Managing Software Vulnerabilities: A Step-by-Step Guide
Software vulnerabilities are problems within software that attackers can exploit to take control of an application, steal data, disrupt service to users or otherwise cause harm. Due to the complexity of applications and the environments in which they run, it is virtually impossible to prevent vulnerabilities from existing within software. Instead, the best defense against vulnerabilities is to deploy tools that can detect and remediate them as they appear.
There are many types of software vulnerabilities, including but not limited to coding flaws, vulnerable dependencies or third-party components and configuration errors. Because software vulnerabilities come in many forms, there is no simple way to address them. Instead, as this article explains, organizations require a well-planned, multi-pronged approach to managing software vulnerabilities.
Main types of software vulnerabilities
The first step in managing software vulnerabilities is understanding how they originate and what they look like. The most common types of vulnerabilities include:
- Coding flaws: Problems within the way developers write source code could invite exploits. For example, lack of proper data validation may allow attackers to inject malicious code into an application in order to access sensitive data or take control of the application.
- Vulnerable components: Third-party components that are introduced into an application, such as open source libraries or modules, could contain flaws that enable breaches.
- Configuration flaws: Mistakes in the way applications or their host environments are configured may lead to exploits. For instance, overly permissive access controls may allow a user to access data in an application that the user should not be able to view.
The risk posed by software vulnerabilities can vary depending on the nature of the vulnerability and the application or data it impacts. For example, a vulnerability that can be executed remotely (as opposed to requiring physical access to a local environment) would typically be considered one that poses a severe level of risk. As another example,vulnerabilities can only be executed under rare conditions, for example, which means they carry a lower risk than those that can be exploited in any type of environment. As a third example, consider a vulnerability that enables a Denial-of-Service exploit: The level of risk it poses would be much greater if it threatens critical systems (like an IoT medical device), as opposed to a non-critical software application.
Steps for managing vulnerabilities
Protecting against software vulnerabilities requires a step-by-step approach that allows you to find, assess and remediate vulnerabilities at all layers of your software stack. Ideally, this process will be automated using tools that scan for, assess and help to remediate vulnerabilities both before and after software has been deployed into production.
Step 1: Identify software components
Using Software Composition Analysis tools, scan your software to determine which components exist within it. Comprehensive scanning is important because your applications may contain dependencies, such as open source modules, that are not documented and that you would not otherwise discover.
To identify as many potential risks as possible, you should scan both application source code (if it’s available to you) and application binaries, such as container images or executable files.
You should also perform scanning at multiple stages of the application development lifecycle: First, scan source code. Next, scan application binaries after you’ve compiled your application but before deploying it. Finally, consider scanning applications in production to provide a third layer of defense against potential risks. CI/CD software platforms can help you to enable automated scanning at each stage of the software delivery process.
Step 2: Map components to vulnerabilities
After identifying software components, scan vulnerability databases to determine which components have known vulnerabilities, and whether those vulnerabilities affect the specific version of the software component that you are using.
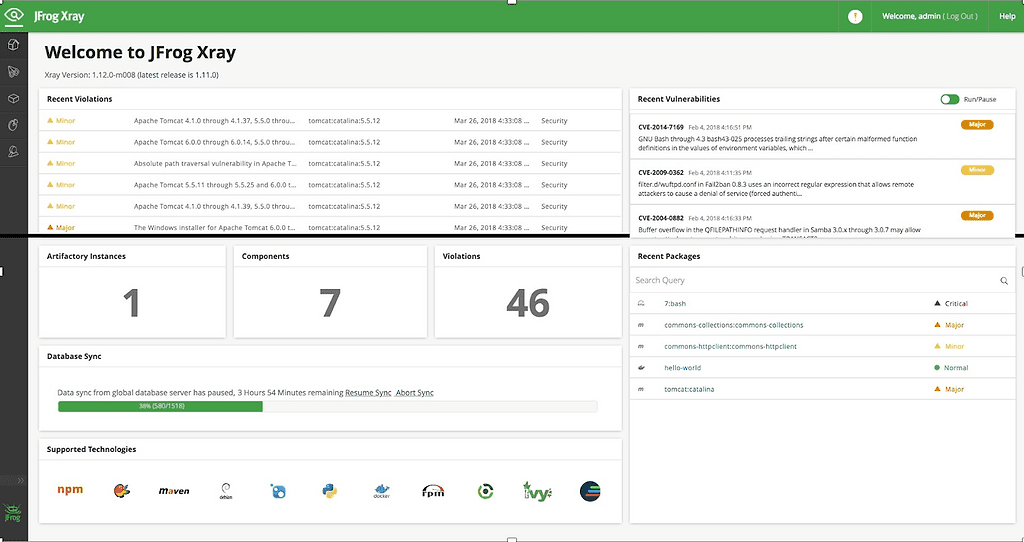
You can simplify this process significantly using a vulnerability scanner like JFrog Xray, which performs deep, iterative scanning in order to detect vulnerabilities across all layers of an application and its dependencies.
Vulnerability scanning with JFrog Xray.
Step 3: Perform static application security testing
Static application security testing (SAST) allows you to detect vulnerabilities in source code that you have developed in-house (otherwise known as first-party source code). By scanning your business’s own source code, you can identify potential vulnerabilities that your developers have inadvertently introduced into an application.
Step 4: Perform dynamic application security testing
While scanning source code and binaries for externally sourced components can detect many vulnerabilities, some risks — especially those that originate from custom, proprietary code that is not tracked in vulnerability databases — are likely to remain undetected using these approaches. Many vulnerability scanners focus on software composition analysis (SCA) and only identify vulnerabilities that have already been identified and reported within publicly available source code or application dependencies.
To catch other types of risks, you should also perform Dynamic Application Security Testing (DAST). DAST tools run tests designed to identify security vulnerabilities or weaknesses by interacting with running applications. For example, a DAST tool may inject malicious commands into an application in order to assess whether the application blocks them.
Step 5: Scan environment configurations
As noted above, some software vulnerabilities originate not from applications, but from the way applications (or the environments that host them) are configured. You can detect these vulnerabilities using configuration auditing tools, which automatically scan application configurations and alert you to settings that appear insecure.
For example, a configuration auditor might flag a firewall configuration that allows anyone on the Internet to access an application that should be exposed only to a private network.
Learn more about the zero-day vulnerabilities
Log4shell Zero-Day Vulnerability – also knows as Log4j Vulnerability
SpringShell Zero-Day Vulnerability