain security is vital for protecting intellectual property and brand reputation. Software vulnerabilities can be used to steal sensitive information, such as trade secrets or customer data, which can damage an organization’s reputation and competitive advantage. By securing the software supply chain, organizations can protect their intellectual property and maintain customer trust.
Key Components of a Secure Software Supply Chain
To effectively secure the software supply chain, organizations should adopt a comprehensive approach that includes:
- Implementing security controls
- Conducting regular security assessments
- Continuously monitoring for threats
This involves employing various security measures such as:
- Code signing
- Secure coding practices
- Vulnerability management
- Access controls
Additionally, organizations should establish clear policies and procedures for software development and deployment, and ensure that all stakeholders are aware of their roles and responsibilities in maintaining software supply chain security.
The role of binaries in software supply chain security
Binaries play a critical role in software supply chain security. Binaries are the compiled executable files that comprise software applications. They’re the final result of the development process and are deployed in production environments. The security of binaries is essential because compromised binaries can lead to serious consequences, such as unauthorized access, system compromises, and data breaches.
To establish the security of binaries, organizations need to implement certain measures like code signing, integrity checks, and secure distribution channels. By focusing on the security of binaries, organizations can mitigate risk and maintain the integrity of their software supply chain.
Common Risks and Threats to Software Supply Chains
Supply chain attacks
These attacks target specific vulnerabilities in the software supply chain to compromise the integrity and security of software products. Attackers may exploit weaknesses in development tools, build systems, or deployment pipelines to inject malicious code or manipulate software packages.
Open-source vulnerabilities
Open-source software components are widely used in modern software development, but they can introduce security vulnerabilities if not properly managed. Outdated or unmaintained open-source libraries may contain known vulnerabilities that can be exploited by attackers to compromise software applications.
Third-party dependencies
Many software products rely on third-party code libraries and modules. However, these dependencies can introduce security risks if they aren’t thoroughly vetted and updated regularly. Malicious third-party code can compromise the security of the entire software product.
Insider threats
Insider threats arise when individuals with authorized access to the software supply chain intentionally or unintentionally compromise its security. Disgruntled employees, contractors, or even trusted partners may introduce malicious code, steal sensitive data, or disrupt software development processes.
Best Practices for Securing Your Software Supply Chain
Implementing effective security measures is crucial for safeguarding your software supply chain from potential vulnerabilities and attacks. Here are some best practices to help you secure your software supply chain:
- Manage and monitor third-party dependencies effectively: Ensure that third-party components are thoroughly vetted and regularly updated to mitigate potential security risks. Use a centralized repository to manage and track third-party dependencies.
- Use a software composition analysis (SCA) tool: Use an SCA tool to identify and manage open-source components and their associated vulnerabilities within your software. SCA tools provide visibility into the open-source dependencies used in your software, helping you identify and mitigate potential security risks.
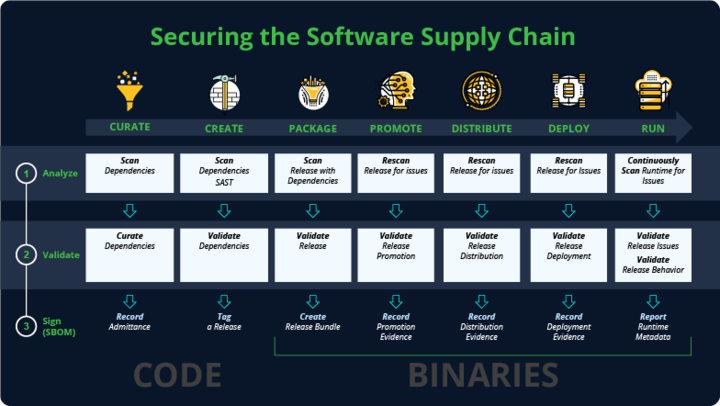
- Compile a Software Bill of Materials (SBOM): An SBOM is a comprehensive list of the components that an application includes or depends on. SBOMs provide the critical visibility you need to identify what’s in your software supply chain.
- Implement strong authentication and access control mechanisms: To restrict access to sensitive information and resources within your software supply chain, you should consider employing multi-factor authentication, role-based access control, and/or least privilege principles.
- Continuously update your SBOM: Because software components and dependencies can change constantly, it’s crucial to update SBOMs on a continuous basis. Whenever you build a new version of your application or update its dependency list, your SBOM should be updated, too.
- Implement secure coding practices: Minimize the introduction of vulnerabilities during software development by following secure coding guidelines, using secure coding tools, and conducting regular code reviews.
- Employ code signing: Employ a code signing mechanism to ensure the integrity and authenticity of your software artifacts throughout the software supply chain. Code signing helps prevent tampering and ensures that only authorized code is deployed.
- Track component versions: Because security issues often impact only certain versions of software or dependencies, it’s important to know not just which components exist in your software supply chain but also what the version of each component is.
- Automate vulnerability detection: Once you know the specific versions of each component of your supply chain, you can use a software supply chain security tool to check automatically whether any components are subject to known security vulnerabilities.
- React based on risk severity: Not all supply chain security risks pose the same level of threat. Some may allow for more severe types of attacks than others, and some may only be able to be exploited under conditions that won’t exist within your environment. For these reasons, it’s important to gain context of the scope of risk that each security issue poses to you and prioritize the most serious threats.
Automating Software Supply Chain Security with CI/CD
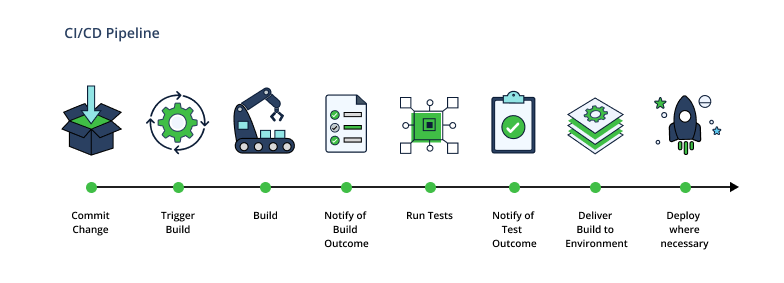
Automating software supply chain security with CI/CD is essential for organizations looking to streamline security processes and ensure continuous protection. By integrating security measures into the continuous integration and continuous delivery (CI/CD) pipeline, organizations can significantly enhance the security posture of their software supply chain.
Leveraging CI/CD pipelines enables organizations to continuously integrate security checks and tests into their software development process. This allows for the early identification and remediation of vulnerabilities, reducing the risk of security breaches. Automated dependency management tools can also be implemented to monitor and update third-party dependencies, ensuring that they are secure and up-to-date.
Container scanning and image signing can further enhance the security of software supply chains by identifying vulnerabilities in container images and verifying their integrity. Automated source code analysis tools can also be used to detect security flaws and enforce coding standards, improving the overall security of the software codebase.
Integrating threat modeling and risk assessment into CI/CD pipelines provides organizations with a proactive approach to security by identifying potential threats and vulnerabilities early in the development process. This allows for the implementation of appropriate mitigation strategies, reducing the likelihood of successful attacks.
By automating software supply chain security with CI/CD, organizations can significantly reduce the risk of security breaches, improve compliance with industry standards and regulations, and enhance the overall trust and reliability of their software products. Here are a few bonus suggestions to help you make the most of CI/CD automations and optimizations:
- Avoid unnecessary tools: A lean CI/CD pipeline is an efficient CI/CD pipeline. Avoid tools and processes that don’t add value to your software delivery operations.
- Strive for scalability: The complexity of each application release can vary, so your CI/CD tools sometimes need to handle more capacity than other times. Where possible, configure tools to be scalable by, for example, taking advantage of IaaS hosting and autoscaling rules in order to avoid paying for CI/CD pipeline infrastructure that you don’t actually need.
- Make smaller releases: In general, it’s better to push our small software updates on a frequent basis than to push out large updates on a less frequent basis. The reason why is that the more changes you include in each set of updates, the higher the risk that you’ll encounter a problem that will delay the new deployment. So, smaller is better when it comes to planning what goes into each release.
- Tweak tooling configurations: Most CI/CD tools are configured by default to automate processes. But you can often improve the efficiency of your tools by modifying the default configurations. For example, you may want to tweak the policies that guide your CI server in order to avoid validation checks that are unnecessary for your code, and that could slow down the CI process.
Choosing the Right Tools and Solutions
Choosing the right tools and solutions is essential for effective software supply chain security. These tools and solutions can help you automate security processes, monitor for threats, and respond to incidents quickly and effectively.
When selecting tools and solutions, consider the following factors:
- The size and complexity of your software supply chain
- The specific risks and threats you face
- Your budget and resources
- Your existing security infrastructure and processes
- The level of integration you need with your existing systems
- The ease of use and maintainability of the tools and solutions
Based on these factors, you can choose from a variety of tools and solutions to secure your software supply chain. Some examples include:
- Software composition analysis (SCA) tools to identify open source components and their associated vulnerabilities
- Vulnerability management tools to track and patch vulnerabilities
- Code signing tools to protect the integrity of your software
- Monitoring tools to detect suspicious activity in your software supply chain
- Incident response tools to help you respond to security incidents quickly and effectively
By choosing the right tools and solutions, you can significantly improve the security of your software supply chain and protect your organization from the risks and threats it faces.
The importance of tool consolidation
According to IDC, most companies use anywhere between six and 20 tools to manage and monitor their software supply chain. It’s no surprise that with so many tools being used, tool sprawl occurs. To combat this, DevOps and Security teams are now considering tool consolidation.
Tool consolidation is the process of combining redundant tools or using a single tool for multiple functions. For example, by using a software supply chain platform as a single source of truth for all their software development activities, organizations can consolidate their DevOps and security tools to streamline their software delivery pipelines and automate software releases.
Future Trends and Emerging Technologies
As the software landscape continues to evolve, it’s crucial to stay aware of emerging trends and technologies that can further enhance software supply chain security. Here are a few examples:
Trend 1: Cloud
With an ever-increasing reliance on free and open source software, ensuring software supply chain security has become vital. This is particularly relevant in cloud-native environments where everything is software-defined. While it may seem relatively straightforward to move images and files to the cloud, the process of moving entire processes to the cloud introduces a new set of challenges.
In cloud-native environments, the complexity of the software supply chain increases as applications are built using microservices and containerization. Each component, such as infrastructure, dependencies, and libraries, needs to be carefully managed and secured to prevent vulnerabilities that might lead to data exposure, system compromise, or unauthorized access. To address these challenges, organizations should prioritize software supply chain security. By doing so, they can mitigate risks, safeguard data, maintain system integrity, and ensure overall security in the cloud-native ecosystem.
Trend 2: Security
Technology that addresses software supply chain security is continuing to evolve. For true end-to-end software supply chain security, vulnerability detection, vulnerability scoring, and remediation should all be unified within a single platform.
A unified platform enables better visibility and control over the entire software supply chain. It provides a centralized view of the security posture, allowing organizations to track vulnerabilities, track remediation progress, and guarantee compliance with security policies and standards. This holistic approach to software supply chain security helps organizations stay ahead of emerging threats, minimize the attack surface, and maintain a robust security posture throughout the software development lifecycle.
Trend 3: AI/ML-Ops
Artificial intelligence (AI) and machine learning (ML) are playing an increasingly important role in software supply chain security. These technologies can analyze vast amounts of data, enabling the identification of anomalous behavior, detection of potential threats, and automation of security responses.
Trend 4: Developer Efficiency and Productivity
While shift-left security is a necessary step for end-to-end software supply chain security, it places more responsibility on developers. To make sure this doesn’t hinder developer efficiency and productivity, security measures are often embedded into development workflows through automation and IDE tools. This allows for real-time identification and remediation of security vulnerabilities, empowering developers to reduce the risk of introducing vulnerabilities while writing code.
Trend 5: DevSecOps
The integration of security into DevOps practices, known as DevSecOps, is becoming increasingly essential for effective software supply chain security. DevSecOps emphasizes the collaboration between development, security, and operations teams throughout the software development lifecycle. By integrating security into devops pipelines, organizations can identify and address vulnerabilities early on, reducing the risk of security breaches.
DevSecOps protects the overall integrity of the software supply chain. With security considerations embedded into the development process, organizations can proactively address potential vulnerabilities and implement necessary security measures. This collaborative approach fosters a culture of shared responsibility for security, enabling teams to work together to deliver secure software and maintain the trust of users and stakeholders.
The JFrog Software Supply Chain Platform
The JFrog platform is the universal software supply chain solution for DevOps, Security, and MLOps. With 50+ integrations, it can house your entire ecosystem of tools, providing automated, integrated, extendable, and secure software supply chain management. Continue to explore more topics related to the software supply chain here, or if you’re ready to give JFrog a try, start your free trial.